ICND2 – Drag and Drop
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Here you will find answers to ICND 2 – Drag And Drop Questions
Question 1
[am4show have=’p2;’]Two offices are displayed below
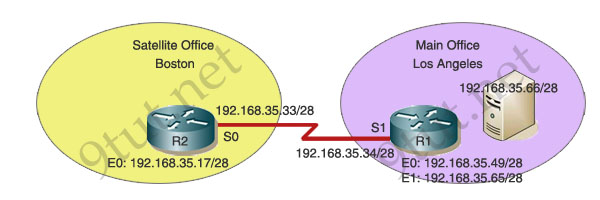
You work as a network technician at 9tut. Study the exhibit carefully. The company has a main office in Los Angeles and a satellite office in Boston. The offices are connected through two Cisco routers. The Boston satellite office is connected through the R2 router s0 interface to the Los Angeles office R1 router s1 interface. R1 has two local area networks. Boston users receive Internet access through the R1 router. Drag the boxes on the top to complete the goal on the left.
Answer:
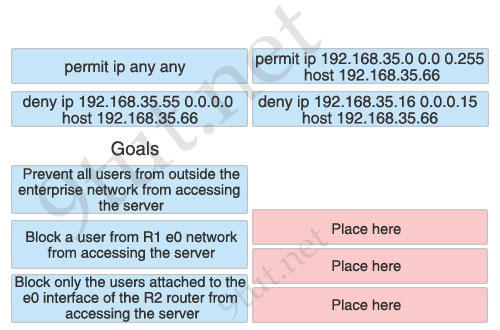
[/am4show]1) Prevent all users from outside the enterprise network from accessing the server: permit ip 192.168.35.0 0.0 0.255 host 192.168.35.66
2) Block a user from R1 e0 network from accessing the server: deny ip 192.168.35.55 0.0.0.0 host 192.168.35.66
3) Block only the users attached to the e0 interface of the R2 router from accessing the server: deny ip 192.168.35.16 0.0.0.15 host 192.168.35.66
Question 2
[am4show have=’p2;’]You are configuring the localhost/nitunetwp office. In particular the host C, with the IP address 192.168.125.34/27, needs to be configured so that it cannot access hosts outside its own subnet. You decide to use the following command:
access-list 100 deny protocol address mask any
You are required to fill in the protocol, address, and mask in this command using the choices below:
Answer:
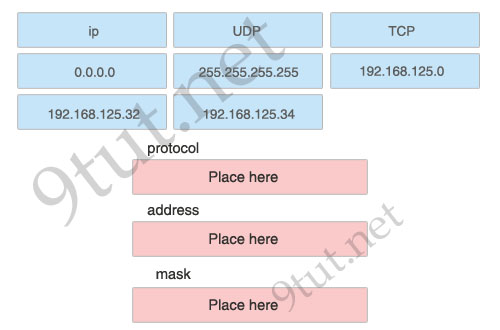
[/am4show]1) protocol: ip
2) address: 192.168.125.34
3) mask: 0.0.0.0
Explanation
The syntax of extended access-list:
access-list 100-199 {permit|deny} {ip|tcp|udp|icmp} source source-mask [lt|gt|eq|neq] [source-port] destination dest-mask [lt|gt|eq|neq] [dest-port]
By telling the router to drop traffic originated from host C (source), we can guarantee that host C can just communicate with hosts inside its own subnet (because this kind of traffic does not need to pass the router and will not be prevented).
Question 3
[am4show have=’p2;’]Exhibit:
| Router# show interfaces s1/0 Seria11/0 is up, line protocol is up Hardware is CD2430 in sync mode Internet address is 192.168.0.10/30 MTU 1500 bytes, BW 128 Kbit, DLY 20000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation PPP, LCP Open Open: CDPCP. IPCP, loopback not set Last input 00:00:00, output 00:00:00, output hang never Last clearing of “show interface” counters 4d21h |
Study the exhibit carefully. You need to match output lines in the exhibit with the proper OSI layer. One line will not be used.
