test
[watupro 1]
Premium Members: You can practice these questions with our quiz here.
Question 1
R1 and R2 are eBGP peers connected via the 192.168.12.0/24 network as follows:
| R1 interface FastEtherent0/0 description to HQ-A662:55028 ip address 192.168.12.33 255.255.255.224 router bgp 100 network 192.168.12.0 neighbor 192.168.1234 remote-as 200 |
R2 interface FastEthernet0/0 description to HQ-B652:42891 ip address 192.168.12.34 255.255.255.224 router bgp 200 network 192.168.12.0 neighbor 192.168.12.33 remote-as 100 |
Both R1 and R2 are failing to advertise the network. Which action must be taken to correct the problem?
A. changing the router bgp 200 command on R2 to router bgp 100
B. changing the neighbor statement on either router so that the neighbor IP addresses on both devices are
the same
C. adding the /27 network mask to the network 192.168.12.0 statement on both routers
D. adding the ebgp-multihop command to both routers
Answer: C
Question 2
Which two statements about configuring a PPP connection between two routers using CHAP authentication are true? (Choose two)
A. Each router can have a different password
B. Each router can have a different username
C. Each router’s username must be the same as its hostname
D. Each router must have the same username
E. Each router must have the same password
Answer: B E
Question 3
Which two characteristics of standard access lists are true? (Choose two)
A. They can compare source traffic only against a permit or deny statement
B. They must be identified with a number between 1 and 99 or 1300 and 1999
C. They can be identified only with a number between 1 and 99
D. They cannot be used to identify traffic path
E. They can compare source and destination traffic against a permit or deny statement
Answer: A B
Question 4
Which two criteria does a host use to choose from among multiple PADO packets? (Choose two)
A. MAC address of the access concentrator
B. IP address of the access concentrator
C. services offered by the access concentrator
D. packet size
E. name of the access concentrator
Answer: C E
Question 5
Which two options are well-known southbound APIs? (Choose two)
A. OpenFlow
B. OpFlex
C. OpenStack Neutron
D. VTN Coordinator
E. Controller
Answer: A B
Question 6
Which two best practices can you apply to secure the native VLAN? (Choose two)
A. Change the VLAN ID to a value other than the default value
B. Assign it as VLAN 1
C. Assign it as a different VLAN ID at each end of the link
D. Separate it from other VLANs within the administrative domain
E. Assign it a value in the private VLAN range
Answer: A D
Question 7
Which statement would prevent a host from being able to connect to a server that resides in a different VLAN?
A. The server is connected to a Layer 3 switch.
B. The server and its default gateway are on the same subnet.
C. The host is connected to an access port on a switch.
D. The gateway on the host is misconfigured.
Answer: D
Question 8
Which type of routing protocol is used to exchange routes between different autonomous systems?
A. link-state
B. distance-vector
C. exterior routing
D. interior routing
Answer: C
Question 9
Which three types of multicast messages do HSRP-configured routers use to communicate? (Choose three)
A. resign
B. hello
C. ping
D. coup
E. ack
F. syn
Answer: A B D
Explanation
With HSRP, three types of multicast messages are sent between the devices:
+ Hello – The hello message is sent between the active and standby devices (by default, every 3 seconds). If the standby device does not hear from the active device (via a hello message) in about 10 seconds, it will take over the active role.
+ Resign – The resign message is sent by the active HSRP device when it is getting ready to go offline or relinquish the active role for some other reason. This message tells the standby router to be ready and take over the active role.
+ Coup – The coup message is used when a standby router wants to assume the active role (preemption).
Reference: http://www.pearsonitcertification.com/articles/article.aspx?p=2141271
Question 10
Which type of traffic does an 802.1x port pass before authentication?
A. DHCP traffic
B. all normal traffic
C. control-plane traffic
D. EAPOL traffic
Answer: D
Question 11
Which two functions of an SDN controller are true? (Choose two)
A. managing the topology
B. protection against DDoS attacks
C. coordinating VTNs
D. tracking hosts
E. Layer 2 forwarding
Answer: A C
Question 12
Refer to the exhibit. If all four routers come up at the same time, which router becomes the HSRP active router for the 192.168.10.0/24 subnet?

| R1 interface fastethernet0/0 ip address 192.168.1.1 255.255.255.0 standby ip 192.168.1.254 standby priority 125 preempt |
R2 interface fastethernet0/0 ip address 192.168.1.2 255.255.255.0 standby ip 192.168.1.254 standby priority 110 preempt |
| R3 interface fastethemet0/0 ip address 192.168.1.3 255.255.255.0 standby ip 192.168.1.254 standby priority 125 preempt |
R4 interface fastethernet0/0 ip address 192.168.1.4 255.255.255.0 standby ip 192.168.1.254 standby priority 115 preempt |
A. R1
B. R2
C. R3
D. R4
Answer: C
Question 13
Which command do you enter to view OSPFv3 adjacencies?
A. show ipv6 ospf database
B. show running-configuration ospfv3
C. show ipv6 ospf neighbor
D. show ipv6 ospf retransmission-list
Answer: C
Question 14
Which command can you enter to verify the status and ports of a specific VLAN?
A. show interfaces trunk
B. show vlan brief
C. show vlan id <vlan-id>
D. show running-config
Answer: C
Question 15
Which technology can identify and classify mission-critical applications for path selection?
A. PBR
B. NBAR
C. PfR
D. QoS
Answer: C
Question 16
Which two pieces of information can be reported by an IP SLA? (Choose two)
A. delay
B. reachability
C. connected devices
D. Cisco IOS version
E. serial number
Answer: A B
Question 17
Which event triggers a switch stack election?
A. disconnecting a stack member
B. changing the priority of the master switch
C. adding a new powered-on standalone switch to the stack
D. resetting any stack member
Answer: C
====================== New Questions (added on 6th-Feb-2020) ======================
Question 18
Refer to the exhibit. Which type of port generated this output?
|
R1#sh interface switchport module 1 |
A. Layer 3 port
B. trunk port
C. access port
D. private VLAN port
Answer: C
Question 19
Which two best practices do you apply to your network to mitigate the potential security risk of the default VLAN? (Choose two)
A. Use a different VLAN ID for the default VLAN on each device within a VTP domain
B. Configure the default VLAN as a private VLAN
C. Configure the default VLAN on trunk ports only
D. Assign all switch ports to a VLAN other than VLAN 1
E. Configure the management VLAN on a VLAN other than the default VLAN
Answer: D E
Question 20
What command sequence will configure a router to run OSPF and to add network 10.1.1.0/24 to area 0?
A. router ospf
network 10.1.1.0 0.0.0.255
B. router ospf 1
network 10.1.1.0 0.0.0.255
C. router ospf
network 10.1.1.0 255.255.255.0 area 0
D. router ospf 1
network 10.1.1.0 0.0.0.255 area 0
E. router ospf area 0
network 10.1.1.0 255.255.255.0 area 0
F. router ospf area 0
network 10.1.1.0 0.0.0.255 area 0
Answer: D
Question 21
You are configuring an EtherChannel interface to carry multiple VLANs using a Cisco proprietary protocol. Drag and drop the relevant configuration commands from the left onto a valid configuration sequence on the right. Not all commands are used.

Answer:
1 – interface range fa0/0-2
2 – channel-group B mode desirable
3 – interface port-channel B
4 – switchport mode trunk
Explanation
First we have to create an Etherchannel port from a group of interfaces (fa0/0 to fa0/2) using PAgP (which is a Cisco proprietary protocol). Then we can set that logical port-channel interface to trunk mode.
Question 22
Drag and drop the GRE configuration commands from the left onto the correct effects on the right.

Answer:
+ assigns a local interface address as a tunnel endpoint: tunnel source
+ prevents packets from being blackholed: keepalive
+ sets the maximum size of a packet that can traverse the tunnel: ip mtu
+ specifies the IP address of the remote tunnel endpoint: tunnel destination
+ specifies the IP address of the tunnel interface: ip address
Question 23
Which effect of the “router ospf 10” command is true?
A. It disables static routing on the router
B. It enables OSPF on a Layer 3 device
C. It enables OSPF on all connected interfaces on a Layer 3 device
D. It sets the device domain ID to 10
Answer: B
Question 24
Which channel group mode must you configure on both ports to enable a static EtherChannel?
A. auto
B. passive
C. active
D. desirable
E. on
Answer: E
Question 25
What happens when you execute the APIC-EM ACL path trace feature and it fails to discover a matching ACE along the path?
A. The ACLs along the path block the path trace attempt
B. The feature reports the flow as implicitly denied
C. The feature aborts the path trace
D. The feature flags all possible ACE entries as invalid
Answer: B
Explanation
An ACL path trace shows whether the traffic matching your criteria would be permitted or denied based on the ACLs configured on the path.
The following rules effect the ACL path trace results:
+ Only matching ACEs are reported.
+ If you leave out the protocol, source port, or destination port when defining a path trace, the results include ACE matches for all possible values for these fields.
+ If no matching ACEs exists in the ACL, the flow is reported to be implicitly denied.
Question 26
Which type of ACL does the access-list command create?
A. standard numbered IPv4 ACL
B. extended named IPv4 ACL
C. extended named IPv6 ACL
D. standard numbered IPv6 ACL
Answer: A
Question 27
Which troubleshooting tool can you use to replicate traffic within a single switch for analysis?
A. RSPAN
B. EEM
C. local SPAN
D. ERSPAN
Answer: C
Question 1
Drag and drop the router DHCP configuration steps from the left into the Cisco-recommended sequence on the right.
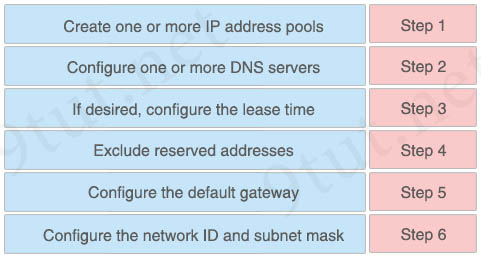
Answer:
+ Step 1: Exclude reserved addresses
+ Step 2: Create one or more IP address pools
+ Step 3: Configure the network ID and subnet mask
+ Step 4: Configure the default gateway
+ Step 5: Configure one or more DNS servers
+ Step 6: If desired, configure the lease time
Explanation
The first step of configuring DHCP is to list the IP addresses that should be excluded from DHCP assignment via the “ip dhcp exclude-address <first-IP> <last-IP>” because this command must be configured in global configuration mode (Router#). Therefore we can only use this command in the first step or last step, but in this question the last step (step 6) should be used to configure the lease time.
Also, according to the “CCNA Official Cert Guide” book, the following steps should be used to configure a DHCP server:
Step 1. Use the “ip dhcp excluded-address first last” command in global configuration mode to list addresses that should be excluded (that is, not leased by DHCP).
Step 2. Use the “ip dhcp pool name” command in global configuration mode to both create a DHCP pool for a subnet and to navigate into DHCP pool configuration mode. Then also:
1. Use the “network subnet-ID mask or network subnet-ID prefix-length” command in DHCP pool configuration mode to define the subnet for this pool.
2. Use the “default-router address1 address2 …” command in DHCP pool configuration mode to define default router IP address(es) in that subnet
3. Use the “dns-server address1 address2 …” command in DHCP pool configuration mode to define the list of DNS server IP addresses used by hosts in this subnet
4. Use the “lease days hours minutes” command in DHCP pool configuration mode to define the length of the lease, in days, hours, and minutes
5. Use the “domain-name name” command in DHCP pool configuration mode to define the DNS domain name.
6. Use the “next-server ip-address” command in DHCP pool configuration mode to define the TFTP server IP address used by any hosts (like phones) that need a TFTP server.
The example below shows how to configure a DHCP server based on above steps:
ip dhcp excluded-address 172.16.1.1 172.16.1.50 ip dhcp pool subnet-left network 172.16.1.0 255.255.255.0 default-router 172.16.1.1 dns-server 172.16.1.12 lease 0 23 59 //means the lease time is "0 Day 23 hours and 59 minutes". domain-name example.com next-server 172.16.2.5
Question 2
Drag and drop the wireless access-point components or features from the left onto the correct description on the right
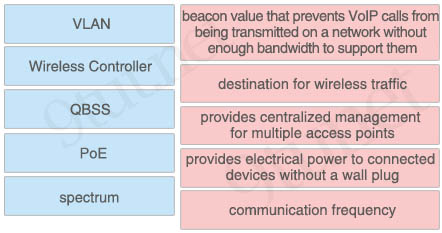
Answer:
+ QBSS: beacon value that prevents VoIP calls from being transmitted on a network without enough bandwidth to support them
+ VLAN: destination for wireless traffic
+ Wireless Controller: provides centralized management for multiple access points
+ PoE: provides electrical power to connected devices without a wall plug
+ spectrum: communication frequency
Question 3
Drag and drop the TCP/IP protocols from the left onto the correct transmission protocols on the right.
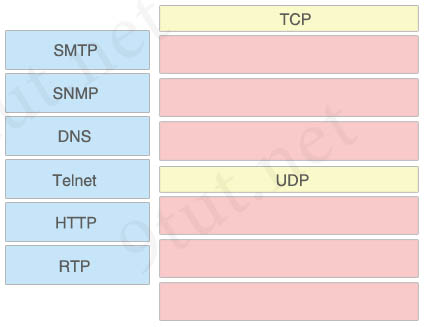
Answer:
TCP:
+ SMTP
+ Telnet
+ HTTP
UDP:
+ SNMP
+ DNS
+ RTP
Explanation
Real Time Transport Protocol (RTP) is a data transfer protocol designed specifically to exchange real-time sensitive, audio-visual data on IP-based networks. RTP is often used in Voice-over-IP telephony (VoIP telephony). RTP is fairly insensitive to packet loss, so it doesn’t require the reliability of TCP.
Question 4
Drag and drop the steps in the process of reloading a router without loading its running configuration from the correct sequence on the right. Not all steps are used.

Answer:
1: Power-cycle the router
2: Enter the break command
3: Enter the confreg 0x2142 command
4: Enter the reset command to reboot the router and ignore the saved configuration
Explanation
Step-by-Step Procedures (to reset your password on 2600 and 2800 Series Routers):
…
3. Use the power switch in order to turn off the router, and then turn the router back on.
4. Press Break on the terminal keyboard within 60 seconds of power up in order to put the router into ROMmon.
If the break sequence does not work, refer to Standard Break Key Sequence Combinations During Password Recovery for other key combinations.
5. Type confreg 0x2142 at the rommon 1> prompt in order to boot from Flash.
This step bypasses the startup configuration where the passwords are stored.
6. Type reset at the rommon 2> prompt.
The router reboots, but ignores the saved configuration.
Question 5
Drag and drop the DHCP configuration commands from the left onto the correct effects on the right.
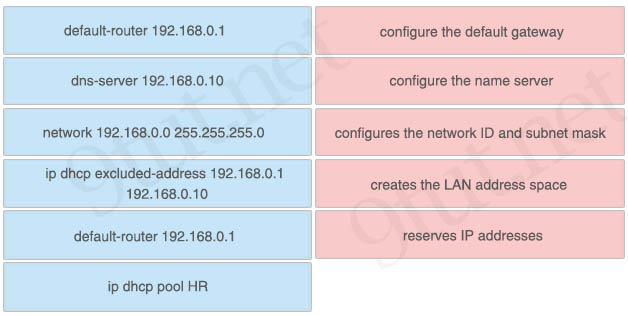
Answer:
+ configure the default gateway: default-router 192.168.0.1
+ configure the name server: dns-server 192.168.0.10
+ configures the network ID and subnet mask: network 192.168.0.0 255.255.255.0
+ creates the LAN address space: ip dhcp pool HR
+ reserves IP addresses: ip dhcp excluded-address 192.168.0.1 192.168.0.10
Question 6
Drag and drop the steps in the process of configuring an ACL to allow web access from a server on the left into the correct sequence on the right. Not all steps are used.

Answer:
1: Begin configuring an extended access list
2: Configure the permit tcp any eq http any statement
3: Apply the ip access-group command to the interface
4: Save the configuration.
(Not used 1): Begin configuring a standard access list
(Not used 2): Apply an access class to the interface
Explanation
This question requires to allow port access so we must use an extended ACL, not a standard ACL.
The command “ip access-class” is only used when applying an ACL to a virtual terminal line (VTY) so it is not correct. Therefore we only have four suitable choices left.
But it seems something is not correct with the “permit tcp any eq http any” statement. With this command HTTP is considered the source port, not destination port. This command is only suitable when we want to drop the reply HTTP traffic from the web server (to the clients).
Note: When a client wants to connect to a web server, it uses the destination port of 80 but chooses a random source port.
Question 7
Which command can you enter to add VLAN 800 to an existing trunk without affecting other VLANs?
A. switchport trunk pruning vlan add 800
B. switchport trunk allowed vlan 800
C. switchport trunk native vlan 800
D. switchport trunk allowed vlan add 800
Answer: D
Explanation
The command “switchport trunk allowed vlan add <vlan-id> adds a new VLAN to the previously allowed VLANs on the trunk. For example suppose our trunk is currently allowing VLANs 1, 4 ,5, 9, 12 then the command “switchport trunk allowed vlan add 10” will allow VLANs 1, 4 ,5, 9, 10, 12 on the trunk.
Question 8
Which purpose of a floating static route is true?
A. It disables dynamic routing.
B. It supersedes the route that is installed in the routing table.
C. It improves resiliency when an interface goes down.
D. It is used in the absence of a default route.
Answer: C
Explanation
Floating static routes are static routes that have an administrative distance greater than the administrative distance (AD) of another static route or dynamic routes. By default a static route has an AD of 1 then floating static route must have the AD greater than 1. Floating static route has a manually configured administrative distance greater than that of the primary route and therefore would not be in the routing table until the primary route fails.
Question 9
Which type of IPv6 address does the SLAAC process create?
A. link-local address
B. multicast address
C. anycast address
D. global address
Answer: D
Explanation
IPv6 stateless address autoconfiguration (SLAAC) is the native IPv6 method used to provide end hosts with IPv6 address and default gateway information dynamically without requiring DHCPv6 address allocation.
Stateless Address Auto-Configuration (SLAAC) is configured as follows:
+ Host sends a router solicitation message.
+ Hosts waits for a Router Advertisement message.
+ Hosts take the first 64 bits of the IPv6 prefix from the Router Advertisement message and combines it with the 64 bit EUI-64 address (in the case of ethernet, this is created from the MAC Address) to create a global unicast message (-> Answer D is correct). The host also uses the source IP address, in the IP header, of the Router Advertisement message, as its default gateway.
Question 10
Which two IPv6 addresses are valid? (Choose two)
A. 2020::DBB::1337:0:5709:3670
B. 2000:::1
C. FF01::101
D. FE80:CD00::0:CDE:1227:0:211D:7790
E. 0001::1:1CD0:8665:9801:96C3:C409
Answer: C E
Explanation
Answer B is not correct with “:::”.
Answer D is not correct as FE80:CD00::0:CDE:1227:0:211D:7790 should be written FE80:CD00::CDE:1227:0:211D:7790 (remove “::0:” with only “::”)
Question 11
Which two differences between the OSI and TCP/IP networking models are true? (Choose two)
A. Only the TCP/IP model has a network interface layer.
B. The OSI model places the TCP protocol in the application layer.
C. Only the OSI model has seven layers.
D. Only the TCP/IP model has a session layer.
E. Only the TCP/IP model has six layers.
Answer: A C
Explanation
The picture below compares the two TCP/IP and OSI models:
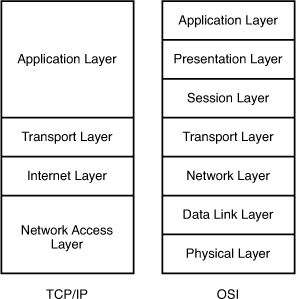
Note: the Network Interface layer (or “Network Access Layer” in the picture above) corresponds to the Physical and Data Link layer in the OSI model. This layer deals with binary digits (0s and 1s) being transmitted across the network medium.
Question 12
Which step is first in the DHCP process between a DHCP client and a DHCP server?
A. The client sends a DHCP Request packet to the server.
B. The server sends a DHCP Offer packet to the client.
C. The client sends a DHCP Discover packet to the server.
D. The server sends a DHCP Ack packet to the client.
Answer: C
Explanation
Remember this order of DHCP messages: DORA (Discover -> Offer -> Request -> Ack). For more information of how DHCP messages are exchanged, please read our DHCP tutorial.
Question 13
Which feature is only supported by named access lists?
A. TCP flag filtering
B. destination-address filtering
C. logging
D. contiguous ports
Answer: A
Explanation
The ACL TCP Flags Filtering feature provides a flexible mechanism for filtering on TCP flags. Before this feature, an incoming packet was matched if any TCP flag in the packet matched a flag specified in the access control entry (ACE). This behavior allowed for a security loop hole, because packets with all flags set could get past the access control list (ACL). TCP flag filtering can be used only with named, extended ACLs.
Question 14
Which type of server is the main authoritative server for DNS requests?
A. recursive resolver
B. root server
C. query server
D. stratum server
Answer: B
Explanation
All DNS servers fall into one of four categories: Recursive resolvers, root name servers, TLD name servers, and authoritative name servers. In a typical DNS lookup (when there is no caching in play), these four DNS servers work together in harmony to complete the task of delivering the IP address for a specified domain to the client (the client is usually a stub resolver – a simple resolver built into an operating system).
Reference: https://www.cloudflare.com/learning/dns/dns-server-types/
The root servers contain the information that makes up the root zone, which is the global list of top level domains. The root zone contains generic top level domains (such as .com, .net, and .org), country code top level domain (such as .se for Sweden or .no for Norway).
Question 15
Drag and drop the ping output characters from the left onto the correct meanings on the right.
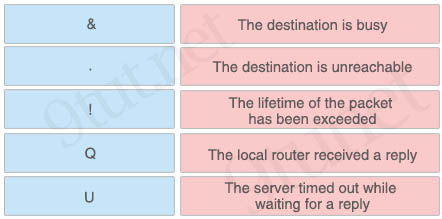
Answer:
+ The destination is busy: Q
+ The destination is unreachable: U
+ The lifetime of the packet has been exceeded: &
+ The local router received a reply: !
+ The server timed out while waiting for a reply: .
Question 16
Which statement about IPv6 address denotation is true?
A. Any group of four zeroes can be omitted from the notation
B. Any group of two or more zeroes can be reduced to a single zero
C. All numbers must be annotated
D. The use of :: indicates a multicast address
Answer: B
Question 17
For which reason does a switch flood a frame to all ports?
A. The destination MAC address of the frame is unknown.
B. The source and destination MAC addresses of the frame are the same.
C. The frame has zero destination MAC addresses.
D. The source MAC address of the frame is unknown.
Answer: A
Question 18
Which banner is the first to be displayed when a user establishes a connection to a router?
A. the MOTD banner
B. the login banner
C. the incoming banner
D. the EXEC banner
Answer: A
| Note for ICND1 candidates (15th-Sep-2019): We have just added many new ICND1 questions at https://www.9tut.net/new-updated-questions/icnd1v3-new-questions-part-3. Please also grasp Part 1 and Part 2 and all the ICND1 100-105 questions at the right-side menu as well. |
| Note for ICND2 candidates (2nd-Feb-2020): We have just added many ICND2 questions at https://www.9tut.net/new-updated-questions/icnd2v3-new-questions-part-8 so please read them carefully before taking the exam. Please also grasp the ICND2 200-105 questions at the right-side menu as well. |
Welcome to Premium Member zone. Now you can access to all the resources for learning ICND1&2 on this site:
+ Flash-based questions to check your knowledge before each topic of ICND1&2. You will find a link to each test before each topic at the right-side menu. We also list all ICND1 specific topic quizzes here for your quick reference:
For ICND1 candidates:
And three parts of ICND1v3 – New Questions (at the right-side menu under “Premium Member Zone”):
+ ICND1v3 – New Questions Part 1
+ ICND1v3 – New Questions Part 2
+ ICND1v3 – New Questions Part 3
+ You can try the ICND1 – Show Configuration Simulator here.
+ You can try the ICND1 – Security Testlet Simulator here.
+ You can try the new ICND1 – DHCP Simulator here.
For ICND2 candidates:
Note for ICND2: There are no VRRP, GLBP, NetFlow, NAT questions (and they are not technologies learned in this exam).
And seven parts of ICND2v3 – New Questions (at the right-side menu under “Premium Member Zone”):
+ ICND2v3 – New Questions Part 1
+ ICND2v3 – New Questions Part 2
+ ICND2v3 – New Questions Part 3
+ ICND2v3 – New Questions Part 4
+ ICND2v3 – New Questions Part 5
+ ICND2v3 – New Questions Part 6
+ ICND2v3 – New Questions Part 7
+ ICND2v3 – New Questions Part 8
+ You can try the ICND2 – EIGRP Troubleshooting Simulator here.
+ You can try the ICND2 – OSPF Neighbor Simulator here.
+ You can try the new ICND2 – GRE Multilink Simulator here.
Note: You should complete all the above quizzes to have strong knowledge of each topic before taking the Composite Quizzes.
+ Composite Flash-based Quizzes to test your whole ICND1&2 knowledge. The 50 questions of Composite Quizzes are randomly taken from specific topic quizzes above. This helps you fully prepare for the ICND1&2 exams. You can find all the composite quizzes for ICND1 exam here and ICND2 exam here.
Also if you have any questions please feel free to comment here or send us an email to support@9tut.net.
Please do not share your account with other people, this would cause your account to be blocked.
Guideline to use the Simulator on 9tut.net
When you access a simulator (for example https://www.9tut.net/final_flash/ICND2/flash_simulator/EIGRP_Troubleshooting_Sim/EIGRP_Troubleshooting_Sim.html) you will see this interface:
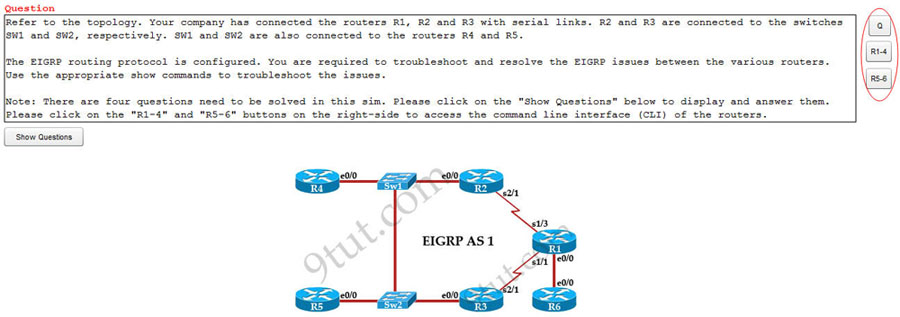
After entering the simulator, please have a look at the right-hand side. Do you see the 3 buttons? Please click on the three buttons on the right-hand side to access the CLI of each device.
Please have a look at the screenshot above:
– The first button (“Q”) represents the question (as the text you are reading).
– The second and third button (“R1-4” & “R5-6”) represents the Command Line Interface (CLI) of six routers from R1 to R6. After click “RT” button, you can type commands to the corresponding textboxes to get information about six routers as shown below
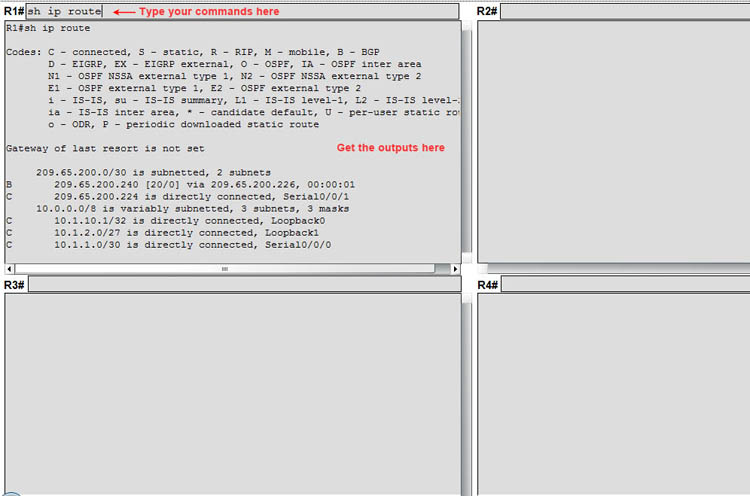
There is a “Show Questions” button at the left-hand side of the simulator. Please click on it to open the questions of that simulator.
Note: These new questions have not been classified into specific topics so please learn them separately.
Premium Member: You can test your knowledge with these questions first via these links:
+ Question 1 to 15
+ Question 16 to 30
+ Question 31 to 50
+ Question 51 to 70
+ Question 71 to 90
+ Question 91 to 110
+ Question 111 to 124
Question 1
Drag and drop the Ethernet types from the left onto the correct service descriptions on the right.
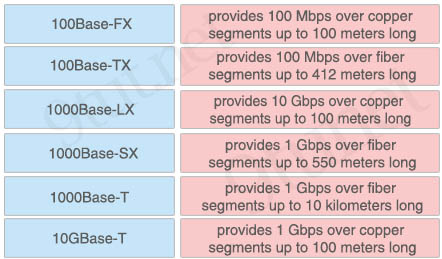
Answer:
+ provides 100 Mbps over copper segments up to 100 meters long: 100Base-TX
+ provides 100 Mbps over fiber segments up to 412 meters long: 100Base-FX
+ provides 10 Gbps over copper segments up to 100 meters long: 10GBase-T
+ provides 1 Gbps over fiber segments up to 550 meters long: 1000Base-SX
+ provides 1 Gbps over fiber segments up to 10 kilometers long: 1000Base-LX
+ provides 1 Gbps over copper segments up to 100 meters long: 1000Base-T
Explanation
First we need to understand the meaning behind each Ethernet type. Let’s take an example with 100Base-FX:
+ 100: represents frequency in MHz (Mega Hertz) for which this cable is made. The greater the MHz, the greater speeds the cable can handle. In this example it is 100MHz. The 100 MHz speed translates to 100Mbit per second.
+ Base (in Ethernet standards): refers to the baseband signalling, which uses the entire bandwidth of the cable to transmit a single signal. Therefore only one communication channel is available at any given time. It is contradict to broadband which shares the bandwidth of the cable.
+ TX/FX: The “T” refers to “Twisted Pair” (pairs that are twisted) physical medium that carries the signal so all “BASE-T…” types are copper.. The “FX” means it’s a two strand fiber-optic cable and supports speeds up to 100 Mbps. Maximum length is usually up to two kms.
100Base-TX (sometimes referred as “T” only) is the IEEE standard that defines the requirement for sending information at 100Mbps on unshielded twisted-pair (UTP) cabling. It uses two of the four available pairs within the UTP cable. It is also called fast Ethernet. Maximum length of 100Base-TX cable is 100 meters.
100Base-FX is simply Fast Ethernet over fiber. The maximum length of any segment of fiber-optic cabling connecting a station (computer) to a hub is 412 meters.
+ SX refers to Short-wavelength laser. It is a fiber optic Gigabit Ethernet standard for operation over multi-mode fiber using a 770 to 860 nanometer, near infrared (NIR) light wavelength. The standard specifies a distance capability between 220 meters and 550 meters.
+ LX refers to Long-wavelength laser. 1000BASE-LX can run over both single mode fiber and multimode fiber with a distance of up to 10 km (for single mode fiber) and 3km (for multimode fiber).
+ ZX refers to extended-wavelength laser. 1000BASE-ZX can only run in single mode fiber. The maximum length can be up to 100km
-> The frequency (in MHz) can be used to eliminate wrong options easily. For the rest we have to remember the maximum distance to solve this question:
Maximum distance: T (TX) (100m) < FX (412m)< SX (220m to 550m) < LX (3km to 10km) < ZX (over 10km)
Question 2
Drag and drop the DHCP messages from the left into the correct sequence for a DHCP IP address request on the right.
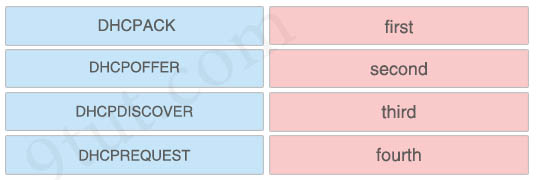
Answer:
+ first: DHCPDISCOVER
+ second: DHCPOFFER
+ third: DHCPREQUEST
+ fourth: DHCPACK
Explanation
Remember this order of DHCP messages: DORA (Discover -> Offer -> Request -> Ack). For more information of how DHCP messages are exchanged, please read our DHCP tutorial.
Question 3
Drag and drop the descriptions of static routing or dynamic routing from the left onto the correct categories on the right.
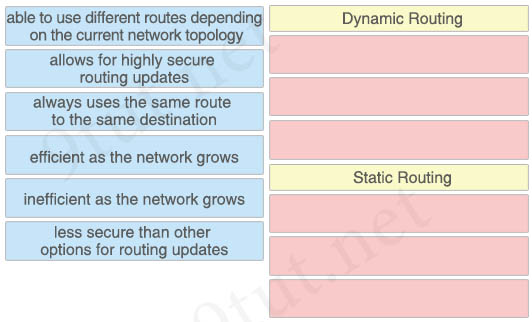
Answer:
Dynamic Routing:
+ able to use different routes depending on the current network topology
+ efficient as the network grows
+ less secure than other options for routing updates
Static Routing:
+ allows for highly secure routing updates
+ always uses the same route to the same destination
+ inefficient as the network grows
Question 4
You are configuring a default route on a Cisco router. Drag and drop the commands from the left into the correct sequence on the right. Not all commands are used.
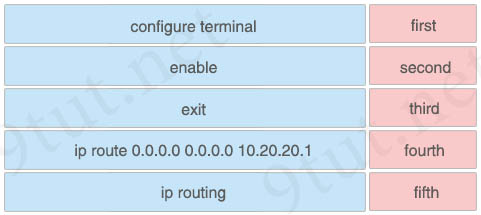
Answer:
+ first: enable
+ second: configure terminal
+ third: ip routing
+ fourth: ip route 0.0.0.0 0.0.0.0 10.20.20.1
+ fifth: exit
Question 5
Drag and drop the address blocks from the left onto the correct address types on the right.

Answer:
+ global unicast: 2000::/3
+ link-local unicast: FE80::/10
+ multicast: FF00::/8
+ unique-local unicast: FC00::/8
Explanation
Below is the list of common kinds of IPv6 addresses:
| Loopback address | ::1 |
| Link-local address | FE80::/10 |
| Site-local address | FEC0::/10 |
| Global address | 2000::/3 |
| Multicast address | FF00::/8 |
Link-local addresses only used for communications within the local subnetwork (automatic address configuration, neighbor discovery, router discovery, and by many routing protocols). It is only valid on the current subnet. It is usually created dynamically using a link-local prefix of FE80::/10 and a 64-bit interface identifier (based on 48-bit MAC address).
Global (unicast) address is globally unicast address sent through the public Internet (equivalent to public IPv4 addresses).
Unique-local unicast (also known as Site-local address). They are analogous to IPv4’s private address classes.
Question 6
Drag and drop the show cdp commands from the left onto the output they generate on the right.
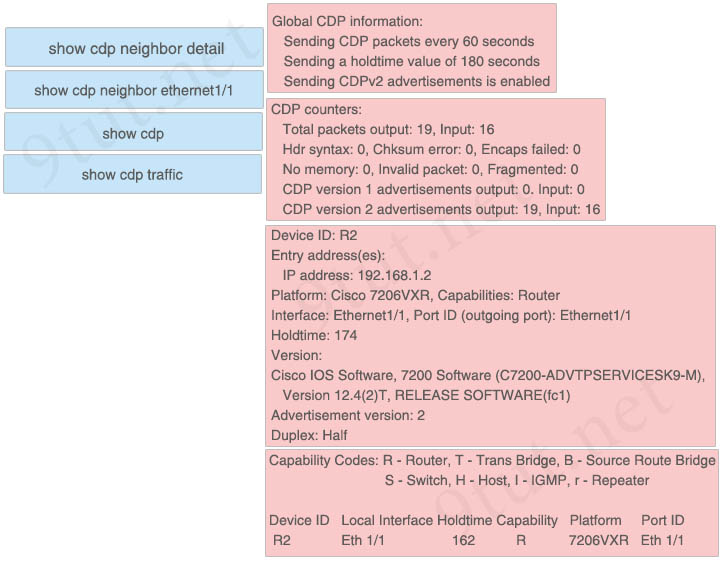
Answer:
+ show cdp:
Global CDP information:
Sending CDP packets every 60 seconds
Sending a holdtime value of 180 seconds
Sending CDPv2 advertisements is enabled
+ show cdp traffic:
CDP counters:
Total packets output: 19, Input: 16
Hdr syntax: 0, Chksum error: 0, Encaps failed: 0
No memory: 0, Invalid packet: 0, Fragmented: 0
CDP version 1 advertisements output: 0. Input: 0
CDP version 2 advertisements output: 19, Input: 16
+ show cdp neighbor detail:
Device ID: R2 Entry address(es): IP address: 192.168.1.2 Platform: Cisco 7206VXR, Capabilities: Router Interface: Ethernet1/1, Port ID (outgoing port): Ethernet1/1 Holdtime: 174 Version: Cisco IOS Software, 7200 Software (C7200-ADVTPSERVICESK9-M), Version 12.4(2)T, RELEASE SOFTWARE(fc1) Advertisement version: 2 Duplex: Half
+ show cdp neighbor ethernet1/1:
Capability Codes: R — Router, T - Trans Bridge, B — Source Route Bridge S - Switch, H - Host, I - IGMP, r - Repeater Device ID Local Interface Holdtime Capability Platform Port ID R2 Eth 1/1 162 R 7206VXR Eth 1/1
Question 7
You are updating the IOS on a Cisco router. Drag and drop the tasks from the left into the correct sequence on the right.
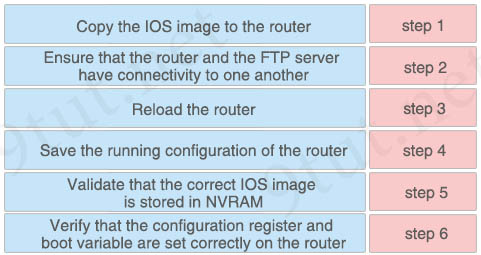
Answer:
Step 1: Ensure that the router and the FTP server have connectivity to one another
Step 2: Copy the IOS image to the router
Step 3: Validate that the correct IOS image is stored in NVRAM
Step 4: Verify that the configuration register and boot variable are set correctly on the router
Step 5: Save the running configuration of the router
Step 6: Reload the router
Explanation
According to https://www.cisco.com/c/en/us/support/docs/routers/3800-series-integrated-services-routers/49044-sw-upgrade-proc-ram.html, the following steps should be performed to upgrade a Cisco IOS software image:
Step 1: Select a Cisco IOS Software Image
Step 2: Download the Cisco IOS Software Image to the TFTP Server
Step 3: Identify the File System to Copy the Image
Step 4: Prepare for the Upgrade
Step 5: Verify that the TFTP Server has IP Connectivity to the Router (equivalent to our Step 1)
Step 6: Copy IOS Image to the Router (equivalent to our Step 2)
Step 7: Verify the Cisco IOS Image in the File System (equivalent to our Step 3)
Step 8: Verify the Configuration Register (equivalent to our Step 4)
Step 9: Verify the Boot Variable (equivalent to our Step 4)
Step 10: Save the Configuration and Reload the Router (equivalent to our Step 5 & 6)
Step 11: Verify the Cisco IOS Upgrade (Verify that the router runs with the proper image)
Question 8
Drag and drop the components of a standard IPv4 access list entry from the left into the correct sequence on the right.

Answer:
+ component 1: access-list
+ component 2: 10
+ component 3: permit
+ component 4: 192.168.1.0
+ component 5: 0.0.0.255
+ component 6: log
Explanation
The full command is “access-list 10 permit 192.168.1.0 0.0.0.255 log”. It allows packets with source IP addresses in the range of 192.168.1.0/24 and creates a log message to the device console. The first packet that the access list inspects triggers the access list to log a message at the device console. Subsequent packets are collected over 5-minute intervals before they are displayed or logged. Log messages include information about the access list number, the source IP address of packets, the number of packets from the same source that were permitted or denied in the previous 5-minute interval, and whether a packet was permitted or denied.
Question 9
Drag and drop the VTP terms from the left onto the correct descriptions on the right.
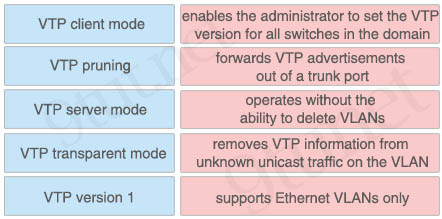
Answer:
+ enables the administrator to set the VTP version for all switches in the domain: VTP server mode
+ forwards VTP advertisements out of a trunk port: VTP transparent mode
+ operates without the ability to delete VLANs: VTP client mode
+ removes VTP information from unknown unicast traffic on the VLAN: VTP pruning
+ supports Ethernet VLANs only: VTP version 1
Explanation
VTPv1 & VTPv2 support VLANs 1 to 1000 only (which is called the Ethernet VLANs).
Question 10
A host is sending packets to a router. Drag and drop the steps in the packet-handling process from the left into the correct sequence on the right.
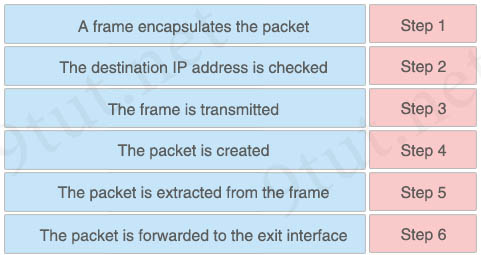
Answer:
+ Step 1: The packet is created
+ Step 2: A frame encapsulates the packet
+ Step 3: The destination IP address is checked
+ Step 4: The frame is transmitted
+ Step 5: The packet is extracted from the frame
+ Step 6: The packet is forwarded to the exit interface
Explanation
Step 1 to 4 describe how the packet is sent from the host: At the host side, data is encapsulated from Layer 7 to Layer 1 so at Layer 3 the packet is created and at Layer 2, a frame encapsulate the packet. The destination IP address is checked before transmitting this frame to the router.
In step 5, the frame arrived to the router and the router extracts the frame to get the packet inside. Then finally the packet is forwarded to the suitable exit interface. Many steps were omitted between step 5 & 6 so it is difficult to understand this question.
Question 11
Drag and drop the OSI model layers from the left onto the correct TCP/IP model layers on the right.
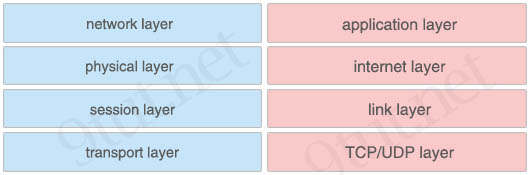
Answer:
+ application layer: session layer
+ internet layer: network layer
+ link layer: physical layer
+ TCP/UDP layer: transport layer
Explanation
The Internet Layer in TCP/IP Model is equivalent to the Network Layer of the OSI Model.

