ICND2 – Port Security Questions
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]The following configuration is applied to a Layer 2 Switch:
interface fastethernet 0/4
switchport mode access
switchport port-security
switchport port-security mac-address 0000.1111.1111
switchport port-security maximum 2
What is the result of the above configuration being applied to the switch?
A. A host with a mac address of 0000.1111.1111 and up to two other hosts can connect to FastEthernet 0/4 simultaneously
B. A host with a mac address of 0000.1111.1111 and one other host can connect to FastEthernet 0/4 simultaneously
C. Violating addresses are dropped and no record of the violation is kept
D. The switch can send an SNMP message to the network management station
E. The port is effectively shutdown
Answer: B[/am4show]
Question 2
[am4show have=’p2;’]Refer to the exhibit. Which of these correctly describes the results of port security violation of an unknown packet?
| Switch(config)#interface fastethernet 0/1 Switch(config-if)#switchport mode access Switch(config-if)#switchport port-security Switch(config-if)#switchport port-security maximum 3 Switch(config-if)#switchport port-security mac-address sticky Switch(config-if)#end |
A. port enabled; unknown packets dropped; no SNMP or syslog messages
B. port enabled; unknown packets dropped; SNMP or syslog messages
C. port disabled; no SNMP or syslog messages
D. port disabled; SNMP or syslog messages
Answer: D[/am4show]
Explanation
The default violation mode is shutdown, which will shutdown the port when the maximum number of secure MAC addresses is exceeded. It also sends an SNMP trap, logs a syslog message, and increments the violation counter.
The three violation modes are listed below:
+protect – When the number of secure MAC addresses reaches the limit allowed on the port, packets with unknown source addresses are dropped until you remove a sufficient number of secure MAC addresses or increase the number of maximum allowable addresses. You are not notified that a security violation has occurred.
+restrict – When the number of secure MAC addresses reaches the limit allowed on the port, packets with unknown source addresses are dropped until you remove a sufficient number of secure MAC addresses or increase the number of maximum allowable addresses. In this mode, you are notified that a security violation has occurred. Specifically, an SNMP trap is sent, a syslog message is logged, and the violation counter increments.
+shutdown – In this mode, a port security violation causes the interface to immediately become error-disabled, and turns off the port LED. It also sends an SNMP trap, logs a syslog message, and increments the violation counter. When a secure port is in the error-disabled state, you can bring it out of this state by entering the errdisable recovery cause psecure-violation global configuration command, or you can manually re-enable it by entering the shutdown and no shutdown interface configuration commands. This is the default mode.
(Reference: http://www.cisco.com/en/US/docs/switches/lan/catalyst6500/ios/12.2SX/configuration/guide/port_sec.html)
Question 3
[am4show have=’p2;’]Refer to the exhibit. What three actions will the switch take when a frame with an unknown source MAC address arrives at the interface? (Select three)
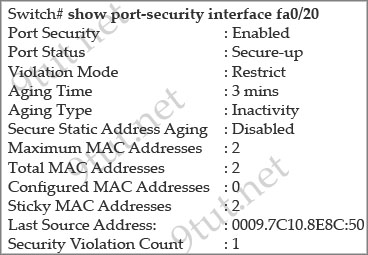
A. Send an SNMP trap.
B. Send a syslog message.
C. Increment the Security Violation counter.
D. Forward the traffic.
E. Write the MAC address to the startup-config.
F. Shut down the port.
Answer: A B C[/am4show]
Explanation
Notice that the Violation Mode is Restrict. In this mod, when the number of port secure MAC addresses reaches the maximum limit allowed on the port, packets with unknown source addresses are dropped. You have to remove the secure mac-addresses below the maximum allowed number in order to learn a new MAC or allowing a host on the port. Also a SNMP trap is sent, a syslog message is logged in the syslog server and the violation counter increases.
(Reference: http://www.cisco.com/en/US/docs/switches/lan/catalyst6500/ios/12.2SX/configuration/guide/port_sec.html)
Question 4
[am4show have=’p2;’]A network administrator needs to configure port security on a switch. Which two statements are true? (Choose two)
A. The network administrator can apply port security to dynamic access ports
B. The network administrator can configure static secure or sticky secure mac addresses in the voice vlan.
C. The sticky learning feature allows the addition of dynamically learned addresses to the running configuration.
D. The network administrator can apply port security to EtherChannels.
E. When dynamic mac address learning is enabled on an interface, the switch can learn new addresses up to the maximum defined.
Answer: C E[/am4show]
Explanation
Follow these guidelines when configuring port security:
+ Port security can only be configured on static access ports, trunk ports, or 802.1Q tunnel ports. -> A is not correct.
+ A secure port cannot be a dynamic access port.
+ A secure port cannot be a destination port for Switched Port Analyzer (SPAN).