Answer:
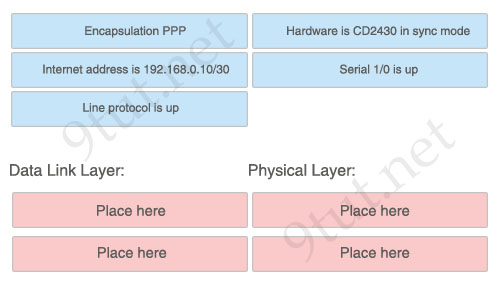
[/am4show]Data Link Layer:
+ Encapsulation PPP
+ Line protocol is up
Physical Layer:
+ Serial 1/0 is up
+ Hardware is CD2430 in sync mode
Question 4
[am4show have=’p2;’]You work as a network administrator for your corporation, your boss is interested in switch ports. Match the options to the appropriate switch ports
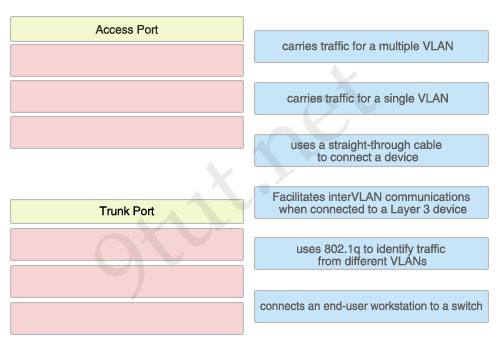
Answer:
[/am4show]Access Port:
+ carries traffic for a single VLAN
+ uses a straight-through cable to connect a device
+ connects an end-user workstation to a switch
Trunk Port:
+ carries traffic for a multiple VLAN
+ Facilitates interVLAN communications when connected to a Layer 3 device
+ uses 802.1q to identify traffic from different VLANs
Question 5
[am4show have=’p2;’]Below is the configuration of the R1 router:
R1(config)# ip route 0.0.0.0 0.0.0.0 192.168.1.1
R1(config)# ip route 10.1.0.0 255.255.255.0 192.168.2.2
R1(config)# ip route 10.1.0.0 255.255.0.0 192.168.3.3
Drag each destination IP address on the top to its correct next hop address at the bottom.
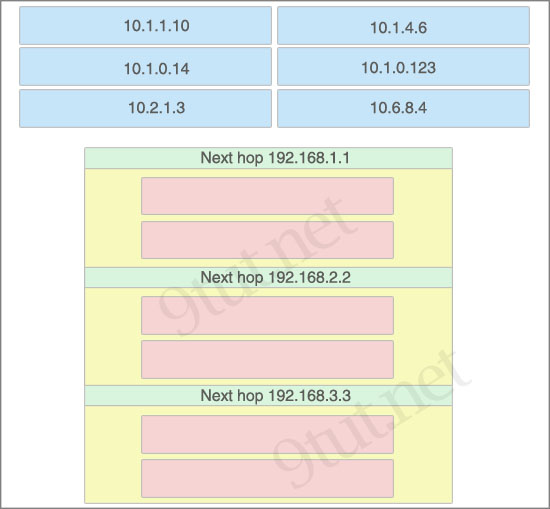
Answer:
[/am4show]Next hop 192.168.1.1:
+ 10.2.1.3
+ 10.6.8.4
Next hop 192.168.2.2:
+ 10.1.0.14
+ 10.1.0.123
Next hop 192.168.3.3:
+ 10.1.1.10
+ 10.1.4.6


Anyone explain Question 5 ?