Question 12
Drag and drop the routing protocols from the left onto the default administrative distances on the right.
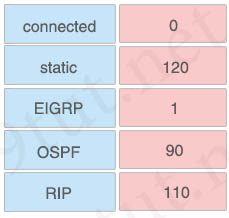
Answer:
+ 0: connected
+ 120: RIP
+ 1: static
+ 90: EIGRP
+ 110: OSPF
Question 13
Drag and drop the VLAN port membership modes from the left onto the correct descriptions on the right.
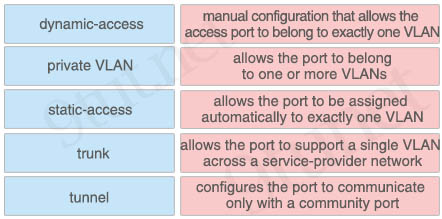
Answer:
+ manual configuration that allows the access port to belong to exactly one VLAN: static-access
+ allows the port to belong to one or more VLANs: trunk
+ allows the port to be assigned automatically to exactly one VLAN: dynamic-access
+ allows the port to support a single VLAN across a service-provider network: tunnel
+ configures the port to communicate only with a community port: private VLAN
Question 14
Drag and drop the IOS commands from a RIP router from the left onto the correct effects on the right.
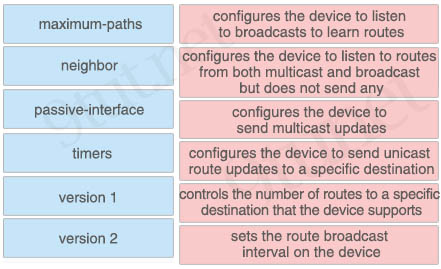
Answer:
+ configures the device to listen to broadcasts to learn routes: version 1
+ configures the device to listen to routes from both multicast and broadcast but does not send any: passive-interface
+ configures the device to send multicast updates: version 2
+ configures the device to send unicast route updates to a specific destination: neighbor
+ controls the number of routes to a specific destination that the device supports: maximum-paths
+ sets the route broadcast interval on the device: timers
Question 15
Drag and drop the DNS-lookup configuration commands from the left onto the correct effects on the right.
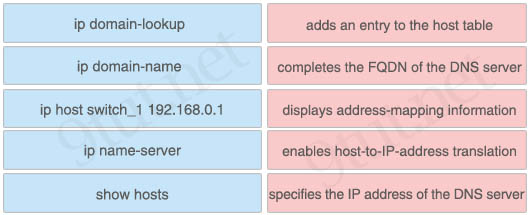
Answer:
+ adds an entry to the host table: ip host switch_1 192.168.0.1
+ completes the FQDN of the DNS server: ip domain-name
+ displays address-mapping information: show hosts
+ enables host-to-IP-address translation: ip domain-lookup
+ specifies the IP address of the DNS server: ip name-server
Explanation
The command “ip name-server <IP address>” specifies the address of one or more name servers.
The command “ip domain-name” defines a default domain name that is used to complete unqualified host names. For example, if we defines “ip domain-name 9tut.net” then a host3 queries to this router is known as host3.9tut.net.
The command “ip domain-lookup” enables DNS lookup feature (DNS-based host name-to-address translation). This command is enabled by default.
Reference: https://www.cisco.com/c/en/us/support/docs/ip/domain-name-system-dns/24182-reversedns.html
The command “ip host” defines a static hostname-to-address mapping in the hostname cache. For example if we define “ip host sw1 192.168.1.1” then we can ping to Sw1 with the command “ping sw1” (or telnet, traceroute… to it with the “telnet sw1”), which is easier to remember than the “ping 192.168.1.1” command.
The following example shows how to configure the DNS server lookup feature:
Switch(config)#ip domain-name 9tut
Switch(config)#ip name-server 192.1.0.1
Switch(config)#ip domain-lookup //Note: this command is enabled by default
Note: A fully qualified domain name (FQDN) is an unambiguous domain name that specifies the exact location in the Domain Name System’s tree hierarchy through to a top-level domain and finally to the root domain. Technically, a FQDN has a trailing dot. For example: router3.9tut.net
The “show hosts” command displays the cached DNS name servers and domain names. For example:
router# show hosts Default domain is 9tut.net Name/address lookup uses domain service Name servers are 255.255.255.255 Host Flags Age(hr) Type Address(es) host1.9tut.net (temp, OK) 1 IP 192.168.1.10 abc (perm, OK) 0 IP 10.0.0.0 10.0.0.2 10.0.0.3
Question 16
Drag and drop the logging types from the left onto the correct descriptions on the right. Not all logging types are used.
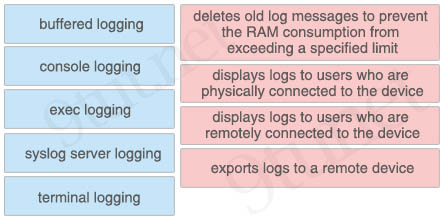
Answer:
+ deletes old log messages to prevent the RAM consumption from exceeding a specified limit: buffered logging
+ displays logs to users who are physically connected to the device: console logging
+ displays logs to users who are remotely connected to the device: terminal logging
+ exports logs to a remote device: syslog server logging
Explanation
Console logging: By default, the router sends all log messages to its console port. Hence only the users that are physically connected to the router console port can view these messages.
Terminal logging: It is similar to console logging, but it displays log messages to the router’s VTY lines instead. This is not enabled by default.
Buffered logging: This type of logging uses router’s RAM for storing log messages. Buffer has a fixed size to ensure that the log will not deplete valuable system memory. The router accomplishes this by deleting old messages from the buffer as new messages are added.
Syslog Server logging: The router can use syslog to forward log messages to external syslog servers for storage. This type of logging is not enabled by default.
Question 17
Refer to the exhibit. Drag and drop the TCP header fields from the left into the correct positions on the right.
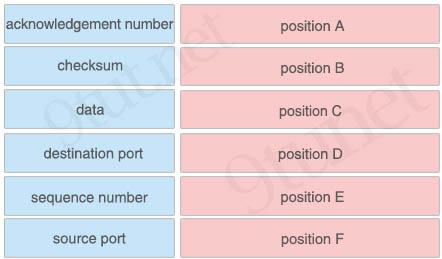
Answer:
+ position A: source port
+ position B: destination port
+ position C: sequence number
+ position D : acknowledgement number
+ position E: checksum
+ position F: data
Explanation
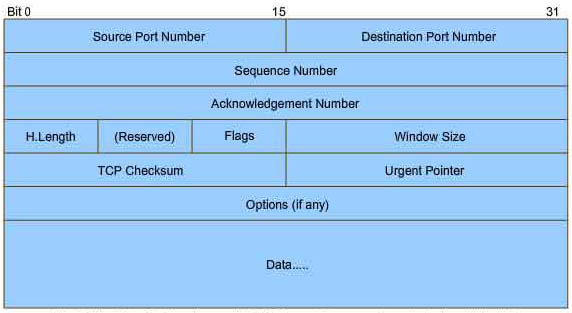
Question 18
Drag and drop the logging configuration commands from the left onto the logging locations they configure on the right.

Answer:
+ syslog server: logging host
+ VTY session: terminal monitor
+ console: logging console
+ internal buffer: logging buffered
Explanation
Console logging: By default, the router sends all log messages to its console port. Hence only the users that are physically connected to the router console port can view these messages. If the console logging is disabled for some reasons, we can enable it again with the “logging console” command. By default, the console receives debugging messages and numerically lower levels. If we want to change the level, we can use the “logging console level” command.
The command “terminal monitor” helps logging messages appear on the your current terminal session.
Buffered logging: This type of logging uses router’s RAM for storing log messages. Buffer has a fixed size to ensure that the log will not deplete valuable system memory. The router accomplishes this by deleting old messages from the buffer as new messages are added.
Syslog Server (logging): The router can use syslog to forward log messages to external syslog servers for storage. This type of logging is not enabled by default.
Question 19
Drag and drop the DNS lookup commands from the left onto the correct effects on the right.
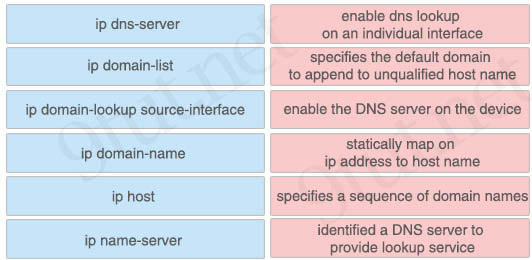
Answer:
+ enable the DNS server on the device: ip name-server
+ specifies a sequence of domain names: ip domain-list
+ enable dns lookup on an individual interface: ip domain lookup source-interface
+ specifies the default domain to append to unqualified host name: ip domain-name
+ statically map on ip address to host name: ip host
+ identified a DNS server to provide lookup service: ip dns-server
Explanation
Question 20
Drag and drop the DHCP client states from the left into the standard order in which the client passes through them on the right.
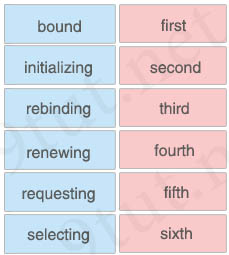
Answer:
initializing – first
selecting – second
requesting – third
bound (binding)– fourth
renewing – fifth
rebinding – sixth
Reference: https://technet.microsoft.com/en-us/library/cc958935.aspx
Question 21
Drag and drop the PDUs from the left onto the correct TCP/IP layers on the right.
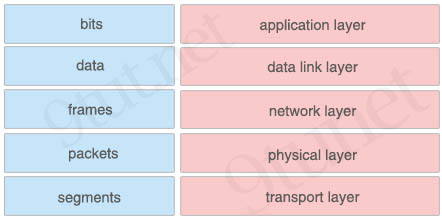
Answer:
+ application layer: data
+ data link layer: frames
+ network layer: packets
+ physical layer: bits
+ transport layer: segments
Question 22
Drag and drop the route source codes in a routing table from the left onto the correct meanings on the right.
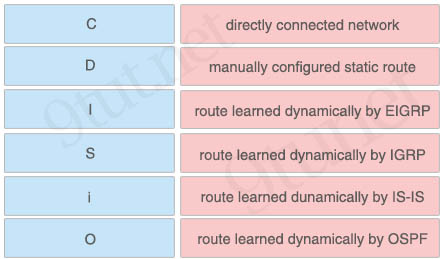
Answer:
+ directly connected network: C
+ manually configured static route: S
+ route learned dynamically by EIGRP: D
+ route learned dynamically by IGRP: I
+ route learned dunamically by IS-IS: i
+ route learned dynamically by OSPF: O
Explanation
The symbol of EIGRP routes is “D”, not “E” because “E” has been used for Exterior Gateway Protocol (EGP), which is the BGP predecessor. But the support for EGP has been removed since Cisco IOS 12.2T.
Question 23
Drag and drop the IEEE standard Cable names from the left onto the correct cable types on the right.
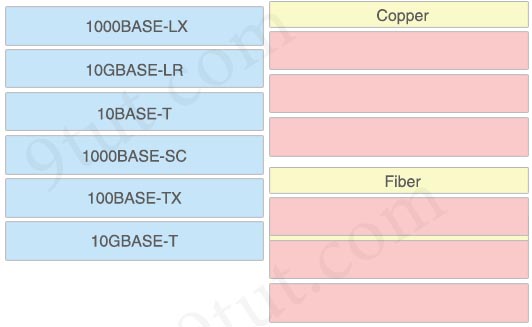
Answer:
Copper:
+ 10BASE-T
+ 100BASE-TX
+ 10GBASE-T
Fiber:
+ 10GBASE-LR
+ 1000BASE-LX
+ 1000BASE-SC
Explanation
The “T” letter symbolizes for “twisted pair cable” so all “BASE-T…” types are copper.
Question 24
Drag and drop the benefits of a Cisco wireless Lan controller from the left onto the correct examples on the right.
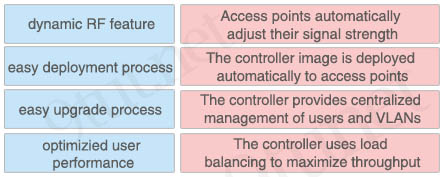
Answer:
+ Access points automatically adjust their signal strength: Dynamic RF Feature
+ The controller image is deployed automatically to access points: Easy upgrade process
+ The controller provides centralized management of users and VLANs: Easy Deployment Process
+ The controller uses load balancing to maximize throughput: Optimized user performance
Question 25
Drag and Drop the protocols from the left onto the correct IP traffic types on the right.
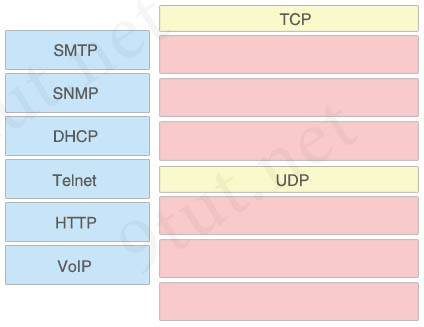
Answer:
TCP:
+ SMTP
+ Telnet
+ HTTP
UDP:
+ SNMP
+ DHCP
+ VoIP
Explanation
In this question we should remember that Simple Mail Transfer Protocol (SMTP) runs on TCP port because email is very important.
Question 26
Drag and drop the IPv6 addresses from the left onto the correct types on the right
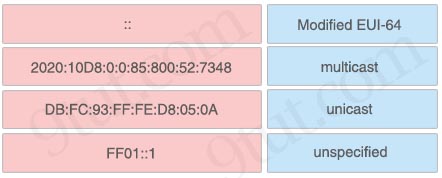
Answer:
+ Modified EUI-64: DB:FC:93:FF:FE:D8:05:0A
+ multicast: FF01::1
+ unicast: 2020:10D8:0:0:85:800:52:7348
+ unspecified: ::
Question 27
Drag and drop the values in a routing table from the left onto the correct meanings on the right
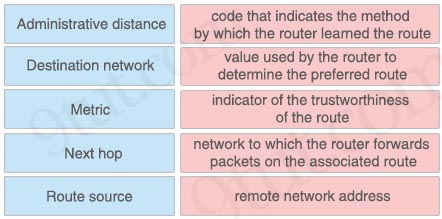
Answer:
+ Administrative distance: indicator of the trustworthiness of the route
+ Destination network: remote network address
+ Metric: value used by the router to determine the preferred route
+ Next hop: network to which the router forwards packets on the associated route
+ Route source: code that indicates the method by which the router learned the route
Question 28
Drag and drop the switching concepts from the left onto the correct descriptions on the right.
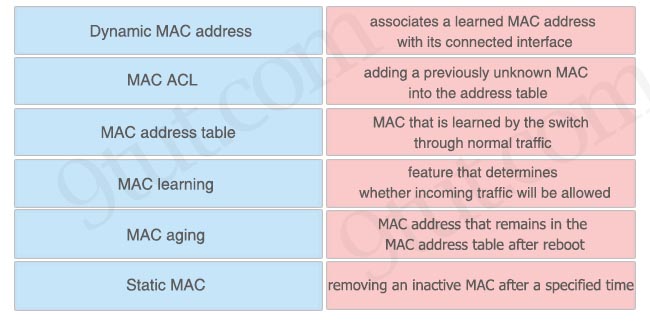
Answer:
+ Dynamic MAC address: MAC that is learned by the switch through normal traffic
+ MAC ACL: feature that determines whether incoming traffic will be allowed
+ MAC address table: associates a learned MAC address with its connected interface
+ MAC learning: adding a previously unknown MAC into the address table
+ MAC aging: removing an inactive MAC after a specified time
+ Static MAC: MAC address that remains in the MAC address table after reboot
Question 29
Refer to the exhibit. Router R4 is reachable from Router R3. Which two scenarios would prevent the subnet 172.16.2.0/24 from being added to the routing table on router R3? (Choose two)
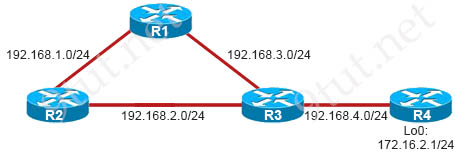
R3#show ip route Gateway of last resort is not set C 192.168.4.0/24 is directly connected, Ethernet1/2 R 192.168.1.0/24 [120/1] via 192.168.3.1, 00:00:09, Ethernet1/0 C 192.168.2.0/24 is directly connected, Ethernet1/1 C 192.168.3.0/24 is directly connected, Ethernet1/0 R3#ping 192.168.4.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.4.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 64/66/68
A. Router R4 is running RIPv1 instead of RIPv2.
B. Network updates are looping around routers R1, R2, and R3.
C. The subnet uses a loopback interface.
D. Routers R3 and R4 are running different versions of RIP.
E. The subnet uses a classless network.
F. Router R3 has split horizon enabled.
Answer: A D
Explanation
Remember that RIPv2 device can understand RIPv1 device but not vice versa so:
+ If R3 runs RIPv1 and R4 runs RIPv2 then R3 cannot understand R4 so it ignores all RIPv2 updates sent from R4.
+ If R3 runs RIPv2 and R4 runs RIPv1 then R4 can only advertise major network 172.16.0.0/24 so R3 can only learn this major network, not the subnet 172.16.2.0/24 (-> Answer A is correct)
-> Answer D is correct.
Question 30
Which address scheme is used to route traffic to the public Internet?
A. 2000::/3
B. 172.30.1.024
C. FC007
D. 192.168.10.024
Answer: A
Explanation
All IPv6 global address starts with 2000::/3 so an IPv6 address must belong to this range to route on the public Internet.
Question 31
Which IP address is the broadcast address for subnet 172.16.0.0/19?
A. 172.16.0.255
B. 172.16.31.255
C. 172.16.32.255
D. 172.31.255.255
Answer: B
Explanation
Increment: 32 (/19 is 1110 0000 at 3rd octet)
Network address: 172.16.0.0
Broadcast address: 172.16.31.255
Question 32
Refer to the exhibit.
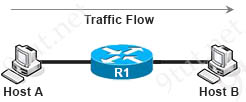
If host A is sending packets to host B, where does the Layer 2 frame rewrite occur?
A. on the router before it forwards the packet to host B
B. on host B when it receives the packet from the router
C. on the router when it receives the packet from host A
D. on host A before it sends the packet toward the router
Answer: A
Explanation
Before forwarding packet to Host B, router R1 needs to rewrite both the source & destination MAC address. The new source MAC would be the MAC address of the exiting interface of R1 and the new destination MAC address would be the MAC address of Host B.
Question 33
Which condition is most important to support the use of syslog messages for troubleshooting?
A. Messages are logged to a UNIX-based server.
B. The router has a large internal buffer space.
C. NTP is in use to ensure accurate timestamps.
D. Messages are logged to a Cisco UCS Server.
Answer: C
Explanation
We have to configure Network Time Protocol (NTP) so that each syslog message is recorded with the correct time which can help us to identify the problem more easily.
Question 34
Which value in a routing table entry represents the subnet mask?
A. prefix length
B. route source code
C. administrative distance
D. next-hop
Answer: A
Explanation
The prefix length in the routing table, for example: 192.168.1.0/24, helps us indicate the subnet mask (in this case /24 is equivalent to the subnet mask of 255.255.255.0).
Question 35
Which statement about port security is true?
A. It is not supported on private VLANs.
B. It can be configured on SPAN destination ports.
C. The default port security configuration allows for a maximum of 10 MAC addresses.
D. In sticky mode, the port retains dynamically-learned addresses during a link failure.
Answer: D
Explanation
The “sticky ” keyword (in the command switchport port-security mac-address sticky [MAC]) is used to make the MAC address appear in the running configuration so even if during a link failure, the port still retains the dynamically-learned addresses. But if we don’t save them (to the startup configuration) before rebooting, they will be lost.
Question 36
Which configuration register value do you enter on a device to bypass the startup configuration?
A. 0x2102
B. 0x2120
C. 0x2124
D. 0x2142
Answer: D
Explanation
By changing the configuration register to 0x2142, when that router reboots it will bypass the startup-config and no password is required.
Question 37
Which two DNS record types are currently supported? (Choose two)
A. NIL
B. A
C. MX
D. B
E. ACK
Answer: B C
Explanation
Commonly used record types:
+ A (Host address)
+ AAAA (IPv6 host address)
+ ALIAS (Auto resolved alias)
+ CNAME (Canonical name for an alias)
+ MX (Mail eXchange)
+ NS (Name Server)
+ PTR (Pointer)
+ SOA (Start Of Authority)
+ SRV (location of service)
+ TXT (Descriptive text)
Question 38
Which command can you enter to forward DHCP requests to a server on behalf of a client on a different network?
A. service dhcp
B. network 192.168.100.0 255.255.255.0
C. ip helper-address address
D. ip dhcp-pool pool_name
Answer: C
Explanation
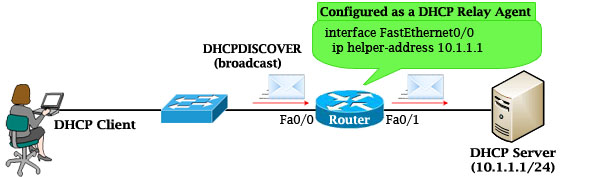
If the DHCP Server is not on the same subnet with the DHCP Client, we need to configure the router on the DHCP client side to act as a DHCP Relay Agent so that it can forward DHCP messages between the DHCP Client & DHCP Server. To make a router a DHCP Relay Agent, simply put the “ip helper-address <IP-address-of-DHCP-Server>” command under the interface that receives the DHCP messages from the DHCP Client.
Question 39
Which statement about device security is true?
A. A router can have a maximum of two passwords configured
B. The password you configure is encrypted in the running configuration by default
C. The enable password must be used before the enable secret password
D. If an encrypted password is lost, the NVRAM configuration must be ignored on boot
Answer: D
Explanation
NVRAM holds the router’s startup configuration file. Therefore if we forget the password of the device, we should ignored the NVRAM configuration on boot. We usually do this by changing the configuration register to 0x2142.
Question 40
Which option can be used in case a backup route is required in the routing table?
A. floating static route
B. No extra configuration is required.
C. next hop
D. route distribution
Answer: A
Explanation
Floating static routes are static routes that have an administrative distance greater than the administrative distance (AD) of another static route or dynamic routes. By default a static route has an AD of 1 then floating static route must have the AD greater than 1. Floating static route has a manually configured administrative distance greater than that of the primary route and therefore would not be in the routing table until the primary route fails.
Question 41
Which two features are supported with SLAAC? (Choose two)
A. Duplicate IPv6 addresses are detected.
B. The first 64 bits of a device IPv6 address can be calculated automatically from its MAC address.
C. IPv6 address have an infinite lifetime by default.
D. Router advertisements can track lifetime timers.
E. Globally-routed paths are preferred over equal-cost link-local paths.
Answer: A D
Explanation
IPv6 stateless address autoconfiguration (SLAAC) is the native IPv6 method used to provide end hosts with IPv6 address and default gateway information dynamically without requiring DHCPv6 address allocation.
Stateless Address Auto-Configuration (SLAAC) is configured as follows:
+ Host sends a router solicitation message.
+ Hosts waits for a Router Advertisement message.
+ Hosts take the first 64 bits of the IPv6 prefix from the Router Advertisement message and combines it with the 64 bit EUI-64 address (in the case of ethernet, this is created from the MAC Address) to create a global unicast message (-> Answer B is not correct). The host also uses the source IP address, in the IP header, of the Router Advertisement message, as its default gateway.
+ Duplicate Address Detection is performed by IPv6 clients in order to ensure that random addresses that are picked do not collide with other clients.
+ The choice of algorithm is up to the client and is often configurable.
The Router Lifetime field in the Router advertisement (RA) can track lifetime timers.
Question 42a
Which IPv4 address type is used to communicate with all hosts on a subnet?
A. broadcast
B. link-local
C. anycast
D. multicast
Answer: A
Question 42b
Which IPv4 address type can reach each node on a network?
A. unicast
B. anycast
C. broadcast
D. multicast
Answer: C
Question 43
Which VLAN ID is reserved?
A. 1
B. 1002
C. 1006
D. 4094
Answer: B
Explanation
VLANs 1002-1005 are default VLANs for FDDI & Token Ring. They are reserved and cannot be deleted or used for Ethernet.
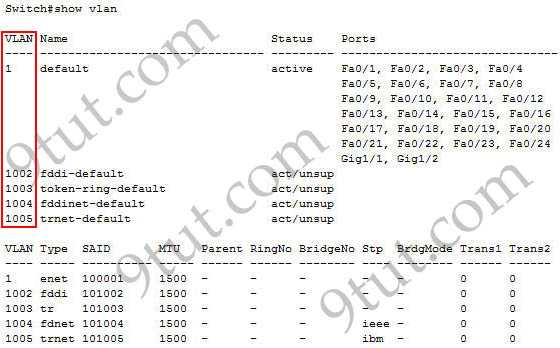
Question 44
An administrator is in the process of changing the configuration of a router. What command will allow the administrator to check the changes that have been made prior to saving the new configuration?
A. Router# show startup-config
B. Router(config)# show running-config
C. Router# show running-config
D. Router# show running-config changes
Answer: C
Question 45
Which step is needed to configure SSH on a switch?
A. Configuring an IP domain name.
B. Configuring RSTP.
C. Configuring an SNMP community string.
D. Configuring Telnet on a VTY line.
Answer: A
Explanation
There are four steps required to enable SSH support on a Cisco IOS router:
1. Configure the hostname command.
2. Configure the DNS domain.
3. Generate the SSH key to be used.
4. Enable SSH transport support for the virtual type terminal (vtys).
Reference: https://www.cisco.com/c/en/us/support/docs/security-vpn/secure-shell-ssh/4145-ssh.html
Question 46a
You attempt to ping a remote device by name from a PC, and the ping operation fails and returns the error message “Ping request could not find host.” You verify that the router DHCP pool is configured with a name server. What are two possible reasons for the problem? (Choose two)
A. The DNS server is not reachable.
B. The PC network interface card device driver is missing.
C. The host that must be resolved does not exist.
D. The subnet mask of the DHCP pool is incorrect.
E. The DHCP server cannot provide an address to the PC.
Answer: A C
Explanation
As we ping by name so a valid DNS server is required. Therefore if we cannot ping to the destination device then maybe either the DNS server or the remote device was down/unreachable.
Question 46b
Refer to the exhibit.
| % Unrecognized host or address, or protocol not running |
You ping a remote device by name from a router, and the ping operation returns this response. What are two reasons for this problem? (Choose two)
A. An ACL on the router blocked the ping.
B. A firewall blocked the ping.
C. The DNS server database does not include a record for the name.
D. The router is blacklisted by the DNS server.
E. Only one DNS server is configured on the router.
Answer: C D
Question 47
Which value does an IPv6 host use to create an EUI-64?
A. the MAC address
B. the OSPFv6 router ID
C. the IPv6 address
D. the IPv4 address
Answer: A
Explanation
Extended Unique Identifier (EUI) allows a host to assign itself a unique 64-Bit IPv6 interface identifier (EUI-64). This feature is a key benefit over IPv4 as it eliminates the need of manual configuration or DHCP as in the world of IPv4. The IPv6 EUI-64 format address is obtained through the 48-bit MAC address. The MAC address is first separated into two 24-bits, with one being OUI (Organizationally Unique Identifier) and the other being NIC specific. The 16-bit 0xFFFE is then inserted between these two 24-bits for the 64-bit EUI address. IEEE has chosen FFFE as a reserved value which can only appear in EUI-64 generated from the an EUI-48 MAC address.
For example, suppose we have the MAC address of C601.420F.0007. It would be divided into two 24-bit parts, which are “C60142” (OUI) and “0F0007” (NIC). Then “FFFE” is inserted in the middle. Therefore we have the address: C601.42FF.FE0F.0007.
Then, according to the RFC 3513 we need to invert the Universal/Local bit (“U/L” bit) in the 7th position of the first octet. The “u” bit is set to 1 to indicate Universal, and it is set to zero (0) to indicate local scope.
Therefore with the subnet of 2001:DB8:0:1::/64, the full IPv6 address is 2001:DB8:0:1:C601:42FF:FE0F:7/64
Question 48
Which protocol does a Cisco IP phone use to identify the voice VLAN?
A. CDP
B. LDAP
C. SIP
D. COS
Answer: A
Explanation
Cisco IP phones use Cisco Discovery Protocol (CDP) to know which VLANs to use.
Note: Voice vlan is just an ordinary VLAN. But in access port configuration you can specify that voice VLAN is exactly for voice traffic.
Question 49
You ping a remote device by name from a router, and the router you are using immediately displays a new prompt. What are two possible reasons for the problem? (Choose two)
A. The IP address of the remote device is listed in multiple ip host statements in the router configuration.
B. The ACL on the router blocked the ping.
C. The DNS server configuration on the router is missing.
D. The DNS server is unreachable.
E. The no ip domain-lookup command is configured on the router.
Answer: C E
Question 50
Which three statements about a meshed topology are true? (Choose three)
A. Every core device is connected to a distribution device.
B. Each access switch must be connected to at least one upstream distribution device and at least one core device.
C. Each distribution device is connected to exactly one core device.
D. Each access switch must be connected to exactly one upstream distribution device.
E. Every upstream distribution device is connected to an access switch.
F. Each access switch must be connected to at least two upstream distribution devices.
Answer: A E F
Explanation
This question wants to mention about hierarchical and meshed topology. Such a topology is shown below:
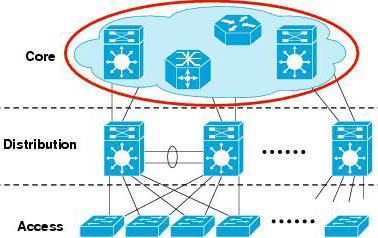
Note: Hierarchical network design has three layers: core, distribution, and access
Reference: https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Campus/HA_campus_DG/hacampusdg.html
Question 51
Which two fields are included in an Ethernet header? (Choose two)
A. source MAC address
B. destination IP address
C. payload
D. Ether Type
E. source IP address
Answer: A D
Explanation
Below is the Ethernet frame format which includes source MAC address and (Ether) type:
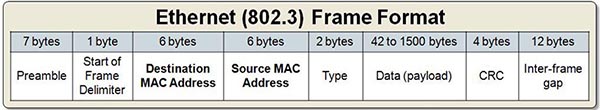
Question 52
Refer to the exhibit.
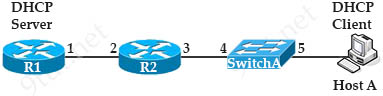
Which interface must be configured as the DHCP relay agent so that host A can receive an IP address from the DHCP server?
A. 1
B. 2
C. 3
D. 4
E. 5
Answer: C
Explanation
If the DHCP Server is not on the same subnet with the DHCP Client, we need to configure the router on the DHCP client side to act as a DHCP Relay Agent so that it can forward DHCP messages between the DHCP Client & DHCP Server. To make a router a DHCP Relay Agent, simply put the “ip helper-address <IP-address-of-DHCP-Server>” command under the interface that receives the DHCP messages from the DHCP Client.

Question 53
Which two network device types perform the translation of internal IP addresses to external IP addresses? (Choose two)
A. ACS
B. routers
C. bridges
D. WLCs
E. firewalls
Answer: B E
Question 54
Which two fields are used in TCP and UDP headers? (Choose two)
A. urgent pointer
B. ACK number
C. checksum
D. length
E. padding
Answer: C D
Explanation
The TCP and UDP headers are shown below:
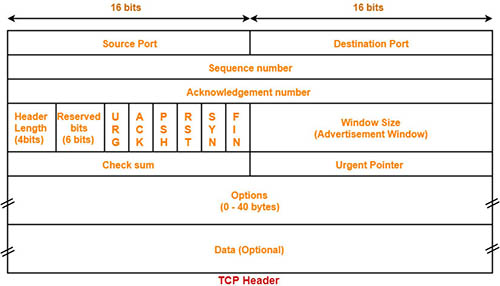
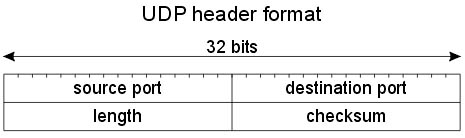
As we can see, the UDP header is very simple with only 4 fields: source port, destination port, length and checksum. The two last fields also present in TCP headers. In which the length field is the size (in bytes) of the UDP header and the encapsulated data.
Question 55
Which two statements about access ports are true? (Choose two)
A. They can act as a host and a trunk port simultaneously
B. They forward all 802.1Q packets to trunk ports
C. An individual access port can transmit traffic for only one data VLAN
D. Each individual access port can support multiple data VLANs
E. They are assigned to VLAN 1 by default
Answer: C E
Question 56
You recently applied a common configuration to several PCs on different VLANs. The PCs are connected to the same switch with a router-on-a-stick, but users report that the PCs cannot ping one another. Which two are possible reasons for the problem? (Choose two)
A. The access ports on the PCs are misconfigured.
B. The native VLAN on the router is misconfigured.
C. The ip default-network command is misconfigured on the router.
D. The trunking protocol is configured incorrectly on the router subinterfaces.
E. The VLAN is configured incorrectly on the router subinterfaces.
Answer: A E
Question 57
Refer to the exhibit.
switch-A#show mac address-table
MAC Address Table
----------------------------------------
Vlan Mac Address Type Ports
---- ----------- ------- --------
1 0000.0000.0001 DYNAMIC Fa0/1
Total Mac Addresses for this criterion: 1
If switch-A receives a frame with destination MAC address 0000.0000.0001 on its Fa0/1 interface, how does it process the frame?
A. It holds the packet until MAC address timer expires and then drops the frame.
B. It forwards the frame back out of interface Fa0/1.
C. It floods the frame to all interfaces except Fa0/1.
D. It drops the frame immediately.
Answer: D
Explanation
In brief, the basic switching function at Layer 2 adheres to these rules for determining forwarding responsibility:
+ If the destination MAC address is found in the CAM table, the switch sends the frame out the port that is associated with that destination MAC address in the CAM table. This process is called forwarding.
+ If the associated port to send the frame out is the same port that the frame originally came in on, there is no need to send the frame back out that same port, and the frame is ignored. This process is called filtering.
+ If the destination MAC address is not in the CAM table (that is, unknown unicast), the switch sends the frame out all other ports that are in the same VLAN as the received frame. This is called flooding. It does not flood the frame out the same port on which the frame was received.
+ If the destination MAC address of the received frame is the broadcast address (FFFF.FFFF.FFFF), the frame is sent out all ports that are in the same VLAN as the received frame. This is also called flooding. The only exception is the frame is not sent out the same port on which the frame was received.
Reference: http://www.ciscopress.com/articles/article.asp?p=2348264
In the output, switch A learned that the device with MAC address of 0000.0000.0001 is attached to port Fa0/1. But the switch receives a frame with the same destination MAC address from port Fa0/1 so the switch will filter out (drop) this frame.
Question 58
Which two statements about prefixes in a routing table are true? (Choose two)
A. The router prefers longer prefixes over shorter prefixes.
B. The router prefers prefixes that have more bit positions for the host than for the network.
C. The router prefers the prefix that includes the most 1 bits in the subnet mask.
D. The router prefers shorter prefixes over longer prefixes.
E. The router prefers the prefix that includes the most 0 bits in the subnet mask.
Answer: A C
Explanation
Suppose there are three routes in our routing table:
router# show ip route .... D 192.168.32.0/26 [90/25789217] via 10.1.1.1 R 192.168.32.0/24 [120/4] via 10.1.1.2 O 192.168.32.0/19 [110/229840] via 10.1.1.3 ....
If a packet arrives on a router interface destined for 192.168.32.1, which route would the router choose? It depends on the prefix length, or the number of bits set in the subnet mask. Longer prefixes are always preferred over shorter ones when forwarding a packet.
In this case, a packet destined to 192.168.32.1 is directed toward 10.1.1.1, because 192.168.32.1 falls within the 192.168.32.0/26 network (192.168.32.0 to 192.168.32.63). It also falls within the other two routes available, but the 192.168.32.0/26 has the longest prefix within the routing table (26 bits verses 24 or 19 bits).
Likewise, if a packet destined for 192.168.32.100 arrives on one of the router’s interfaces, it’s forwarded to 10.1.1.2, because 192.168.32.100 doesn’t fall within 192.168.32.0/26 (192.168.32.0 through 192.168.32.63), but it does fall within the 192.168.32.0/24 destination (192.168.32.0 through 192.168.32.255). Again, it also falls into the range covered by 192.168.32.0/19, but 192.168.32.0/24 has a longer prefix length.
-> This is called “longest prefix match” rule so answer A is correct.
Answer C has the same meaning as “the most 1 bits in the subnet mask” means “longer prefix”
Question 59
Which two attributes of a packet change at every router along the path from source to destination? (Choose two)
A. destination IP address
B. source MAC address
C. packet MTU
D. source IP address
E. destination MAC address
Answer: B E
Explanation
When a packet is sent from a source to a destination, only the source & destination MAC addresses are changed on each segment while the source & destination IP addresses remain unchanged.
Question 60
Refer to the exhibit.

If Host A pings Host B, which statement about the ping is true?
A. The router looks up the destination IP network of the ping in its MAC address table
B. Host A encapsulates the packet within a frame before sending it
C. The ping packet includes both the destination MAC address and the source address
D. Host A sends the packet one byte at a time
Answer: B
Explanation
The router will check the destination IP network in its routing table -> Answer A is not correct.
The ping packet from host A will include: the source IP address of host A, the destination IP address of host B; the source MAC address of host A and the destination MAC address of the inbound interface of R1 -> Answer C is not correct.
When we make a ping from a Windows OS host, each ping packet is 32 bytes but if we ping from a Linux OS host, each ping packet is 64 bytes so it depends on the Operating System (OS) of the host. But each ping packet is surely larger than one byte -> Answer D is not correct.
Question 61
Which statement about port security on a trunk link is true?
A. It error-disables the port after 10 MAC addresses are statically configured
B. It is not supported
C. By default, it shuts down the port if it learns more than one MAC address
D. When it is enabled, it disables the native VLAN configuration
Answer: C
Explanation
Although some online Cisco documents say that “A secure port cannot be a trunk port” (like this document) but some say “Trunk port security extends port security to trunk ports” (like this document) so we decided to test on a Cisco switch version 15.1 and had this result:
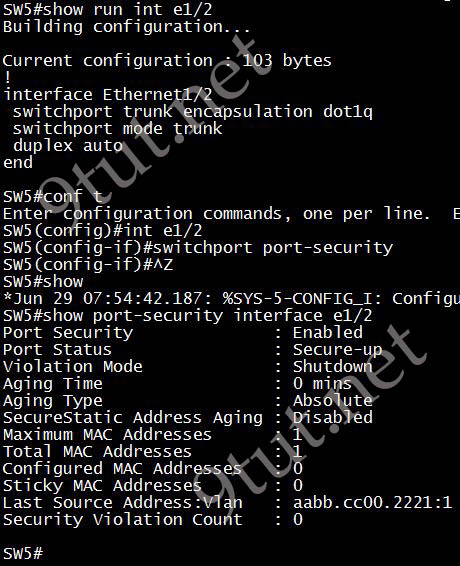
So we can configure port-security on a trunk port and the maximum MAC addresses allowed is 1 and the violation mode is “Shutdown” by default. Therefore it will shutdown the port if it learns more than one MAC address.
Question 62
Which component of an Ethernet frame supports error detection?
A. EtherType
B. frame check sequence
C. 802.1Q tag
D. preamble
Answer: B
Explanation
At the end of each frame there is a Frame Check Sequence (FCS) field. FCS can be analyzed to determine if errors have occurred. FCS uses cyclic redundancy check (CRC) algorithm to detect errors in the transmitted frames. Before sending data, the sending host generates a CRC based on the header and data of that frame. When this frame arrives, the receiving host uses the same algorithm to generate its own CRC and compare them. If they do not match then a CRC error will occur.