+ A secure port cannot belong to a Fast EtherChannel or Gigabit EtherChannel port group. -> D is not correct
+ You cannot configure static secure or sticky secure MAC addresses on a voice VLAN. -> B is not correct.
+ When you enable port security on an interface that is also configured with a voice VLAN, you must set the maximum allowed secure addresses on the port to at least two.
+ If any type of port security is enabled on the access VLAN, dynamic port security is automatically enabled on the voice VLAN.
+ When a voice VLAN is configured on a secure port that is also configured as a sticky secure port, all addresses seen on the voice VLAN are learned as dynamic secure addresses, and all addresses seen on the access VLAN (to which the port belongs) are learned as sticky secure addresses.
+ The switch does not support port security aging of sticky secure MAC addresses.
+ The protect and restrict options cannot be simultaneously enabled on an interface.
Note: Dynamic access port or Dynamic port VLAN membership must be connected to an end station. This type of port can be configured with the “switchport access vlan dynamic” command in the interface configuration mode. Please read more about Dynamic access port here: http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3550/software/release/12-1_19_ea1/configuration/guide/3550scg/swvlan.html#wp1103064
Question 5
[am4show have=’p2;’]Refer to the exhibit. The following commands are executed on interface fa0/1 of 2950Switch.
2950Switch(config-if)#switchport port-security
2950Switch(config-if)#switchport port-security mac-address sticky
2950Switch(config-if)#switchport port-security maximum 1
The Ethernet frame that is shown arrives on interface fa0/1. What two functions will occur when this frame is received by 2950Switch? (Choose two)
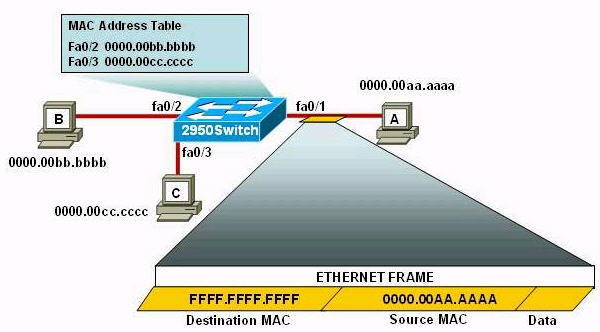
A. The MAC address table will now have an additional entry of fa0/1 FFFF.FFFF.FFFF.
B. Only host A will be allowed to transmit frames on fa0/1.
C. This frame will be discarded when it is received by 2950Switch.
D. All frames arriving on 2950Switch with a destination of 0000.00aa.aaaa will be forwarded out fa0/1.
E. Hosts B and C may forward frames out fa0/1 but frames arriving from other switches will not be forwarded out fa0/1.
F. Only frames from source 0000.00bb.bbbb, the first learned MAC address of 2950Switch, will be forwarded out fa0/1.
Answer: B D[/am4show]
Explanation
The first command 2950Switch(config-if)#switchport port-security is to enable the port-security in a switch port.
In the second command 2950Switch(config-if)#switchport port-security mac-address sticky, we need to know the full syntax of this command is switchport port-security mac-address sticky [MAC]. The STICKY keyword is used to make the MAC address appear in the running configuration and you can save it for later use. If you do not specify any MAC addresses after the STICKY keyword, the switch will dynamically learn the attached MAC Address and place it into your running-configuration. In this case, the switch will dynamically learn the MAC address 0000.00aa.aaaa of host A and add this MAC address to the running configuration.
In the last command 2950Switch(config-if)#switchport port-security maximum 1 you limited the number of secure MAC addresses to one and dynamically assigned it (because no MAC address is mentioned, the switch will get the MAC address of the attached MAC address to interface fa0/1), the workstation attached to that port is assured the full bandwidth of the port.Therefore only host A will be allowed to transmit frames on fa0/1 -> B is correct.
After you have set the maximum number of secure MAC addresses for interface fa0/1, the secure addresses are included in the “Secure MAC Address” table (this table is similar to the Mac Address Table but you can only view it with the show port-security address command). So in this question, although you don’t see the MAC address of host A listed in the MAC Address Table but frames with a destination of 0000.00aa.aaaa will be forwarded out of fa0/1 interface -> D is correct.


Is the “shutdown” violation mode supposed to not send syslog messages? And therefore in question 2 it should be C. port disabled; no SNMP or syslog messages
Or am I wrong? Please help
It’s in default mode which is shutdown – In this mode, a port security violation causes the interface to immediately become error-disabled, and turns off the port LED. It also sends an SNMP trap, logs a syslog message, and increments the violation counter.
@9tut, Q4 totally contradicts explanation on CCNAquestions_oct2019.pdf where it says it’s fine to use port security on etherchannel and compatible with VOICE vlan…unless I misunderstood. Can you help?