Remember the routing table process more specific routes first. Another way is to think that the routing table process routes with more bits in the network part of the address first. So a /32 will be process before a /31 and a /31 before a /30 and …
R1(config)# ip route 0.0.0.0 0.0.0.0 192.168.1.1
R1(config)# ip route 10.1.0.0 255.255.255.0 192.168.2.2
R1(config)# ip route 10.1.0.0 255.255.0.0 192.168.3.3
So when these routes get put in to the routing table more specific routes get processed first. So what you need to do is look at the three routes and go okay what is my most specific.
In this case it will be the ip route 10.1.0.0 255.255.255.0 192.168.2.2 so anything in then 10.1.0.X/24 network will go to 192.168.2.2.
Then work your way out so the next least specific route is the ip route 10.1.0.0 255.255.0.0 192.168.3.3 which is saying anything to the 10.1.X.X/16 network goes to 192.168.3.3 So in this case it will be anything that is in 10.1.X.X/16 but isn’t in 10.1.0.X/24 (because we have a more specific route) goes into this box
Finally you have your default route ip route 0.0.0.0 0.0.0.0 192.168.1.1 which is saying anything not listed needs to go to me so put your remaining entries into this box.
excellent explanation
I agree.
Question 1: deny the individual host (#2) needs to come before permit all internal hosts (#1).
@Joe is right.
1st command permit ip 192.168.35.0 0.0 0.255 host 192.168.35.66 permits traffic from host 192.168.35.55 to web server.
deny ip 192.168.35.55 0.0.0.0 host 192.168.35.66 should be first.
Yea Q1 kind of threw me for a loop.
Allowing the whole class C encompasses all the networks in the diagram. So it should be
Deny ip 192.168.35.16 0.0.0.15 host 192.168.35.66 correct? (Preventing all users from outside the enterprise network from accessing the server)
Or maybe just let us know the definition of Enterprise, because to me the two different locations are 2 different Enterprises…unless you are only looking at the networks then it would be the correct answer.
Question, if…”In this case it will be the ip route 10.1.0.0 255.255.255.0 192.168.2.2 so anything in then 10.1.0.X/24 network will go to 192.168.2.2.” is the case, shouldn’t the IPs that go to the “Next hop 192.168.1.1” be:
10.1.0.14
10.1.0.123
?
Correct me if I am wrong, ACL has been removed from ICND2 and moved to ICND1.
I thought so too, yet it still in the ICND2 section.
ACL Theroy is in ICND1. ACL Theroy and Configuration is in ICND2.
IN Question (1)
The answer to “Block only users from e0 network on R2 ” is WEONG
It’s not :deny ip 192.168.35.16 0.0.0.15 host 192.168.35.66
The solution:
The e0 interface ip address is :192.168.35.17/28
so the Subnet ID for this network is :192.168.35.0/28
so the ACL command should be:
(1) deny ip 192.168.35.0 0.0.0.63 host 192.168.35.66
or it may be to be as close as the above choices:(2) deny ip 192.168.35.16 0.0.0.63 host 192.168.35.66
(1) and (2) are the same , the decimal number 16 will be ignored anyway.
I hope some one confirm my answer as well 🙂
cheers
IGNORE MY COMMENT
the answer is right , i made my calculations on a /26 mask not /28
I’m Relly sorry , the answer provided by 9tut is right .
sorry one more time 🙂
To all those who have already made the ICND2
Drag and Drop
It still valid?
All you guys have to do to validate what material is still on the exam is refer to Cisco’s homepage.
They give you the whole material outline here: http://www.cisco.com/web/learning/exams/docs/200-101_icnd2.pdf
VTP and ACLs have been removed completely. And I personally have not encountered a single associated question both times I took the test.
Mike// Refer to the explanation by if_only_i_had_one. Simply saying, longest subnet mask comes first.
10.1.0.14 & 10.1.0.123 meet every condition of ip route command so the longest subnet mask ‘R1(config)# ip route 10.1.0.0 255.255.255.0 192.168.2.2’ is considered first.