Question 63
Which two statements about administrative distance are true? (Choose two)
A. The metric is used to determine which administrative distance is selected from the routing table.
B. The metric is calculated independently of the administrative distance.
C. It identifies the routing protocol priority.
D. It identifies the metric used for path calculation.
E. The metric uses the administrative distance to calculate a path.
Answer: B C
Explanation
The administrative distance (AD) of a routing protocol is fixed while the metric of each routing protocol is calculated based on some parameters (for example in RIP it is the hop count, in OSPF it is the bandwidth…) -> Answer B is correct.
The lower the AD, the higher priority of the routing protocol. For example, EIGRP (AD of 90) is always preferred to OSPF (AD of 110).
Question 64
Which two IPv6 multicast groups are joined when an IPv6 address is configured on an interface? (Choose two)
A. FF02::2
B. 2002::5
C. FF80::6
D. FF80::5
E. FF02::1
Answer: A E
Explanation
Every device automatically joins the all nodes (FF02::1) and solicited-node (FF02::1:FFxx:xxxx) multicast groups. The all-node group is used to communicate with all interfaces on the local link, and the solicited-nodes multicast group is required for link-layer address resolution. Routers also join a third multicast group, the all-routers group (FF02::2).
Reference: IP Routing on Cisco IOS, IOS XE, and IOS XR: AN Essential Guide to Understanding and Implementing IP Routing Protocols
These addresses are equivalent to IPv4 well-known multicast addresses in the range 224.0.0.0 to 239.255.255.255
Question 65
Which command do you enter to assign all untagged packets on a trunk to VLAN 999?
A. switchport trunk pruning vlan add 999
B. switchport trunk allowed vlan 999
C. switchport trunk native vlan 999
D. swtichport trunk allowed vlan add 999
Answer: C
Explanation
By default the native VLAN is 1 but we can assign a new native VLAN by the command “switchport trunk native vlan <vlan-id>”.
Question 66
Which two commands must you apply to a router to configure it as a router-on-a-stick? (Choose two)
A. spanning-tree portfast
B. encapsulation
C. vtp domain
D. vtp transparent
E. ip address
Answer: B E
Explanation
An example of how to configure a router-on-a-stick at router side is shown below:
R1(config)#int fa0/0
R1(config-if)#no ip address
R1(config-if)#no shutdown
R1(config-if)#exit
R1(config)#int fa0/0.10
R1(config-subif)#encapsulation dot1q 10 //Configure dot1q encapsulation for VLAN 10 on sub-interface fa0/0.10
R1(config-subif)#ip address 192.168.1.0 255.255.255.0
R1(config-subif)#no shutdown
R1(config)#int fa0/0.20
R1(config-subif)#ip address 192.168.2.0 255.255.255.0
R1(config-subif)#no shutdown
Question 67
How does an access port configured for VLAN 10 handle an incoming packet with an 802.1q tag for VLAN 2?
A. It drops the packet.
B. It dynamically configures the port to accept traffic on VLAN 2.
C. It adds VLAN 2 to the VLAN database.
D. It forwards the packet to a port on VLAN 2.
E. It processes the packet and places it in a queue for future delivery.
Answer: A
Question 68
In which network topology does each network device have a direct physical connection to every other device?
A. point-to-multipoint
B. mesh
C. bus
D. star
Answer: B
Explanation
Full-mesh is a network topology in which there is a direct link between all pairs of nodes. Below is an example of full-mesh topology.
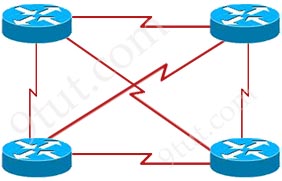
Question 69
Which two statements about IPv6 SLAAC are true? (Choose two)
A. The default gateway of the host is configured during the SLAAC process
B. It is incompatible with DHCP
C. The host uses the EUI-64 algorithm to calculate the first 64 bits of the destination IPv6 address from the MAC address
D. It has a built-in mechanism to identify duplicate IP addresses on the network
E. The host sends a router advertisement message to begin the SLAAC process
Answer: A D
Explanation
IPv6 stateless address autoconfiguration (SLAAC) is the native IPv6 method used to provide end hosts with IPv6 address and default gateway information dynamically without requiring DHCPv6 address allocation.
Stateless Address Auto-Configuration (SLAAC) is configured as follows:
+ Host sends a router solicitation message.
+ Hosts waits for a Router Advertisement message.
+ Hosts take the first 64 bits of the IPv6 prefix from the Router Advertisement message and combines it with the 64 bit EUI-64 address (in the case of ethernet, this is created from the MAC Address) to create a global unicast message (-> Answer B is not correct). The host also uses the source IP address, in the IP header, of the Router Advertisement message, as its default gateway.
+ Duplicate Address Detection is performed by IPv6 clients in order to ensure that random addresses that are picked do not collide with other clients.
+ The choice of algorithm is up to the client and is often configurable.
Question 70
In which two scenarios do you implement private IPv4 IP addresses? (Choose two)
A. on the webmail portal of an organization
B. on the connection that a mobile device uses for application updates
C. to connect network equipment between different IDFs
D. for the VPN solution that end users use to connect to the local network
E. on an application server that connects to a local database server
Answer: C E
Explanation
In general, private IPv4 addresses are suitable for applications/connections that do not need to go to the Internet.
The intermediate distribution frames (IDF) refers to the switches in the access layer which provide connection in a building so they don’t need to use public IPv4 address to go to the Internet -> Answer C is correct.
Question 71
Which two ACL types support IP Access List Entry Sequence Numbering? (Choose two)
A. named
B. reflexive
C. firewall
D. dynamic
E. standard
Answer: A E
Explanation
The IP Access List Entry Sequence Numbering feature allows you to apply sequence numbers to permit or deny statements as well as reorder, add, or remove such statements from a named IP access list. The IP Access List Entry Sequence Numbering feature makes revising IP access lists much easier. Prior to this feature, you could add access list entries to the end of an access list only; therefore, needing to add statements anywhere except at the end of a named IP access list required reconfiguring the entire access list.
For example, we can resequence a standard/extended access list like this:
Device(config)# ip access-list resequence MYACCESSLIST 100 15 //resequence the MYACCESSLIST, starting from 100 and increment 15
After this command the “MYACCESSLIST” ACL will be like this:
| R1#show access-list Standard IP access list MYACCESSLIST 100 permit ip host xxxx host xxxxx 115 permit ip host xxxx host xxxxx 130 permit ip host xxxx host xxxxx 145 permit ip host xxxx host xxxxx 160 permit ip host xxxx host xxxxx 175 permit ip host xxxx host xxxxx 190 permit ip host xxxx host xxxxx |
We can use The IP Access List Entry Sequence Numbering feature in standard, extended and named ACL.
Question 72
Which command can you enter in ROMmon to bypass the password in the router startup configuration?
A. confreg 0x2142
B. configure terminal
C. config-register 0x2102
D. reset
Answer: A
Question 73
For which reason is a DHCP client unable to reach a host in different subnet?
A. The client and its gateway router have been assigned different subnet masks.
B. The client has been configured with only one DNS server.
C. DNS lookup has been disabled on the gateway router.
D. The client is connected to a switch in the same VLAN as its gateway router.
Answer: A
Question 74
Which command or command sequence do you enter to install a default route into a router that is configured with the no ip routing command?
A. ip route 0.0.0.0 0.0.0.0
B. router rip ip default-gateway
C. ip default-network
D. ip default-gateway
Answer: D
Explanation
When using the “no ip routing” command, a router will function like a host so we cannot perform routing function on it. We can only use the “ip default-gateway <IP address>” command to assign a default gateway for it (same as the default gateway in a host).
Question 75
Refer to the exhibit.
| show ip route 192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks |
Router R1 produced this partial output running on a current IOS. Which two statements about R1 and its network environment are true? (Choose two)
A. R1 has a combination of local and connected routes totaling two subnets.
B. R1 has learned a maximum of four networks via routing protocols.
C. R1 has a maximum of two connected subnets including local route.
D. R1 has learned at least one network via routing protocols.
E. R1 has a network environment that supports a maximum of 16 hosts.
Answer: C D
Question 76
Under which circumstance should a network administrator implement only outgoing NAT towards an ISP?
A. when traffic that originates inside the network must be routed to internal hosts
B. when the network has few public IP addresses and many private IP addresses that require outside access
C. when the network must route UDP traffic
D. when traffic that originates outside the network must be routed to internal hosts
Answer: B
Question 77
Which two syslog configuration commands do you use to log warnings to the syslog server? (Choose two)
A. logging trap level informational
B. logging trap level alerts
C. logging trap level notice
D. logging trap level critical
E. logging trap level error
Answer: A C
Question 78
Which three values must you specify to resequence an IP access list? (Choose three)
A. access list name
B. increment
C. starting sequence number
D. interface
E. dynamic access list number
F. ending sequence number
Answer: A B C
Question 79
For which two reasons might you choose to configure dynamic routing instead of static routing on a router? (Choose two)
A. The router is part of a stub network.
B. The router needs access only to a single default route.
C. Dynamic routing requires less router configuration throughout the network than static routing.
D. The network is growing intermittently.
E. Dynamic routing updates are more secure than static routing updates.
Answer: C D
Question 80
All protocols on a network are using their default administrative distances with no redistribution. In which two different ways can you modify them so that OSPF and RIPv2 learned routes are preferred over EIGRP-learned routes? (Choose two)
A. Change the OSPF administrative distance to 5.
B. Change the RIP administrative distance to 70.
C. Change the EIGRP administrative distance to 70.
D. Change the RIP administrative distance to 100.
E. Change the EIGRP administrative distance to 100.
Answer: A B
Question 81
Which two characteristics of plenum cable are true? (Choose two)
A. It is more fire-resistant than nonplenum cable.
B. It can be installed above a drop-down ceiling without additional safety precautions.
C. It is less fire-resistant than nonplenum cable.
D. When it burns, it may release more toxins than nonplenum cable.
E. It requires additional safety precautions when installed above a drop-down ceiling.
Answer: A B
Question 82
Which statement about wireless access points is true?
A. They are Layer 2 devices that are used to extend a LAN to wireless clients.
B. They provide full duplex connectivity to host devices.
C. They are used as routers between LANs in a wireless network.
D. They are used to physically connect host devices to the wireless network.
Answer: A
Question 83
Which option is the default time zone used on Cisco devices?
A. CST
B. UTC
C. EST
D. GMT
E. PST
Answer: B
Question 84
Which circumstance causes a security violation on a switch port with port security enabled?
A. The maximum number of secure MAC addresses is reached on a secure port and an unidentified MAC address attempts an ingress connection.
B. A configured MAC address attempts an ingress connection on a different port in a different VLAN.
C. The minimum number of secure MAC addresses is configured on a secure port and an unidentified MAC address attempts an ingress connection.
D. A minimum number of secure MAC addresses has filled the dynamic table.
Answer: A
Question 85
You have configured two hosts that are connected to a single switch, but reside in different VLANs. Which statement about the configuration is true?
A. The two hosts are unable to communicate without a router.
B. The two hosts can communicate with ICMP.
C. The two hosts are unable to communicate without a trunk port.
D. The two hosts are unable to communicate without a hub.
Answer: A
Question 86
Which type of route is the most trusted?
A. BGP
B. OSPF
C. static
D. connected
Answer: D
Question 87
Which statement about the enable password is true?
A. The space character is not supported.
B. It is not stored in a secured format.
C. It can be up to 32 characters long.
D. It is stored in a secured format.
Answer: B
Question 88
For what reason do you use a standard access list?
A. to filter traffic from identified source addresses
B. to deny traffic to identified destination addresses
C. to load-balance traffic over different interfaces
D. to identify traffic to be label-switched through the network
E. to deny traffic to unidentified destination addresses
Answer: A
Question 89
How does a switch handle a frame in which it detects an error in the frame check sequence?
A. It updates the frame check sequence and forwards the frame to its destination.
B. It discards the damaged frame without further action.
C. It forwards the frame to its destination unchanged.
D. It discards the damaged frame and requests the sender to retransmit it.
Answer: B
Question 90
Which static route can be used to forward a packet that is destined to 192.168.1.23?
A. ip route 192.168.1.16 255.255.255.252 192.168.255.1
B. ip route 192.168.1.0 255.255.255.240 192.168.255.1
C. ip route 192.168.0.0 255.255.255.0 192.168.255.1
D. ip route 192.168.1.20 255.255.255.252 192.168.255.1
Answer: D
Question 91
If a router receives a route 192.168.1.0/24 from peers running OSPF and EIGRP, how does the router forward traffic destined to that network?
A. It uses the path with the lowest metric.
B. It always uses the path learned from OSPF because OSPF is a vendor-neutral protocol.
C. It load-balances traffic across both paths.
D. It always uses the path learned from EIGRP because EIGRP has a lower administrative distance.
Answer: D
Question 92
Which statement about a router on a stick is true?
A. It requires encapsulation to be configured on subinterfaces.
B. It requires encapsulation to be configured on the main interface.
C. The VLAN tag is randomly assigned as a frame exists the interface.
D. A single VLAN can traverse the link.
Answer: A
Question 93
Which IPv6 address does a device use for neighbor discovery?
A. the link-local address
B. the multicast address
C. the unique local address
D. the global unicast address
Answer: A
Question 94
How are MAC addresses removed from a MAC address table?
A. They are removed automatically if they remain inactive for the duration of the switch aging timer.
B. They are removed automatically on a FIFO basis when the address-table limit has been reached.
C. They must be manually cleared from the table.
D. They are removed automatically if they remain inactive for the duration of the global MAC address timer.
Answer: D
Question 95
Which two statements are true about the operation of a full-duplex Ethernet network? (Choose two)
A. There are no collisions in full-duplex mode.
B. A dedicated switch port is not required for each full-duplex node.
C. Ethernet hub ports are preconfigured for full-duplex mode.
D. The device network card and the switch port must be capable of operating in full-duplex mode.
E. In a full-duplex environment, the host network card must check for the availability of the network media before transmitting.
Answer: A D
Question 96
Which value represents a host route?
A. 192.168.1.0/30
B. 192.168.1.0/24
C. 192.168.1.2/31
D. 192.168.1.0/32
Answer: D
Question 97
Which Cisco IOS feature can dynamically assign IP addresses to hosts?
A. DHCP Relay
B. TFTP
C. DNS
D. DHCP
Answer: D
Question 98
Which two statements about the default configuration of a Cisco IOS router are true? (Choose two)
A. In privileged EXEC mode, the console times out after 10 minutes of inactivity.
B. The loopback 0 interface is enabled.
C. The first connected interface becomes the gateway of last resort.
D. The enable password password and enable secret password are both set to cisco.
E. The hostname of the device is displayed in lower-case letters only, even if you specify capital letters.
F. The default hostname is Router.
Answer: A F
Question 99
Which statement about a router-on-a-stick configuration is true?
A. It is most appropriate for use on large networks with both Layer2 and Layer3 switches.
B. It can perform 802.1q encapsulation.
C. It can act as a multilayer switch.
D. It can classify packets for QoS.
Answer: B
Question 100
Which information is missing from a default syslog message?
A. HOSTNAME
B. SEVERITY
C. MESSAGE
D. TIMESTAMP
Answer: A
Question 101
Which statement about the default Cisco Discovery Protocol configuration is true?
A. CDPv1 is disabled on FastEthernet interfaces.
B. CDPv2 advertisements are unicast.
C. CDPv1 is enabled on Frame Relay subinterfaces.
D. CDPv2 advertisements are broadcast.
Answer: D
Question 102
A router is deployed with the default factory settings. If a user on the router mistypes a command, which option is the result?
A. The router immediately returns an error message.
B. The router recognizes the mistake and discards the request.
C. The router autocorrects the mistyped command.
D. The router attempts to resolve the command to an IP address.
E. The router disables DNS lookup.
Answer: D
Explanation
When you mistype a command in privileged mode (Router#), the router thinks you’re trying to Telnet to a remote host so you have to wait with a message like this:
Translating “contin”…domain server (255.255.255.255)
This is because by default the command “ip domain-lookup” is enabled. It enables the Domain Name Server (DNS) lookup feature which performs a DNS lookup on what you entered. If you haven’t configured DNS on the router, the command prompt will hang until the DNS lookup fails. We can cancel the translation with Ctrl + Shift + 6. If we don’t have a real DNS server then we should turn this feature off with the “no ip domain-lookup” command.
Question 103
Which value does RIPv2 use to calculate its route metric?
A. delay
B. bandwidth
C. hop count
D. reliability
Answer: C
Explanation
RIP only uses hop count (the number of routers) to determine the best way to a remote network.
Question 104
Which value is calculated by the sender and receiver of a frame to determine whether the frame has been damaged in transit?
A. the runt value
B. the CRC value
C. the giant value
D. the collision value
Answer: B
Explanation
At the end of each frame there is a Frame Check Sequence (FCS) field. FCS can be analyzed to determine if errors have occurred. FCS uses cyclic redundancy check (CRC) algorithm to detect errors in the transmitted frames. Before sending data, the sending host generates a CRC based on the header and data of that frame. When this frame arrives, the receiving host uses the same algorithm to generate its own CRC and compare them. If they do not match then a CRC error will occur.

Note:
+ Runts are frames which do not meet the minimum frame size of 64 bytes. Runts are usually created by collisions.
+ Giants: frames that are larger than 1,518 bytes
Question 105
What is the default number of secure MAC addresses for an interface configured with port security?
A. 1
B. 255
C. 1042
D. 3072
Answer: A
Question 106
Which device mode must you use to recover a password on a Cisco IOS device?
A. privileged EXEC
B. global configuration
C. user EXEC
D. ROMmon
Answer: D
Explanation
To reset the password we can type “confreg 0x2142” under rommon mode to set the configuration register to 2142 in hexadecimal (the prefix 0x means hexadecimal (base 16)). With this setting when that router reboots, it bypasses the startup-config.
Question 107
Which difference between TCP and UDP is true?
A. Only TCP orders the packets that are transmitted.
B. Only UDP retransmits packets to ensure delivery.
C. Only TCP has eliminated error checking.
D. Only UDP requires recipients to acknowledge packet receipt.
Answer: A
Explanation
UDP header does have a checksum field which provides error detection for this protocol. But the difference (from TCP) is it does not request a retransmit when an error is found, it just simply discards that packet. In short, UDP has error detection while TCP has error recovery mechanism.
Question 108
Which command do you enter to configure a device as an authoritative time server?
A. ntp authenticate
B. ntp server 127.0.0.1
C. ntp source 127.0.0.1
D. ntp master 1
Answer: D
Explanation
An Authoritative NTP Server can distribute time even when it is not synchronized to an existing time server. To configure a Cisco device as an Authoritative NTP Server, use the ntp master [stratum] command.
Question 109
Which two configuration steps will prevent an unauthorized PC from accessing the corporate network? (Choose two)
A. set the port security aging time to 0
B. create the port as a protected port and statically assign the MAC address to the address table
C. configure the switch to discover new MAC addresses after a set time of inactivity
D. enable port security on the switch
E. create the port as an access port and statically assign the MAC address to the address table
Answer: D E
Question 110
Which description refers to administrative distance?
A. the advertised metric to reach a network
B. the cost of a link between two neighboring routers
C. the cost to reach a network that is administratively set
D. a measure of the trustworthiness of a routing information source
Answer: D
Question 111
Which command do you enter on a router running RIP so that it advertises a route on the same interface on which it received the route?
A. no auto-summary
B. no ip split-horizon
C. passive-interface default
D. ip rip v2-broadcast
Answer: B
Explanation
The split-horizon rule states that “a router never sends information about a route back in same direction which is original information came”. This rule is used in distance vector protocol (like RIP or EIGRP) to prevent Layer 3 routing loop. But we can disable the rule with the “no ip split-horizon” command.
Question 112
Which hashing algorithm does NTP use for its authentication keys?
A. MD5
B. AES-256
C. 3DES
D. SHA
Answer: A
Explanation
MD5 keys are used for authentication only, not encryption. The purpose of the keys is to ensure a client it is receiving NTP time stamps from ONLY the intended server.
Question 113
Multicast IP addresses can be grouped into which two address-range assignments? (Choose two)
A. registered
B. dynamic
C. GLOP
D. source-specific multicast
E. private
Answer: A B
Question 114
Which two statements about 802.1Q are true? (Choose two)
A. It is an open-standard trunking protocol
B. It is a Cisco-proprietary trunking protocol
C. It inserts a 4-byte identifying tag in the Ethernet frame after the source MAC address field.
D. It encapsulates the original data frame inside a trunking header.
E. It uses a 20-bit label to identify packets within a trunk.
Answer: A C
Explanation
IEEE 802.1Q uses an internal tagging mechanism which inserts a 4-byte tag field in the original Ethernet frame itself between the Source Address (SA) and Type/Length fields. Because the frame is altered, the trunking device recomputes the FCS on the modified frame.
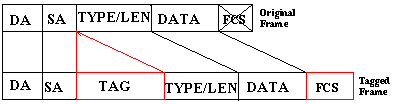
Reference: https://www.cisco.com/c/en/us/support/docs/lan-switching/8021q/17056-741-4.html
Question 115
Which component is part of an Ethernet frame?
A. checksum
B. TTL
C. sequence number
D. frame check sequence
Answer: D
Explanation
An Ethernet frame structure is shown below:

There are no checksum, Time-to-live (TTL) or sequence number in an Ethernet frame.
At the end of each frame there is a Frame Check Sequence (FCS) field. FCS can be analyzed to determine if errors have occurred. FCS uses cyclic redundancy check (CRC) algorithm to detect errors in the transmitted frames. Before sending data, the sending host generates a CRC based on the header and data of that frame. When this frame arrives, the receiving host uses the same algorithm to generate its own CRC and compare them. If they do not match then a CRC error will occur.
Note: In fact in the Ethernet frame structure shown above, the CRC field should be written as FCS field.
Question 116
Which Cisco SDN controller supports existing enterprise network devices?
A. APIC-EM
B. OpenFlow
C. Open SDN
D. ACI
Answer: A
Question 117
Which command can you enter to configure an IPv6 floating static route?
A. router(config)#ipv6 route FE80:0202::/32 serial 0/1 1
B. router (config)#ipv6 route ::/0 serial 0/1
C. router(config)#ipv6 route static resolve default
D. router(config)#ipv6 route FE80.0202::/32serial 0/1 201
Answer: D
Explanation
IPv6 Floating static route is static route with a higher administrative distance than the dynamic routing protocol it is backing up.
Question 118
Which feature can validate address requests and filter out invalid messages?
A. IP Source Guard
B. port security
C. DHCP snooping
D. dynamic ARP inspection
Answer: C
Explanation
DHCP snooping can prevent DHCP spoofing attacks. DHCP snooping is a Cisco Catalyst feature that determines which switch ports can respond to DHCP requests. Ports are identified as trusted and untrusted.
Only ports that connect to an authorized DHCP server are trusted, and allowed to send all types of DHCP messages. All other ports on the switch are untrusted and can send only DHCP requests.
Question 119
Which subnet address is for the IP address 172.19.20.23/28?
A. 172.19.20.20
B. 172.19.20.0
C. 172.19.20.32
D. 172.19.20.15
E. 172.19.20.16
Answer: E
Explanation
Increment: 16 (/28 = 1111 0000 in fourth octet)
Network address: 172.19.20.16
Broadcast address: 172.19.20.31
Question 120
Which two statements are true for multicast MAC address directions? (Choose two)
A. 01:00:5E:AE:17:28
B. one to one
C. 01 00 43 AF5426B
D. 02 46 54BDCF6A8
E. one to many
Answer: A E
Question 121
How many host addresses are available on the network 192.168.1.0 subnet 255.255.255.240? (Choose two)
A. 6
B. 8
C. 14
D. 16
Answer: C
Explanation
240 = 1111 0000 in fourth octet so the formula of host addresses is: the number of host addresses = 2k – 2 (where k is the number of bit 0). In this case k = 4 so the number of host addresses = 24 – 2 = 14.
Question 122
Which two statements about fiber cable are true? (Choose two)
A. Single-mode fiber supports SC and LC connectors only.
B. Multimode cable supports speeds between 100 Mbps and 9.92 Gbps.
C. Single-mode cable is most appropriate for installations longer than 10 km.
D. Fiber cable is relatively inexpensive and supports a higher data rate than coaxial cable.
E. Mulitimode cable supports speeds between 100 Mbps and 100 Gpbs.
Answer: D E
Question 123
After you configure the ip dns spoofing command globally on a device, under which two conditions is DNS spoofing enabled on the device? (Choose two)
A. The ip dns spoofing command is disabled on the local interface
B. The ip host command is disabled
C. All configured IP name server addresses are removed
D. The DNS server queue limit is disabled
E. The no ip domain lookup command is configured
Answer: B C
Explanation
DNS spoofing is designed to allow a router to act as a proxy DNS server and “spoof” replies to any DNS queries using either the configured IP address in the ip dns spoofing ip-address command or the IP address of the incoming interface for the query. This feature is useful for devices where the interface toward the Internet service provider (ISP) is not up. Once the interface to the ISP is up, the router forwards DNS queries to the real DNS servers.This feature turns on DNS spoofing and is functional if any of the following conditions are true:
+ The no ip domain-lookup command is configured.
+ IP name server addresses are not configured.
+ There are no valid interfaces or routes for sending to the configured name server addresses
Question 124
Which statement about unique local IPv6 addresses is true?
A. Summarization is not supported.
B. They require all prefixes to be unique.
C. Their global IDs are assigned sequentially.
D. They are routable to the public Internet.
Answer: B
Explanation
IPv6 Unique Local Address is the approximate IPv6 counterpart of the IPv4 private address. It is not routable on the global Internet but it can be routable inside of a company’s multiple sites. A IPv6 Unique Local Address is an IPv6 address in the block FC00::/7.
Unique Local IPv6 addresses can be viewed as globally unique “private routable” IPv6 addresses, but only inside an organization -> Answer B seems to be correct.
Premium Members: You can practice these questions with our quizzes first at:
+ Question 1 to 20
+ Question 21 to 40
+ Question 41 to 60
+ Question 61 to 80
+ Question 81 to 102
Question 1
Which two statements about the Cisco APIC-EM ACL Path Trace feature are true? (Choose two)
A. Higher-priority ACEs override lower-priority ACEs in the same ACL.
B. The trace analyzes only the egress interface of all devices in the path.
C. The trace analyzes the ingress interface and the egress interface of all devices in the path.
D. The trace analysis stops as soon as the trace encounters a deny entry on the path.
E. The trace analyzes only the ingress interface of all devices in the path.
Answer: A C
Explanation
Access Control List (ACL) Trace analyzes how a flow is affected by ACLs programmed on the path. After the path is calculated between the source and the destination, the ACL Trace analyzes both ingress and egress interfaces of all devices on the path -> C is correct.
Analysis of entries within an individual ACL is cumulative. That is, if a higher priority ACE is a match, lower-priority ACEs are ignored -> A is correct.
Question 2
Which effect of the monitor session 16 source interface gigabitethernet 3/1 command is true?
A. It configures the device to monitor uni-directional source traffic for session 16.
B. It configures the device to monitor uni-directional destination traffic for session 16.
C. It configures the device interface as a source to monitor bi-directional traffic for session 16.
D. It configures the device interface as destination to monitor bi-directional traffic for session 16.
Answer: C
Explanation
Switched Port Analyzer (SPAN) feature copies network traffic from a VLAN or group of ports to a selected port. SPAN is generally referred to as Port mirroring. An example of configuring SPAN port is shown below:
| Switch(config)#monitor session 1 source interface FastEthernet 0/1 Switch(config)#monitor session 1 destination interface FastEthernet 0/2 |
The above configuration will capture all traffic from interface FastEthernet 0/1 and send it to interface FastEthernet 0/2.
By default, both incoming and outgoing traffic is monitored.
Question 3
Which two benefits of using MPLS for WAN access are true? (Choose two)
A. It supports hub-and-spoke connectivity.
B. It supports CoS.
C. It provides VPN support.
D. It provides payload security with ESP.
E. It supports Authentication Header.
Answer: B C
Question 4
Which BGP command do you enter to allow a device to exchange IPv6 prefixes with its neighbor?
A. neighbor ip-address activate
B. neighbor ip-address remote-as ASN
C. router bgp ASN
D. show ip bgp neighbors
Answer: A
Question 5
For which type of connection is broadband PPPoE most appropriate?
A. satellite
B. DSL
C. GRE tunnel
D. PPTP
Answer: B
Explanation
PPPoE is commonly used in a broadband aggregation, such as by digital subscriber line (DSL). PPPoE provides authentication with the CHAP or PAP protocol.
Question 6
While troubleshooting the failure of an OSPFv3 Ethernet connection between routers R1 and R2, you determine that the hello timers are mismatched and that R2 is configured with default settings. Which command do you enter on R1 to correct the problem?
A. R1(config-if)#ipv6 ospf hello-interval 20
B. R1(config-if)#ip ospf hello-interval 10
C. R1(config-if)#ip ospf hello-interval 20
D. R1(config-if)#no ipv6 ospf hello-interval
Answer: D
Explanation
The default hello interval of OSPFv3 is 10 seconds when using Ethernet and 30 seconds when using nonbroadcast. To change the hello interval of OSPFv3, we use the “ipv6 ospf hello-interval seconds” command. Or we can use the “no” form to reset the hello timers to the default values.
Note: Answer B is not correct as it is for IPv4 OSPF, not IPv6 OSPF (should be “ipv6 ospf hello-interval 10, not “ip ospf hello-interval 10”)
Question 7
Which three statements about inform-request options are true? (Choose three)
A. The default number of retries is 3.
B. By default, the maximum number of pending informs is 10.
C. The default timeout is 60 seconds.
D. The default number of retries is 5.
E. The default timeout is 30 seconds.
F. By default, the maximum number of pending informs is 25.
Answer: A E (?) F
Explanation
SNMP inform-request. To specify inform request options, use the snmp-server inform [ pending pending ] [ retries retries ] [ timeout seconds ] command in global configuration mode.
The default value of “retries” is 3.
The default value of “timeout” is 15 seconds -> answer E is not correct but we don’t have any better choice.
The default value of “pending” is 25 (Number of unacknowledged informs to hold).
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/snmp/command/nm-snmp-cr-book/nm-snmp-cr-s5.html
Question 8
Which switch port mode prevents DTP frames from being sent?
A. trunk
B. dynamic auto
C. dynamic desirable
D. nonegotiate
Answer: D
Explanation
Disable DTP with the “switchport nonegotiate” so that DTP messages are not advertised out of the interface is also a good way to prevent auto trunking.
Question 9
Which difference between PVST+ and RPVST+ is true?
A. RPVST+ is based on 802.1D and PVST+ is based on 802.1s.
B. RPVST+ is based on 802.1w and PVST+ is based on 802.1s.
C. RPVST+ has slower convergence than PVST+.
D. Only PVST+ includes Cisco proprietary standards.
Answer: B
Explanation
RPVST+ is the Cisco’s version of RSTP that also uses PVST+ and provides a separate instance of 802.1w per VLAN.
Note: 802.1w is also called Rapid Spanning Tree Protocol (RSTP)
PVST+ is the Cisco proprietary enhancement for STP that provides a separate 802.1d spanning-tree instance for each VLAN.
Question 10
When troubleshooting an issue with an SVI, which three areas do you check? (Choose three)
A. frame size
B. routing
C. interfaces
D. ASIC
E. gateway
F. encapsulation
Answer: B C E
Question 11
Which command do you enter to configure local authentication for PPP on a Cisco device?
A. router(config-if)#ppp authentication chap callin
B. router(config)#username router password password1
C. router(config-if)#ppp authentication chap
D. router(config-if)#ppp chap password password1
Answer: C
Question 12
Which three statements are benefits of using a shadow router as the source of IP SLA measurements? (Choose three)
A. It offsets the resource load from a production router.
B. It can be managed independently of production network traffic.
C. It reduces traffic through existing interfaces by adding another network interface.
D. It provides a better estimation of Layer 2 network traffic.
E. It enables switched traffic to take precedence over local traffic.
F. It adds an NTP synchronization point.
Answer: A B D
Question 13
When a user attempts to authenticate with TACACS+, which three responses from the TACACS+ daemon are possible? (Choose three)
A. PERSIST
B. FAULT
C. CONTINUE
D. ERROR
E. ACCEPT
F. REPEAT
Answer: C D E
Explanation
The network access server will eventually receive one of the following responses from the TACACS+ daemon:
+ ACCEPT – The user is authenticated and service may begin. If the network access server is configured to requite authorization, authorization will begin at this time.
+ REJECT – The user has failed to authenticate. The user may be denied further access, or will be prompted to retry the login sequence depending on the TACACS+ daemon.
+ ERROR – An error occurred at some time during authentication. This can be either at the daemon or in the network connection between the daemon and the network access server. If an ERROR response is received, the network access server will typically try to use an alternative method for authenticating the user.
+ CONTINUE – The user is prompted for additional authentication information.
Question 14
Which three statements about QoS policing are true? (Choose three)
A. It can be applied to outbound traffic only.
B. It avoids queuing delays.
C. It drops excess packets.
D. It can be applied to inbound and outbound traffic.
E. It queues excess traffic.
F. It is configured in bits per second.
Answer: B C D
Explanation
Unlike traffic shaping, QoS policing avoids delays due to queuing.
QoS policing drops (or remarks) excess packets above the committed rates. Does not buffer.
QoS policing is configured in bytes (while QoS traffic shaping is configured in bits per second)
QoS policing can be applied to both inbound and outbound traffic (while QoS shaping can only be applied to outbound traffic)
Question 15
Which three states are the HSRP stages for a router? (Choose three)
A. standby
B. speak
C. secondary
D. listen
E. learn
F. primary
Answer: A B D E (?)
Explanation
HSRP consists of 6 states:
| State | Description |
| Initial | This is the beginning state. It indicates HSRP is not running. It happens when the configuration changes or the interface is first turned on |
| Learn | The router has not determined the virtual IP address and has not yet seen an authenticated hello message from the active router. In this state, the router still waits to hear from the active router. |
| Listen | The router knows both IP and MAC address of the virtual router but it is not the active or standby router. For example, if there are 3 routers in HSRP group, the router which is not in active or standby state will remain in listen state. |
| Speak | The router sends periodic HSRP hellos and participates in the election of the active or standby router. |
| Standby | In this state, the router monitors hellos from the active router and it will take the active state when the current active router fails (no packets heard from active router) |
| Active | The router forwards packets that are sent to the HSRP group. The router also sends periodic hello messages |
Please notice that not all routers in a HSRP group go through all states above. In a HSRP group, only one router reaches active state and one router reaches standby state. Other routers will stop at listen state.
In this question there are four correct answers so maybe in the exam one correct answer would not exists but you should grasp the concept behind it.
Question 16
Which statement about link-state and distance-vector routing protocols is true?
A. Unlike distance-vector routing protocols, link-state routing protocols can cause routing loops.
B. Distance-vector routing protocols converge more quickly than link-state routing protocols.
C. Distance-vector routing protocols use more memory than link-state routing protocols.
D. Unlike distance-vector routing protocols, link-state routing protocols send routing-table updates to neighbors only after adjacency is established.
Answer: D
Question 17
Which three statements about the ACEs that are matched by a Cisco APIC-EM ACL path are true? (Choose three)
A. If the trace fails to find a matching ACE in an ACL, it is reported as implicitly permitted.
B. If an optional criterion is omitted from the trace, the results include all possible ACE matches.
C. If the trace fails to find a matching ACE in an ACL, it is reported as implicitly denied.
D. ACEs are reported only if they match.
E. All ACEs found by the trace are reported, including those that fail to match.
F. If an optional criterion is omitted from the trace, the results are reported as if the default value was specified.
Answer: B C D
Explanation
The following rules effect the ACL path trace results:
+ Only matching access control entry (ACE) are reported.
+ If you leave out the protocol, source port, or destination port when defining a path trace, the results include ACE matches for all possible values for these fields (-> These are optional criterion and if they are omitted, all possible results are included)
+ If no matching ACEs exists in the ACL, the flow is reported to be implicitly denied (-> It is same as an access-list, which always has an implicit “deny all” statement at the end)
Question 18
Which command do you enter to permit IPv6 functionality on an EIGRPv3 interface?
A. Router1(config)#ipv6 unicast-routing
B. Router1(config-if)#ipv6 router eigrp 1
C. Router1(config-if)#ipv6 enable
D. Router1(config-if)#ipv6 eigrp 1
Answer: D
Explanation
An example of configuring EIGRPv3 is shown as below:
| R1(config)#ipv6 router eigrp 1 R1(config-rtr)#router-id 1.1.1.1 R1(config-rtr)#no shutdown R1(config)#interface GigabitEthernet 0/1 R1(config-if)#ipv6 eigrp 1 |
This question asks about “on an EIGRPv3 interface” so it is the only command this is required on an EIGRPv3 interface.
Question 19
Which command do you enter to create an SVI?
A. switch(config)#interface vlan 5
B. switch(config)#interface FastEthernet 0/5
C. switch(config)#interface FastEthernet 0/0.5
D. switch(vlan)#interface svi vlan 5
Answer: A
Question 20
Which command do you enter to protect a PortFast-enabled port against unauthorized switches on the network?
A. switch(config)#spanning-tree portfast bpdufilter default
B. switch(config)#spanning-tree portfast bpduguard default
C. switch(config-if)#spanning-tree guard root
D. switch(config-if)#spanning-tree portfast
Answer: B
Explanation
The BPDU guard feature can be globally enabled on the switch or can be enabled per port, but the feature operates with some differences.
At the global level, you enable BPDU guard on Port Fast-enabled ports by using the spanning-tree portfast bpduguard default global configuration command. Spanning tree shuts down ports that are in a Port Fast-operational state if any BPDU is received on them. In a valid configuration, Port Fast-enabled ports do not receive BPDUs. Receiving a BPDU on a Port Fast-enabled port means an invalid configuration, such as the connection of an unauthorized device, and the BPDU guard feature puts the port in the error-disabled state. When this happens, the switch shuts down the entire port on which the violation occurred.
Question 21
Which VTP operating mode enables a switch to forward VTP information while ignoring synchronization?
A. off
B. server
C. transparent
D. client
Answer: C
Question 22
Which switch architecture is scalable, flexible, resilient, and relatively inexpensive?
A. aggregate switch
B. single switch
C. stacked switch
D. modular-chassis switch
Answer: C
Explanation
Some network switches have the ability to be connected to other switches and operate together as a single unit. These configurations are called stacks, and are useful for quickly increasing the capacity of a network.
Stackable switches can be added or removed from a stack as needed without affecting the overall performance of the stack. Depending on its topology, a stack can continue to transfer data even if a link or unit within the stack fails. This makes stacking an effective, flexible, and scalable solution to expand network capacity.
Question 23
Which technology can prevent client devices from arbitrarily connecting to the network without state remediation?
A. 802.1x
B. IP Source Guard
C. MAC Authentication Bypass
D. 802.11n
Answer: A
Question 24
Which routing protocol is most appropriate for sending and receiving routes directly to and from the Internet?
A. RIP
B. BGP
C. EIGRP
D. OSPF
Answer: B
Question 25
Which command do you enter to configure client authentication for PPPoE?
A. Dev1(config-if)#ppp pap sent-username cisco password password1
B. Dev1(config)#aaa authentication ppp default local
C. Dev1(config-if)#ppp chap password password1
D. Dev1(config)#username cisco password password1
Answer: D
Question 26
Which two factors can affect the price of leased point-to-point WAN links? (Choose two)
A. amount of bandwidth used
B. type of traffic
C. amount of bandwidth requested
D. number of sites interconnected
E. distance between two points
Answer: A E
Question 27
In which LACP channel mode can the port initiate negotiations with other switch ports?
A. auto
B. active
C. desirable
D. passive
Answer: B
Question 28
To troubleshoot a network connection, you execute the ping utility on a route and it returns the response code Q. Which symptom is a probable root cause?
A. The ICMP time was exceed.
B. The destination is unreachable.
C. The connection timed out awaiting the reply.
D. The destination is receiving too much traffic.
Answer: D
Explanation
The table below lists the possible output characters from the ping facility:
| Character | Description |
|---|---|
| ! | Each exclamation point indicates receipt of a reply. |
| . | Each period indicates the network server timed out while waiting for a reply. |
| U | A destination unreachable error PDU was received. |
| Q | Source quench (destination too busy). |
| M | Could not fragment. |
| ? | Unknown packet type. |
| & | Packet lifetime exceeded. |
Question 29
Which two encapsulation types can use the keepalive command to monitor the link state of a WAN serial interface? (Choose two)
A. PPP
B. LMI
C. Frame Relay
D. HDLC
E. LCP
Answer: A D
Explanation
The keepalive command applies to serial interfaces that use High-Level Data Link Contol (HDLC) or PPP encapsulation. It does not apply to serial interfaces that use Frame Relay encapsulation.
For both PPP and HDLC encapsulation types, a keepalive of zero disables keepalives and is reported in the show running-config command output as keepalive disable.
Question 30
Which tool or utility can report whether traffic matching specific criteria can reach a specified destination on the ACLs along the path?
A. Cisco Security Device Manager
B. Cisco Prime
C. APIC-EM
D. Cisco Network Assistant
Answer: C
Explanation
If you performed an ACL trace, the devices show whether the traffic matching your criteria would be permitted or denied based on the ACLs configured on the interfaces.
Question 31
Which type of VPN allows for one endpoint to be learned dynamically during tunnel negotiation?
A. DMVPN
B. site-to-site VPN
C. GRE
D. client VPN
Answer: A
Question 32
Which function is performed by a TACACS+ server?
A. It hosts an access list that permits or denies IP traffic to the control plane of a device.
B. It provides external AAA verification.
C. It filters usernames and passwords for Telnet and SSH.
D. It serves as a database for line passwords.
Answer: B
Question 33
What do SNMPv1 and SNMPv2 have in common?
A. They use the same authentication techniques.
B. They both use the local database to permit username access.
C. They both protect against message tampering in transit.
D. They both encrypt packets.
Answer: A
Explanation
Both SNMPv1 and v2 did not focus much on security and they provide security based on community string only. Community string is really just a clear text password (without encryption). Any data sent in clear text over a network is vulnerable to packet sniffing and interception.
SNMPv3 provides significant enhancements to address the security weaknesses existing in the earlier versions. The concept of community string does not exist in this version. SNMPv3 provides a far more secure communication using entities, users and groups.
Question 34
Which three features are QoS congestion-management tools? (Choose three)
A. PPPoE
B. PQ
C. FIFO
D. PPP
E. PDQ
F. WFQ
Answer: B C F
Explanation
Good reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/qos_conmgt/configuration/xe-3s/qos-conmgt-xe-3s-book/qos-conmgt-oview.html
Question 35
Which two statements about exterior gateway routing protocols are true? (Choose two)
A. BGP is considered to be a path-vector protocol.
B. They can be used to connect to another AS across the Internet as a virtual instance.
C. eBGP is considered to be a distance-vector protocol.
D. EGP is considered to be a path-vector protocol.
E. They can be used to connect to the Internet.
Answer: A E
Question 36
Which two characteristics of a link-state routing protocol are true? (Choose two)
A. It sends periodic updates.
B. It has a higher CPU requirement than distance-vector protocols.
C. It supports a hop-count limit.
D. It receives updates on the multicast address.
E. It receives updates on the broadcast address.
Answer: B D
Question 37
Which statement about OSPFv3 configuration is true?
A. You can add networks under the routing process.
B. You must configure neighbors manually.
C. You must individually add interface IP addresses to the OSPFv3 database.
D. You can enable OSPFv3 for a network under the interface configuration mode.
Answer: D
Question 38
In which three circumstances may your organization require a high-bandwidth Internet connection? (Choose three)
A. It uses cloud computing
B. It uses network devices that require frequent IOS upgrades
C. It uses peer-to-peer file sharing
D. It is undergoing a SAN expansion
E. It uses Infrastructure as a Service
F. It uses resource-intensive applications
Answer: A C E
Question 39
After you notice that the SNMP manager is failing to receive traps, your troubleshooting verifies that the engine ID, username, group name, and host values are
set appropriately. Which configuration item is a probable root cause?
A. Traps are disabled.
B. The snmp-server enable traps command is missing from the configuration.
C. The snmp-server host informs command is missing from the configuration.
D. The host is down.
Answer: B
Question 40
In the Software-Defined Networking model, where is the interface between the control plane and the data plane?
A. between the control layer and the infrastructure layer
B. between the collocated layer and the dislocated layer
C. between the control layer and application layer
D. between the application layer and the infrastructure layer
Answer: A
Question 41
Which command do you enter so that a switch configured with Rapid PVST+ listens and learns for a specific time period?
A. switch(config)#spanning-tree vlan 1 max-age 6
B. switch(config)#spanning-tree vlan 1 hello-time 10
C. switch(config)#spanning-tree vlan 1 priority 4096
D. switch(config)#spanning-tree vlan 1 forward-time 20
Answer: D
Explanation
The forward delay is the time that is spent in the listening and learning state. This time is equal to 15 sec by default, but you can tune the time to be between 4 and 30 sec.
Reference: https://www.cisco.com/c/en/us/support/docs/lan-switching/spanning-tree-protocol/19120-122.html
Question 42
Which three protocols does APIC-EM support with Path Trace? (Choose three)
A. HSRP
B. ECMP
C. WLC
D. SNMP
E. SMTP
F. ECMP/TR
Answer: A B F
Explanation
Path Trace Supported Device Protocols and Network Connections:
Access Control List (ACL)
Border Gateway Protocol (BGP)
Dynamic Multipoint VPN (DMVPN)
Enhanced Interior Gateway Routing Protocol (EIGRP)
Equal Cost Multipath/Trace Route (ECMP/TR)
Equal Cost Multi Path (ECMP)
Hot Standby Router Protocol (HSRP)
Intermediate System-to-Intermediate System (IS-IS) Protocol
…
For more information about these supported protocols and network connections, please visit https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/application-policy-infrastructure-controller-enterprise-module/1-3-x/config-guide/b_apic-em_config_guide_v_1-3-x/b_apic-em_config_guide_v_1-3-x_chapter_0111.html
Question 43
Which step must you perform first to enable OSPFv3 process 20 for IPv6?
A. Enter the ipv6 router ospf 20 command to enable OSPFv3.
B. Enter the ip routing command to enable IPv4 unicast routing.
C. Enter the router ospf 20 commands to enable OSPF.
D. Enter the ipv6 unicast-routing command to enable IPv6 unicast routing.
Answer: D
Question 44
How can you mitigate VLAN hopping attacks?
A. Configure an unused nondefault VLAN as the native VLAN.
B. Enable dynamic ARP inspection.
C. Configure a used nondefault VLAN as the native VLAN.
D. Configure extended VLANs
Answer: A
Explanation
To mitigate VLAN Hopping, the following things should be done:
1) If no trunking is required, configure port as an access port, this also disables trunking on that interface:
Switch(config-if)# switchport mode access
2) If trunking is required, try to configure the port to Nonegotiate to prevent DTP frames from being sent.
Switch(config-if)# switchport mode trunk
Switch(config-if)# switchport nonegotiate
3) Set the native VLAN to an unused VLAN and don’t use this VLAN for any other purpose (-> Therefore answer A is correct)
Switch(config-if)# switchport trunk native vlan VLAN-ID
4) Force the switch to tag the native VLAN on all its 802.1Q trunks:
Switch(config)# vlan dot1q tag native
Question 45
Which two statements about CHAP are true? (Choose two)
A. The CHAP negotiation phase begins after the LCP phase is complete.
B. Each authenticating router has a unique username and password.
C. It uses a three-way handshake to identify the peer router.
D. The local MD5 secret is transmitted to the peer for authentication.
E. The LCP phase begins after CHAP authentication is complete.
Answer: A C
Explanation
After the LCP (Link Control Protocol) phase is complete, and CHAP is negotiated between both devices, the authenticator sends a challenge message to the peer.
Question 46
After you configure multiple point-to-point tunnels on one interface, you notice that the interface is suffering from saturation. Which action do you take to correct the problem?
A. set the tunnel mode
B. set the bandwidth value
C. set the tunnel key argument
D. set the keepalive period
Answer: B
Question 47
Which two traffic types must always be transmitted on VLAN 1? (Choose two)
A. UDP
B. DTP
C. NTP
D. CDP
E. TCP
Answer: B D
Explanation
Control plane traffic (like CDP, VTP, STP…) runs on VLAN 1 by default. We cannot move these protocols to another VLAN.
Question 48
Which command can you enter to display the default VLAN?
A. show interface brief
B. show run
C. show ip interface brief
D. show interface f0/2 switchport
Answer: D
Explanation
An example of the “show interface e0/0 switchport” command is shown below:
Name: Et0/0 Switchport: Enabled Administrative Mode: trunk Operational Mode: trunk Administrative Trunking Encapsulation: dot1q Operational Trunking Encapsulation: dot1q Negotiation of Trunking: On Access Mode VLAN: 100 (VLAN0100) Trunking Native Mode VLAN: 1 (default) Administrative Native VLAN tagging: enabled Voice VLAN: none Administrative private-vlan host-association: none Administrative private-vlan mapping: none Administrative private-vlan trunk native VLAN: none Administrative private-vlan trunk Native VLAN tagging: enabled Administrative private-vlan trunk encapsulation: dot1q Administrative private-vlan trunk normal VLANs: none Administrative private-vlan trunk associations: none Administrative private-vlan trunk mappings: none Operational private-vlan: none Trunking VLANs Enabled: ALL Pruning VLANs Enabled: 2-1001 Capture Mode Disabled Capture VLANs Allowed: ALL Appliance trust: none
This command dispalys the default access mode VLAN & native VLAN.
Question 49
Which STP mode supports spanning-tree interoperability between Cisco and non-Cisco switches?
A. MSTP
B. PVST+
C. PVSTP
D. RSTP
Answer: B
Explanation
PVST: Cisco has a proprietary version of STP that offers more flexibility than the CST version. Per-VLAN Spanning Tree (PVST) operates a separate instance of STP for each individual VLAN. This allows the STP on each VLAN to be configured independently, offering better performance and tuning for specific conditions.
Cisco has a second proprietary version of STP that allows devices to interoperate with both PVST and CST. Per-VLAN Spanning Tree Plus (PVST+) effectively supports three groups of STP operating in the same campus network:
+ Catalyst switches running PVST
+ Catalyst switches running PVST+
+ Switches running CST over 802.1Q
To do this, PVST+ acts as a translator between groups of CST switches and groups of PVST switches. PVST+ can communicate directly with PVST by using ISL trunks. To communicate with CST, however, PVST+ exchanges BPDUs with CST as untagged frames over the native VLAN. BPDUs from other instances of STP (other VLANs) are propagated across the CST portions of the network by tunneling. PVST+ sends these BPDUs by using a unique multicast address so that the CST switches forward them on to downstream neighbors without interpreting them first. Eventually, the tunneled BPDUs reach other PVST+ switches where they are understood.
Reference: CCNP SWITCH Official Certification Guide
In short, PVST+ supports interoperability between CST switches (run on non-Cisco devices) and PVST switches (run on Cisco devices)
Question 50
Where must you configure switch-level global features on a switch stack?
A. on the stack master
B. on the stack master and each individual stack member
C. on the stack master or any individual stack member
D. on each individual stack member
Answer: A
Question 51
Which HSRP feature do you configure so that the device with the highest priority immediately becomes the active router?
A. standby timers
B. preemption
C. standby authentication
D. holdtime
Answer: B
Question 52
Which Cisco IOS feature can you use to dynamically identify a connectivity problem between a Cisco device and a designated endpoint?
A. traceroute
B. ICMP Echo IP SLAs
C. IP SLAs threshold monitoring
D. Multi Operation Scheduler IP SLAs
Answer: B
Question 53
Which command must you enter to prepare an interface to carry voice traffic?
A. Switch1(config-if)#switchport mode access
B. Switch1(config-if)#switchport mode trunk
C. Switch1(config-if)#switchport access vlan 10
D. Switch1(config-if)#switchport host
Answer: B (?)
Explanation
In fact only old switches require a trunk to carry voice traffic. Modern switches can carry voice traffic in access mode.
Question 54
Which command do you enter to verify an SVI?
A. show running-configuration | include vlan5
B. show vlan5
C. show interface vlan5
D. show startup-configuration | include vlan5
Answer: C
Explanation
An SVI is nearly the same as an physical interface (except it is virtual and dedicated for a VLAN) so we can check it with the “show interface <vlan-id>” or “show ip interface <vlan-id>” command.
Question 55
What two options are causes of network slowness that can result from inter-VLAN routing problems? (Choose two)
A. Root guard disabled on an EtherChannel
B. Packet loss
C. DTP disabled on a switchport
D. BPDU guard enabled on a switchport
E. Hardware forwarding issues
Answer: B E
Explanation
Causes for Network Slowness
Packet Loss
In most cases, a network is considered slow when higher-layer protocols (applications) require extended time to complete an operation that typically runs faster. That slowness is caused by the loss of some packets on the network, which causes higher-level protocols like TCP or applications to time out and initiate retransmission.
Hardware Forwarding Issues
With another type of slowness, caused by network equipment, forwarding (whether Layer 2 [L2] or L3) is performed slowly. This is due to a deviation from normal (designed) operation and switching to slow path forwarding. An example of this is when Multilayer Switching (MLS) on the switch forwards L3 packets between VLANs in the hardware, but due to misconfiguration, MLS is not functioning properly and forwarding is done by the router in the software (which drops the interVLAN forwarding rate significantly).
Question 56
Which command do you enter to determine the root priority?
A. Show spanning-tree mapping
B. Show spanning-tree summary
C. Show spanning-tree bpdu-filter 1
D. Show spanning-tree backbonefast
Answer: B (?) in fact there is no correct answer
Explanation
The “show spanning-tree summary” command displays all the features that are enabled for STP (which includes PortFast BPDU Guard, Loop Guard, Root Guard); this command also displays the number of blocked, listening, learning, and forwarding interfaces. But it does not show the root priority. Other answers are not correct either.
Question 57
Which two commands debug a PPPoE connection that has failed to establish? (Choose two)
A. Debug ppp compression
B. Debug ppp negotiation
C. Debug dialer events
D. Debug ppp cbcp
E. Debug dialer packet
Answer: B E
Question 58
Which two commands debug a PPPoE connection that has failed to establish? (Choose two)
A. debug ppp compression
B. debug ppp negotiation
C. debug dialer events
D. debug ppp cbcp
E. debug dialer packet
Answer: B E
Explanation
According to this link https://supportforums.cisco.com/t5/network-infrastructure-documents/troubleshooting-for-pppoe-connection-failure-part-1/ta-p/3147204
The following debug commands can be used to troubleshoot PPPoE connection that failed:
+ debug ppp authentication
+ debug ppp negotiation
+ debug pppoe event
The debug ppp negotiation command enables you to view the PPP negotiation transactions, identify the problem or stage when the error occurs, and develop a resolution.
We are not sure about the “debug dialer packet” command but it seems to be the most reasonable answer left.
Question 59
Which command do you enter to verify that a VLAN has been removed from a trunk?
A. Switch(config-if)# switchport trunk allowed vlan none
B. Switch(config-if)# switchport trunk except vlan 10
C. Switch(config-if)# switchport trunk remove vlan 10
D. Switch(config-if)# no switchport trunk allowed vlan add 10
Answer: B (?)
Explanation
The command “switchport trunk allowed vlan none” remove all allowed VLANs on a trunk while the “switchport trunk except vlan <vlan-id>” will remove only the <vlan-id> out of the allowed VLAN list. But the question asks about verification so it is a bit unclear.
Question 60
Which command do you enter to determine whether LACP is in use on a device?
A. Show etherchannel summary
B. Show port-channel summary
C. Show etherchannel load-balance
D. Show ip protocols
Answer: B
Question 61
Which channel mode is available to static EhterChannels?
A. On
B. Passive
C. Active
D. Desirable
Answer: A
Question 62
Which three commands do you use to verify that IPSec over a GRE tunnel is working properly? (Choose three.)
A. Clear Crypto isakmp
B. PPP encrypt mppe auto
C. Show crypto engine connections active
D. Show crypto ipsec sa
E. Show crypto isakmp sa
F. Debug crypto isakmp
Answer: D E F
Question 63
Which combination of values is valid for a router-on-a-stick implementation?
A. IP address 173.15.20.6/20, gateway 173.15.30.1, and VLAN 20
B. FastEhernet interface 0/0.30, IP address 173.15.20.33/27, gateway 173.15.20.1 and VLAN 30
C. IP address 173.15.30.6/26, gateway 173.15.30.62, and VLAN 20
D. FastEthernet interface 0/0.20, IP address 173.15.30.33/27, gateway 173.15.30.1 and VLAN 30
Answer: C
Explanation
The gateway and the IP address of the subinterface must be in the same subnet -> only answer C is correct.
Question 64
Which two types of cloud services may require you to alter the design of your network infrastructure? (Choose two)
A. Sudo as a Service
B. Platform as a Service
C. Infrastructure as a Service
D. Software as a Service
E. Business as a Service
Answer: B C
Explanation
These different types of cloud computing services delivery models are called infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS).
Question 65
Through which three states does a BGP routing process pass when it establishes a peering session with a neighbor? (Choose three)
A. Open receive
B. Inactive
C. Active
D. Connected
E. Open sent
F. Idle
Answer: C E F
Explanation
BGP forms a TCP session with neighbor routers called peers. The BGP session may report in the following states:
+ Idle
+ Connect
+ Active
+ OpenSent
+ OpenConfirm
+ Established
Reference: http://www.ciscopress.com/articles/article.asp?p=2756480&seqNum=4
Question 66
Which encryption method does CHAP authentication use for the peer response?
A. EAP
B. MD5
C. DES
D. DSS
E. AES
F. 3DES
Answer: B
Question 67
Which two characteristics of stacked switches are true? (Choose two)
A. They reduce management complexity.
B. They are less scalable than modular switches.
C. They can manage multiple IP addresses across multiple switches.
D. They have a single management interface.
E. Each unit in the stack can be assigned its own IP address for administration.
Answer: A D
Question 68
Which option describes a drawback of proxy ARP?
A. It overwrites MAC addresses that were learned with inverse ARP.
B. It can make it more difficult for the administrator to locate device misconfigurations.
C. It dynamically establishes Layer 2 tunneling protocols, which increases network overhead.
D. If proxy ARP is configured on multiple devices, the internal Layer 2 network may become vulnerable to DDoS attacks.
Answer: D
Question 69
Which feature or value must be configured to enable EIGRPv6?
A. Network statement
B. Shutdown feature
C. Router ID
D. Remote AS
Answer: C
Question 70
Which command do you enter to enable local authentication for Multilink PPP on an interface?
A. Router(config-if)# l2tp authentication
B. Router(config)# username router password password1
C. Router(config-if)# ppp chap password password1
D. Router(config)#aaa authentication ppp default local
Answer: B
Question 71
Which options are the two differences between HSRP versions 1 and 2? (Choose two)
A. Only HSRP version 2 can be configured to use authentication.
B. Only HSRP version 2 sends hello packets to 224.0.0.2.
C. Only HSRP version 1 sends hello packets to IPv6 multicast address FF02::66.
D. Only HSRP version 1 can be configured with a group number of 4095.
E. Only HSRP version 2 can be configured with a group number of 4095.
F. Only HSRP version 2 sends hello packets to 224.0.0.102.
Answer: E F
Explanation
In HSRP version 1, group numbers are restricted to the range from 0 to 255. HSRP version 2 expands the group number range from 0 to 4095 -> E is correct.
HSRP version 2 uses the new IP multicast address 224.0.0.102 to send hello packets instead of the multicast address of 224.0.0.2, which is used by version 1 -> F is correct.
Question 72
Which component of an IPv6 OSPFv3 connection must be configured in IPv4 format?
A. Router ID
B. Primary interface
C. Neighbor address
D. Secondary interface
Answer: A
Question 73
Which protocol can be used between administrative domains?
A. IS-IS
B. EIGRP
C. BGP
D. OSPF
Answer: C
Explanation
BGP is an example of an Exterior Gateway Protocol (EGP) which exchanges routing information between different autonomous systems.
BGP is a path vector protocol. Path vector protocol does not rely on the bandwidth of the links (like OSPF) or hop count (like RIP) or a group of parameters (like EIGRP). Path vector protocol relies on the number of autonomous systems it has to go through. In other words, it choose the path with least number of autonomous systems (shortest AS Path) to reach the destination, provided that the path is loop-free.
Question 74
For which reason can a GRE tunnel have an UP/DOWN status?
A. The tunnel source interface is UP.
B. A tunnel destination is undefined.
C. The tunnel destination address is routable via a route that is separate from the tunnel.
D. The tunnel has been shut down.
Answer: B
Explanation
Under normal circumstances, there are only three reasons for a GRE tunnel to be in the up/down state:
– There is no route, which includes the default route, to the tunnel destination address.
– The interface that anchors the tunnel source is down.
– The route to the tunnel destination address is through the tunnel itself, which results in recursion.
Question 75
Which utility do you use to view IP traffic that is switched through the router to locate errors in a TCP stream?
A. Wireshark
B. Packet debugging
C. Ethereal
D. Ping
E. Traceroute
Answer: B
Explanation
Cisco routers provide a basic method of viewing IP traffic switched through the router called packet debugging. Packet debugging enables a user to determine whether traffic is travelling along an expected path in the network or whether there are errors in a particular TCP stream. Although in some cases packet debugging can eliminate the need for a packet analyzer, it should not be considered a replacement for this important tool.
Reference: https://www.cisco.com/en/US/docs/internetworking/troubleshooting/guide/tr1907.html
Question 76
Which command do you enter so that a port enters the forwarding state immediately when a PC is connected to it?
A. Switch(config)# spanning-tree portfast bpduguard default
B. Switch(config)# spanning-tree portfast default
C. Switch(config-if)# spanning-tree portfast trunk
D. Switch(config-if)#no spanning-tree portfast
Answer: B
Explanation
If there is a “spanning-tree portfast” answer then it will surely be a correct answer. If not then answer B is the most suitable one even though the “spanning-tree portfast default” command enables PortFast globally on all non-trunking ports, not a single port.
Question 77
Which information is provided by the output of the show snmp engineID command?
A. Information about remote SNMP engines on the network only.
B. Information about the local SNMP engine and remote SNMP engines that are configured on the device.
C. Information about SNMP users and SNMP groups in the network.
D. Information about the local SNMP engine only.
Answer: B
Explanation
The “show snmp engineID” displays the identification of the local SNMP engine and all remote engines that have been configured on the router. The following example specifies 00000009020000000C025808 as the local engineID and 123456789ABCDEF000000000 as the remote engine ID, 171.69.37.61 as the IP address of the remote engine (copy of SNMP) and 162 as the port from which the remote device is connected to the local device:
Router# show snmp engineID Local SNMP engineID: 00000009020000000C025808 Remote Engine ID IP-addr Port 123456789ABCDEF000000000 171.69.37.61 162
Question 78
Which term represents the minimum bandwidth provided in a Metro Ethernet connection?
A. UNI
B. CIR
C. EVC
D. PIR
Answer: B
Explanation
Committed information rate (CIR): The minimum guaranteed data transfer rate agreed to by the routing device.
Question 79
What is the default value of the Read-Write-All-SNMP community string?
A. Secret
B. Private
C. Public
D. Cisco
Answer: A
Explanation
On Catalyst switches such as the 4000, 5000, and 6000 series that run a regular catalyst Operating System (OS), SNMP is enabled by default with the community strings set to:
+ Read-Only: Public
+ Read-Write: Private
+ Read-Write-all: Secret
With these community strings and the IP address of your switch’s management interface, anyone is able to reconfigure the device. You must change the community strings on the Catalyst switch immediately after you set the device on the network. This is very important.
Reference: https://www.cisco.com/c/en/us/support/docs/ip/simple-network-management-protocol-snmp/7282-12.html
Question 80
Which three effects of using local SPAN are true? (Choose three)
A. It doubles the load on the forwarding engine.
B. It prevents SPAN destinations from using port security.
C. It doubles internal switch traffic.
D. It reduces the supervisor engine workload by half.
E. it reduces the load on the switch fabric.
Answer: A B C
Question 81
Refer to the exhibit.
| switch#configure terminal switch(config)#interface ethernet1/0 switch(config-if)#switchport mode trunk switch(config-if)#switchport mode access switch(config-if)#switchport access vlan 10 |
Which option is the effect of this configuration?
A. It configures the switch port for trunk only.
B. It configures the switch port for voice traffic.
C. It configures the switch port for access and trunk.
D. It configures the switch port for access only.
Answer: D
Explanation
With this configuration, the first switchport command “switchport mode trunk” will be overwritten by the “switchport mode access” command and this port becomes an access port.
Question 82
Which command do you enter to allow a new VLAN across a trunk?
A. Switch(config-if)# switchport trunk except vlan10
B. Switch(config-if)# no switchport trunk remove vlan10
C. Switch(config-if)# switchport trunk allowed vlan add 10
D. Switch(config-if)# switchport trunk allowed vlan10
Answer: C
Explanation
The command “switchport trunk allowed vlan add <vlan-id> adds a new VLAN to the previously allowed VLANs on the trunk. For example suppose our trunk is currently allowing VLANs 1, 4 ,5, 9, 12 then the command “switchport trunk allowed vlan add 10” will allow VLANs 1, 4 ,5, 9, 10, 12 on the trunk.
Question 83
Which feature can prevent a rogue device from assuming the role of the root bridge in a switching domain?
A. VTP
B. BPDU Filter
C. DTP
D. Root Guard
Answer: D
Explanation
Root Guard ensures that the port on which root guard is enabled is the designated port. If the bridge receives superior BPDUs on a root guard-enabled port, root guard moves this port to a root-inconsistent STP state (which is equal to STP listening state). No traffic is forwarded across this port. In this way, the root guard enforces the position of the root bridge.
Question 84
Which configuration do you apply to an HSRP router so that it is most likely to come up if the active router goes down?
A. Standby 4 preempt
B. Standby 4 priority 110 preempt delay 300
C. Standby 4 priority 115
D. Standby 4 priority 145
Answer: A
Question 85
In which two models can control-plane functionality be implemented? (Choose two)
A. Dispersed
B. Distributed
C. Fragmented
D. Centralized
E. Allocated
Answer: B D
Explanation
In its simplest form, the control plane provides layer-2 MAC reachability and layer-3 routing information to network devices that require this information to make packet forwarding decisions. In the case of firewalls, the control plane would include stateful flow information for inspection. Control plane functionality can implemented as follows:
+ Distributed – Conventional routers and switches operate using distributed protocols for control, i.e. where each device makes its own decisions about what to do, and communicate relevant information to other devices for input into their decision making process. For example, the Spanning Tree Protocol (STP), Fabric Path, and routing protocols such as IS-IS and BGP provide distributed control of packet forwarding functionality to networking devices.
+ Centralized – In this case, a centralized controller provides the necessary information for a network element to make a decision. For example, these controller(s) instruct networking devices on where to forward packets by explicitly programming their MAC and FIBs.
Reference: https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Data_Center/VMDC/SDN/SDN.html
Question 86
Which type of IPv6 ACL is applied first in the order of precedence?
A. TCAM
B. router ACLs
C. Fragmented frames
D. Port ACLs
Answer: D
Explanation
As with IPv4 ACLs, IPv6 port ACLs take precedence over router ACLs:
+ When an input router ACL and input port ACL exist in an SVI, packets received on ports to which a port ACL is applied are filtered by the port ACL. Routed IP packets received on other ports are filtered by the router ACL. Other packets are not filtered.
+ When an output router ACL and input port ACL exist in an SVI, packets received on the ports to which a port ACL is applied are filtered by the port ACL. Outgoing routed IPv6 packets are filtered by the router ACL. Other packets are not filtered.
Question 87
Which three fields can be marked with QoS? (Choose three)
A. Header checksum
B. IP precedence
C. DSCP
D. Total length
E. Discard Class
F. TTL
Answer: B C E
Explanation
For a single class, you can set operations on any two out of the following five fields: CoS, IP Precedence, DSCP, QoS Group, and Discard Class.
Question 88
Drag and drop the CSMA components from the left onto the correct descriptions on the right
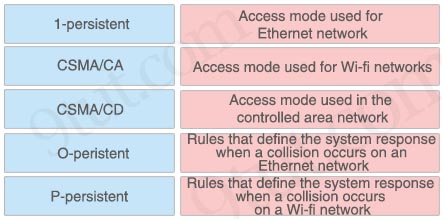
Answer:
+ 1-persistent: Access mode used for Ethernet network
+ CSMA/CA: Rules that define the system response when a collision occurs on a Wi-fi network
+ CSMA/CD: Rules that define the system response when a collision occurs on an Ethernet network
+ O-peristent: Access mode used in the controlled area network
+ P-persistent: Access mode used for Wi-fi networks
Explanation
1-persistent CSMA is an aggressive transmission algorithm. When the transmitting node is ready to transmit, it senses the transmission medium for idle or busy. If idle, then it transmits immediately. If busy, then it senses the transmission medium continuously until it becomes idle, then transmits the message (a frame) unconditionally (i.e. with probability=1). In case of a collision, the sender waits for a random period of time and attempts the same procedure again. 1-persistent CSMA is used in CSMA/CD systems including Ethernet.
Non persistent CSMA is a non aggressive transmission algorithm. When the transmitting node is ready to transmit data, it senses the transmission medium for idle or busy. If idle, then it transmits immediately. If busy, then it waits for a random period of time (during which it does not sense the transmission medium) before repeating the whole logic cycle (which started with sensing the transmission medium for idle or busy) again. This approach reduces collision, results in overall higher medium throughput but with a penalty of longer initial delay compared to 1–persistent.
P-persistent is an approach between 1-persistent and non-persistent CSMA access modes. [1]When the transmitting node is ready to transmit data, it senses the transmission medium for idle or busy. If idle, then it transmits immediately. If busy, then it senses the transmission medium continuously until it becomes idle, then transmits with probability p. If the node does not transmit (the probability of this event is 1-p), it waits until the next available time slot. If the transmission medium is not busy, it transmits again with the same probability p. This probabilistic hold-off repeats until the frame is finally transmitted or when the medium is found to become busy again (i.e. some other node has already started transmitting). In the latter case the node repeats the whole logic cycle (which started with sensing the transmission medium for idle or busy) again. p-persistent CSMA is used in CSMA/CA systems including Wi-Fi and other packet radio systems.
O-persistent
Each node is assigned a transmission order by a supervisory node. When the transmission medium goes idle, nodes wait for their time slot in accordance with their assigned transmission order. The node assigned to transmit first transmits immediately. The node assigned to transmit second waits one time slot (but by that time the first node has already started transmitting). Nodes monitor the medium for transmissions from other nodes and update their assigned order with each detected transmission (i.e. they move one position closer to the front of the queue).[2] O-persistent CSMA is used by CobraNet, LonWorks and the controller area network.
Reference: https://en.wikipedia.org/wiki/Carrier-sense_multiple_access
Question 89
Drag and drop the PPPoE message types from the left into the sequence in which PPPoE messages are sent on the right.
| PADR | 1 |
| PADS | 2 |
| PADI | 3 |
| PADO | 4 |
Answer:
1. PADI
2. PADO
3. PADR
4. PADS
Question 90
Drag drop about characteristics of a cloud environment.
Answer:
+ Multitenancy: One or more clients can be hosted with the same physical or virtual infrastructure
+ Scalability: Resources can be added and removed as needed to support current workload and tasks
+ Workload movement: Tasks can be migrated to different physical locations to increase efficiency or reduce cost
+ On-demand: Resources are dedicated only when necessary instead of on a permanent basis
+ Resiliency: Tasks and data residing on a failed server can be seamlessly migrated to other physical resources
Question 91
Drag and drop the network programmability features from the left onto the correct description on the right.
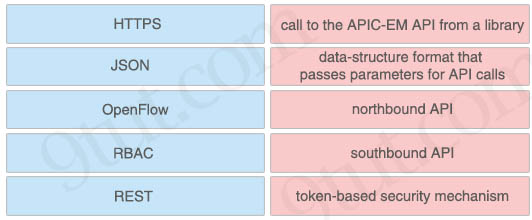
Answer:
+ HTTPS: call to the APIC-EM API from a library
+ JSON: data-structure format that passes parameters for API calls
+ OpenFlow: southbound API
+ RBAC: token-based security mechanism
+ REST: northbound API
Explanation
What is the data format used to send/receive data when making REST calls for APIC-EM?
Javascript Object Notation (JSON) is used to pass parameters when making API calls and is also the returned data format.
What’s RBAC?
The Role-Based Access Controls (RBAC) mechanism utilizes security tokens that the controller issues upon successful authentication of a user of the APIC-EM controller. All subsequent requests from the authenticated user must provide a valid token.
Reference: https://communities.cisco.com/docs/DOC-60530#q16
Question 92
Drag and drop the descriptions of performing an initial device configuration from the left onto the correct features or components on the right.
Answer:
+ feature that allows remote access to the console: VTY line
+ feature that confirms a user is permitted to access the device: password
+ value that enables routing when the device is unable to locate a specific route on the routing table: default gateway
+ value that uniquely identifies the device: hostname
+ encrypted value that is used to confirm a user is permitted to access the device: enable secret password
Question 93
Drag and drop the BGP components from the left onto the correct descriptions on the right.
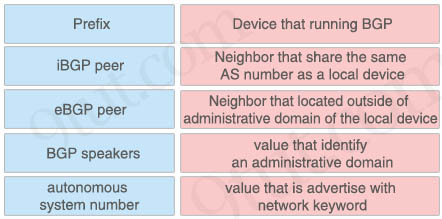
Answer:
+ autonomous system number: Value that identifies an administrative domain
+ BGP Speaker: device that is running BGP
+ eBGP: Peer neighbor that located outside of administrative domain of the local device
+ BGP Peer: neighbor device that shares the same AS number as the local device
+ Prefix: value that is advertised with the network keyword
Question 94
Which two QoS tools can provide congestion management? (Choose two)
A. CBWFQ
B. FRTS
C. CAR
D. PQ
E. PBR
Answer: A D
Explanation
This module discusses the types of queueing and queueing-related features (such as bandwidth management) which constitute the congestion management QoS features:
Class-based WFQ (CBWFQ): extends the standard WFQ functionality to provide support for user-defined traffic classes. For CBWFQ, you define traffic classes based on match criteria including protocols, access control lists (ACLs), and input interfaces. Packets satisfying the match criteria for a class constitute the traffic for that class.
Priority queueing (PQ): With PQ, packets belonging to one priority class of traffic are sent before all lower priority traffic to ensure timely delivery of those packets.
Note: Committed Access Rate (CAR) is only used for bandwidth limitation by dropping excessive traffic.
Question 95
Which two statements about EIGRP on IPv6 device are true? (Choose two)
A. It is configured on the interface
B. It is globally configured
C. It is configured using a network statement
D. It is vendor agnostic
E. It supports a shutdown feature
Answer: A E
Explanation
This is an example of how to configure EIGRP for IPv6:
| interface Serial0/0 no ip address ipv6 address FE80::1 link-local ipv6 address 2010:AB8::1/64 ipv6 enable ipv6 eigrp 1 ! ipv6 router eigrp 1 eigrp router-id 2.2.2.2 no shutdown |
As you can see, EIGRP for IPv6 can only be enabled under each interface -> A is correct.
Under EIGRP process there is a shutdown feature where you can turn on or off -> E is correct.
Question 96
In which STP state does MAC address learning take place on a PortFast-enabled port?
A. learning
B. listening
C. discarding
D. forwarding
Answer: D
Explanation
PortFast-enabled port will ignore listening and learning state and jump to forwarding state immediately so it can only learn MAC addresses in this state.
Question 97
Which protocols does the internet layer in the tcp/ip model encapsulation? (Choose two)
A. smtp
B. tcp
C. arp
D. dns
E. icmp
F. udp
Answer: C E
Question 98
You notice that the packets that are sent from a local host to well-know service tcp port 80 of a remote host are sometimes lost you suspect an ACL issue. Which two APIC-EM path trace ACL-analysis options should you use to troubleshoot the problem? (Choose two)
A. protocol
B. debug
C. destination port
D. QoS
E. Performance monitor
Answer: A C
Question 99
Which IOS troubleshooting tool should yo use to direct system messages to your screen?
A. Local SPAN
B. Terminal monitor
C. APIC-EM
D. Log events
Answer: B
Question 100
In CDP environment what happens when the cdp interface on an adjacent device is configured without an IP address?
A. CDP becomes inoperable on that neighbor
B. CDP operates normally but it can cannot provide any information for that neighbor
C. CDP uses the ip address of another interface for that neighbor
D. CDP operates normally but it cannot provide ip address information for that neighbor
Answer: D
Question 101
Which two pieces of information about a Cisco device can Cisco Discovery Protocol communicate? (Choose two)
A. The native VLAN
B. The spanning tree protocol
C. The trunking protocol
D. The spanning tree priority
E. The VTP domain
Answer: A E
Explanation
The information contained in Cisco Discovery Protocol advertisements varies based on the type of device and the installed version of the operating system. Some of the information that Cisco Discovery Protocol can learn includes:
+ Cisco IOS version running on Cisco devices
+ Hardware platform of devices
+ IP addresses of interfaces on devices
+ Locally connected devices advertising Cisco Discovery Protocol
+ Interfaces active on Cisco devices, including encapsulation type
+ Hostname
+ Duplex setting
+ VLAN Trunking Protocol (VTP) domain
+ Native VLAN
Question 102
Drag drop about Administrative Distances of EIGRP and BGP.
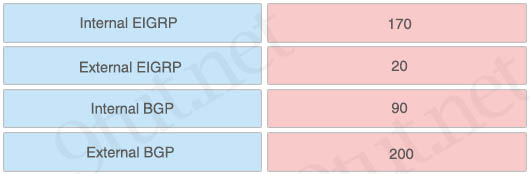
Answer:
+ Internal EIGRP – 90
+ External EIGRP – 170
+ Internal BGP – 200
+ External BGP – 20
Premium Members: You can practice these questions with our quizzes first at:
+ Question 1 to 10
+ Question 11 to 26
+ Question 27 to 50
+ Question 51 to 70
+ Question 71 to 90
+ Question 91 to 100
Question 1
Drag and drop the SPAN terms from the left onto the correct description on the right.
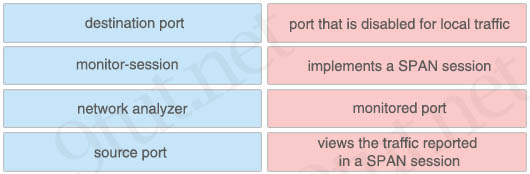
Answer:
+ port that is disabled for local traffic: destination port
+ implements a SPAN session: monitor-session
+ monitored port: source port
+ views the traffic reported in a SPAN session: network analyzer
Question 2
Drag and drop the descriptions of ACLs from the left onto the correct ACL types on the right.
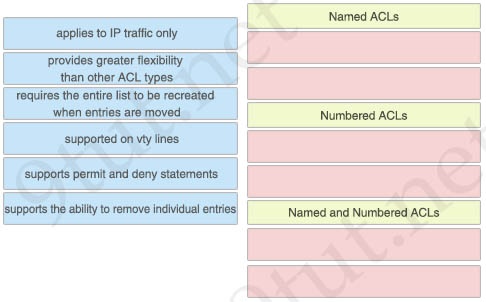
Answer:
Named ACLs:
+ supports the ability to remove individual entries
+ provides greater flexibility than other ACL types
Numbered ACLs:
+ requires the entire list to be recreated when entries are moved
+ supported on vty lines
Named and Numbered ACLs:
+ supports permit and deny statements
+ applies to IP traffic only
Explanation
When you apply an access list to a vty (by using the access-class command), the access list must be a numbered access list, not a named access list.
With named ACL, we can easily remove an individual entry. For example:
R1# show access-list
Standard IP access list nat_traffic
10 permit 10.1.0.0, wildcard bits 0.0.255.255
20 permit 10.2.0.0, wildcard bits 0.0.255.255
30 permit 10.3.0.0, wildcard bits 0.0.255.255
Then to remove the second statement (the line “20 permit 10.2.0.0, wildcard bits 0.0.255.255”) we just need to type “no 20”:
R1(config)#ip access-list standard nat_traffic
R1(config-std-nacl)#no 20
Question 3
Drag and drop the terms associated with a hub-and-spoke topology from the left onto the correct descriptions on the right.
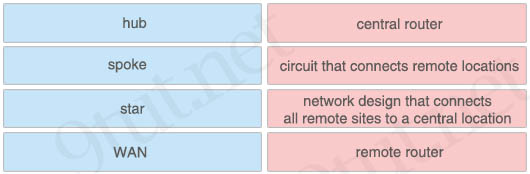
Answer:
+ central router: hub
+ circuit that connects remote locations: WAN
+ network design that connects all remote sites to a central location: star
+ remote router: spoke
Question 4
Drag and drop the routing protocols from the left onto the correct routing protocol types on the right.
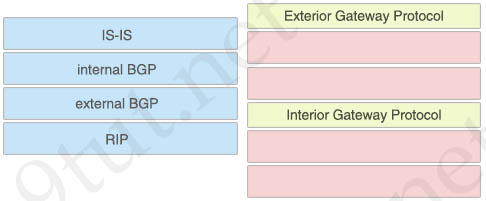
Answer:
Exterior Gateway Protocol:
+ internal BGP
+ external BGP
Interior Gateway Protocol:
+ IS-IS
+ RIP
Question 5
Drag and drop the descriptions of traffic shaping and policing from the left onto the correct categories on the right.
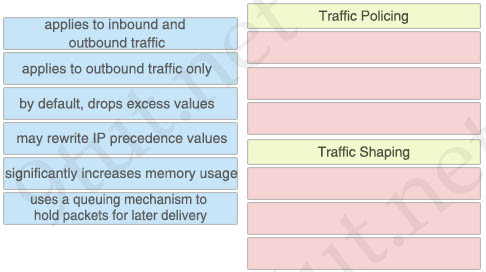
Answer:
Traffic Policing:
+ applies to inbound and outbound traffic
+ by default, drops excess values
+ may rewrite IP precedence values
Traffic Shaping:
+ applies to outbound traffic only
+ uses a queuing mechanism to hold packets for later delivery
+ significantly increases memory usage
Explanation
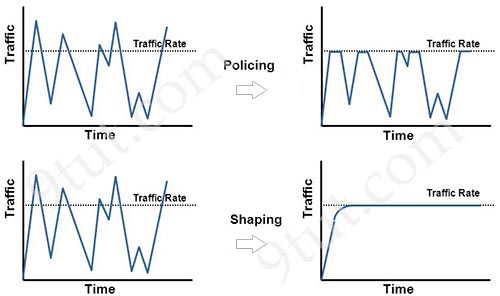
Traffic policing propagates bursts. When the traffic rate reaches the configured maximum rate, excess traffic is dropped (or remarked). The result is an output rate that appears as a saw-tooth with crests and troughs. In contrast to policing, traffic shaping retains excess packets in a queue and then schedules the excess for later transmission over increments of time. The result of traffic shaping is a smoothed packet output rate.
Shaping implies the existence of a queue and of sufficient memory to buffer delayed packets, while policing does not. Queueing is an outbound concept; packets going out an interface get queued and can be shaped. Only policing can be applied to inbound traffic on an interface.
With policing, the token bucket determines whether a packet exceeds or conforms to the applied rate. In either case, policing implements a configurable action, which includes setting the IP precedence or Differentiated Services Code Point (DSCP).
Question 6
Two EIGRP routers have failed to establish a neighbor relationship. Drag and drop the configuration parameters from the left onto the categories on the right.
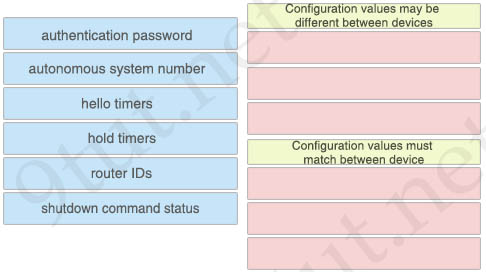
Answer:
Configuration values may be different between devices:
+ hello timers
+ hold timers
+ router IDs
Configuration values must match between device:
+ authentication password
+ autonomous system number
+ shutdown command status
Question 7
Drag and drop the steps in the process of establishing an OSPFv3 neighbor relationship from the left onto the correct sequence on the right.
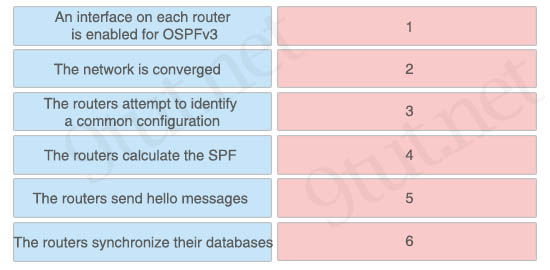
Answer:
1: An interface on each router is enabled for OSPFv3
2: The routers send hello messages
3: The routers attempt to identify a common configuration
4: The routers calculate the SPF
5: The routers synchronize their databases
6: The network is converged
Explanation
An OSPFv3 router sends a special message, called a hello packet, out each OSPF-enabled interface to discover other OSPFv3 neighbor routers. Once a neighbor is discovered, the two routers compare information in the Hello packet to determine if the routers have compatible configurations. The neighbor routers attempt to establish adjacency, which means that the routers synchronize their link-state databases to ensure that they have identical OSPFv3 routing information. Adjacent routers share link-state advertisements (LSAs) that include information about the operational state of each link, the cost of the link, and any other neighbor information. The routers then flood these received LSAs out every OSPF-enabled interface so that all OSPFv3 routers eventually have identical link-state databases. When all OSPFv3 routers have identical link-state databases, the network is converged
Question 8
Drag and drop the EIGRP K values from the left onto the correct metric components on the right.
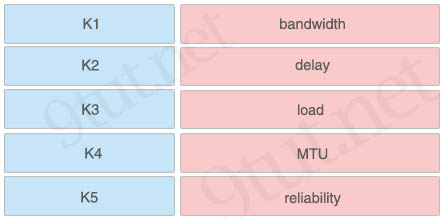
Answer:
K1 – bandwidth
K2 – load
K3 – delay
K4 – Reliability
K5 – MTU
Question 9
You recently configured your enterprise network to use resources in a public cloud. Drag and drop the steps in the end-user process to access the cloud resources from the left onto the correct sequence on the right. Not all steps are used.
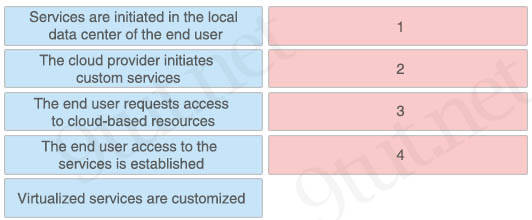
Answer:
1: The end user requests access to cloud-based resources
2: The cloud provider initiates custom services
3: Virtualized services are customized
4: The end user access to the services is established
Question 10
Drag and drop the descriptions if EtherChannel protocols from the left onto the correct protocols on the right.
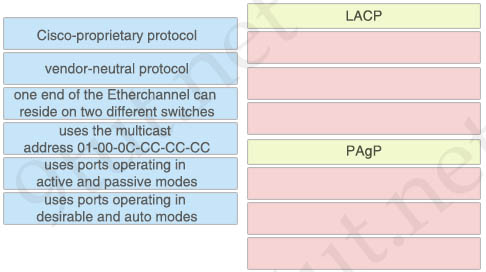
Answer:
LACP:
+ vendor-neutral protocol
+ one end of the Etherchannel can reside on two different switches
+ uses ports operating in active and passive modes
PAgP:
+ Cisco-proprietary protocol
+ uses the multicast address 01-00-0C-CC-CC-CC
+ uses ports operating in desirable and auto modes
Question 11
You are troubleshooting a variety of Layer 3 connectivity issues on your network. Drag and drop the issues from the left onto the location where you will start troubleshooting the issue on the right.
Answer:
ARP Table:
+ missing ARP entry
Interface:
+ misconfigured IP address
+ misconfigured subnet mask
Routing Table:
+ misconfigured gateway
+ missing route
Question 12
Drag and drop the BGP peering states from the left onto the correct statements on the right.
Answer:
+ Routing between the two devices begins: established
+ The local device receives a reply acknowledging BGP parameters from the remote device: open confirm
+ The local device searches for a route to the remote device: idle
+ The local device sends BGP parameters to the remote device: active
+ The two devices perform a TCP handshake: connect
Explanation
Below is the list of BGP states in order, from startup to peering:
1 – Idle: the initial state of a BGP connection. In this state, the BGP speaker is waiting for a BGP start event, generally either the establishment of a TCP connection or the re-establishment of a previous connection. Once the connection is established, BGP moves to the next state.
2 – Connect: In this state, BGP is waiting for the TCP connection to be formed. If the TCP connection completes, BGP will move to the OpenSent stage; if the connection cannot complete, BGP goes to Active
3 – Active: In the Active state, the BGP speaker is attempting to initiate a TCP session with the BGP speaker it wants to peer with. If this can be done, the BGP state goes to OpenSent state.
4 – OpenSent: the BGP speaker is waiting to receive an OPEN message from the remote BGP speaker
5 – OpenConfirm: Once the BGP speaker receives the OPEN message and no error is detected, the BGP speaker sends a KEEPALIVE message to the remote BGP speaker
6 – Established: All of the neighbor negotiations are complete. You will see a number, which tells us the number of prefixes the router has received from a neighbor or peer group.
Question 13
Drag and drop the components of an inter-switch connection from the left onto the correct descriptions in the right.
Answer:
+ Cisco-proprietary trunking protocol: ISL
+ link that can be traversed by multiple VLANs: trunk
+ vendor-neutral trunking protocol: 802. 1Q
+ default VLAN on a switch: native VLAN
+ VLAN identification information associated with a packet: tag
Question 14
Drag and drop the STP features from the left onto the correct descriptions on the right.
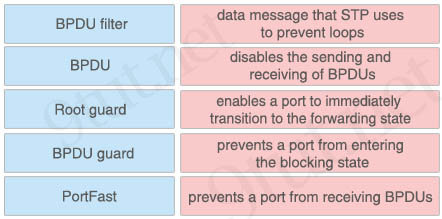
Answer:
+ data message that STP uses to prevent loops: BPDU
+ disables the sending and receiving of BPDUs: BPDU filter
+ enables a port to immediately transition to the forwarding state: PortFast
+ prevents a port from entering the blocking state: Root guard
+ prevents a port from receiving BPDUs: BPDU guard
Explanation
If a BPDU is received on a port where BPDU guard is configured, that port is put into errdisable state (nearly the same as shutdown state) immediately.
Root Guard ensures that the port on which root guard is enabled is the designated port. If the bridge receives superior BPDUs on a root guard-enabled port, root guard moves this port to a root-inconsistent STP state (which is equal to STP listening state). No traffic is forwarded across this port. In this way, the root guard enforces the position of the root bridge.
When BPDU filtering is enabled on a specific port, it prevents this port from sending or receiving BPDUs (so if BPDUs are seen, they will be dropped)
Question 15
Drag and drop the cloud-based resources from the left onto the correct definitions on the right.
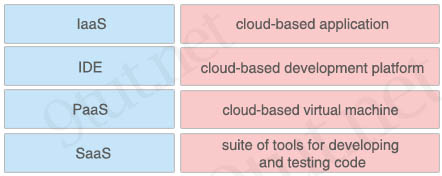
Answer:
cloud-based application: SaaS
cloud-based development platform: PaaS
cloud-based virtual machine: IaaS
suite of tools for developing and testing code: IDE
Explanation
Below are the 3 cloud supporting services cloud providers provide to customer:
+ SaaS (Software as a Service): SaaS uses the web to deliver applications that are managed by a third-party vendor and whose interface is accessed on the clients’ side. Most SaaS applications can be run directly from a web browser without any downloads or installations required, although some require plugins.
+ PaaS (Platform as a Service): are used for applications, and other development, while providing cloud components to software. What developers gain with PaaS is a framework they can build upon to develop or customize applications. PaaS makes the development, testing, and deployment of applications quick, simple, and cost-effective. With this technology, enterprise operations, or a third-party provider, can manage OSes, virtualization, servers, storage, networking, and the PaaS software itself. Developers, however, manage the applications.
+ IaaS (Infrastructure as a Service): self-service models for accessing, monitoring, and managing remote datacenter infrastructures, such as compute (virtualized or bare metal), storage, networking, and networking services (e.g. firewalls). Instead of having to purchase hardware outright, users can purchase IaaS based on consumption, similar to electricity or other utility billing.
Reference: https://apprenda.com/library/paas/iaas-paas-saas-explained-compared/
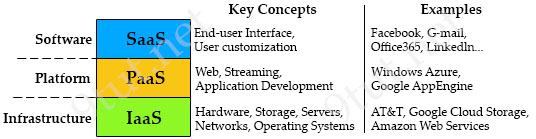
Question 16
Drag and drop the features of an Ethernet interface from the left onto the correct statements on the right.
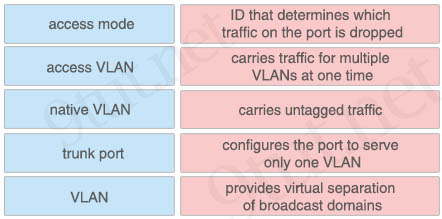
Answer:
ID that determines which traffic on the port is dropped: access VLAN
carries traffic for multiple VLANs at one time: trunk port
carries untagged traffic: native VLAN
configures the port to serve only one VLAN: access mode
provides virtual separation of broadcast domains: VLAN
Question 17
Drag and drop the descriptions of AAA device-security protocols from the left onto the correct protocols on the right.
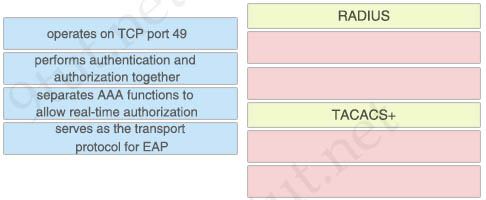
Answer:
RADIUS:
+ performs authentication and authorization together
+ serves as the transport protocol for EAP
TACACS+:
+ operates on TCP port 49
+ separates AAA functions to allow real-time authorization
Explanation
The comparison of two protocols is listed below:
| RADIUS | TACACS+ | |
| Transportation & Ports |
UDP port 1812/1645 (Authentication) 1813/1646 (Accounting) |
TCP port 49 |
| Encryption | only passwords | entire payload of each packet (leaving only the TACACS+ header in cleartext) |
| Standards | Open standard | Cisco proprietary (but actually now it is an open standard defined by RFC1492) |
| Operation | Authentication and authorization are combined in one function | authentication, authorization and accounting are separated |
| Logging | No command logging | Full command logging (commands typed by users can be recorded on the servers) |
Note: In fact both RADIUS and TACACS+ support Extensible Authentication Protocol (EAP), which is an authentication framework frequently used in wireless networks and point-to-point connections
Question 18
Which two steps must occur before two routers can become BGP peers? (Choose two)
A. The routers must establish a TCP connection to one another
B. The routers must exchange BGP version information
C. The routers must receive multicast hello packets from one another
D. The routers must receive more than one BGP routing update from one another
E. Each router must reset its BGP timers to their default settings
Answer: A B
Explanation
In order to become BGP peers, the two routers must establish a TCP connection (via a three-way TCP handshake) in the “Connect” state.
In the OpenSent state, an Open message has been sent from the originating router and is awaiting an Open message from the other router. After the originating router receives the OPEN message from the other router, both OPEN messages are checked for errors. The following items are being compared:
+ BGP Versions must match.
+ The source IP address of the OPEN message must match the IP address that is configured for the neighbor.
+ The AS number in the OPEN message must match what is configured for the neighbor.
+ BGP Identifiers (RID) must be unique. If a RID does not exist, this condition is not met.
+ Security Parameters (Password, TTL, and the like).
Reference: http://www.ciscopress.com/articles/article.asp?p=2756480&seqNum=4
Question 19
Which two actions must you take to configure a static EtherChannel between two switches, S1 and S2? (Choose two)
A. Configure the channel-group 1 mode auto command on S2
B. Configure the channel-group 1 mode active command on S2
C. Configure the channel-group 1 mode on command on S1
D. Configure the channel-group 1 mode active command on S1
E. Configure the channel-group 1 mode on command on S2
F. Configure the channel-group 1 mode auto command on S1
Answer: C E
Explanation
To configure a static EtherChannel (not LACP or PAgP mode), the only way we can configure is to configure mode “on” on both ends.
Question 20
Which QoS prioritization method is most appropriate for interactive voice and video?
A. policing
B. low-latency queuing
C. round-robin scheduling
D. expedited forwarding
Answer: D
Explanation
There are three standard service classes defined for DiffServ: the default Best-Effort (BE), Expedited Forwarding (EF) and Assured Forwarding (AF).
EF minimizes delay, jitter and loss, hence making it suitable for real-time services e.g. interactive voice, video etc.
Reference: Next Generation Mobile Networks and Ubiquitous Computing Book
Note: Interactive Video has the same service level requirements as VoIP because a voice call is embedded within the video stream.
Question 21
Which port type is used in a stacked deployment?
A. StackWise ports
B. uplinks
C. Ethernet ports
D. console ports
Answer: A
Explanation
A stack port is a port on the switch that is used to communicate with other switches in the stack. Depending on the model, a switch can have either preconfigured or user-defined stack ports.
Question 22
What is the effect of the switchport access vlan 300 command?
A. It configures the interface to perform Layer 2 switching
B. It displays the VLAN configuration of the interface
C. It configures the interface as an access port
D. It assigns the interface to a VLAN
Answer: D
Explanation
The example below configures a port on a switch to access mode and assign VLAN 300 to it:
Switch(config)#interface fa0/1
Switch(config-if)#switchport mode access
Switch(config-if)#switchport access vlan 300
Switch(config-if)#no shutdown
Question 23
Which two statements about access ports are true? (Choose two)
A. VLANs must be in the VLAN database before they can be assigned to an access port
B. They are configured with 802.1Q encapsulation
C. A device must have at least one access port configured for each trunk port
D. They are assigned to VLAN 1 by default
E. They record all MAC addresses they receive
Answer: A D
Explanation
Answer A is correct but in practical we can assign an access port to a non-existent VLAN because the switch will create it automatically before assign this access port to this VLAN.
By default all access ports belong to VLAN 1. If we want to assign a new VLAN, we have to use the command “switchport access vlan <vlan-id>” under interface mode.
Question 24
Which programming language do you use to script interactions between Cisco devices and network controllers such as APIC-EM?
A. POSIX
B. Python
C. Java
D. C++
Answer: B
Question 25
Which two functions are performed by DHCP snooping? (Choose two)
A. It determines which DHCP messages are valid
B. It hands out DHCP IP addresses to clients requesting access to the network
C. It rate-limits certain traffic
D. It listens to multicast traffic to support packet forwarding
E. It propagates VLAN information between switches
F. It provides DDoS mitigation
Answer: A C
Explanation
DHCP snooping is a security feature that acts like a firewall between untrusted hosts and trusted DHCP servers. The DHCP snooping feature performs the following activities:
+ Validates DHCP messages received from untrusted sources and filters out invalid messages.
+ Rate-limits DHCP traffic from trusted and untrusted sources.
+ Builds and maintains the DHCP snooping binding database, which contains information about untrusted hosts with leased IP addresses.
+ Utilizes the DHCP snooping binding database to validate subsequent requests from untrusted hosts.
Reference: https://www.cisco.com/en/US/docs/general/Test/dwerblo/broken_guide/snoodhcp.html
Question 26
For which two reasons do you implement a PAgP EtherChannel? (Choose two)
A. to dynamically assign VLANs to a trunk port
B. to increase bandwidth
C. to provide redundancy
D. to exchange VLAN information
E. to dynamically determine whether a port is an access port or trunk port
Answer: B C
Question 27
Which three components must you configure to establish a GRE tunnel? (Choose three)
A. BGP autonomous system number
B. authentication mode
C. tunnel destination IP address
D. IGP type at each site
E. tunnel source IP address
F. logical tunnel interface
Answer: C E F
Explanation
The below example shows how to configure a GRE tunnel at one end:
| R1 interface tunnel0 ip address 12.12.12.1 255.255.255.252 tunnel mode gre ip //this command can be ignored tunnel source 192.168.13.1 tunnel destination 192.168.23.2 |
Question 28
Which two statements about CHAP authentication are true? (Choose two)
A. The called router sends a challenge packet to the calling router
B. It is by definition a one-way authentication method
C. PPP authentication is performed after the CHAP process is complete
D. CHAP authentication can only be used in one direction
E. By default, the calling router authenticates the called router
F. It is by definition a two-way authentication method
Answer: A B
Explanation
CHAP is defined as a one-way authentication method. However, you use CHAP in both directions to create a two-way authentication. Hence, with two-way CHAP, a separate three-way handshake is initiated by each side.
In the Cisco CHAP implementation, by default, the called party must authenticate the calling party (unless authentication is completely turned off) (-> answer B is correct while answer F is not correct). Therefore, a one-way authentication initiated by the called party is the minimum possible authentication. However, the calling party can also verify the identity of the called party, and this results in a two-way authentication ( -> answer D is not correct). Hence, with two-way CHAP, a separate three-way handshake is initiated by each side.
With CHAP, the protocol begins with a random text (called a challenge) sent from the Server, which asks the Client to authenticate. After receiving the challenge, the Client uses its password to perform a one-way hash algorithm (MD5) to encrypt the random text received from the server. The result is then sent back to the Server. Therefore even if someone can capture the messages between client and server, he cannot know what the password is. At the Server side, the same algorithm is used to generate its own result. If the two results match, the passwords must match too.
Question 29
Which type of routing protocol uses the Bellman-Ford algorithm?
A. path-vector
B. link-state
C. distance-vector
D. hybrid routing
Answer: C
Explanation
Distance Vector routing protocols use the Bellman-Ford algorithm for exchanging routing information.
Question 30
Which technology supports fast provisioning for cloud resources?
A. static routing
B. IPS
C. DHCP
D. HSRP
Answer: C
Question 31
Which two statements about the PPPoE client physical interface configuration are true? (Choose two)
A. It must be physically connected to an ATM switch
B. It must be linked to a dialer interface
C. It must be in shutdown mode while the PPPoE configuration is enabled
D. It must be configured without an IP address
E. It must be configured as a trunk port
Answer: B D
Explanation
The picture below shows all configuration needed for PPPoE. Notice that under PPPoE client physical interface Ethernet0/1 there is no IP address configured and it is linked to the Dialer pool 1 (with the dialer pool 1 command.)
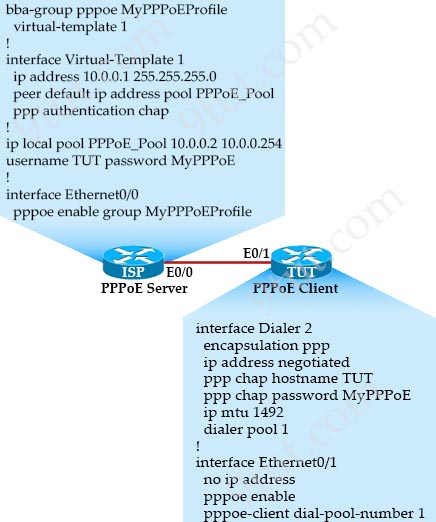
Question 32
Which result occurs when you configure the standby preempt command on an HSRP router that has the same priority as the active router and a higher IP
address?
A. The router becomes the active router only when the current active router fails
B. The router fails to become the active router under any circumstances
C. The router immediately becomes the active router because it has the highest configured IP address
D. The router becomes the active router only when another router triggers renegotiation of the active router
Answer: A
Explanation
In earlier versions, a standby router with the same priority and higher IP address than the active HSRP router will immediately become the active router. But with newer IOS versions, the standby router only becomes the active router only when the current active router fails.
Also in an expired Cisco document, it also said “A standby router with equal priority but a higher IP address will not preempt the active router”
Question 33
Which two values can HSRP use to determine the device with the highest priority? (Choose two)
A. highest configured IP address
B. lowest root bridge ID
C. lowest port ID
D. highest configured priority value
E. highest interface MA C address
Answer: A D
Question 34
Which two features are compatible with SPAN sessions? (Choose two)
A. using private VLANs to identify SPAN destination ports
B. source ports configured as routed ports
C. port security
D. using active port channels as source ports
E. destination ports configured as trunk ports
Answer: D E
Question 35
Which two characteristics of eBGP peers are true? (Choose two)
A. They must be directly connected
B. They must reside in different IP subnets
C. They must reside in the same autonomous system
D. They must reside in the same IP subnet
E. They must reside in two different autonomous systems
Answer: A E
Explanation
eBGP (external BGP) requires two peers must belong to two different AS while iBGP (internal BGP) requires two peers must belong to the same AS.
Unlike iBGP, iBGP requires two peers must be directly connected but they can still use their loopback interfaces for the connection
Question 36
Which feature would prevent a workstation from receiving a DHCP address?
A. STP
B. 802.1Q
C. VTP
D. DTP
Answer: A
Explanation
When a host is connected to a switchport, we have to wait about 50 seconds in order to STP to turn on the port. In this time DHCP cannot assign an IP address for the host. If we want STP to transit to forwarding state immediately we need to issue the “switchport portfast” command.
Question 37
What is the effect of the switchport voice vlan 20 command?
A. It assigns the interface to a voice VLAN
B. It displays the voice VLAN configuration of the interface
C. It configures priority tagging for voice traffic on VLAN 20
D. It configures the interface as an access port
Answer: A
Question 38
Refer to the output. Applying this configuration will result in which outcome?
username CISCO secret Str0ng50690847! aaa authentication login default group tacacs+ group radius local-case aaa authorization exec login default group tacacs+ aaa authorization network login default group tacacs+ aaa accounting exec default start-stop group tacacs+ aaa accounting exec network start-stop group tacacs+ tacacs server Server1 address ipv4 192.168.10.1 key TACACSserver radius server Server2 address ipv4 192.168.20.1 key RADIUSserver
A. Command starting with aaa are rejected because the aaa new-model command is missing
B. The user is authenticated against the configured RADIUS server
C. The user is authenticated against the local database
D. When the enable secret password is entered the user will gain access to the device
Answer: A
Question 39
Which two protocols can support trunking? (Choose two)
A. LACP
B. 802.1Q
C. ISL
D. VTP
E. PAgP
Answer: B C
Explanation
Cisco switches support two trunking protocols 802.1q & ISL. 802.1q is an open standard and is thus compatible between most vendors’ equipment while Inter-Switch Link (ISL) is Cisco proprietary.
Question 40
Which two values can a standard IPv6 ACL use to identify traffic? (Choose two)
A. UDP header
B. TCP header
C. source IPv6 address
D. DSCP value for QoS
E. destination IPv6 address
Answer: C E
Explanation
IPv6 supports only extended ACLs so we always have to specify both the source and destination IPv6 addresses. An example of a standard IPv6 ACL is shown below:
ipv6 access-list Deny_Subnet
deny ipv6 2001:DB8:0:12::/64 any
permit ipv6 any any
Question 41
Which QoS feature can change the value of the IPv4 Type of Service and the IPv6 Traffic Class header fields?
A. shaping
B. marking
C. prioritization
D. policing
Answer: B
Explanation
The IPv6 Traffic Class header field is equivalent to the IPv4 Type of Service field.
Traffic marking allows you to mark (that is, set or change) a value (attribute) for the traffic belonging to a specific class. Attributes that can be set and modified include the DSCP value in the type of service (ToS) byte.
Note: Traffic policing is used to control the rate of traffic flowing across an interface. Traffic shaping retains excess packets in a queue and then schedules the excess for later transmission over increments of time.
Question 42
On which port type is the spanning-tree portfast command supported without additional configuration?
A. access ports
B. Layer 3 subinterfaces
C. Layer 3 main interfaces
D. trunk ports
Answer: A
Explanation
The “spanning-tree portfast” command has no effect on trunk ports (we have to use “spanning-tree portfast trunk” command instead). It is only effective on access ports. This command cannot be used on a Layer 3 interface.
Question 43
How does an IP SLA ICMP Echo operation measure response time?
A. It checks the timestamp on source and destination ICMP Time Exceeded messages
B. It checks the timestamp on ICMP Echo messages
C. It calculates the time that elapses from when the device sends an ICMP Echo request to when it receives an ICMP Echo reply
D. It checks the one-way delay of each ICMP Echo packet received
Answer: B
Explanation
In ICMP operations, the source IP SLA device sends several ICMP packets to the destination. The destination device, which is any IP device, echoes with replies. The source IP SLA device uses the sent and received time stamps to calculate the response time.
Question 44
Refer to the exhibit. All three PCs on the network are in different VLANs. If you want to permit PC A to communicate with PC C, but prevent communications from PC B to PC C, where on this network do you place a standard ACL?
A. on interface S0/0 on R2
B. on interface F0/0 on R1
C. on interface F0/0 on R2
D. on interface S0/0 on R1
Answer: A
Explanation
Standard Access Control List (ACL) filters the traffic based on source IP address. Therefore a standard ACL should be placed on the router which is near to the destination network/host where it is denied. If we place the standard ACL near to source of the traffic, there is a chance for denial or other legitimate traffic from the source network to some other network.
Therefore in this case we should place the ACL on R2 which near the destination PC C. We should place on S0/0 interface as the traffic should be checked first before making any routing decision to save R2’s resource.
Another reason we should not place the ACL on R1 is PC A and PC B belong to different VLANs so we may have subinterfaces on Fa0/0 of R1. As the result of this, we have to apply ACL to two subinterfaces and it is not effective. Please notice that ACL applied to the main interface does not affect the traffic of subinterfaces.
Question 45
When you configure a new switch interface, to which VLAN it is automatically assigned?
A. VLAN with the lowest ID
B. default VLAN
C. management VLAN
D. native VLAN
Answer: B
Explanation
If we configure an access port as follows:
| Switch(config)#interface fa0/1 Switch(config-if)#switchport mode access |
Then this interface, by default, will belong to VLAN 1 (the default VLAN). Of course we can assign another VLAN to this port via the “switchport access vlan {vlan-number}” command.
Question 46
Which two functions of the APIC-EM Path Trace ACL Analysis tool are true? (Choose two)
A. It can identify the path between two specified IP addresses
B. It can determine whether traffic along a specific path will be filtered
C. It can manage access lists in an SDN environment
D. It can create and modify access lists in a private cloud infrastructure
E. It applies the ACLs from a specified path to permit and deny incoming traffic
Answer: A B
Explanation
In the APIC-EM Path Trace ACL Analysis tool, we can identify the path between the source and destination IP addresses.
The APIC-EM Path Trace ACL Analysis Tool can display the ACLs that are using (by downloading the configurations after a specific period of time and shows them when we do a path trace). Therefore it helps verify the ACLs more easily.
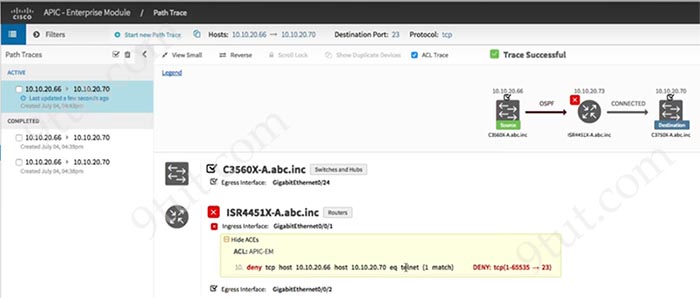
Question 47
Which two statements about the BGP network command are true? (Choose two)
A. It must be configured to enable BGP between neighbors
B. It references a connected interface
C. It must match the subnet and mask of a route in the routing table
D. It references the routing table
E. It can specify a different subnet mask than the mask configured on the interface
Answer: C D
Explanation
For example we have the following topology and config in R1:
| R1(config)#interface fastethernet0/0 R1(config-if)#ip address 11.0.0.1 255.255.255.0 R1(config-if)#no shutdown |
With BGP, we must advertise the correct network and subnet mask in the “network” command. (in this case network 11.0.0.0/24). BGP is very strict in the routing advertisements. In other words, BGP only advertises the network which exists exactly in the routing table (in this case network 11.0.0.0/24 exists in the routing table). If you put the command “network 11.0.0.0 mask 255.255.0.0” or “network 11.0.0.0 mask 255.0.0.0” or “network 11.0.0.1 mask 255.255.255.255” then BGP will not advertise anything.
Question 48
Which networking function occurs on the data plane?
A. forwarding remote client/server traffic
B. sending and receiving OSPF Hello packets
C. spanning-tree election
D. processing inbound SSH management traffic
Answer: A
Explanation
The control plane: The control plane is the brain of the router. It consists of dynamic IP routing protocols (that is OSPF, IS-IS, BGP, and so on), the RIB, routing updates, in addition to other protocols such as PIM, IGMP, ICMP, ARP, BFD, LACP, and so on. In short, the control plane is responsible for maintaining sessions and exchanging protocol information with other router or network devices.
The data plane: The data plane is the forwarding plane, which is responsible for the switching of packets through the router (that is, process switching and CEF switching). In the data plane, there could be features that could affect packet forwarding such as quality of service (QoS) and access control lists (ACLs).
Question 49
What is the maximum bandwidth of a T1 point-to-point connection?
A. 1.544 Mbps
B. 2.048 Mbps
C. 34.368 Mbps
D. 43.7 Mbps
Answer: A
Question 50
According to Cisco best practices, which two tasks must you perform to support a voice VLAN? (Choose two)
A. Disable PortFast on the switch
B. Configure the voice VLAN on a private VLAN port
C. Modify the default QoS settings of the port
D. Enable the voice VLAN on the switch
E. Configure the voice VLAN on a normal-range VLAN
Answer: C D
Explanation
Before you enable voice VLAN, we recommend that you enable QoS on the switch by entering the mls qos global configuration command and configure the port trust state to trust by entering the mls qos trust cos interface configuration command -> By default, QoS is disabled on the switch and all ports are untrusted. These command modifies the default QoS settings.
The Port Fast feature is automatically enabled when voice VLAN is configured. When you disable voice VLAN, the Port Fast feature is not automatically disabled.
Question 51
Which result occurs when you configure the switchport mode dynamic auto command on the switch ports at both ends of a trunk link?
A. The trunk forms immediately because both switch ports are configured for permanent trunking mode
B. Either switch port can initiate the trunk
C. Both switch ports actively form the trunk
D. The trunk fails to form because both switch ports fail to initiate trunking
Answer: D
Explanation
switchport mode dynamic auto makes the interface able to convert the link to a trunk link. The interface becomes a trunk interface if the neighboring interface is set to trunk or desirable mode. The default switchport mode for newer Cisco switch Ethernet interfaces is dynamic auto. Note that if two Cisco switches are left to the common default setting of auto, a trunk will never form.
Reference: http://www.ciscopress.com/articles/article.asp?p=2181837&seqNum=8
Note: We just need to remember that in “dynamic auto” mode, the interface does not try to negotiate a trunk. In “trunk”, “dynamic desirable” modes, the interface try to negotiates a trunk link.
Question 52
To which two categories of routing protocols does BGP belong? (Choose two)
A. link-state
B. distance-vector
C. path-vector
D. composite
E. exterior
Answer: C E
Explanation
BGP is an example of an Exterior Gateway Protocol (EGP) which exchanges routing information between different autonomous systems.
BGP is a path vector protocol. Path vector protocol does not rely on the bandwidth of the links (like OSPF) or hop count (like RIP) or a group of parameters (like EIGRP). Path vector protocol relies on the number of autonomous systems it has to go through. In other words, it choose the path with least number of autonomous systems (shortest AS Path) to reach the destination, provided that the path is loop-free.
Question 53
Drag and drop the HSRP feature from the left onto the correct descriptions on the right.
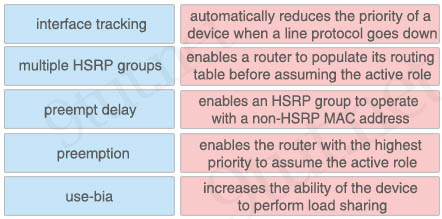
Answer:
+ automatically reduces the priority of a device when a line protocol goes down: interface tracking
+ enables a router to populate its routing table before assuming the active role: preempt delay
+ enables an HSRP group to operate with a non-HSRP MAC address: use-bia
+ enables the router with the highest priority to assume the active role: preemption
+ increases the ability of the device to perform load sharing: multiple HSRP groups
Question 54
Which purpose of the network command in the BGP configuration of a router is true?
A. It advertises a valid network as local to the autonomous system of a router
B. It enables router advertisement in the BGP routing process on the router
C. It indicates whether a neighbor supports route refresh
D. It advertisers any route in BGP with no additional configuration
Answer: B
Question 55
Refer to the exhibit.
| #show ip eigrp events Ignored route, dup router: 2.2.2.2 |
Which problem is indicated by this error?
A. Two or more networks have been defined in the OSPF process
B. The same EIGRP process has already been defined on another router
C. Two or more devices on the network have the same router ID
D. Two or more interfaces have been assigned to the same network
Answer: C
Explanation
In Cisco IOS Software Release 12.0(2) and later, Cisco records the duplicate router IDs in the EIGRP events log, which you can view with the show ip eigrp events command.
Question 56
In which configuration can a PPPoE client operate normally?
A. on a dialer interface configured with multilink PPP
B. on a CPE with more than 10 other clients
C. on an Ethernet connection between two endpoints
D. on a dialer interface configured for QoS queuing
Answer: A
Explanation
The following is an example of configuring Multilink PPP over a dialer interface link:
| Router(config)# interface dialer 1 Router(config-if)# ip address 10.10.100.1 255.255.255.0 Router(config-if)# encapsulation ppp Router(config-if)# dialer pool 3 Router(config-if)# service-policy output policy1 Router(config-if)# service-policy input policy1 Router(config-if)# ppp authentication chap Router(config-if)# ppp chap hostname ISPCorp Router(config-if)# ppp chap password 7 Router(config-if)# ppp multilink Router(config-if)# ppp multilink fragment delay 20 Router(config-if)# ppp multilink interleave |
Reference: https://www.cisco.com/en/US/docs/ios-xml/ios/qos_latjit/configuration/15-2mt/qos-mlppp-dl.html
According to this link: http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/bbdsl/configuration/xe-3s/bba-pppoe-client.html
The PPPoE client does not support the following:
+ More than ten clients per customer premises equipment (CPE)-> This means a CPE can support up to 10 clients so answer B is not correct.
+ Coexistence of the PPPoE client and server on the same device
+ Quality of service (QoS) transmission with queueing on the dialer interface -> answer D is not correct
Answer C is a bit funny as PPPoE cannot operate on a connection. It can only operate on a host/device/router.
Question 57
Which two outcomes are effects of configuring the snmp-server host 10.1.1.1 traps version 3 auth md5 cisco command on router R1? (Choose two)
A. It configures R1 to accept SNMP traffic from the device at 10.1.1.1
B. It configures R1 to send SNMP traps to the device at 10.1.1.1
C. It sets the username cisco on the device at 10.1.1.1
D. It sets the R1 password to cisco
E. It configures R1 to send SNMP informs to the device at 10.1.1.1
Answer: B D
Explanation
In fact, the above command is not correct as we tested it with IOSv15.4:
The correct command should be ” snmp-server host 10.1.1.1 traps version 3 auth cisco”
The syntax of above command is shown below:
snmp-server host host-addr [informs | traps] [version {1 | 2c | 3 {auth | noauth | priv}}] community-string [udp–port port]
This command specify the recipient of an SNMP trap operation.
+ For host-addr, specify the name or Internet address of the host (the targeted recipient).
+ (Optional) Enter informs to send SNMP informs to the host.
+ (Optional) Enter traps (the default) to send SNMP traps to the host.
+ (Optional) Specify the SNMP version (1, 2c, or 3). Default is version 1. SNMPv1 does not support informs.
+ (Optional) For Version 3, select authentication level auth, noauth, or priv.
Note: The priv keyword is available only when the cryptographic software image is installed.
+ For community-string, when version 1 or version 2c is specified, enter the password-like community string sent with the notification operation. When version 3 is specified, enter the SNMPv3 username.
+ (Optional) For port, specify the UDP port of the notification host. Default is port 162.
Therefore with the above command, “md5” is in fact the SNMPv3 username:
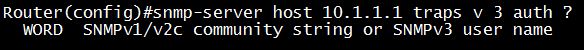
Question 58
Which value is considered first when a stack elects the stack master switch for all stack members powered on within the 20 sec time frame?
A. priority of each switch
B. software feature set of each switch
C. startup time of each switch
D. MAC address of each switch
Answer: A
Explanation
Master Election
The stack master is elected based on one of these factors in the order listed:
1. The switch that is currently the stack master.
2. The switch with the highest stack member priority value.
3. The switch that has the configuration file.
4. The switch with the highest uptime.
5. The switch with the lowest MAC address.
If this is the first time this stack elects a master then it will elect the switch with the highest priority to be the master.
Question 59
Drag and drop the DHCP snooping terms from the left onto the correct descriptions on the right.
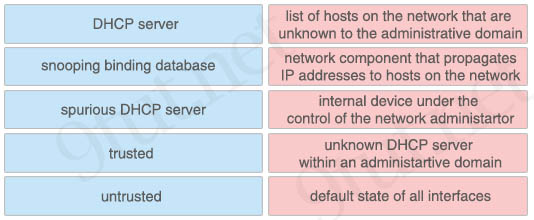
Answer:
+ DHCP server: network component that propagates IP addresses to hosts on the network
+ snooping binding database: list of hosts on the network that are unknown to the administrative domain
+ spurious DHCP server: unknown DHCP server within an administrative domain
+ trusted: internal device under the control of the network administrator
+ untrusted: default state of all interfaces
Question 60
Drag and drop the SDN components from the left onto the correct API types on the right.
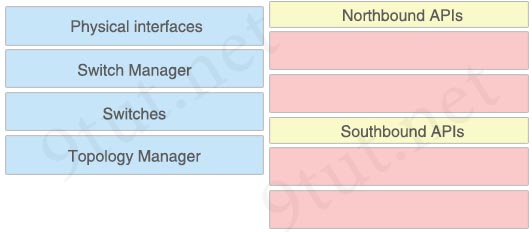
Answer:
Northbound APIs:
+ Switch Manager
+ Topology Manager
Southbound APIs:
+ Physical interfaces
+ Switches
Question 61
Drag and drop the networking features or functions from the left onto the planes on which they operate on the right.
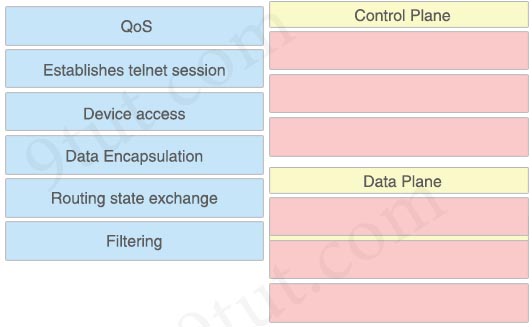
Answer:
Control Plane:
3. Routing state exchange
4. Establishes telnet session
5. Device access
Data Plane:
1. QoS
2. Filtering
6. Data Encapsulation
Explanation
The control plane: The control plane is the brain of the router. It consists of dynamic IP routing protocols (that is OSPF, IS-IS, BGP, and so on), the RIB, routing updates, in addition to other protocols such as PIM, IGMP, ICMP, ARP, BFD, LACP, and so on. In short, the control plane is responsible for maintaining sessions and exchanging protocol information with other router or network devices.
The data plane: The data plane is the forwarding plane, which is responsible for the switching of packets through the router (that is, process switching and CEF switching). In the data plane, there could be features that could affect packet forwarding such as quality of service (QoS) and access control lists (ACLs).
Reference: http://www.ciscopress.com/articles/article.asp?p=2272154&seqNum=3
Question 62
Drag and drop about QoS.
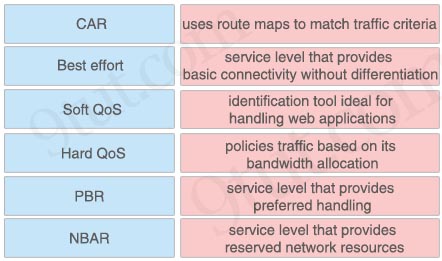
Answer:
+ CAR: policies traffic based on its bandwidth allocation
+ Best effort: service level that provides basic connectivity without differentiation
+ Soft QoS: service level that provides preferred handling
+ Hard QoS: service level that provides reserved network resources
+ PBR: uses route maps to match traffic criteria
+ NBAR: identification tool ideal for handling web applications
Note:
+ Committed Access Rate (CAR)
+ Network-based application recognition (NBAR)
+ Policy-based routing (PBR)
+ Soft QoS: also known as Differentiated Services (Diffserv), which ensures resources for applications based on available bandwidth
+ Hard QoS: Differentiated Service (DiffServ) is an appropriate example for this type of QoS service
Question 63
In an HSRP failover environment, which two tasks must you perform on the preferred active router so that it always assumes the active role when it comes up? (Choose two)
A. Configure the router with a higher priority than the other routers in the group
B. Configure the router with a higher MAC address than the other routers in the group
C. Configure preemption on the router
D. Configure the router with a higher IP address than the other routers in the group
E. Configure tracking on the router
Answer: A C
Explanation
If a HSRP router with highest priority is booted at the same time with other HSRP router in the same group then it will take the active role. But if it is rebooted without configuring preemption then it will lose the active role so we have to configure preemption in this case.
Question 64
Which two services can the ICMP Echo IP SLA provide? (Choose two)
A. network performance monitoring
B. inventory maintenance
C. asset depreciation reporting
D. hardware information exchange between devices
E. network device availability reporting
Answer: A E
Explanation
The ICMP Echo operation measures end-to-end response time between a Cisco router and any devices using IP. Response time is computed by measuring the time taken between sending an ICMP Echo request message to the destination and receiving an ICMP Echo reply.
With IP SLAs, routers and switches perform periodic measurements. Therefore ICMP Echo IP SLA can be used to monitor network performance and network device availability reporting
Using IP SLAs can provide these benefits:
+ Service-level agreement monitoring, measurement, and verification.
+ Network performance monitoring
– Measures the jitter, latency, or packet loss in the network.
– Provides continuous, reliable, and predictable measurements.
Question 65
Which interior routing protocol reduces the size of route tables by advertising default routes for all destinations outside of the default area?
A. OSPF
B. BGP
C. EIGRP
D. RIP
Answer: A
Explanation
This question wants to mention about the Stub/Totally Stubby area of OSPF.
In stub area, the routers do not accept routes belonging to external autonomous systems (AS). In order to reach the outside networks, the routers in the stub area use a default route which is injected into the area by the Area Border Router (ABR)
In totally stubby area, only intra-routes are allowed and the routers use default route to send any traffic outside the area.
Note: Although EIGRP also support stub routing but the router in this area will not advertise routes received from other EIGRP neighbors to the hub router. The stub routers do not receive queries from the hub router any more.
Question 66
Which state does a port with BPDU guard enabled enter when it receives a BPDU?
A. learning
B. err-disabled
C. forwarding
D. disabled
Answer: B
Explanation
BPDU Guard feature allows STP to shut an access port in the event of receiving a BPDU and put that port into err-disabled state.
Question 67
Which role is used by VLAN 1 by default?
A. to propagate VLAN information between switches
B. to pass management traffic
C. to initialize the STP protocol
D. to pass traffic designated for isolation from other traffic on the switch
Answer: B
Explanation
The default Ethernet VLAN is VLAN 1. It is a security best practice to configure all the ports on all switches to be associated with VLANs other than VLAN 1. All used ports are associated with VLANs distinct from VLAN 1.
Reference: http://www.ciscopress.com/articles/article.asp?p=2181837&seqNum=11
All control/management traffic (like CDP, VTP, DTP…) is sent on VLAN 1 and we should separate management and user data traffic. Another reason is by default, the native VLAN is also VLAN 1 which is untagged on trunk links so it may cause a security hole.
Question 68
Which two requirements must be met to allow two routers running EIGRP for IPv6 to become neighbors? (Choose two)
A. Both routers must be configured to use the MTU K value for metric calculations.
B. The peering interface on each router must be set to passive.
C. The EIGRP process must be in no shutdown mode on both routers.
D. The autonomous system numbers must match.
E. The routers must be operating on different subnets.
Answer: C D
Explanation
The following requirements must be met to allow EIGRPv4 and EIGRPv6 to establish a neighbor relationship:
| Requirement | EIGRPv4 | EIGRPv6 |
| Interface is in up/up state | Yes | Yes |
| Interface addresses are in the same subnet | Yes | No |
| The same ASN is used on router eigrp/ipv6 router eigrp commands | Yes | Yes |
| Hello and hold timers have to match | No | No |
| RIDs (router IDs) have to be unique | No | No |
| K-values (used in EIGRP metric calculation formula) have to match | Yes | Yes |
| EIGRP authentication must pass (optional) | Yes | Yes |
Question 69
Which two tasks use OSPFv3 hello packets? (Choose two)
A. Beginning neighbor discovery
B. Requesting topology changes
C. Sharing link-state databases
D. Acknowledging message receipt
E. Performing DR election
Answer: A E
Explanation
Hello packets are OSPF packet Type 1. These packets are multicast periodically to 224.0.0.5 multicast address on all interfaces (unicast on virtual-links) enabling dynamic discovery of neighbors and maintain neighbor relationships. On broadcast and NBMA networks, Hello packets are used to elect DR and BDR.
Question 70
Which two statements about LACP are true? (Choose two)
A. A port in active mode initiates an EtherChannel peering
B. A port in passive mode can receive LACP requests
C. A port in on mode attempts to negotiate an EtherChannel peering
D. A port in auto mode accepts EtherChannel requests without making requests of its own
E. A port in desirable mode initiates an EtherChannel peering
Answer: A B
Explanation
In LACP there are only two modes which are “active” and “passive”. “On” belongs to static mode.
Question 71
Which two features are supported only in named access lists? (Choose two)
A. identifying QoS traffic for marking
B. filtering traffic on VTY lines
C. limiting debug output
D. noncontiguous port filtering
E. deleting entries
Answer: D E
Explanation
The Named ACL Support for Noncontiguous Ports on an Access Control Entry feature allows you to specify noncontiguous ports in a single access control entry, which greatly reduces the number of entries required in an access control list when several entries have the same source address, destination address, and protocol, but differ only in the ports. For example:
Router(config)#ip access-list extended noncontiguousPorts
Router(config-ext-nacl)# permit tcp any eq telnet ftp any eq 23 45 34
Only with named ACL, we can easily remove an individual entry. For example:
R1# show access-list
Standard IP access list nat_traffic
10 permit 10.1.0.0, wildcard bits 0.0.255.255
20 permit 10.2.0.0, wildcard bits 0.0.255.255
30 permit 10.3.0.0, wildcard bits 0.0.255.255
Then to remove the second statement (the line “20 permit 10.2.0.0, wildcard bits 0.0.255.255”) we just need to type “no 20”:
R1(config)#ip access-list standard nat_traffic
R1(config-std-nacl)#no 20
But for numbered ACL, we have to recreated the whole ACL when entries are moved.
Question 72
Which statement describes how the EIGRP feasible distance is calculated?
A. It is the best metric along a path that includes the metric to the neighbor advertising the path
B. It is a path with a reported distance less than the current best path
C. It is the sum of all K values in EIGRP process
D. It is the total metric advertised by the upstream neighbor
Answer: A
Explanation
Feasible distance (FD) is the sum of the the cost from the neighbor to the destination (AD) plus the cost between the local router and the next-hop router.
Maybe it’s a bit confused with these terms so below is an example to make it clear.
Suppose you are in NEVADA and want to go to IOWA. From NEVADA you need to specify the best path (smallest cost) to IOWA.
In this topology, suppose router A & B are exchanging their routing tables for the first time. Router B says “Hey, the best metric (cost) from me to IOWA is 50 and the metric from you to IOWA is 90” and advertises it to router A. Router A considers the first metric (50) as the Advertised distance. The second metric (90), which is from NEVADA to IOWA (through IDAHO), is called the Feasible distance.
All of these routes are placed in the topology table of router A:
| Route | Advertised distance | Feasible distance |
| NEVADA -> IDAHO -> IOWA | 50 | 90 |
| NEVADA -> OKLAHOMA -> IOWA | 70 | 130 |
Router A will select the route to IOWA via IDAHO as it has the lowest Feasible distance and put it into the routing table.
Question 73
Which type of routing protocol relies on the shortest path tree?
A. path-vector
B. hybrid routing
C. link-state
D. distance-vector
Answer: C
Question 74
Which two marking methods are supported with the IPv4 header? (Choose two)
A. DSCP
B. IPP
C. EXP
D. CoS
E. TID
Answer: A B
Explanation
QoS Packet Marking refers to changing a field within a packet either at Layer 2 (802.1Q/pCoS, MPLS EXP) or Layer 3 (IP Precedence, DSCP and/or IP ECN).
At Layer 3, packet marking can be accomplished using the ToS byte in an IPv4 header. Two predominant types of marking mechanisms leverage the ToS byte: IP Precedence (IPP) and Differentiated Services Code Point (DSCP).
IP Precendence is an old approach and has been successively replaced by DSCP for marking IP packets. IP Precedence uses the 3 leftmost bits in the ToS byte.
Reference: CCIE Collaboration Quick Reference
Note: MPLS Experimental (EXP) is a Layer 2 marking technique for IP packet which is encapsulated in MPLS. We cannot mark the DSCP within the IP header as that would require first de-capsulating from MPLS). In this question, it only asks about IPv4 header which is Layer 3 marking.
Question 75
Which two statements about VLAN port assignment are true? (Choose two)
A. By default, all ports are assigned to VLAN 2
B. Ports are assigned to a dynamic VLAN based on the device IP address
C. It can be performed statically or dynamically
D. Static port assignments are based on a preset configuration on a dedicated server.
E. A port in access mode can be assigned to only one VLAN
Answer: C E
Explanation
By default all ports are assigned to VLAN 1, which is the default VLAN.
Ports are assigned to a dynamic VLAN based on its MAC address, not IP address.
The administrator can assign static port on any VLAN and it is not based on any configuration on a server. Only dynamic VLAN assignment requires the configuration from a dedicated server, called the VMPS (VLAN Member Policy Server).
When in access mode, a port can only be assigned to only one VLAN.
This is also a good reference:
VLAN Port Assignments
+ VLANs are assigned to individual switch ports.
+ Ports can be statically assigned to a single VLAN or dynamically assigned to a single VLAN.
+ All ports are assigned to VLAN 1 by default
+ Ports are active only if they are assigned to VLANs that exist on the switch.
+ Static port assignments are performed by the administrator and do not change unless modified by the administrator, whether the VLAN exists on the switch or not.
+ Dynamic VLANs are assigned to a port based on the MAC address of the device plugged into a port.
+ Dynamic VLAN configuration requires a VLAN Membership Policy Server (VMPS) client, server, and database to operate properly.
Reference: http://www.ciscopress.com/articles/article.asp?p=29803&seqNum=2
Question 76
Which two statements identify differences between single-homed and dual-homed WAN topologies? (Choose two)
A. Dual-homed topologies provide greater redundancy than single-homed topologies
B. Only dual-homed connections require dynamic routing to the ISP
C. Single-homed topologies are more costly to an enterprise than dual-homed topologies
D. Only dual-homed connections are connected to the same ISP
E. Single-homed topologies are more appropriate for small-business networks than dual-homed topologies
Answer: A E
Explanation
Single-homed: single connection to only one ISP