I can’t understand Q1 second answer:
2) Block a user from R1 e0 network from accessing the server: deny ip 192.168.35.55 0.0.0.0 host 192.168.35.66
Can somebody explain “deny ip 192.168.35.55 0.0.0.0” – this part ?
Thank you.
I’m sorry guys.
I’ve missed “Block a USER from…”
Just missed word “user” and got confused what the ip 192.168.35.55 is))
Can we write in Q2
access-list 100 deny ip 0.0.0.0 255.255.255.255
???
is it right?
Passed today my ICND@2 by 1000. Got different configuration of the Eigrp & frame Relay labs where there were different DLCIs and IP addresses, but same process was used to get answers (show commands, show ip protocols, show ip interface brief ).
A question about GLBP and a question about netflow were on my test. You can find them here: http://www.examtut.com/2013/09/new-questions-in-ccna-200-120-hsrp-vrrp.html
Study 9tut and this guy i found him really helpful. He has unique way of teaching http://www.danscourses.com If you can do all his videos again and again. Trust me you will get the concept. Also one thing i learned today is if you don’t know the concept it’ll be hard for you in the exam.
All the best to every one in their path. Keep me in your good wishes.
none of these were there today
you should get free dumps and many other helping materials from [ http://adf.ly/o7ba3 ]
Its a direct and safe download and the download speed is ultra high.
Also the dumps is super easy to download.
Enjoy.
Took the exam today. Pass 986/1000. nothing of this were on there.
Thanks 9tut.
Just duplicated the environment in question 1 and although its true that in a normal situation you would need to list the “deny” commands first before the “permit” command – that is not what the question is actually asking. What it is asking is if you can identify the right command with the action that it will take. IE: The first listing says “to prevent all users from outside the enterprise network from entering the server” So you need to match up the right command string with that first listing and put it in the first box next to it. This is not about knowing what order the commands should be in. It is about knowing what each command actually does. That is why it is correct as shown on 9tut.
Tested today, 8/20. None of these were on there.
Do any of the dumps have actual drag and drop questions to practice? If not, i’ll have to go the pencil and paper low tech way.
on question 1, block A user why the subnet mask of all zero’s. to identify a singe user?
the entire enterprise has networks in the 192.168.30 0.0.0 255 range, since there is an implicit deny, allowing all users within this range will keep everyone else out because of the implicit deny at the end of the acl statement?
this seems like a trick question in that the choice for denying is using a permit statement to allow all the addresses within the range of the ip addresses in the enterprise access, without having a choice of statements to deny all addresses outside of this range, but because of the implicit deny, all addresses outside of this range will be denied??
Regarding Question #1
I think the questions that state “Block only the users attached to the e0 interface of the R2 router from accessing the server: deny ip 192.168.35.16 0.0.0.15 host 192.168.35.66”.
Answer should be:
deny ip 192.168.35.0 0.0.0.15 192.168.35.66.
If you breaking down the wildcard mask, it should be 0.0.0.0.15 because it is only the “users”.
There is only 14 users for that subnet plus the subnet number and broadcast for that number.
—->192.168.35.0 —Subnet Number
—->192.168.35.1 —First Usable Address
—->192.168.35.14 —Last usable Address
—->192.168.35.15 –Broadcast.
Even though, if I am wrong, please somebody correct me. Thank you.
Q5 was on my exam on 21st of dec
#5 seems confusing to some. Just find the addresses on the same subnet.