In a dual-homed setup, the router in a company is still connected to the outside networks via only one ISP, but with two routers or two connections. When one of the dual-homed connection fails, traffic can still flow via other connection so it can tolerate the loss of a network link.
Question 77
Which two characteristics of extended access lists are true? (Choose two)
A. They can compare source traffic only against a permit or deny statement
B. They must be identified with a number between 100 and 199 or 2000 and 2699
C. They can be identified only with a number between 100 and 199
D. They can be configured to filter only UDP or TCP traffic
E. They can compare source and destination traffic against a permit or deny statement
Answer: B E
Question 78
When you configure VTP on a switch, which VTP mode is enabled by default?
A. transparent
B. server
C. off
D. client
Answer: B
Question 79
Which WAN technology is secure and encrypted by default?
A. VPN
B. VSAT
C. DSL
D. MPLS
Answer: A
Question 80
You attempt to execute the APIC-EM ACL path trace feature without specifying the protocol. How does the ACL path trace respond?
A. It runs normally and reports all possible ACE matches for the protocol field.
B. It runs normally and reports that traffic for all possible protocol matches is denied.
C. It fails to execute the path trace.
D. It runs normally and flags all possible ACE entries as invalid.
Answer: A
Explanation
The following rules effect the ACL path trace results:
+ Only matching access control entry (ACE) are reported.
+ If you leave out the protocol, source port, or destination port when defining a path trace, the results include ACE matches for all possible values for these fields.
+ If no matching ACEs exists in the ACL, the flow is reported to be implicitly denied.
Question 81
Which two statements about traffic shaping are true? (Choose two)
A. It can be applied in the outbound direction only.
B. Packets that exceed the configured threshold are remarked and sent.
C. Packets that exceed the configured threshold are held in a buffer.
D. It can be applied in the inbound and outbound directions.
E. Packets that exceed the configured threshold are dropped
Answer: A C
Explanation
The following diagram illustrates the key difference between traffic policing and traffic shaping. Traffic policing propagates bursts. When the traffic rate reaches the configured maximum rate (or committed information rate), excess traffic is dropped (or remarked). The result is an output rate that appears as a saw-tooth with crests and troughs. In contrast to policing, traffic shaping retains excess packets in a queue and then schedules the excess for later transmission over increments of time. The result of traffic shaping is a smoothed packet output rate.

Traffic shaping is applicable only on outbound interfaces as buffering and queuing happens only on outbound interfaces.
Question 82
Which two values are combined to generate the PVST+ bridge ID on the root switch? (Choose two)
A. the root path cost
B. the switch priority
C. the MAC address
D. the port ID
E. the interface number
Answer: B C
Explanation
The Bridge ID is composed of the bridge priority value (0-65535, 2 bytes) and the bridge MAC address (6 bytes).
Bridge ID = Bridge Priority + MAC Address
Question 83
By default, which two K values does EIGRP for IPv6 use to calculate the metric? (Choose two)
A. reliability
B. bandwidth
C. load
D. MTU
E. delay
Answer: B E
Explanation
First you should learn the formula to calculate the metric. It’s a bit complex conditional formula, I think 🙂
metric = [K1 * bandwidth + (K2 * bandwidth)/(256 – load) + K3 * delay] * [K5/(reliability + K4)] if K5 > 0
metric = [K1 * bandwidth + (K2 * bandwidth)/(256 – load) + K3 * delay] if K5 = 0
By default, K1 = 1, K2 = 0, K3 = 1, K4 = 0, K5 = 0 which means that the default values use only bandwidth & delay parameters while others are ignored. The metric formula is now reduced:
metric = bandwidth + delay
Question 84
What is the minimum level of SNMP that provides encryption?
A. SNMPv3 authPriv
B. SNMPv3 authNoPriv
C. SNMPv3 noAuthNoPriv
D. SNMPv2 noAuthNoPriv
Answer: A
Explanation
+ noAuthNoPriv – Security level that does not provide authentication or encryption.
+ authNoPriv – Security level that provides authentication but does not provide encryption.
+ authPriv – Security level that provides both authentication and encryption.
Question 85
Which two statements about interior gateway routing protocols are true? (Choose two)
A. They may use the Dijkstra algorithm.
B. They can be used to connect to another AS across the Internet as a virtual instance.
C. They may use the Bellman-Ford algorithm.
D. They cannot be used when two devices are connected through a firewall.
E. They can be used to connect to the Internet backbone.
Answer: A C
Explanation
Interior gateway routing protocols like OSPF (uses Dijkstra algorithm), RIP (uses Bellman-Ford algorithm) should be used within an organization or ISP.
Question 86
Which two characteristics of a distance-vector routing protocol are true? (Choose two)
A. It may use the Dijkstra algorithm.
B. It has a complete picture of the network.
C. It has a higher CPU requirement than link-state protocols.
D. It sends periodic updates.
E. It may use the Bellman-Ford algorithm.
Answer: D E
Question 87
Which two statements are benefits of stackable switches? (Choose two)
A. They can support dissimilar Cisco IOS features in a single stack.
B. They are less redundant than modular aggregation.
C. They cannot perform switch-to-router aggregation.
D. They can perform link aggregation.
E. They perform unified management from a single switch stack.
Answer: D E
Question 88
Refer to the exhibit.
| R1(config)#interface GigabitEthernet 1/1/1 R1(config-if)# no ip address R1(config-if)#pppoe enable R1(config-if)#pppoe-client dial-pool-number 1 R1(config-if)#exit |
Which effect of this configuration is true?
A. It configures PPP over Ethernet globally for the device.
B. It configures PPP over Ethernet in client mode.
C. It configures PPP over Multilink.
D. It configures PPP over Ethernet in server mode.
Answer: B
Explanation
The picture below shows all configuration needed for PPPoE. Notice that under PPPoE client physical interface Ethernet0/1 there is no IP address configured and it is linked to the Dialer pool 1 (with the dialer pool 1 command.)

Question 89
For which reason can OSPFv3 fail to start between two routers?
A. OSPFv3 is configured only under an interface.
B. The interface assigned to OSPFv3 is in NBMA mode with only one neighbor defined.
C. The router is configured with IPv6 addresses only and it is unable to find an OSPFv3 router ID.
D. IPv6 unicast routing is enabled.
Answer: C
Explanation
Although OSPFv3 deals solely with IPv6 addresses, it still uses 32-bit router IDs, which are expressed in dotted-decimal (IPv4) format. This router ID must be manually configured if we don’t have any IPv4 interfaces on our router. For example:
ipv6 router ospf 1
router-id 172.16.1.1
Question 90
Which statement about using the keepalive command on a tunnel interface is true?
A. It can be configured on either side of the tunnel or on both sides.
B. It can be configured only on the downstream side of the tunnel.
C. If it is configured on both sides of the tunnel, the values must match.
D. It can be configured only on the upstream side of the tunnel.
Answer: A
Explanation
GRE tunnels are designed to be completely stateless. This means that each tunnel endpoint does not keep any information about the state or availability of the remote tunnel endpoint. A consequence of this is that the local tunnel endpoint router does not have the ability to bring the line protocol of the GRE Tunnel interface down if the remote end of the tunnel is unreachable. Such scenarios would cause data packets that go through the GRE tunnel to be “black holed”. Keepalives on the GRE tunnel interface are used in order to solve this issue in the same way as keepalives are used on physical interfaces. With this feature, the tunnel interface dynamically shuts down if the keepalives fail for a certain period of time.
Generic routing encapsulation (GRE) keepalive packets may be sent from both sides of a tunnel or from just one side. If they are sent from both sides, the period and retry parameters can be different at each side of the link. If you configure keepalives on only one side of the tunnel, the tunnel interface on the sending side might perceive the tunnel interface on the receiving side to be down because the sending interface is not receiving keepalives. From the receiving side of the tunnel, the link appears normal because no keepalives were enabled on the second side of the link.
Reference: https://www.cisco.com/c/en/us/td/docs/ios/12_2sb/feature/guide/sb_gretk.html
Note: GRE tunnel keepalives are only supported on point-to-point GRE tunnels. Tunnel keepalives are configurable on multipoint GRE (mGRE) tunnels but have no effect.
Question 91
Which statement about STP root bridges is true?
A. Each VLAN must have a separate root bridge.
B. An individual switch can be the root bridge for only one VLAN.
C. The switch with the highest root ID is elected as the root bridge.
D. Dynamic root bridge assignment is most efficient.
Answer: A
Explanation
With STP, RSTP or PVST, each VLAN must have its own root bridge.
Question 92
Which statement about the default VLAN is true?
A. It is always the same as the native VLAN.
B. Its name is Default by default.
C. It can be removed without additional configuration.
D. It is always VLAN 1.
Answer: D
Question 93
In which two ways can you isolate the location of a connectivity issue between two devices on your network? (Choose two)
A. Test whether the next hop from the source can reach the destination and work toward the destination.
B. Send an extended ping from the destination to the source.
C. Execute a traceroute from the destination and work toward the source to locate the problematic hop.
D. Send an extended ping from the source to the destination.
E. Execute a traceroute from the source to the destination to locate the problematic hop.
Answer: C E
Explanation
To isolate the connectivity issue location we have to use traceroute to find out the exact location where the trace stops.
Question 94
Which configuration item is the default username for PPP local authentication?
A. the router MAC address
B. the router hostname
C. cisco
D. The router serial number
Answer: B
Explanation
By default for the authentication, CHAP uses the hostname of the router is used to identify itself. If the ppp chap hostname name command is configured, a router uses the name in place of the hostname to identify itself.
With PAP, we have to configure the command “ppp pap sent-username username password password” to match with the local username on the other side (configured with “username username password password” global configuration command)
Question 95
Which three features are supported when you use TACACS+ for device management? (Choose three)
A. It can restrict the commands that individual users are allowed to execute.
B. It can connect disparate networks.
C. It can create network access clients.
D. It can provide additional challenges beyond the username and password.
E. It supports UNIX server functionality.
F. It supports user notifications.
Answer: A D F
Explanation
During a session, if additional authorization checking is needed, the access server checks with a TACACS+ server to determine if the user is granted permission to use a particular command. This provides greater control over the commands that can be executed on the access server while decoupling from the authentication mechanism -> Answer A is correct.
The authentication facility provides the ability to conduct an arbitrary dialog with the user (for example, after a login and password are provided, to challenge a user with a number of questions, like home address, mother’s maiden name, service type, and social security number). In addition, the TACACS+ authentication service supports sending messages to user screens. For example, a message could notify users that their passwords must be changed because of the company’s password aging policy -> Answer F is correct.
Answer F seems to be correct too as “TACACS+ is a security application that provides centralized validation of users attempting to gain access to a router or network access server. TACACS+ services are maintained in a database on a TACACS+ daemon running, typically, on a UNIX or Windows NT workstation”
Question 96
Which WAN topology has the highest degree of reliability?
A. hub-and-spoke
B. full mesh
C. point-to-point
D. router-on-a-stick
Answer: B
Explanation
Full-mesh is a network topology in which there is a direct link between all pairs of nodes. Below is an example of full-mesh topology.

Question 97
Which command do you enter to determine the status of the SVI for VLAN 10?
A. show ip interface brief
B. show run interface vlan 10
C. show vtp status
D. show interface trunk
Answer: A
Explanation
The Switched Virtual Interface (SVI) can be checked using the same command as physical interfaces like “show ip interface brief”. For example we can see the SVIs of VLANs 10 & 20 here:
L3Switch#show ip interface brief Interface IP-Address OK? Method Status Protocol FastEthernet0/1 10.1.4.6 YES manual up up Vlan10 10.2.1.1 YES manual up up Vlan20 10.2.2.2 YES manual up up
Question 98
Which protocol is incompatible with CGMP leave processing?
A. GARP
B. VRRP
C. HSRPv1
D. HSRPv2
Answer: C
Explanation
HSRPv1 uses the multicast address 224.0.0.2 to send hello packets, which can conflict with Cisco Group Management Protocol (CGMP) leave processing. You cannot enable HSRPv1 and CGMP at the same time; they are mutually exclusive.
Question 99
After you configure a new IP SLA, you notice that it is failing to run or generate statistics. Which step do you take first to identify the problem?
A. Use the debug ip sla trace command on the device to troubleshoot.
B. Add the verify-data command to the IP SLA configuration.
C. Add procative threshold conditions to the IP SLA to facilitate troubleshooting.
D. Use the debug ip sla error command on the device to troubleshoot.
Answer: B
Explanation
The command “debug ip sla error” enables debugging output of Cisco IOS IP Service Level Agreements (SLAs) operation run-time errors
Note: The command “debug ip sla trace” traces the execution of a Cisco IOS IP Service Level Agreements (SLAs) operation, use the debug ip sla trace command
+ If the IP Service Level Agreements (SLAs) operation is not running and not generating statistics, add the verify-data command to the configuration (while configuring in IP SLA configuration mode) to enable data verification. When data verification is enabled, each operation response is checked for corruption. Use the verify-data command with caution during normal operations because it generates unnecessary overhead.
+ Use the debug ip sla trace and debug ip sla error commands to help troubleshoot issues with an IP SLAs operation.
Therefore we should add the “verify-data” command first before using the “debug ip sla error” or “debug ip sla trace” command.
Question 100
Which statement about GRE tunnels is true?
A. They pass clear-text traffic.
B. They are stateful.
C. They are unable to carry multicast traffic.
D. They use MD5 for encryption.
Answer: A
Explanation
GRE tunnels are completely stateless. This means that each tunnel endpoint does not keep any information about the state or availability of the remote tunnel endpoint. GRE tunnels can carry multicast traffic so they can be used to transport multicast traffic over networks that have no multicast support. GRE support IPSec for encryption.
Premium Members: You can practice these questions with our quizzes first here.
Question 1
What protocols are supported by trunking? (Choose two)
A. DTP
B. PagP
C. LACP
D. STP
E. VTP
F. 802.1Q
Answer: A F
Question 2
What can be used to modify ToS field in IPv4 and traffic class on IPv6 header?
A. Shaping
B. Prioritising
C. Policing
D. Marking
Answer: D
Question 3
How would you fix connectivity issue between R1 and R2?
Configurations:
R1: int s0/0
ip add x.x.1.1 255.255.255.0
router bgp 100
network x.x.0.0
neighbor x.x.1.2 remote-as 200
R2: int s0/0
ip add x.x.1.2 255.255.255.0
router bgp 100
network x.x.0.0
neighbor x.x.1.1 remote-as 100
A. add the network mask /24 to the network command
B. configure the serial interface with no shutdown
C. replace the router bgp 100 command on R2 with router bgp 200
Answer: C
Question 4
R1 and R2 are connected via Gigaethernet0/0, R1 loses connectivity to R2, what will be your first step of troubleshooting?
A. make sure the encapsulation on R1 and R2 is set to HDLC
B. verify that g0/0 on R1 is up and line protocol down
C. verify that g0/0 on R2 is up and line protocol down
D. verify that g0/0 on R1 and R2 is up and line protocol up
Answer: D
Question 5
Drag and Drop question. Why router R1 doesn’t form an OSPF link with R2?
Answer:
Configurations must be the same:
+ shutdown status
+ hello time
+ hold time
Configuration may differ:
+ interface status
+ serial configuration
+ <one more option>
=============================== New Updated Questions (added on 2nd-May-2019) ===============================
Question 6
Which version of SNMP first allowed user-based access?
A. SNMPv3 with RBAC
B. SNMPv3
C. SNMPv1
D. SNMPv2
Answer: B
Explanation
The user-based access control implemented by SNMPv3 is based on contexts and user names, rather than on IP addresses and community strings. It is a partial implementation of the view-based access control model (VACM).
Question 7
Drag drop about EIGRP K values.
Answer:
K1 – bandwidth
K2 – load
K3 – delay
K4 – Reliability
K5 – MTU
=============================== New Updated Questions (added on 22nd-May-2019) ===============================
Question 8
What routing protocols are supported on stub routers? (Choose two)
or
Which routing protocols are compatible with stubs? (Choose two)
A. RIP
B. EIGRP
C. IS-IS
D. OSPF
E. BGP
Answer: B D
Explanation
Both EIGRP and OSPF support stub areas.
In OSPF, stubs remove either external routes and/or inter-area routes and tends to replace them with a default route. The general idea is that if you have 200 routes in your routing table, the branch doesn’t necessarily need that level of detail and if it is a smaller Cisco 800 or such then it may not do well with a ton of routes.
In EIGRP, stubs work similar but its main goal is to optimize the EIGRP network by stopping the branch for being queried when the hub has a route become active so the route doesn’t become stuck in active as the hub asks all the branches that probably don’t have the route anyway.
Question 9
Refer to the exhibit:
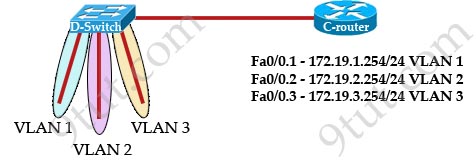
C-router is to be used as a “router-on-a-stick” to route between the VLANs. All the interfaces have been properly configured and IP routing is operational. The hosts in the VLANs have been configured with the appropriate default gateway. What can be said about this configuration?
A. These commands need to be added to the configuration:
C-router(config)# router eigrp 123
C-router(config-router)# network 172.19.0.0
B. No further routing configuration is required.
C. These commands need to be added to the configuration:
C-router(config)# router ospf 1
C-router(config-router)# network 172.19.0.0 0.0.3.255 area 0
D. These commands need to be added to the configuration:
C-router(config)# router rip
C-router(config-router)# network 172.19.0.0
Answer: B
Question 10
DHCP can be prevented by which protocol?
A. VTP
B. DTP
C. 802.1q
D. STP
Answer: D
Explanation
When a host is connected to a switchport, we have to wait for about 50 seconds in order to STP to turn on the port. In this time DHCP cannot assign an IP address for the host. If we want STP to transit to forwarding state immediately we need to issue the “switchport portfast” command.
Question
TUT Company recently installed a new router in their office. Complete the network installation by performing the initial router configurations and configuring RIPv2 routing using the router command line interface (CLI) on the R2-TUT.
Name of the router is R2-TUT
Enable-secret password is Sec@ret
The password to access user EXEC mode using the console is Sec@ret2
The password to allow telnet access to the router is Sec@ret3
IPV4 addresses must be configured as follows:
Ethernet network 213.123.20.128/27 – router has last assignable host address in subnet
Serial network is 200.0.1.16/28 – router has last assignable host address in the subnet. Interfaces should be enabled.
Router protocol is RIPv2
Answer and Explanation
We have 15 Composite Quizzes for the ICND2 200-105 exam. Each Composite quiz comprises of 50 questions of all topics of the new ICND2 exam. If you can pass all of them then congratulations, you have full knowledge for the ICND2 exam. But please grasp the concept of the sims in the ICND2 exam as well before taking the exam.
| Note: The questions of these Composite Quizzes are taken randomly from the pool of specific topic quizzes so some questions are repeated among the Composite Quizzes. This is good because you can practice one question a few times. But we highly recommend you to practice all the specific quizzes carefully before taking these Composite Quizzes. The Composite Quizzes only helps you have a feeling of the real exam with 50 randomly chosen questions from the specific topic quizzes. |
ICND2 exam Composite Quizzes:
Note: Please also check all the “ICND2v3 – New Questions …” at the right-side menu. The Composite Quizzes above may not include these new questions so please practice them separately
Note: We really hope you clearly understand the concept behind each question, not learn by heart the answers.
We have 15 Composite Quizzes for the ICND1 exam. Each Composite quiz comprises of 50 questions of all topics of the ICND1 100-105 exam. If you can pass all of them then congratulations, you have full knowledge for the ICND1 exam. But please grasp the concept of the sims in the ICND1 exam as well before taking the exam.
| Note: The questions of these Composite Quizzes are taken randomly from the pool of specific topic quizzes so some questions are repeated among the Composite Quizzes. This is good because you can practice one question a few times. But we highly recommend you to practice all the specific quizzes (at the right-side menu under “ICND1 100-105” category) carefully before taking these Composite Quizzes. The Composite Quizzes only helps you have a feeling of the real exam with 50 randomly chosen questions from the specific topic quizzes. |
ICND1 exam:
Note: Please also check all the “ICND1v3 – New Questions …” at the right-side menu. The Composite Quizzes above may not include these new questions so please practice them separately
Note: We really hope you clearly understand the concept behind each question, not learn by heart the answers.
[am4show have=’p2;’]
Premium Member: You can practice this sim with our simulator via this link.
[/am4show]
The topology below is running OSPF. You are required to troubleshoot and resolve the OSPF issues between the various routers. Use the appropriate show commands to troubleshoot the issues.
Topology:
[am4show have=’p2;’]
Premium Member: You can try this sim with our simulator here.
[/am4show]
Refer to the topology below and answer the questions.
Note: These new questions have not been classified into specific topics so please practice them separately.
Premium Members: You can practice these questions with our quizzes first at:
+ Question 1 to 20
+ Question 21 to 40
+ Question 41 to 60
Question 1
In the Software-Defined Networking model, where is the interface between the control plane and the data plane?
A. between the control layer and the infrastructure layer
B. between the collocated layer and the dislocated layer
C. between the control layer and application layer
D. between the application layer and the infrastructure layer
Answer: A
Question 2
Which function is performed by a TACACS+ server?
A. It hosts an access list that permits or denies IP traffic to the control plane of a device.
B. It provides external AAA verification.
C. It filters usernames and passwords for Telnet and SSH.
D. It serves as a database for line passwords.
Answer: B
Question 3
Which option is the master redundancy scheme for stacked switches?
A. 1:N
B. 1:1
C. N:1
D. 1+N
Answer: A
Question 4
Which Cisco IOS feature can you use to dynamically identify a connectivity problem between a Cisco device and a designated endpoint?
A. traceroute
B. ICMP Echo IP SLAs
C. IP SLAs threshold monitoring
D. Multi Operation Scheduler IP SLAs
Answer: B
Question 5
Drag and drop the SDN components from the left onto the correct API types on the right.

Answer:
Northbound APIs:
+ Switch Manager
+ Topology Manager
Southbound APIs:
+ Physical interfaces
+ Switches
Question 6
Which two benefits of using MPLS for WAN access are true? (Choose two)
A. It supports hub-and-spoke connectivity.
B. It supports CoS.
C. It provides VPN support.
D. It provides payload security with ESP.
E. It supports Authentication Header.
Answer: B C
Question 7
Which two statements about MPLS are true? (Choose two)
A. It encapsulates all traffic in an IPv4 header
B. It provides automatic authentication
C. It uses labels to separate and forward customer traffic
D. It can carry multiple protocols, including IPv4 and IPv6
E. It tags customer traffic using 802.1Q
Answer: C D
Question 8
Which three statements about the ACEs that are matched by a Cisco APIC-EM ACL path are true? (Choose three)
A. If the trace fails to find a matching ACE in an ACL, it is reported as implicitly permitted.
B. If an optional criterion is omitted from the trace, the results include all possible ACE matches.
C. If the trace fails to find a matching ACE in an ACL, it is reported as implicitly denied.
D. ACEs are reported only if they match.
E. All ACEs found by the trace are reported, including those that fail to match.
F. If an optional criterion is omitted from the trace, the results are reported as if the default value was specified.
Answer: B C D
Explanation
An ACL path trace shows whether the traffic matching your criteria would be permitted or denied based on the ACLs configured on the path.
The following rules effect the ACL path trace results:
+ Only matching access control entries (ACEs) are reported.
+ If you leave out the protocol, source port, or destination port when defining a path trace, the results include ACE matches for all possible values for these fields.
+ If no matching ACEs exists in the ACL, the flow is reported to be implicitly denied.
Note:
Question 9
Which three protocols does APIC-EM support with Path Trace? (Choose three)
A. HSRP
B. ECMP
C. WLC
D. SNMP
E. SMTP
F. ECMP/TR
Answer: A B F
Explanation
Path Trace Supported Device Protocols and Network Connections:
Access Control List (ACL)
Border Gateway Protocol (BGP)
Dynamic Multipoint VPN (DMVPN)
Enhanced Interior Gateway Routing Protocol (EIGRP)
Equal Cost Multipath/Trace Route (ECMP/TR)
Equal Cost Multi Path (ECMP)
Hot Standby Router Protocol (HSRP)
Intermediate System-to-Intermediate System (IS-IS) Protocol
…
For more information about these supported protocols and network connections, please visit https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/application-policy-infrastructure-controller-enterprise-module/1-3-x/config-guide/b_apic-em_config_guide_v_1-3-x/b_apic-em_config_guide_v_1-3-x_chapter_0111.html
Question 10
Where must you configure switch-level global features on a switch stack?
A. on the stack master
B. on the stack master and each individual stack member
C. on the stack master or any individual stack member
D. on each individual stack member
Answer: A
Question 11
Which two statements about the Cisco APIC-EM ACL Path Trace feature are true? (Choose two)
A. Higher-priority ACEs override lower-priority ACEs in the same ACL.
B. The trace analyzes only the egress interface of all devices in the path.
C. The trace analyzes the ingress interface and the egress interface of all devices in the path.
D. The trace analysis stops as soon as the trace encounters a deny entry on the path.
E. The trace analyzes only the ingress interface of all devices in the path.
Answer: A C
Explanation
Access Control List (ACL) Trace analyzes how a flow is affected by ACLs programmed on the path. After the path is calculated between the source and the destination, the ACL Trace analyzes both ingress and egress interfaces of all devices on the path -> C is correct.
Analysis of entries within an individual ACL is cumulative. That is, if a higher priority ACE is a match, lower-priority ACEs are ignored -> A is correct.
Question 12
Which two data integrity algorithms are commonly used in VPN solutions? (Choose two)
A. DH1
B. DH2
C. HMAC-MD5
D. HMAC-SHA-1
E. RSA
Answer: C D
Explanation
Two popular algorithms a VPN gateway uses for verifying integrity of data are HMAC-Message Digest 5 (HMAC-MD5) and HMAC-Secure Hash Algorithm 1 (HMAC-SHA1)
+ HMAC-MD5 uses a 128-bit shared-secret key of any size. The variable-length message and shared-secret key are combined and run through the HMAC-MD5 hash algorithm. The output is a 128-bit hash. The hash is appended to the original message and is forwarded to the remote end.
+ HMAC-SHA-1 uses a secret key of any size. The variable-length message and the shared-secret key are combined and run through the HMAC-SHA-1 hash algorithm. The output is a 160-bit hash. The hash is appended to the original message and is forwarded to the remote end.
Diffie-Hellman Group 1 (DH-1) & Diffie-Hellman Group 2 (DH-2) are two encryption algorithms for VPN, not data integrity algorithms.
RSA is also an encryption algorithm, not data integrity algorithm.
Question 13
Which component of VPN technology ensures that data is unaltered between the sender and recipient?
A. encryption
B. authentication
C. key exchange
D. data integrity
Answer: D
Question 14
In which three circumstances may your organization require a high-bandwidth Internet connection? (Choose three)
A. It uses cloud computing
B. It uses network devices that require frequent IOS upgrades
C. It uses peer-to-peer file sharing
D. It is undergoing a SAN expansion
E. It uses Infrastructure as a Service
F. It uses resource-intensive applications
Answer: A C E
Question 15
Which tool or utility can report whether traffic matching specific criteria can reach a specified destination on the ACLs along the path?
A. Cisco Security Device Manager
B. Cisco Prime
C. APIC-EM
D. Cisco Network Assistant
Answer: C
Explanation
If you performed an ACL trace, the devices show whether the traffic matching your criteria would be permitted or denied based on the ACLs configured on the interfaces.
Question 16
Which three features are QoS congestion-management tools? (Choose three)
A. PPPoE
B. PQ
C. FIFO
D. PPP
E. PDQ
F. WFQ
Answer: B C F
Explanation
Good reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/qos_conmgt/configuration/xe-3s/qos-conmgt-xe-3s-book/qos-conmgt-oview.html
Question 17
For which two reasons might you choose chassis aggregation instead of stacking switches? (Choose two)
A. to avoid the use of a centralized configuration manager
B. to avoid relying solely on Ethernet interfaces
C. to allow hot-swapping modules
D. to increase the number of devices in use
E. to increase the maximum port count
Answer: B C
Explanation
Chassis aggregation is a Cisco technology to make multiple switches operate as a single switch. It is similar to stacking but meant for powerful switches (like the 6500 and 6800 series switches). Chassis aggregation is often used in the core layer and distribution layer (while switching stacking is used for access layer). Chassis aggregation refers to a technology implemented on modular switches (like Catalyst 6500 and 4500s). The modules can be hot-swapped on these switches.
With switch stacking, the switches that are added to or removed from the switch stack must be powered off -> Answer C is correct.
A switch stack is a set of up to nine Cisco EtherSwitch service modules or Catalyst 3750 switches connected through their Cisco StackWise ports while Chassis aggregation is a Cisco technology to make two switches operate as a single logical switch. Therefore stacking switches have more ports than chassis aggregation -> Answer E is not correct.
Both chassis aggregation and switch stacking increase the number of devices in use and they also use a centralized conf -> Answer D is not correct.
Switch stacking elects a master switch to control the configuration and administration of the stack. Chassis aggregation also uses a single Supervisor module to control all of the Spanning-Tree protocol running in both switches that were bundled together. Therefore we can consider both of them use a centralized manager -> Answer A is not correct.
Chassis aggregation is used for high-end switches (like cat6500s and Cat4500s) which support many types of linecards/modules other than Ethernet while switch stacking only supports Ethernet interfaces -> Answer B is correct.
Question 18
Which option is the master redundancy scheme for stacked switches?
A. 1:N
B. N:1
C. 1:1
D. 1+N
E. N+1
Answer: A
Explanation
1:N master redundancy: Every switch in the stack can act as the master. If the current master fails, another master is elected from the stack.
1:N master redundancy allows each stack member to serve as a master, providing the highest reliability for forwarding. Each switch in the stack can serve as a master, creating a 1:N availability scheme for network control. In the unlikely event of a single unit failure, all other units continue to forward traffic and maintain operation.
Note:
N+1 simply means that there is a power backup in place should any single system component fail. The ‘N’ in this equation stands for the number of components necessary to run your system. The ‘+1’ means there is one independent backup should a component of that system fail. An example of “N+1” is your family has 5 members, so you need 5 cups to drink. But you have one extra cup for redundancy (6 cups in total) so that if any cup breaks, you still have enough cups for the family.
Question 19
Which three statements about QoS policing are true? (Choose three)
A. It can be applied to outbound traffic only.
B. It avoids queuing delays.
C. It drops excess packets.
D. It can be applied to inbound and outbound traffic.
E. It queues excess traffic.
F. It is configured in bits per second.
Answer: B C D
Explanation
Unlike traffic shaping, QoS policing avoids delays due to queuing.
QoS policing drops (or remarks) excess packets above the committed rates. Does not buffer.
QoS policing is configured in bytes (while QoS traffic shaping is configured in bits per second)
QoS policing can be applied to both inbound and outbound traffic (while QoS shaping can only be applied to outbound traffic)
Question 20
Which switch architecture is scalable, flexible, resilient, and relatively inexpensive?
A. aggregate switch
B. single switch
C. stacked switch
D. modular-chassis switch
Answer: C
Question 21
Which device might be installed at a branch office to enable and manage an IPsec site-to-site VPN?
A. Cisco IOS IPsec/SSL VPN client
B. Cisco VPN Client
C. ISDN terminal adapter
D. Cisco Adaptive Security Appliance
Answer: D
Explanation
An example of IPsec site-to-site VPN is your corporation has departments in many countries which need to communicate with each other. A popular solution is site-to-site (LAN-to-LAN) VPN to create private networks through the Internet. But as we know, Internet is not a safe environment for important data to be transferred. That is the reason why we need IPsec, a protocol suite for securing Internet Protocol (IP) communications by authenticating and encrypting each IP packet of a communication session.
Cisco Adaptive Security Appliance (ASA) supports IPsec, that’s all I can say! If you wish to learn more about the configuration, please read http://www.cisco.com/en/US/products/ps5855/products_configuration_example09186a0080a9a7a3.shtml
Question 22
Which option is the main function of congestion management?
A. discarding excess traffic
B. queuing traffic based on priority
C. classifying traffic
D. providing long-term storage of buffered data
Answer: B
Question 23
Which IPv6 address is the all-router multicast group?
A. FF02::1
B. FF02::2
C. FF02::3
D. FF02::4
Answer: B
Explanation
A packet sent to an all-router multicast group is received and processed by all IPv6 routers on the link or network
Question 24
Which IPv6 routing protocol uses multicast group FF02::9 to send updates?
A. static
B. RIPng
C. OSPFv3
D. IS-IS for IPv6
Answer: B
Explanation
Some special IPv6 addresses:
FF02::5 – OSPFv3 All SPF routers
FF02::6 – OSPFv3 All DR routers
FF02::9 – All routing information protocol (RIP) routers on a link
FF02::A – EIGRP routers
Question 25
Drag and drop the BGP components from the left onto the correct descriptions on the right.