R1(config)# ip route 0.0.0.0 0.0.0.0 192.168.1.1
Destination addresses 10.2.1.3 and 10.6.8.4 are on different subnets completely than the /24 & /16 routes so traffic is sent using the default route to 192.168.1.1
R1(config)# ip route 10.1.0.0 255.255.255.0 192.168.2.2
Destination addresses 10.1.0.4 and 10.1.0.123 are on the same subnet 10.1.0.x —->
Subnet , Valid Hosts , Broadcast
10.1.0.0 , 10.1.0.1 to 10.1.0.254 , 10.1.0.255
R1(config)# ip route 10.1.0.0 255.255.0.0 192.168.3.3
Destination addresses 10.1.1.10 and 10.1.4.6 are on the same subnet 10.1.x.x —->
Subnet , Valid Hosts , Broadcast
10.1.0.0 , 10.1.0.1 to 10.1.255.254 , 10.1.255.255
#1 The term enterprise integrates both main office and a satellite office. The question says to prevent the users from outside the enterprise, that is to say block all the users whose ip address does not fall within 192.168.35.0/24. Its because enterprise (both main office and the satellite office) uses the subnetted ip address of 192.168.35.0 /24. The permit ip 192.168.35.0 0.0 0.255 host 192.168.35.66 statement permit all the users of the enterprise while the implicit deny statement at the end of ACL prevents other users from accessing the server, 192.168.35.66.
so 9tut is right..:)
#1 statement #1 makes no sense. If you permit all the LA office would get in also..CMON PEOPLE WAKE UP
@APRIL WHY ARE YOU TAKING 9TUT BUSINESS AWAY? 9TUT DOES A GREAT JOB WITH LATEST DUMPS… GO AWAY!
hi, for the ICND 2 exam, will I have to configure any routers?
thanks
@ Orla Brian, good question! In INCD2 are we only troubleshooting in Sim (as in icnd1) or do we have to configure too??
Because ACLs are processed top/down we should deny the most specific host first, then deny the more specific segment, then permit only the required block. The implicit deny will handle the rest.
For Question 2, why would you use the .34 address? its a /27 so a new network is formed every 32 address so with the range being .32 – .63 shouldn’t the address used be 192.168.125.32? Would that not prevent the host from communicating outside its subnet as the question has asked you to do?
You’ve misread the question. Its to block a single host not a range.
I hate these kind of questions…. and drag and drop… the way they want us to reorder numbers and shit… don’t cisco have the actual drag and drop, wouldn’t that be much easier?
@all: We had to move all the questions and answers out of 9tut. We can only keep the explanation. You can download the questions and answers at: https://mega.co.nz/#!oIdESYbD!yyu33vygrfKPy4rcmcbV6qW2fxINNoTokuDM3CjA_og
Hi guys!
I think, Question 1 is wrong. First of all, in my opinion, we have to consider these 3 entries not as 3 entries of one single ACL, but as 3 separate ACL’s, each containing one single entry.
1) Prevent all users from outside the enterprise network from accessing the server: permit ip 192.168.35.0 0.0 0.255 host 192.168.35.66 – this seems to be OK.
2) Block a user from R1 e0 network from accessing the server.
e0 interface ip address on R1 is 192.168.35.17/28 , so subnet address is 192.168.35.16. The answer should be: deny ip 192.168.35.16 0.0.0.15 host 192.168.35.66
3) Block only the users attached to the e0 interface of the R2 router from accessing the server
e0 interface ip address on R2 is 192.168.35.49/28 , so subnet address is 192.168.35.48. The range of valid host addresses in this subnet is from 192.168.35.49 to 192.168.35.62. The answer should be: deny ip 192.168.35.55 0.0.0.0 host 192.168.35.66
Passed on the 9th of October 2015 and had Q 4 and 5
I am in agreement with Leila:
For Question 1, Answer 2: Block a user from R1 e0 network from accessing the server: deny ip 192.168.35.55 0.0.0.0 host 192.168.35.66.
The subnet displayed for R1 port e0 is 192.168.35.17/28. The subnet in the answer does not match the subnet of R1 port e0, it but it does match an host address on R2 port e0.
Also of note, the subnet listed as answer 3 does not match the subnet for R2 port e0 (it matches R1 port e0).
Question 1 is correct but its from the expired 640-816 exam. probably will never see it again
FooF u r correct again! Q1 is correct for all u kids who think it’s wrong go back and study ACL’s seems your getting the networks mixed up with a single IP address. OUT