Answer:
+ Device that running BGP: BGP speakers
+ Neighbor that share the same AS number as a local device: iBGP peer
+ Neighbor that located outside of AD domain of the local device: eBGP peer
+ Value that identify an administrative domain: Autonomous system number
+ Value that is advertise with network keyword: Prefix
Question 26
Which two statements about switch stacking are true? (Choose two)
A. The stack is powered by a single power cable
B. The switches are connected in a daisy-chain fashion
C. The first and last switch in the stack must be connected to one another
D. The switches are connected by crossover cables
E. The switches must be fully meshed
Answer: B C
Question 27
Which name describes an IPv6 host-enabled tunneling technique that uses IPv4 UDP, does not require dedicated gateway tunnels, and can pass through existing IPv4 NAT gateways?
A. manual 6to4
B. dual stack
C. dynamic
D. Teredo
Answer: D
Question 28
Which two steps must you perform on each device that is configured for IPv4 routing before you implement OSPFv3? (Choose two)
A. configure an autonomous system number
B. configure a loopback interface
C. configure a router ID
D. enable IPv6 on an interface
E. enable IPv6 unicast routing
Answer: C E
Question 29
What is the alternative notation for the IPV6 address B514:82C3:0000:0000:0029:EC7A:0000:EC72?
A. B514:82C3:0029::EC7A:0000:EC72
B. B514:82C3:0029:EC7A:EC72
C. B514:82C3::0029:EC7A:0:EC72
D. B514:82C3::0029:EC7A:EC72
Answer: C
Question 30
Refer to the exhibit.
|
R1 interface FastEthernet0/0 ipv6 router ospf 1 |
R2 interface FastEthernet0/0 ipv6 router ospf 1 |
After you apply the give configurations to R1 and R2 you notice that OSPFv3 fails to start. Which reason for the problem is most likely true?
A. The area numbers on R1 and R2 are mismatched
B. The IPv6 network addresses on R1 and R2 are mismatched
C. The autonomous system numbers on R1 and R2 are mismatched
D. The router ids on R1 and R2 are mismatched
Answer: A
Question 31
Which two of these statements are true of IPv6 address representation? (Choose two)
A. There are four types of IPv6 addresses: unicast, multicast, anycast, and broadcast
B. A single interface may be assigned multiple IPv6 addresses of any type.
C. Every IPv6 interface contains at least one loopback address.
D. The first 64 bits represent the dynamically created interface ID.
E. Leading zeros in an IPv6 16 bit hexadecimal field are mandatory.
Answer: B C
Explanation
A single interface may be assigned multiple IPv6 addresses of any type (unicast, anycast, and multicast).
Every IPv6-enabled interface must contain at least one loopback (::1/128) and one link-local address. Optionally, an interface may have multiple unique local and global addresses.
Leading zeros in IPv6 are optional do that 05C7 equals 5C7 and 0000 equals 0 -> E is not correct.
Question 32
Which two statements describe characteristics of IPv6 unicast addressing? (Choose two)
A. Global addresses start with 2000::/3
B. Link-local addresses start with FE00:/12
C. Link-local addresses start with FF00::/10
D. There is only one loopback address and it is ::1
E. If a global address is assigned to an interface, then that is the only allowable address for the interface.
Answer: A D
Explanation
Below is the list of common kinds of IPv6 addresses:
| Loopback address | ::1 |
| Link-local address | FE80::/10 |
| Site-local address | FEC0::/10 |
| Global address | 2000::/3 |
| Multicast address | FF00::/8 |
From the above table, we learn that A and D are correct while B and C are incorrect. Notice that the IPv6 unicast loopback address is equivalent to the IPv4 loopback address, 127.0.0.1. The IPv6 loopback address is 0:0:0:0:0:0:0:1, or ::1.
E is not correct because of anycast addresses which are indistinguishable from normal unicast addresses. You can think of anycast addresses like this: “send it to nearest one which have this address”. An anycast address can be assigned to many interfaces and the first interface receives the packet destined for this anycast address will proceed the packet. A benefit of anycast addressing is the capability to share load to multiple hosts. An example of this benefit is if you are a Television provider with multiple servers and you want your users to use the nearest server to them then you can use anycast addressing for your servers. When the user initiates a connection to the anycast address, the packet will be routed to the nearest server (the user does not have to specify which server they want to use).
Question 33
Which address is the IPv6 all-RIP-routers multicast group address that is used by RIPng as the destination address for RIP updates?
A. FF02::6
B. FF02::9
C. FF05::101
D. FF02::A
Answer: B
Question 34
Which value must you configure on a device before EIGRP for IPv6 can start running?
A. public IP address
B. loopback interface
C. router ID
D. process ID
Answer: C
Question 35
Which component of an IPv6 OSPFv3 connection must be configured in IPv4 format?
A. Router ID
B. Primary interface
C. Neighbor address
D. Secondary interface
Answer: A
Question 36
Which IPv6 address is the equivalent of the IPv4 interface loopback address 127.0.0.1?
A. ::1
B. ::
C. 2000::/3
D. 0::/10
Answer: A
Question 37
Which three are characteristics of an IPv6 anycast address? (Choose three)
A. one-to-many communication model
B. one-to-nearest communication model
C. any-to-many communication model
D. a unique IPv6 address for each device in the group
E. the same address for multiple devices in the group
F. delivery of packets to the group interface that is closest to the sending device
Answer: B E F
Question 38
You enter the show ipv6 route command on an OSPF device and the device displays a remote route. Which conclusion can you draw about the environment?
A. OSPF is distributing IPv6 routes to BGP.
B. The router is designated as an ABR.
C. The router is designated as totally stubby.
D. OSPFv3 is in use.
Answer: D
Question 39
Which command do you enter to permit IPv6 functionality on an EIGRPv3 interface?
A. Router1(config)#ipv6 unicast-routing
B. Router1(config-rf)#ipv6 router eigrp 1
C. Router1(config-if)#ipv6 enable
D. Router1(config-if)#ipv6 eigrp 1
Answer: D
Question 40
What are three features of the IPv6 protocol? (Choose three)
A. complicated header
B. plug-and-play
C. no broadcasts
D. checksums
E. optional IPsec
F. autoconfiguration
Answer: B C F
Question 41
Which three checks must you perform when troubleshooting EIGRPv6 adjacencies? (Choose three)
A. Verify that IPv6 is enabled.
B. Verify that the network command has been configured.
C. Verify that auto summary is enabled.
D. Verify that the interface is up.
E. Verify that an IPv4 address has been configured.
F. Verify that the router ID has been configured.
Answer: A D F
Question 42
Which of these represents an IPv6 link-local address?
A. FE08::280e:611:a:f14f.3d69
B. FE81::280f.512b:e14f:3d69
C. FE80::380e:611a:e14f:3d69
D. FEFE:0345:5f1b::e14d:3d69
Answer: C
Explanation
The range of IPv6 link-local address (similar to the Windows auto-configuration IP address of 169.254.x.x.) is FE80::/10. For more information about IPv6, please read my IPv6 tutorial.
Question 43
Identify the four valid IPv6 addresses. (Choose four)
A. ::
B. ::192:168:0:1
C. 2000::
D. 2001:3452:4952:2837::
E. 2002:c0a8:101::42
F. 2003:dead:beef:4dad:23:46:bb:101
Answer: A B E F
Explanation
Answers B E F are correct because A and B are the short form of 0:0:0:0:192:168:0:1 and 2002:c0a8:0101:0:0:0:0:0042 while C are normal IPv6 address.
Answer A is correct because “::” is named the “unspecified” address and is typically used in the source field of a datagram that is sent by a device that seeks to have its IP address configured.
Answer C is not correct because a global-unicast IPv6 address is started with binary 001, denoted as 2000::/3 in IPv6 and it also known as an aggregatable global unicast address. The 2000:: (in particular, 2000::/3) is just a prefix and is not a valid IPv6 address.
In fact answer D is acceptable but it is considered the network portion of an IPv6 address so it is a worse choice than others.
The entire global-unicast IPv6 address range is from 2000::/128 to 3FFF:FFFF:FFFF:FFFF:FFFF:FFFF:FFFF/128, resulting in a total usable space of over 42,535,295,865,117,307,932,921,825,928,971,000,000 addresses, which is only 1/8th of the entire IPv6 address space!
Question 44
Which type of IPv6 ACL is applied first in the order of precedence?
A. TCAM
B. router ACLs
C. Fragmented frames
D. Port ACLs
Answer: D
Question 45
Which IPv6 address is valid?
A. 2031:0:130F::9C0:876A:130B
B. 2001:0DB8:0000:130F:0000:0000:08GC:140B
C. 2001:0DB8:0:130H::87C:140B
D. 2031::130F::9C0:876A:130B
Answer: A
Explanation
Answer B is not correct because it has a letter “G”.
Answer C is not correct because it has a letter “H”.
Answer D is not correct because it has two “::”.
Question 46
Which step must you perform first to enable OSPFv3 process 20 for IPv6?
A. Enter the ipv6 router ospf 20 command to enable OSPFv3.
B. Enter the ip routing command to enable IPv4 unicast routing.
C. Enter the router ospf 20 commands to enable OSPF.
D. Enter the ipv6 unicast-routing command to enable IPv6 unicast routing.
Answer: D
Question 47
Which two are features of IPv6? (Choose two)
A. multicast
B. broadcast
C. allcast
D. podcast
E. anycast
Answer: A E
Explanation
Anycast IPv6 addresses are 128-bit identifiers for interfaces and sets of interfaces. A packet sent to an anycast address is delivered to one of the interfaces identified by that address (the “nearest” one, according to the routing protocols’ measure of distance)
Question 48
Which BGP command do you enter to allow a device to exchange IPv6 prefixes with its neighbor?
A. neighbor ip-address activate
B. neighbor ip-address remote-as ASN
C. router bgp ASN
D. show ip bgp neighbors
Answer: A
Question 49
Which protocol can be used between administrative domains?
A. IS-IS
B. EIGRP
C. BGP
D. OSPF
Answer: C
Question 50
Which two statements about eBGP neighbor relationships are true? (Choose two)
A. The two devices must reside in different autonomous systems
B. Neighbors must be specifically declared in the configuration of each device
C. They can be created dynamically after the network statement is con-figured.
D. The two devices must reside in the same autonomous system
E. The two devices must have matching timer settings
Answer: A B
Question 51
What does it take for BGP to establish connection? (Choose two)
A. Enable CDP
B. AS number on local router
C. AS number on remote router
D. IGP
E. EGP
Answer: B C
Question 52
A security administrator wants to profile endpoints and gain visibility into attempted authentications. Which 802.1x mode allows these actions?
A. Monitor mode
B. High-Security mode
C. Low-impact mode
D. Closed mode
Answer: A
Explanation
There are three authentication and authorization modes for 802.1x:
+ Monitor mode
+ Low impact mode
+ High security mode
Monitor mode allows for the deployment of the authentication methods IEEE 802.1X without any effect to user or endpoint access to the network. Monitor mode is basically like placing a security camera at the door to monitor and record port access behavior.
With AAA RADIUS accounting enabled, you can log authentication attempts and gain visibility into who and what is connecting to your network with an audit trail. You can discover the following:
+ Which endpoints such as PCs, printers, cameras, and so on, are connecting to your network
+ Where these endpoints connected
+ Whether they are 802.1X capable or not
+ Whether they have valid credentials
+ In the event of failed MAB attempts, whether the endpoints have known, valid MAC addresses
Monitor mode is enabled using 802.1X with the open access and multiauth mode Cisco IOS Software features enabled, as follows:
sw(config-if)#authentication open
sw(config-if)#authentication host-mode multi-auth
For more information about each mode, please read this article: http://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Security/TrustSec_1-99/Phased_Deploy/Phased_Dep_Guide.html
Question 53
Refer to the exhibit.
| R1 interface Loopback0 ip address 172.16.1.33 255.255.255.224 interface FastEthernet0/0 ip address 192.168.12.1 255.255.255.0 router bgp 100 neighbor 192.168.12.2 remote-as 100 |
Which command do you enter so that R1 advertises the loopback0 interface to the BGP Peers?
A. Network 172.16.1.32 mask 255.255.255.224
B. Network 172.16.1.0 0.0.0.255
C. Network 172.16.1.32 255.255.255.224
D. Network 172.16.1.33 mask 255.255.255.224
E. Network 172.16.1.32 mask 0.0.0.31
F. Network 172.16.1.32 0.0.0.31
Answer: A
Question 54
Drag and drop the DHCP snooping terms from the left onto the correct descriptions on the right.

Answer:
+ DHCP server: network component that propagates IP addresses to hosts on the network
+ snooping binding database: list of hosts on the network that are unknown to the administrative domain
+ spurious DHCP server: unknown DHCP server within an administrative domain
+ trusted: internal device under the control of the network administrator
+ untrusted: default state of all interfaces
Question 55
Drag and drop the network programmability features from the left onto the correct description on the right.

Answer:
+ HTTPS: call to the APIC-EM API from a library
+ JSON: data-structure format that passes parameters for API calls
+ OpenFlow: southbound API
+ RBAC: token-based security mechanism
+ REST: northbound API
Explanation
What is the data format used to send/receive data when making REST calls for APIC-EM?
Javascript Object Notation (JSON) is used to pass parameters when making API calls and is also the returned data format.
What’s RBAC?
The Role-Based Access Controls (RBAC) mechanism utilizes security tokens that the controller issues upon successful authentication of a user of the APIC-EM controller. All subsequent requests from the authenticated user must provide a valid token.
Reference: https://communities.cisco.com/docs/DOC-60530#q16
Question 56
Drag drop about characteristics of a cloud environment.

Answer:
+ Multitenancy: One or more clients can be hosted with the same physical or virtual infrastructure
+ Scalability: Resources can be added and removed as needed to support current workload and tasks
+ Workload movement: Tasks can be migrated to different physical locations to increase efficiency or reduce cost
+ On-demand: Resources are dedicated only when necessary instead of on a permanent basis
+ Resiliency: Tasks and data residing on a failed server can be seamlessly migrated to other physical resources
Question 57
Which two statements about exterior gateway routing protocols are true? (Choose two)
A. BGP is considered to be a path-vector protocol.
B. They can be used to connect to another AS across the Internet as a virtual instance.
C. eBGP is considered to be a distance-vector protocol.
D. EGP is considered to be a path-vector protocol.
E. They can be used to connect to the Internet
Answer: A E
Question 58
Drag and drop the BGP components from the left onto the correct descriptions on the right.

Answer:
+ autonomous system number: Value that identifies an administrative domain
+ BGP Speaker: device that is running BGP
+ eBGP: Peer neighbor that located outside of administrative domain of the local device
+ BGP Peer: neighbor device that shares the same AS number as the local device
+ Prefix: value that is advertised with the network keyword
Question 59
Which routing protocol is most appropriate for sending and receiving routes directly to and from the Internet?
A. RIP
B. BGP
C. EIGRP
D. OSPF
Answer: B
Question 60
Drag and drop the descriptions of performing an initial device configuration from the left onto the correct features or components on the right.

Answer:
+ feature that allows remote access to the console: VTY line
+ feature that confirms a user is permitted to access the device: password
+ value that enables routing when the device is unable to locate a specific route on the routing table: default gateway
+ value that uniquely identifies the device: hostname
+ encrypted value that is used to confirm a user is permitted to access the device: enable secret password
Question
[am4show have=’p2;’]A new switch is being added to our LAN. Complete the following steps:
+ Configuring the building_2 switch with an IP address and default gateway.
+ Use the last available IP address on the management subnet for the switch host address.
+ In addition, the switch needs to be configured to be in the same VTP domain as the building_1 switch and also needs to be configured as a VTP client.
+ Assume that the IP configuration and VTP configuration on building_1 are complete and correct.
The configuration of the router is not accessible for this exercise. You must accomplish the following tasks:
Determine and configure the IP host address of the new switch.
Determine and configure the default gateway of the new switch.
Determine and configure the correct VTP domain name for the new switch.
Configure the new switch as a VTP client.
Note: You might be asked to use first, second… available IP address on the management subnet.[/am4show]
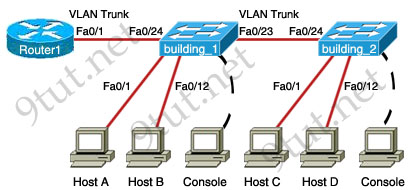
Answer and Explanation
Question
A network associate is configuring a router for the TUT company to provide internet access. The ISP has provided the company six public IP addresses of 198.18.184.105 198.18.184.110. The company has 14 hosts that need to access the internet simultaneously. The hosts in the company LAN have been assigned private space addresses in the range of 192.168.100.17 – 192.168.100.30.
|
The following have already been configured on the router: – The basic router configuration |
Tasks:
+ Use NAT to provide Internet access to all hosts in the company LAN.
+ Name the router TUT
+ Inside global addresses: 198.18.184.105 198.18.184.110/29
+ Inside local addresses: 192.168.100.17 – 192.168.100.30/28
+ Numer of inside hosts: 14
Solution:
Question
9tut.net company has decided to network three locations to improve efficiency in inventory control. The routers have been named to reflect the location: Boston, Frankfurt, Lancaster.
The necessary networking has been completed at each location, and the routers have been configured with single area OSPF as the routing protocol. The Boston router was recently installed but connectivity is not complete because of incomplete routing tables. Identify and correct any problem you see in the configuration.
Note: The OSPF process must be configured to allow interfaces in specific subnets to participate in the routing process.
You can download this lab and open with Packet Tracer here: https://www.9tut.net/download/OSPF_Sim_with_Solution.zip. Please say thanks to Renan who shared the files with us!
Answer and Explanation:
=========================New Questions added on 1st-Jun-2018============================
Note: These new questions have not been classified into specific topics so please practice them separately. Also in this page we are testing show/hide answer button.
Question 1
What are three reasons a company needs high speed Internet access? (Choose three)
A. SAN upgrade
B. Large network device IOS upgrades
C. Peer2peer
D. IaaS
E. ?
Question 2
How do you configure a voice port?
Question 3
What command do you look to see native VLAN?
A. show interfaces
B. show interface trunk
C. show ip interface brief
Question 4
What are the three things that can cause congestion? (Choose three)
A. Broadcast
B. defective hardward
C. Collision domains
D. ?
Question 5
What are the results of a saturated tunnel?
Explanation
Load on the interface as a fraction of 255 (255/255 is completely saturated), calculated as an exponential average over 5 minutes.
Question 6
Which utility can you use to identify redundant or shadow rules?
A. The ACL trace tool in Cisco APIC-EM.
B. The ACL analysis tool in Cisco APIC-EM.
C. The Cisco APIC-EM automation scheduler.
D. The Cisco IWAN application.
Explanation
Cisco APIC-EM supports the following policy analysis features:
+ Inspection, interrogation, and analysis of network access control policies.
+ Ability to trace application specific paths between end devices to quickly identify ACLs in use and problem areas.
+ Enables ACL change management with easy identification of conflicts and shadows -> Maybe B is the most suitable answer.
The ACL trace tool can only help us to identify which ACL on which router is blocking or allowing traffic. It cannot help identify redundant/shadow rules.
Note:
Cisco Application Policy Infrastructure Controller Enterprise Module (APIC-EM) is a Cisco Software Defined Networking (SDN) controller, which uses open APIs for policy-based management and security through a single controller, abstracting the network and making network services simpler. APIC-EM provides centralized automation of policy-based application profiles.
Reference: CCNA Routing and Switching Complete Study Guide
Cisco Intelligent WAN (IWAN) application simplifies the provisioning of IWAN network profiles with simple business policies. The IWAN application defines business-level preferences by application or groups of applications in terms of the preferred path for hybrid WAN links. Doing so improves the application experience over any connection and saves telecom costs by leveraging cheaper WAN links.
Shadow rules are the rules that are never matched (usually because of the first rules). For example two access-list statements:
access-list 100 permit ip any any
access-list 100 deny tcp host A host B
Then the second access-list statement would never be matched because all traffic have been already allowed by the first statement. In this case we call statement 1 shadows statement 2.
Question 7
Which two (or three) are effects of local spanning tree? (Choose two)
A. Doubles the load
B. Doubles internal switch traffic
C. Prevents span destination
D. ?
Answer: unknown
Question 8
What is true about the default VLAN?
A. It is VLAN 1
B. It is always the same as Native VLAN
Question 9
Which command to see information about neighbors in OSPFv3?
A. show ipv6 ospf neighbors
B. show ipv6 interface brief
Question 10
Which two actions must you take to configure a LACP between two switches, S1 and S2? (Choose two)
A. Configure mode auto command on S1.
B. Configure mode passive command on S1.
C. Configure mode desirable command on S1.
D. Configure mode auto command on S2.
E. Configure mode desirable command on S2.
F. Configure mode active command on S2.
Question 11
How can QoS be implemented?
A. Only outbound
B. Only inbound
C. Inbound and outbound
Explanation
On the inbound path, a packet is classified before it is switched. On the outbound path, a packet is classified after it is switched.
At the inbound direction, QoS can do:
+ Input marking (class-based marking or Committed Access Rate (CAR))
+ Input policing (through a class-based policer or CAR)
At the outbound direction, QoS can do:
+ Output marking
+ Output policing (through a class-based policer or CAR)
+ Queueing (Class-Based Weighted Fair Queueing (CBWFQ) and Low Latency Queueing (LLQ)), and Weighted Random Early Detection (WRED)
Question 12
What do you need to reduce GRE fragmentation (Choose two)?
A. MTU 1360
B. MSS 1360
C. MTU 1400
D. MSS 1400
E. MTU 1500
Question 13
In OSPF or EIGRP, which of the following IPs will choose as router ID?
A. 192.168.x.x
B. 172.x.x.x
C. 172.x.x.x
D. 172.x.x.x
Question 14
How can you see the PPP authentication?
A. show running-config
B. show interface
C. show ip interface
Question 15
Which is the first step to configure OSPFv3 area 1?
A. (config)#ipv6 unicast-routing
B. (config)#router ospf ipv6 1
Question 16
A topology of host named X and Y connected to a switch and the switch was connected to a router as well. No other information (IP addresses, protocols, etc, nothing just the diagram). Host X cannot communicate with Host Y, why?
A. Host X has a broadcast IP address configured.
B. Host X has an invalid subnet mask.
C. Host Y has a network ID address configured.
D. Host Y has invalid IP and invalid subnet mask.
Answer: B
============================ New Questions added on 14th-July-2018 ============================
Question 17
A question about SVI and how to troubleshoot them (Choose three)
A. ASIC
B. Frame Size
C. IP routing
D. Encapsulation
E. Interfaces
F. ?
Answer: C D E
Question 18
When you use cloud services which service is more “exposed” to the cloud?
A. Desktop as a Service
B. Software as a Service
C. Infrastructure as a Service
D. Platform as a Service
Answer: B
Question 19
Question about Dynamic VPN? (choose three)
A. It can auto create IPSec tunnels
B. It allows dynamic addressing…
C. It does not need additional configuration on the hub for new spokes
D. It allows partial mesh topology
Answer: B C D
Question 20
Question for SNMPv3 what does this do? (choose two)
R1# snmp-server host 1.1.1.1 trap v3 auth md5 cisco
A. Sets the R1 password to cisco
B. Configures host 1.1.1.1 to receive informs
C. Configures host 1.1.1.1 to send informs
D. Configures host 1.1.1.1 to receive traps
E. Sets the host 1.1.1.1 password to cisco
Answer: D and A (although answer A is a bit unclear)
Explanation
The syntax of above command is shown below:
snmp-server host host-addr [informs | traps] [version {1 | 2c | 3 {auth | noauth | priv}}] community-string [udp–port port]
This command specify the recipient of an SNMP trap operation.
+ For host-addr, specify the name or Internet address of the host (the targeted recipient).
+ (Optional) Enter informs to send SNMP informs to the host.
+ (Optional) Enter traps (the default) to send SNMP traps to the host.
+ (Optional) Specify the SNMP version (1, 2c, or 3). Default is version 1. SNMPv1 does not support informs.
+ (Optional) For Version 3, select authentication level auth, noauth, or priv.
Note: The priv keyword is available only when the cryptographic software image is installed.
+ For community-string, when version 1 or version 2c is specified, enter the password-like community string sent with the notification operation. When version 3 is specified, enter the SNMPv3 username.
+ (Optional) For port, specify the UDP port of the notification host. Default is port 162.
Question 21
What are the differences between link state vs vector routing protocols? (Choose two)
A. Vector routing protocols are faster than link state protocols
B. Link state protocols are faster than vector routing protocols
C. Vector routing protocols take up more memory than link state protocols
D. Link state protocols take up more memory than vector routing protocols
Answer: B D
============================ New Questions added on 18th-Oct-2018 ============================
Question 22
Drag drop question.
Native vlan – Untagged
802.1Q – Trunk
Question 23
Drag drop question about TACACS+ and RADIUS.
Answer:
TACACS+ server:
Encrypts entire packet
Port 49
TCP
RADIUS Server:
Encrypts only password
Port 1812, 1813; 1645,1646
UDP
[am4show have=’p2;’]
Premium Member: You can try this sim with our simulator here.
[/am4show]
This task requires the use of various show commands from the CLI of Router1 to answer 5 multiple-choice questions. This does not require any configuration.
NOTE: The show running-configuration and the show startup-configuration commands have been disabled in this simulation.
To access the multiple-choice questions, click on the numbered boxes on the right of the top panel.
There are 5 multiple-choice questions with this task. Be sure to answer all 5 questions before leaving this item.
=========================New Questions added on 24th-Feb-2018============================
Premium Members: You can practice these questions with our quizzes first here.
Question 1
What two options are causes of network slowness that can result from inter-VLAN routing problem? (Choose two)
A. Root guard disabled on an etherchannel
B. Packet Loss
C. DTP disabled on a switchport
D. BPDU guard enabled on a switchport
E. Hardware forwarding issues
Answer: B E
Explanation
Causes for Network Slowness
Packet Loss
In most cases, a network is considered slow when higher-layer protocols (applications) require extended time to complete an operation that typically runs faster. That slowness is caused by the loss of some packets on the network, which causes higher-level protocols like TCP or applications to time out and initiate retransmission.
Hardware Forwarding Issues
With another type of slowness, caused by network equipment, forwarding (whether Layer 2 [L2] or L3) is performed slowly. This is due to a deviation from normal (designed) operation and switching to slow path forwarding. An example of this is when Multilayer Switching (MLS) on the switch forwards L3 packets between VLANs in the hardware, but due to misconfiguration, MLS is not functioning properly and forwarding is done by the router in the software (which drops the interVLAN forwarding rate significantly).
Question 2
Which two commands debug a PPPoE connection that has failed to establish? (Choose two)
A. debug ppp compression
B. debug ppp negotiation
C. debug dialer events
D. debug ppp cbcp
E. debug dialer packet
Answer: B E
Explanation
According to this link https://supportforums.cisco.com/t5/network-infrastructure-documents/troubleshooting-for-pppoe-connection-failure-part-1/ta-p/3147204
The following debug commands can be used to troubleshoot PPPoE connection that failed:
+ debug ppp authentication
+ debug ppp negotiation
+ debug pppoe event
The debug ppp negotiation command enables you to view the PPP negotiation transactions, identify the problem or stage when the error occurs, and develop a resolution.
We are not sure about the “debug dialer packet” command but it seems to be the most reasonable answer left.
Question 3
Which command do you enter to determine whether LACP is in use on a device?
A. Show port-channel summary
B. Show etherchannel summary
Answer: B
Explanation
In fact both of the answers are correct so maybe there is something wrong with this question. But we choose “show etherchannel summary” as it is the more popular command
Question 4
Which three commands do you use to verify that IPsec over a GRE tunnel is working properly? (Choose three)
A. clear crpto iskamp
B. ppp encrypt mppe auto
C. show crypto engine connections active
D. show crypto ipsec sa
E. show crypto isakmp sa
F. debug crypto isakmp
Answer: D E F
Question 5 (posted at Q.48 of https://www.9tut.net/new-updated-questions/new-icnd2v3-questions)
Which two types of cloud services may require you to alter the design of your network infrastructure? (Choose two)
A. Sudo as a Service
B. Platform as a Service
C. Infrastructure as a Service
D. Software as a Service
E. Business as a Service
Answer: B C
Explanation
+ SaaS (Software as a Service): SaaS uses the web to deliver applications that are managed by a third-party vendor and whose interface is accessed on the clients’ side. Most SaaS applications can be run directly from a web browser without any downloads or installations required, although some require plugins. In other words, SaaS are applications designed for end-users, delivered over web.
+ PaaS (Platform as a Service): are used for applications, and other development, while providing cloud components to software. What developers gain with PaaS is a framework they can build upon to develop or customize applications. PaaS makes the development, testing, and deployment of applications quick, simple, and cost-effective. With this technology, enterprise operations, or a third-party provider, can manage OSes, virtualization, servers, storage, networking, and the PaaS software itself. Developers, however, manage the applications. In other words, PaaS is a set of tools and services designed to make coding and deploying those applications quick and efficient.
+ IaaS (Infrastructure as a Service): self-service models for accessing, monitoring, and managing remote datacenter infrastructures, such as compute (virtualized or bare metal), storage, networking, and networking services (e.g. firewalls). Instead of having to purchase hardware outright, users can purchase IaaS based on consumption, similar to electricity or other utility billing. In other words, IaaS is the hardware and software (servers, storage, networks, operating systems) that powers PaaS & SaaS.

Only the two lower layers services (IaaS, PaaS) may require us to alter the design of the network infrastructure.
Question 6
Which purpose of the network command in the BGP configuration of a router is true?
A. It enables route advertisement in the BGP routing process on the router
B. It advertises any route in BGP with no additional configuration
C. It advertises a valid network as local to the autonomous system of a router
D. It indicates whether a neighbor supports route refresh
Answer: C
Question 7
Through with three states does a BGP routing process pass when it establishes a peering session?
A. open receive
B. inactive
C. active
D. connected
E. open sent
F. idle
Answer: C E F
Explanation
BGP forms a TCP session with neighbor routers called peers. The BGP session may report in the following states:
+ Idle
+ Connect
+ Active
+ OpenSent
+ OpenConfirm
+ Established
Reference: http://www.ciscopress.com/articles/article.asp?p=2756480&seqNum=4
Question 8
Which encryption method does CHAP authentication use for the peer response?
A. EAP
B. MD5
C. DES
D. DSS
E. AES
F. 3DES
Answer: B
Question 9
Which two characteristics of stacked switches are true? (Choose two)
A. They reduce management complexity
B. They are less scalable than modular switches
C. They can manage multiple ip addresses across multiple switches
D. They have a single management interface
E. Each unit in the stack can be assigned its own IP address
Answer: A D
Question 10
Which option describes a drawback of proxy ARP?
A. It overwrites MAC addresses
B. It can make it more difficult for the administrator to locale device misconfigurations
C. It dynamically establishes layer 2 tunneling protocol which increase network overhead
D. If proxy ARP is configured on multiple devices, the internal L2 network may become vulnerable to DDOS
Answer: D
Question 11
Which layer 2 attack is specifically mitigated by changing the native VLAN to an unused VLAN?
A. Double tagging
B. DHCP spoofing
C. VLAN spoofing
D. switch hopping
Answer: A
Explanation
Let us learn about double-tagging attack.
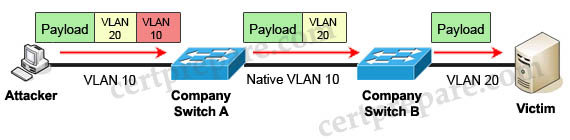
In double-tagging attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).
When the packet from the attacker reaches Switch A, Switch A only sees the first VLAN 10 and it matches with its native VLAN 10 so this VLAN tag is removed. Switch A forwards the frame out all links with the same native VLAN 10. Switch B receives the frame with an tag of VLAN 20 so it removes this tag and forwards out to the Victim computer.
Note: This attack only works if the trunk (between two switches) has the same native VLAN as the attacker.
According to this link http://www.ciscopress.com/articles/article.asp?p=2181837&seqNum=10
“The best approach to mitigating double-tagging attacks is to ensure that the native VLAN of the trunk ports is different from the VLAN of any user ports. In fact, it is considered a security best practice to use a fixed VLAN that is distinct from all user VLANs in the switched network as the native VLAN for all 802.1Q trunks.” -> Answer A is correct.
Question 12
Which feature or value must be configured to enable EIGRPv6?
A. Network statement
B. Shutdown feature
C. Router ID
D. Remote AS
Answer: C
Question 13
Which command do you enter to enable local authentication for MPPP on an interface?
A. l2tp authentication
B. username router password x1
C. ppp chap password password1
D. aaa authentication ppp default local
Answer: C
Explanation
Multilink PPP (also referred to as MP, MPPP, MLP, or Multilink) provides a method for spreading traffic across multiple physical WAN links while providing packet fragmentation and reassembly, proper sequencing, multivendor interoperability, and load balancing on inbound and outbound traffic.
Reference: https://www.cisco.com/c/en/us/support/docs/wan/point-to-point-protocol-ppp/10239-mppp-ddr.html
The command “aaa authentication ppp default local” is used to specify the local username database as the default method for user authentication but this command is configured under global configuration mode only, not on an interface.
Reference: https://www.cisco.com/c/en/us/td/docs/ios/12_2/security/configuration/guide/fsecur_c/scfathen.html
The command “username router password x1” is used under global configuration mode too.
So maybe the “ppp chap password…” command is the best choice here.
Question 14
Which options are the two differences between HSRP V1 and V2? (Choose two)
A. Only HSRPv2 can be configured to use authentication
B. Only HSRPv2 send hello packet to 224.0.0.2
C. Only HSRPv1 send hello packet to FF02:66
D. Only HSRPv1 can be configured with a group number of 4095
E. Only HSRPv2 can be configured with a group number of 4095
F. Only HSRPv2 send hello to 224.0.0.102
Answer: E F
Explanation
In HSRP version 1, group numbers are restricted to the range from 0 to 255. HSRP version 2 expands the group number range from 0 to 4095 -> E is correct.
HSRP version 2 uses the new IP multicast address 224.0.0.102 to send hello packets instead of the multicast address of 224.0.0.2, which is used by version 1 -> F is correct.
Question 15
For which reason can a GRE tunnel have an up/down status?
A. the tunnel source interface is up
B. a tunnel destination is undefined
C. the tunnel destination is routable via a route that is separate from the tunnel
D. tunnel has been shut down
Answer: B
Explanation
Normally, a P2P GRE Tunnel interface comes up as soon as it is configured with a valid tunnel source address or interface which is up and a tunnel destination IP address which is routable -> B is correct.
Question 16
Which utility do you use to view IP traffic that is switched through the router to locate erros in a TCP stream?
A. wireshark
B. packet debugging
C. ethereal
D. ping
E. traceroute
Answer: B
Explanation
Cisco routers provide a basic method of viewing IP traffic switched through the router called packet debugging. Packet debugging enables a user to determine whether traffic is travelling along an expected path in the network or whether there are errors in a particular TCP stream. Although in some cases packet debugging can eliminate the need for a packet analyzer, it should not be considered a replacement for this important tool.
Reference: https://www.cisco.com/en/US/docs/internetworking/troubleshooting/guide/tr1907.html
Question 17
Which command do you enter so that a port enters the forwarding state immediately when a PC is connected to it ?
A. spanning-tree portfast bpduguard default
B. spanning-tree portfast default
C. spanning-tree portfast trunk
D. no spanning tree portfas
Answer: B
Explanation
If there is a “spanning-tree portfast” answer then it will surely be a correct answer. If not then answer B is the most suitable one even though the “spanning-tree portfast default” command enables PortFast globally on all non-trunking ports, not a single port.
Question 18
Which term represents the minimum bandwidth provided in a metro Ethernet connection?
A. UNI
B. CIR
C. EVC
D. PIR
Answer: B
Explanation
Committed information rate (CIR): The minimum guaranteed data transfer rate agreed to by the routing device.
Question 19
Which three effects of using local span are true? (Choose three)
A. It doubles the load on the forwarding engine
B. It prevents span destination from using port security
C. It double internal switch traffic
D. It reduces the supervisor engine
E. It reduces the load on the switch fabric
Answer: A B C
Question 20
Which tree fields can be marked with QoS? (Choose three)
A. Header checksum
B. IP precedence
C. DSCP
D. total length
E. discard class
F. TTL
Answer: B C E
Explanation
For a single class, you can set operations on any two out of the following five fields: CoS, IP Precedence, DSCP, QoS Group, and Discard Class.
Question 21
Which two values are needed to run the APIC-EM ACL analysis tool?
A. Destination port
B. Source address
C. Protocol
D. Source port
E. Periodic refresh interval
F. Destination address
Answer: B F
Explanation
We must type the source and destination addresses. Other parameters are just optional.
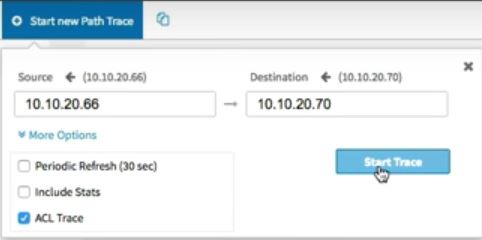
Question 22
In which two models can control plane functionality be implemented? (Choose two)
A. Dispersed
B. Distributed
C. Fragmented
D. Centralized
E. Allocated
Answer: B D
Explanation
Control Plane Function
In its simplest form, the control plane provides layer-2 MAC reachability and layer-3 routing information to network devices that require this information to make packet forwarding decisions. In the case of firewalls, the control plane would include stateful flow information for inspection. Control plane functionality can implemented as follows:
+ Distributed – Conventional routers and switches operate using distributed protocols for control, i.e. where each device makes its own decisions about what to do, and communicate relevant information to other devices for input into their decision making process. For example, the Spanning Tree Protocol (STP), Fabric Path, and routing protocols such as IS-IS and BGP provide distributed control of packet forwarding functionality to networking devices.
+ Centralized – In this case, a centralized controller provides the necessary information for a network element to make a decision. For example, these controller(s) instruct networking devices on where to forward packets by explicitly programming their MAC and FIBs.
Reference: https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Data_Center/VMDC/SDN/SDN.html#wp1440878
Question 23
Which PPPoE authentication method is the least secure?
A. CHAP
B. PAP
Answer: B
Question 24
What do you need to reduce with GRE tunnel? (Choose two)
A. PMTUD
B. MSS
C. MTU
Answer: B C
Question 25
Which choice permit congestion management on QOS? (Choose three)
Answer: FIFO CBWFQ PQ
Or
Which two QoS tools can provide congestion management? (Choose two)
A. CBWFQ
B. FRTS
C. CAR
D. PQ
E. PBR
Answer: A D
Explanation
This module discusses the types of queueing and queueing-related features (such as bandwidth management) which constitute the congestion management QoS features:
Class-based WFQ (CBWFQ): extends the standard WFQ functionality to provide support for user-defined traffic classes. For CBWFQ, you define traffic classes based on match criteria including protocols, access control lists (ACLs), and input interfaces. Packets satisfying the match criteria for a class constitute the traffic for that class.
Priority queueing (PQ): With PQ, packets belonging to one priority class of traffic are sent before all lower priority traffic to ensure timely delivery of those packets.
Note: Committed Access Rate (CAR) is only used for bandwidth limitation by dropping excessive traffic.
Question 26
Which three protocols can you use with APIC-EM path trace? (Choose three)
Answer: ECMP SNMP SMTP
Question 27
Drag the term on the left to its definition on the right (not all options are used)
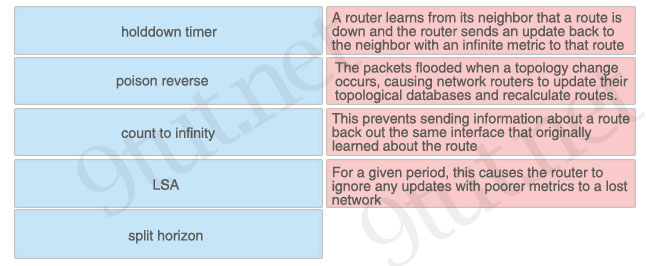
Answer:
+ poison reverse: A router learns from its neighbor that a route is down and the router sends an update back to the neighbor with an infinite metric to that route
+ LSA: The packets flooded when a topology change occurs, causing network routers to update their topological databases and recalculate routes
+ split horizon: This prevents sending information about a route back out the same interface that originally learned about the route
+ holddown timer: For a given period, this causes the router to ignore any updates with poorer metrics to a lost network
Question 28
Which three effects of using local span are true? (Choose three)
A. It doubles the load on the forwarding engine
B. It prevents span destination from using port security
C. It double internal switch traffic
D. It reduces the supervisor engine
E. It reduces the load on the switch fabric
Answer: A B C
=========================New Questions added on 29th-Mar-2018============================
Question 29
Which component of the Cisco SDN solution serves as the centralized management system?
A. Cisco OpenDaylight
B. Cisco ACI
C. Cisco APIC
D. Cisco IWAN
Answer: C
Explanation
Cisco Application Policy Infrastructure Controller (APIC)
The infrastructure controller is the main architectural component of the Cisco ACI solution. It is the unified point of automation and management for the Cisco ACI fabric, policy enforcement, and health monitoring. The APIC appliance is a centralized, clustered controller that optimizes performance and unifies operation of physical and virtual environments. The controller manages and operates a scalable multitenant Cisco ACI fabric.
Question 30
Which mode are in PAgP? (Choose two)
A. Auto
B. Desirable
C. Active
D. Passive
E. On
Answer: A B
Explanation
There are two PAgP modes:
| Auto | Responds to PAgP messages but does not aggressively negotiate a PAgP EtherChannel. A channel is formed only if the port on the other end is set to Desirable. This is the default mode. |
| Desirable | Port actively negotiates channeling status with the interface on the other end of the link. A channel is formed if the other side is Auto or Desirable. |
The table below lists if an EtherChannel will be formed or not for PAgP:
| PAgP | Desirable | Auto |
| Desirable | Yes | Yes |
| Auto | Yes | No |
Question 31
Which LACP mode sends offer to connect device?
A. active
B. passive
C. desirable
D. auto
Answer: A
Question 32
Which feature can prevent switch to become Root Bridge?
A. VTP
B. DTP
C. Root Guard
C. BPDU Guard filter
Answer: C
Question 33
what does this monitor session command mean?
monitor session 16 source interface Gi0/11
A. source monitoring session – unidirection
B. destination monitoring session – bi-direction
C. source monitoring session – bi-direction
Answer: C
Question 34
Which IPv6 ACL rules are applied as first?
A. ACL port filter
B. ACL router filter
C. ?
D. ?
Answer: A
=========================New Questions added on 8th-May-2018============================
Question 35
Drag drop about southbound and northbound APIs.
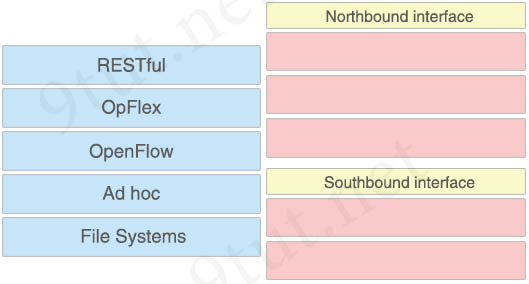
Answer:
Northbound interface:
+ RESTful
+ Ad hoc
+ File Systems
Southbound interface:
+ OpFlex
+ OpenFlow
Explanation
Cisco OpFlex is a southbound protocol in a software-defined network (SDN) designed to facilitate the communications between the SDN Controller and the infrastructure (switches and routers). The goal is to create a standard that enables policies to be applied across physical and virtual switches/routers in a multi-vendor environment.
Question 36
Which command will you use to show the snmp version and collection of users?
Answer: show snmp group
Explanation
To display the names of configured SNMP groups, the security model being used, the status of the different views, and the storage type of each group, use the show snmp group command in privileged EXEC mode.
=========================New Questions added on 15th-May-2018============================
Question 37
Drag and drop the BGP states from the left to the matching definitions on the right.
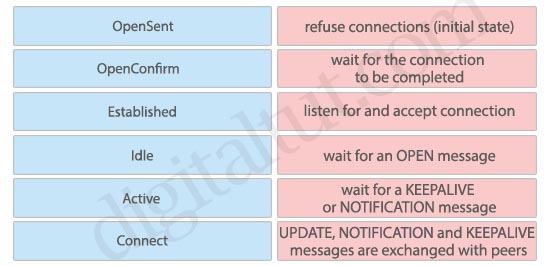
Answer:
+ OpenSent: wait for an OPEN message
+ OpenConfirm: wait for a KEEPALIVE or NOTIFICATION message
+ Established: UPDATE, NOTIFICATION and KEEPALIVE messages are exchanged with peers
+ Idle: refuse connections
+ Active: listen for and accept connection
+ Connect: wait for the connection to be completed
Explanation
The order of the BGP states is: Idle -> Connect -> (Active) -> OpenSent -> OpenConfirm -> Established
+ Idle: No peering; router is looking for neighbor. Idle (admin) means that the neighbor relationship has been administratively shut down.
+ Connect: TCP handshake completed.
+ Active: BGP tries another TCP handshake to establish a connection with the remote BGP neighbor. If it is successful, it will move to the OpenSent state. If the ConnectRetry timer expires then it will move back to the Connect state. Note: Active is not a good state.
+ OpenSent: An open message was sent to try to establish the peering.
+ OpenConfirm: Router has received a reply to the open message.
+ Established: Routers have a BGP peering session. This is the desired state.
Reference: http://www.ciscopress.com/articles/article.asp?p=1565538&seqNum=3
Question 38
Which three HSRP multicast messages are sent between the devices? (Choose three)
A. Ping
B. Hello
C. Coup
D. Resign
Answer: B C D
Explanation
With HSRP, three types of multicast messages are sent between the devices:
+ Hello – The hello message is sent between the active and standby devices (by default, every 3 seconds). If the standby device does not hear from the active device (via a hello message) in about 10 seconds, it will take over the active role.
+ Resign – The resign message is sent by the active HSRP device when it is getting ready to go offline or relinquish the active role for some other reason. This message tells the standby router to be ready and take over the active role.
+ Coup – The coup message is used when a standby router wants to assume the active role (preemption).
Reference: http://www.pearsonitcertification.com/articles/article.aspx?p=2141271
Question 39
How will HSRP choose the active router? (Choose two)
A. Highest ip add
B. Highest MAC address
C. Configured priority
D. Lowest bridge ID
Answer: A C
Question 40 (similar like this about preempt delay)
You administer a network that uses two routers, R1 and R2, configured as an HSRP group to provide redundancy for the gateway. Router R1 is the active router and has been configured as follows:
| R1#configure terminal R1(config)#interface fa0/0 R1(config-if)#ip address 10.10.0.5 255.255.255.0 R1(config-if)#standby 1 priority 150 R1(config-if)#standby preempt delay minimum 50 R1(config-if)#standby 1 track interface fa0/2 15 R1(config-if)#standby 1 ip 10.10.0.20 |
Which of the following describes the effect the “standby preempt delay minimum 50” command will have on router R1?
A. The HSRP priority for router R1 will increase to 200.
B. Router R1 will become the standby router if the priority drops below 50.
C. The HSRP priority for router R1 will decrease to 50 points when Fa0/2 goes down.
D. Router R1 will wait 50 seconds before attempting to preempt the active router.
Answer: D
Explanation
If R1, for some reason, loses its active state, the “standby preempt delay minimum 50” command will cause R1 to wait 50 seconds before it tries to get the active state again -> D is correct.
Question 41
Drag drop about Southbound & Northbound
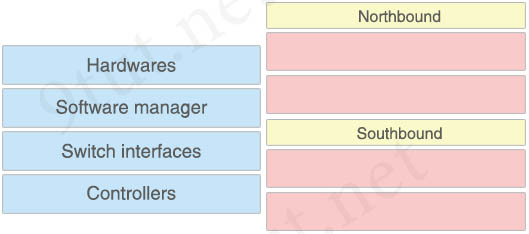
Answer:
Southbound
+ Hardwares
+ Switch interfaces
Northbound
+ Software manager
+ Controllers
Question 1
What is the default read-only (RO) mode of SNMP community string?
A. Public
B. Private
C. Cisco
D. Secret
Answer: A
Question 2
What is the output of the command “show snmp engineID”?
Answer: Local SNMP engineID and remote engineID
Question 3
Which protocol HSRP uses to interchange?
A. PPP
B. PPPoE
C. BPDU
D. Hello
Answer: D
Question 4
When does your enterprise require high-speed broadband internet?
A. P2P file sharing
B. Cloud computing
C. IaaS
D. vSAN expansion
E. upgrade IOS
F. resource-intensive application
Answer: B
Question 5
Responses from the TACACS+ daemon?
Answer: ACCEPT, REJECT, ERROR, CONTINUE
Question 6
What protocol CGMP is NOT compatible with?
A. HSRPv1
B. HSRPv2
Answer: A
Explanation
HSRPv1 uses the multicast address 224.0.0.2 to send hello packets, which can conflict with Cisco Group Management Protocol (CGMP) leave processing. You cannot enable HSRPv1 and CGMP at the same time; they are mutually exclusive.
Question 7
Which about GRE tunnel is true?
Answer: sends in plain text
Question 8
Which algorithm routing protocols are using?
Answer:
+ Dijkstra -> OSPF
+ Bellman-Ford -> RIP
+ DUAL -> EIGRP
Question 9
Which command is used to remove VLANs from trunk?
Answer: switchport trunk allowed vlan remove <VLANs>
Question 10
Which command is used to configure IPv6 peer for BGP?
Answer: neighbor xxxx remote-as xxxx
Question 11
Which command is used to verify GRE tunnel connectivity?
Answer: (not sure but maybe) traceroute OR “show tunnel interface tunnel <tunnel-ID>”
=============================New Questions added on 12nd-Feb-2018=============================
Question 12
Which of the following provide the highest availability?
A. full mesh
B. partial mesh
C. hub and spoke
Answer: A
Question 13
What can MPLS provide? (Choose two)
A. Authentication Header
B. secure payload of packet with ESP
C. VPN
D. CoS
Answer: A C
Question 14
Which ACL rules are applied as first?
A. Port filter
B. Router filter
C. VLAN filter
D. MAC filter
Answer: A
Explanation
In merge mode, the ACLs are applied in the following order:
1. PACL for the ingress port
2. VACL for the ingress VLAN
3. VACL for the egress VLAN
Port ACLs are similar to Router ACLs but are supported on physical interfaces and configured on Layer 2 interfaces on a switch. Port ACL supports only inbound traffic filtering. Port ACL can be configured as three type access lists: standard, extended, and MAC-extended
Reference: http://www.ciscopress.com/articles/article.asp?p=1181682&seqNum=4
Question 15
Which is true about IGP? (Choose two)
A. May use Bellman-Ford algorithm
B. May use Dijkstra Algorithm
C. Can be used between company and ISP
D. Can be used between router – Firewall – router
Answer: A B
Question 16 (maybe same as Question 9)
Which command will remove vlan 10 from trunk?
A. switchport trunk allowed vlan remove 10
B. switchport trunk allowed vlan add 10
C. switchport trunk allowed vlan except 10
Answer: A
Note: Another command to do this task is switchport trunk allowed vlan {all VLANS except 10}
Question 17
Troubleshooting connectivity between two devices. How will you start? (Choose two)
A. ping
B. extended ping with source
C. traceroute
D. something like connect to source’s next hop and do ping to destination
Answer: A C
Question 18
Which is true about keep-alive interval?
A. if was modified – should be equal on both side
B. have to apply on both side
Answer: A
Explanation
Since HDLC keepalives are ECHOREQ type keepalives, the keepalive frequency is important and it is recommended that they match up exactly on both sides. If the timers are out of sync, the sequence numbers start to get out of order. For example, if you set one side to 10 seconds and the other to 25 seconds, it will still allow the interface to remain up as long as the difference in frequency is not sufficient to cause the sequence numbers to be off by a difference of three.
Question 19
Which of the command enable PPP over Ethernet?
A. pppoe-client dial-pool-number
B. ppoe enable
Answer: B
Question 20
Which command immediately put port into forwarding state?
A. spanning-tree portfast default
B. spanning-tree portfast bpduguard default
Answer: A
Explanation
Portfast is often configured on switch ports that connect to hosts. Interfaces with Portfast enabled will go to forwarding state immediately without passing the listening and learning state. Therefore it can save about 30 to 45 seconds to transition through these states.
To enable this feature, configure this command under interface mode:
Switch(config-if)#spanning-tree portfast
or we can use the spanning-tree portfast default global configuration command to globally enable the Port Fast feature on all nontrunking ports.
Question 21
Which feature can prevent switch to become Root Bridge?
A. VTP
B. DTP
C. Root Guard
C. BPDU Guard filter
Answer: C
Question 22
Which mode of VTP will only forward messages and ignore updates?
A. Client
B. Server
C. Transparent
Answer: C
Question 23
Which is correct about APIC-EM Path trace ACL? (Choose two)
A. It checks only ingress interface
B. It checks only egress interface
C. It checks ingress and egress interface
D. If finds ACL which deny traffic, will stop …
Answer: C and ?
Question 24
If TRAP in SNMP is not working, where can be issue?
A. Trap was not set
B. wasn’t put command “snmp-server enable traps”
C. SNMP server host has not configured inform messages
Answer: B
Explanation
Maybe this question wants to ask why TRAP is not sent after setting the trap.
If you do not enter an snmp-server enable traps command, no notifications controlled by this command are sent. In order to configure the router to send these SNMP notifications, you must enter at least one snmp-server enable traps command. If you enter the command with no keywords, all notification types are enabled. If you enter the command with a keyword, only the notification type related to that keyword is enabled. In order to enable multiple types of notifications, you must issue a separate snmp-server enable traps command for each notification type and notification option.
Note: For SNMP configuration please read https://www.9tut.com/simple-network-management-protocol-snmp-tutorial
Question 25
Which of the following two things does QOS provide? (Choose two)
Answer: checksum and inspection (not sure)
Question 26
Which of the following is true about Link state protocol?
Answer: (maybe) instant update
Question 27
Which of the following is true about Distance Vector?
Answer: (maybe) periodic update
Question 28
How can BGP advertise routes?
Answer: put command “network prefix mask DDN-mask”
Question 29
What is the default DTP mode?
A. Dynamic Desirable
B. Dynamic Auto
C. On
D. Off
Answer: B
Note: This question is same as Question 4 of https://www.9tut.net/icnd2-200-105/dtp-questions
Explanation
The Dynamic Trunking Protocol (DTP) is used to negotiate forming a trunk between two Cisco devices.
In fact this question is unclear as it does not ask about a specific switch model. The default DTP configuration for Cisco Catalyst 2960 and 3560 switches is dynamic auto while older 3550 switches run Dynamic Desirable as the default mode. So in this question we should follow the “newer” switches (which is “dynamic auto” mode).
New switches are only set to “dynamic auto” mode by default so they are safer as they do not try to form a trunk aggressively.
Therefore in this question “dynamic auto” is the best choice.
Reference: http://www.ciscopress.com/articles/article.asp?p=2181837&seqNum=8
Question 30
Which three options are benefits of using TACACS+ on a device? (Choose three)
A. It ensures that user activity is untraceable.
B. It provides a secure accounting facility on the device.
C. device-administration packets are encrypted in their entirely.
D. It allows the user to remotely access devices from other vendors.
E. It allows the users to be authenticated against a remote server.
F. It supports access-level authorization for commands.
Answer: C E F
Explanation
TACACS+ (and RADIUS) allow users to be authenticated against a remote server -> E is correct.
TACACS+ encrypts the entire body of the packet but leaves a standard TACACS+ header -> C is correct.
TACACS+ supports access-level authorization for commands. That means you can use commands to assign privilege levels on the router -> F is correct.
Note:
By default, there are three privilege levels on the router.
+ privilege level 1 = non-privileged (prompt is router>), the default level for logging in
+ privilege level 15 = privileged (prompt is router#), the level after going into enable mode
+ privilege level 0 = seldom used, but includes 5 commands: disable, enable, exit, help, and logout
Question 31
What prevents DDOS (Denial-of-service attack) attack?
Answer: DHCP snooping
Question 32
What allows two neighbor to establish EIGRP adjacency?
Answer: (recommended) same AS number, same subnet, same K values, same mask
Question 33
What command to check if a trunk is enable on an interface?
Answer: show int trunk
Question 34
What command will remove IPv6 OSPF address on an interface?
Answer: no ipv6 ospf 1 area x
Question 35
Why security of RADIUS may be compromised?
Answer: only the password is encrypted
Question 36
Which layer is ACL APIC-EM Path running on?
A. Layer 1
B. Layer 2
C. Layer 3
D. Layer 4
Answer: D
Question 37
What command will statically configure Etherchannel?
A. Desirable
B. Auto
C. On
D. Passive
Answer: C
Question 38
Which two options describe benefits of aggregated chassis technology? (Choose two)
A. It reduces management overhead
B. Switches can be located anywhere regardless of there physical location
C. It requires only one IP address per VLAN
D. It requires only three IP addresses per VLAN
E. It supports HSRP VRRP GLBP
F. It support redundant configuration files
Answer: A C
Explanation
Chassis aggregation is a Cisco technology to make multiple switches operate as a single switch. It is similar to stacking but meant for powerful switches (like the 6500 and 6800 series switches). Chassis aggregation is often used in the core layer and distribution layer (while switching stacking is used for access layer).
The books do not mention about the benefits of chassis aggregation but they are the same as switch stacking.
+ The stack would have a single management IP address.
+ The engineer would connect with Telnet or SSH to one switch (with that one management IP address), not multiple switches.
+ One configuration file would include all interfaces in all physical switches.
+ STP, CDP, VTP would run on one switch, not multiple switches.
+ The switch ports would appear as if all are on the same switch.
+ There would be one MAC address table, and it would reference all ports on all physical switches.
Reference: CCNA Routing and Switching ICND2 200-105 Official Cert Guide
VSS is a chassis aggregation technology but it is dedicated for Cisco Catalyst 6500 Series Switches. VSS increases operational efficiency by simplifying the network, reducing switch management overhead by at least 50 percent -> A is correct
Single point of management, IP address, and routing instance for the Cisco Catalyst 6500 virtual switch
+ Single configuration file and node to manage. Removes the need to configure redundant switches twice with identical policies.
+ Only one gateway IP address is required per VLAN, instead of the three IP addresses per VLAN used today -> C is correct while D is not correct.
+ Removes the need for Hot Standby Router Protocol (HSRP), Virtual Router Redundancy Protocol (VRRP), and Gateway Load Balancing Protocol (GLBP)-> so maybe E is not correct.
Question 39
When troubleshooting client DNS issues, which two tasks must you perform? (Choose two)
A. Ping a public website IP address.
B. Ping the DNS Server.
C. Determine whether a DHCP address has been assigned.
D. Determine whether the hardware address is correct.
E. Determine whether the name servers have been configured
Answer: B E
Explanation
Complete these steps to troubleshoot this problem:
Ensure the router can reach the DNS server. Ping the DNS server from the router using its IP address, and make sure that the ip name-server command is used to configure the IP address of the DNS server on the router.
Reference: https://www.cisco.com/c/en/us/support/docs/ip/domain-name-system-dns/24182-reversedns.html
Question 40
What routing protocol use first-hand information?
A. link-state
B. distance-vector
C. path-vector
D. other
Answer: A
Explanation
The information available to a distance vector router has been compared to the information available from a road sign. Link state routing protocols are like a road map. A link state router cannot be fooled as easily into making bad routing decisions, because it has a complete picture of the network. The reason is that unlike the routing-by-rumor approach of distance vector, link state routers have firsthand information from all their peer routers. Each router originates information about itself, its directly connected links, and the state of those links (hence the name). This information is passed around from router to router, each router making a copy of it, but never changing it. The ultimate objective is that every router has identical information about the internetwork, and each router will independently calculate its own best paths.
Reference: http://www.ciscopress.com/articles/article.asp?p=24090&seqNum=4
Question 41
Two features of the extended ping command? (Choose two)
A. It can send a specific number of packet
B. It can send packet from specified interface of IP address
C. It can resolve the destination host name
D. It can ping multiple host at the same time
Answer: A B
Explanation
There are many options to choose when using extended ping. Below shows the options that we can choose:
In which:
+ Repeat count [5]: Number of ping packets that are sent to the destination address. The default is 5 -> A is correct.
+ Source address or interface: The interface or IP address of the router to use as a source address for the probes -> B is correct.
For more information about extended ping, please read: http://www.cisco.com/c/en/us/support/docs/ip/routing-information-protocol-rip/13730-ext-ping-trace.html
Question 42
Which statement about IPv6 link-local addresses is true?
A. They must be configured on all IPv6 interface
B. They must be globally unique
C. They must be manually configured
D. They are advertised globally on the network
Answer: A
Explanation
Link-local addresses refer only to a particular physical link and are used for addressing on a single link for purposes such as automatic address configuration and neighbor discovery protocol. Link-local addresses can be used to reach the neighboring nodes attached to the same link. The nodes do not need a globally unique address to communicate. Routers will not forward datagram using link-local addresses. All IPv6 enabled interfaces have a link-local unicast address.
A link-local address is an IPv6 unicast address that can be automatically configured on any interface using the link-local prefix FE80::/10 (1111 1110 10) and the interface identifier in the modified EUI-64 format. Link-local addresses are not necessarily bound to the MAC address (configured in a EUI-64 format). Link-local addresses can also be manually configured in the FE80::/10 format using the “ipv6 address link-local” command.
Reference: http://www.cisco.com/c/en/us/support/docs/ip/ip-version-6-ipv6/113328-ipv6-lla.html
In summary, if you do not configure a link-local on an IPv6 enabled interface, it will automatically use the FE80::/10 and the interface identifier in the modified EUI-64 format to form a link-local address.
Question 43
Which command can you enter on a switch to determine the current SNMP security model?
A. snmp-server contact
B. show snmp pending
C. show snmp group
D. show snmp engineID
Answer: C
Explanation
Three security models are available: SNMPv1, SNMPv2c, and SNMPv3. The security model combined with the security level determine the security mechanism applied when the SNMP message is processed.
The command “show snmp group” displays the names of groups on the router and the security model, the status of the different views, and the storage type of each group. Below is an example of this command.
=========================New Questions added on 24th-Feb-2018============================
Question 44
What two options are causes of network slowness that can result from inter-VLAN routing problem? (Choose two)
A. Root guard disabled on an etherchannel
B. Packet Loss
C. DTP disabled on a switchport
D. BPDU guard enabled on a switchport
E. Hardware forwarding issues
Answer: B E
Explanation
Causes for Network Slowness
Packet Loss
In most cases, a network is considered slow when higher-layer protocols (applications) require extended time to complete an operation that typically runs faster. That slowness is caused by the loss of some packets on the network, which causes higher-level protocols like TCP or applications to time out and initiate retransmission.
Hardware Forwarding Issues
With another type of slowness, caused by network equipment, forwarding (whether Layer 2 [L2] or L3) is performed slowly. This is due to a deviation from normal (designed) operation and switching to slow path forwarding. An example of this is when Multilayer Switching (MLS) on the switch forwards L3 packets between VLANs in the hardware, but due to misconfiguration, MLS is not functioning properly and forwarding is done by the router in the software (which drops the interVLAN forwarding rate significantly).
Question 45
Which two commands debug a PPPoE connection that has failed to establish? (Choose two)
A. debug ppp compression
B. debug ppp negotiation
C. debug dialer events
D. debug ppp cbcp
E. debug dialer packet
Answer: B E
Explanation
According to this link https://supportforums.cisco.com/t5/network-infrastructure-documents/troubleshooting-for-pppoe-connection-failure-part-1/ta-p/3147204
The following debug commands can be used to troubleshoot PPPoE connection that failed:
+ debug ppp authentication
+ debug ppp negotiation
+ debug pppoe event
The debug ppp negotiation command enables you to view the PPP negotiation transactions, identify the problem or stage when the error occurs, and develop a resolution.
We are not sure about the “debug dialer packet” command but it seems to be the most reasonable answer left.
Question 46
Which command do you enter to determine wheter LACP is in use on a device?
A. Show port-channel summary
B. Show etherchannel summary
Answer: B
Question 47
Which three commands do you use to verify that IPsec over a GRE tunnel is working properly? (Choose three)
A. clear crpto iskamp
B. ppp encrypt mppe auto
C. show crypto engine connections active
D. show crypto ipsec sa
E. show crypto isakmp sa
F. debug crypto isakmp
Answer: D E F
Question 48
Which two types of cloud services may require you to alter the design of your network infrastructure? (Choose two)
A. Sudo as a service
B. Platform as a service
C. Infrastructure as a service
D. Software as a service
E. Business as a service
Answer: B C
Explanation
There are only three types of cloud services. These different types of cloud computing services delivery models are called
infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS).
Question 49
Which purpose of the network command in the BGP configuration of a router is true?
A. It enables route advertisement in the BGP routing process
B. It advertises any route in BGP with no additional configuration
C. It advertises a valid network as local to the autonomous system of a router
Answer: C
Question 50
Through with three states does a BGP routing process pass when it establishes a peering session?
A. open receive
B. inactive
C. active
D. connected
E. open sent
F. idle
Answer: C E F
Explanation
BGP forms a TCP session with neighbor routers called peers. The BGP session may report in the following states:
+ Idle
+ Connect
+ Active
+ OpenSent
+ OpenConfirm
+ Established
Reference: http://www.ciscopress.com/articles/article.asp?p=2756480&seqNum=4
Question 51
Which encryption method does CHAP authentication use for the peer response?
A. EAP
B. MD5
C. DES
D. DSS
E. AES
F. 3DES
Answer: B
Question 52
Which two characteristics of stacked switches are true? (Choose two)
A. They reduce management complexity
B. They are less scalable than modular switches
C. They can manage multiple ip addresses across multiple switches
D. They have a single management interface
E. Each unit in the stack can be assigned its own IP address
Answer: A D
Question 53
Which option describes a drawback of proxy ARP?
A. It overwrites MAC addresses
B. It can make it more difficult for the administrator to locale device misconfigurations
C. It dynamically establishes layer 2 tunneling protocol which increase network overhead
D. If proxy ARP is configured on multiple devices , the internal L2 network may become vulnerable to DDOS
Answer: D
Question 54
Which layer 2 attack is specifically mitigated by changing the native VLAN to an unused VLAN?
A. Double tagging
B. DHCP spoofing
C. VLAN spoofing
D. switch hopping
Answer: A
Explanation
Let us learn about double-tagging attack.

In double-tagging attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).
When the packet from the attacker reaches Switch A, Switch A only sees the first VLAN 10 and it matches with its native VLAN 10 so this VLAN tag is removed. Switch A forwards the frame out all links with the same native VLAN 10. Switch B receives the frame with an tag of VLAN 20 so it removes this tag and forwards out to the Victim computer.
Note: This attack only works if the trunk (between two switches) has the same native VLAN as the attacker.
According to this link http://www.ciscopress.com/articles/article.asp?p=2181837&seqNum=10
“The best approach to mitigating double-tagging attacks is to ensure that the native VLAN of the trunk ports is different from the VLAN of any user ports. In fact, it is considered a security best practice to use a fixed VLAN that is distinct from all user VLANs in the switched network as the native VLAN for all 802.1Q trunks.” -> Answer A is correct.
Question 55
Which feature or value must be configured to enable EIGRPv6?
Answer: Router id
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Note: If you are not sure about OSPF, please read my OSPF tutorial first.
Question
This item contains several questions that you must answer. You can view these questions by clicking on the corresponding button to the left. Changing questions can be accomplished by clicking the numbers to the left of each question. In order to complete the questions, you will need to refer to the topology.
To gain access to the topology, click on the topology button at the bottom of the screen. When you have finished viewing the topology, you can return to your questions by clicking on the Questions button to the left.
Each of the windows can be minimized by clicking on the [-]. You can also reposition a window by dragging it by the title bar.
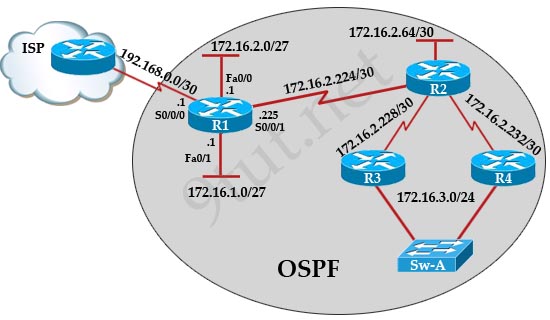
Question 1
[am4show have=’p2;’]R1 is configured with the default configuration of OSPF.
From the following list of IP addresses configured on R1, which address will the OSPF process select as the router ID?
A. 192.168.0.1
B. 172.16.1.1
C. 172.16.2.1
D. 172.16.2.225
Answer: A[/am4show]
Explanation
The Router ID (RID) is an IP address used to identify the router and is chosen using the following sequence:
+ The highest IP address assigned to a loopback (logical) interface.
+ If a loopback interface is not defined, the highest IP address of all active router’s physical interfaces will be chosen.
+ The router ID can be manually assigned
In this case, because a loopback interface is not configured so the highest active IP address 192.168.0.1 is chosen as the router ID.
Question 2
[am4show have=’p2;’]After the network has converged, what type of messaging, if any, occurs between R3 and R4?
A. No messages are exchanged.
B. Hellos are sent every 10 seconds.
C. The full database from each router is sent every 30 seconds.
D. The routing table from each router is sent every 60 seconds.
Answer: B[/am4show]
Explanation
HELLO messages are used to maintain adjacent neighbors so even when the network is converged, hellos are still exchanged. On broadcast and point-to-point links, the default is 10 seconds, on NBMA the default is 30 seconds.
Although OSPF is a link-state protocol but the full database from each router is sent every 30 minutes (not seconds) -> C and D are not correct.
Question 3
[am4show have=’p2;’]To allow or prevent load balancing to network 172.16.3.0/24, which of the following commands could be used in R2? (Choose two)
A. R2(config-if)#clock rate
B. R2(config-if)#bandwidth
C. R2(config-if)#ip ospf cost
D. R2(config-if)#ip ospf priority
E. R2(config-router)#distance ospf
Answer: B C[/am4show]
Question 4
[am4show have=’p2;’]R1 is unable to establish an OSPF neighbor relationship with R3. What are possible reasons for this problem? (Choose two)
A. All of the routers need to be configured for backbone Area 1
B. R1 and R2 are the DR and BDR, so OSPF will not establish neighbor adjacency with R3
C. A static route has been configured from R1 to R3 and prevents the neighbor adjacency from being established.
D. The hello and dead interval timers are not set to the same values on R1 and R3
E. EIGRP is also configured on these routers with a lower administrative distance
F. R1 and R3 are configured in different areas
Answer: D F[/am4show]
Question 5
[am4show have=’p2;’]OSPF is configured using default classful addressing. With all routers and interfaces operational, how many networks will be in the routing table of R1 that are indicated to be learned by OSPF?
A. 2
B. 3
C. 4
D. 5
E. 6
F. 7
Answer: C[/am4show]
Explanation
Although OSPF is configured using default classful addressing but OSPF is a link-state routing protocol so it will always send the subnet mask of each network in their advertised routes. Therefore R1 will learn the the complete subnets. Four networks list below will be in the routing table of R1:
+ 172.16.2.64/30
+ 172.16.2.228/30
+ 172.16.2.232/30
+ 172.16.3.0/24
Note: Other networks will be learned as “Directly connected” networks (marked with letter “C”)
Question 1
[am4show have=’p2;’]Syslog – what does not belong?
A. host name
B. severity
C. timestamp
D. message
Answer: A[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which statement about named ACLs is true?
A. They support standard and extended ACLs.
B. They are used to filter usernames and passwords for Telnet and SSH.
C. They are used to filter Layer 7 traffic.
D. They support standard ACLs only.
E. They are used to rate limit traffic destined to targeted networks.
Answer: A[/am4show]
Explanation
The syntax of a named ACL is:
| ip access-list {standard | extended} {name | number} |
Therefore we can configure a standard acl with keyword “standard” and configure an extended acl with keyword “extended”. For example this is how to configure an named extended access-list:
| Router(config)#ip access-list extended in_to_out permit tcp host 10.0.0.1 host 187.100.1.6 eq telnet |
Question 2
[am4show have=’p2;’]Which identification number is valid for an extended ACL?
A. 1
B. 64
C. 99
D. 100
E. 299
F. 1099
Answer: D[/am4show]
Explanation
Below is the range of standard and extended access list:
| Access list type | Range |
| Standard | 1-99, 1300-1999 |
| Extended | 100-199, 2000-2699 |
In most cases we only need to remember 1-99 is dedicated for standard access lists while 100 to 199 is dedicated for extended access lists.
Question 3
[am4show have=’p2;’]What three pieces of information can be used in an extended access list to filter traffic? (Choose three)
A. VLAN number
B. TCP or UDP port numbers
C. source switch port number
D. source IP address and destination IP address
E. protocol
F. source MAC address and destination MAC address
Answer: B D E[/am4show]
Explanation
The syntax of an extended acl is:
| access-list access-list-number {permit | deny} protocol source-IP {source-mask} destination-IP {destination-mask} [eq destination-port] |
-> We can define protocol, source & destination IP addresses, destination port number.
For example, we will create an extended ACL that will permit FTP traffic (port 20, 21) from network 10.0.0.0/8 to reach 187.100.1.6 but deny other traffic to go through:
Router(config)#access-list 101 permit tcp 10.0.0.0 0.255.255.255 187.100.1.6 0.0.0.0 eq 21
Router(config)#access-list 101 permit tcp 10.0.0.0 0.255.255.255 187.100.1.6 0.0.0.0 eq 20
Question 4
[am4show have=’p2;’]Which statement about access lists that are applied to an interface is true?
A. you can apply only one access list on any interface
B. you can configure one access list, per direction, per layer 3 protocol
C. you can place as many access lists as you want on any interface
D. you can configure one access list, per direction, per layer 2 protocol
Answer: B[/am4show]
Explanation
We can have only 1 access list per protocol, per direction and per interface. It means:
+ We can not have 2 inbound access lists on an interface
+ We can have 1 inbound and 1 outbound access list on an interface
Question 5
[am4show have=’p2;’]When you are troubleshooting an ACL issue on a router, which command can help you to verify which interfaces are affected by the ACL?
A. show ip access-lists
B. show access-lists
C. show interface
D. show ip interface
E. list ip interface
Answer: D[/am4show]
Question 6
[am4show have=’p2;’]In which solution is a router ACL used?
A. filtering packets that are passing through a router
B. to change the default administrative distance of a route in the route table
C. protecting a server from unauthorized access
D. controlling path selection, based on the route metric
Answer: A[/am4show]
Question 7
[am4show have=’p2;’]Refer to the exhibit.
| R1# show access-lists Extended IP access list 175 10 deny tcp any any time-range nonworkhours (active) 20 permit tcp any any time-range workhours (inactive) |
While you troubleshoot a connectivity issue to a PC behind R1, you enter the show access-lists command to generate this output. Which reason for the problem is most likely true?
A. The permit all ACL entry on R1 is inactive.
B. The ACL of R1 is misconfigured.
C. A deny all ACL entry is currently active on R1.
D. An implicit deny is causing R1 to block network traffic.
Answer: D[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which two circumstances can cause collision domain issues on VLAN domain? (Choose two)
A. duplex mismatches on Ethernet segments in the same VLAN
B. multiple errors on switchport interfaces
C. congestion on the switch inband path
D. a failing NIC in an end device
E. an overloaded shared segment
Answer: A C[/am4show]
Explanation
On an Ethernet connection, a duplex mismatch is a condition where two connected devices operate in different duplex modes, that is, one operates in half duplex while the other one operates in full duplex. Duplex mismatch can easily cause collision domain issue as the device that operates in full duplex mode turns off CSMA/CD. So it is eager to send data immediately without checking if the link is free to use -> A is correct.
An “inband path” is the path which provides path for management traffic (like CDP, VTP, PAgP…) but we are not sure why congestion on the switch inband path can cause collision domain issues. Maybe congestion on inband path prevents the JAM signal (sent when a collision occurs on the link) to be sent correctly on the link.
Question 2
[am4show have=’p2;’]Which three statements are typical characteristics of VLAN arrangements? (Choose three)
A. A new switch has no VLANs configured.
B. Connectivity between VLANs requires a Layer 3 device.
C. VLANs typically decrease the number of collision domains.
D. Each VLAN uses a separate address space.
E. A switch maintains a separate bridging table for each VLAN.
F. VLANs cannot span multiple switches.
Answer: B D E[/am4show]
Explanation
By default, all ports on a new switch belong to VLAN 1 (default & native VLAN). There are also some well-known VLANs (for example: VLAN 1002 for fddi-default; VLAN 1003 for token-ring…) configured by default -> A is not correct.
To communicate between two different VLANs we need to use a Layer 3 device like router or Layer 3 switch -> B is correct.
VLANs don’t affect the number of collision domains, they are the same -> C is not correct. Typically, VLANs increase the number of broadcast domains.
We must use a different network (or sub-network) for each VLAN. For example we can use 192.168.1.0/24 for VLAN 1, 192.168.2.0/24 for VLAN 2 -> D is correct.
A switch maintains a separate bridging table for each VLAN so that it can send frame to ports on the same VLAN only. For example, if a PC in VLAN 2 sends a frame then the switch look-ups its bridging table and only sends frame out of its ports which belong to VLAN 2 (it also sends this frame on trunk ports) -> E is correct.
We can use multiple switches to expand VLAN -> F is not correct.
Question 3
[am4show have=’p2;’]What is the default VLAN on an access port?
A. 0
B. 1
C. 10
D. 1024
Answer: B[/am4show]
Explanation
If we configure an access port as follows:
| Switch(config)#interface fa0/1 Switch(config-if)#switchport mode access |
Then this interface, by default, will belong to VLAN 1. Of course we can assign another VLAN to this port via the “switchport access vlan {vlan-number}” command.
Question 4
[am4show have=’p2;’]What are three valid reasons to assign ports to VLANs on a switch? (Choose three)
A. to make VTP easier to implement
B. to isolate broadcast traffic
C. to increase the size of the collision domain
D. to allow more devices to connect to the network
E. to logically group hosts according to function
F. to increase network security
Answer: B E F[/am4show]
Question 5
[am4show have=’p2;’]What command can you enter to assign an interface to the default VLAN?
A. Switch(config-if)# switchport access vlan 1
B. Switch(config-if)# switchport trunk native vlan 1
C. Switch(config-if)# vlan 1
D. Switch(config)# int vlan 1
Answer: A[/am4show]
Explanation
The “switchport access vlan 1” assigns VLAN 1 to this interface. In fact, by default all access ports belong to VLAN 1 so this command is hidden in the switch configuration.
Question 6
[am4show have=’p2;’]Which statement about switch access ports is true?
A. They drop packets with 802.1Q tags.
B. A VLAN must be assigned to an access port before it is created.
C. They can receive traffic from more than one VLAN with no voice support
D. By default, they carry traffic for VLAN 10.
Answer: A[/am4show]
Explanation
A VLAN does not need to be assigned to any port -> B is not correct.
An access port can only receive traffic from one VLAN -> C is not correct.
If not assigned to a specific VLAN, an access port carries traffic for VLAN 1 by default -> D is not correct.
An access port will drop packets with 802.1Q tags -> A is correct. Notice that 802.1Q tags are used to packets moving on trunk links.
Question 7
[am4show have=’p2;’]Which feature facilitates the tagging of frames on a specific VLAN?
A. Routing
B. hairpinning
C. switching
D. encapsulation
Answer: D[/am4show]
Question 8
[am4show have=’p2;’]Which three options are types of slow Vlan connectivity? (Choose three)
A. Slow broadcast domain connectivity.
B. Slow routing domain connectivity.
C. Slow default gateway connectivity.
D. Slow application domain connectivity.
E. Slow collision domain connectivity.
F. Slow inter Vlan connectivity.
Answer: A E F[/am4show]
Question 9
[am4show have=’p2;’]Which statement about VLAN configuration is true?
A. The switch must be in config-vlan mode before you configure an extended VLAN.
B. Dynamic inter-vlan routing is supported on VLAN 2 through VLAN 4064.
C. A switch in VTP transparent mode saves the VLAN database to the running configuration only.
D. The switch must be in VTP server or transparent mode before you configure a VLAN.
Answer: D[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which statement about DTP is true?
A. It uses the native VLAN.
B. It negotiates a trunk link after VTP has been configured.
C. It uses desirable mode by default.
D. It sends data on VLAN 1.
Answer: D[/am4show]
Explanation
Control traffic like CDP, DTP, PAgP, and VTP uses VLAN 1 to operate, even if you change the native VLAN.
Question 2
[am4show have=’p2;’]How can you disable DTP on a switch port?
A. Configure the switch port as a trunk.
B. Add an interface on the switch to a channel group.
C. Change the operational mode to static access.
D. Change the administrative mode to access.
Answer: A (no correct answer, in fact)[/am4show]
Explanation
Although some books and websites said DTP is disabled if the switch port is configured as trunk or access mode (via the command “switchport mode trunk” or “switchport mode access”) but in fact DTP is still running in these modes. Please read at http://packetlife.net/blog/2008/sep/30/disabling-dynamic-trunking-protocol-dtp/. The only way to disable DTP on a switch port is to use the “switchport nonegotiate” command. But notice this command can only be used after configuring that switch port in “trunk” or “access” mode.
Therefore this is a question with no correct answer but if we have to choose an answer, we will choose answer A. At least it is correct in theory.
Question 3
[am4show have=’p2;’]Which three statements about DTP are true? (Choose three)
A. It is enabled by default.
B. It is a universal protocol.
C. It is a proprietary protocol.
D. It is disabled by default.
E. It is a Layer 3-based protocol.
F. It is a Layer 2-based protocol.
Answer: A C F[/am4show]
Question 4
[am4show have=’p2;’]What is the DTP’s default mode in a switch?
A. ON
B. OFF
C. Dynamic Desirable
D. Dynamic Auto
Answer: D[/am4show]
Explanation
The Dynamic Trunking Protocol (DTP) is used to negotiate forming a trunk between two Cisco devices.
In fact this question is unclear as it does not ask about a specific switch model. The default DTP configuration for Cisco Catalyst 2960 and 3560 switches is dynamic auto while older 3550 switches run Dynamic Desirable as the default mode. So in this question we should follow the “newer” switches (which is “dynamic auto” mode).
New switches are only set to “dynamic auto” mode by default so they are safer as they do not try to form a trunk aggressively.
Therefore in this question “dynamic auto” is the best choice.
Reference: http://www.ciscopress.com/articles/article.asp?p=2181837&seqNum=8
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Refer to the exhibit:
What can be determined about the interfaces of the Main_Campus router from the output shown?
A. The LAN interfaces are configured on different subnets.
B. Interface FastEthernet 0/0 is configured as a trunk.
C. The Layer 2 protocol of interface Serial 0/1 is NOT operational.
D. The router is a modular router with five FastEthernet interfaces.
E. Interface FastEthernet 0/0 is administratively deactivated.
Answer: B[/am4show]
Explanation
We can’t confirm answer B is totally correct but all other answers are wrong so B is the best choice.
+ We only have 1 LAN interface on Main_Campus router with 4 subinterfaces -> answer A is not correct (although it is a bit unclear).
+ The “protocol” column of interface Serial0/1 is up so its Layer 2 is operating correctly -> answer C is not correct.
+ This router has only 1 FastEthernet interface -> answer D is not correct.
+ The “status” column of Fa0/0 is currently “up” so it is operating -> answer E is not correct.
Question 2
[am4show have=’p2;’]Refer to the exhibit. A technician has configured the FastEthernet 0/1 interface on Sw11 as an access link in VLAN 1. Based on the output from the show vlan brief command issued on Sw12, what will be the result of making this change on Sw11?
A. Only the hosts in VLAN 1 on the two switches will be able to communicate with each other.
B. The hosts in all VLANs on the two switches will be able to communicate with each other.
C. Only the hosts in VLAN 10 and VLAN 15 on the two switches will be able to communicate with each other.
D. Hosts will not be able to communicate between the two switches.
Answer: D[/am4show]
Explanation
Fa0/1 of Switch11 is configured as an access link of VLAN1 so only frames in VLAN1 can communicate through the two switches. But from the output above we see there is no interface belongs to VLAN1 on Switch12 -> no hosts can communicate between the two switches.
Question 3
[am4show have=’p2;’]Which three of these statements regarding 802.1Q trunking are correct? (Choose three)
A. 802.1Q native VLAN frames are untagged by default.
B. 802.1Q trunking ports can also be secure ports.
C. 802.1Q trunks can use 10 Mb/s Ethernet interfaces.
D. 802.1Q trunks require full-duplex, point-to-point connectivity.
E. 802.1Q trunks should have native VLANs that are the same at both ends.
Answer: A C E[/am4show]
Question 4
[am4show have=’p2;’]Which three commands must you enter to create a trunk that allows VLAN 20? (Choose three)
A. Switch(config-if)#switchport mode dynamic auto
B. Switch(config-if)#switchport mode trunk
C. Switch(config-if)#switchport trunk allowed vlan 20
D. Switch(config-if)#switchport mode dynamic desirable
E. Switch(config-if)#switchport trunk encapsulation dot1q
F. Switch(config-if)#switchport trunk native vlan 20
Answer: B C E[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Refer to the exhibit. While troubleshooting a switch, you executed the “show interface port-channel 1 etherchannel” command and it returned this output. Which information is provided by the Load value?
A. the percentage of use of the link
B. the preference of the link
C. the session count of the link
D. the number source-destination pairs on the link
Answer: D[/am4show]
Explanation
The way EtherChannel load balancing works is that the switch assigns a hash result from 0-7 based on the configured hash method ( load balancing algorithm ) for the type of traffic. This hash result is commonly called as Result Bundle Hash (RBH).
Now we need to convert Load value from Hexadecimal to Binary numbers. Therefore:
+ Gi1/1: 36 (Hex) = 00110110 (Bin) -> Bits 1, 2, 4, 5 are chosen (read from right to left, start from 0)
+ Gi1/2: 84 (Hex) = 10000100 (Bin) -> Bits 2, 7 are chosen
+ Gi1/3: 16 (Hex) = 00010110 (Bin) -> Bits 1, 2, 4 are chosen
Therefore if the RBH is 5, it will choose Gi1/1. If RBH is 4, it will choose Gi1/1 and Gi1/3 interfaces. If RBH is 2 it will choose all three above interfaces. And the bit sharing ratio is 3:3:2 (from “No of bits” column) hence two links has higher probability of getting utilized as compared to the third link.
Question 2
[am4show have=’p2;’]Which two actions must you take to configure a PAgP EtherChannel between two switches, S1 and S2? (Choose two)
A. Configure the channel-group 1 mode auto command on S1.
B. Configure the channel-group 1 mode desirable command on S2.
C. Configure the channel-group 1 mode active command on S2.
D. Configure the channel-group 1 mode on command on S2.
E. Configure the channel-group 1 mode active command on S1.
Answer: A B[/am4show]
Explanation
In PAgP we only have two modes: auto and desirable.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which protocol provides a method of sharing VLAN configuration information between two Cisco switch?
A. VTP
B. 802.1Q
C. RSTP
D. STP
Answer: A[/am4show]
Question 2
[am4show have=’p2;’]Which protocol supports sharing the VLAN configuration between two or more switches?
A. multicast
B. STP
C. VTP
D. split-horizon
Answer: C[/am4show]
Explanation
With VTP, switches can learn VLAN configuration of other switches dynamically.
Question 3
[am4show have=’p2;’]What are two characteristics of a switch that is configured as a VTP client? (Choose two)
A. If a switch that is configured to operate in client mode cannot access a VTP server, then the switch reverts to transparent mode.
B. The local vlan configuration is updated only when an update that has a higher configuration revision number is received.
C. VTP advertisements are not forwarded to neighboring switches that are configured in vtp transparent mode.
D. When switches in vtp client mode are rebooted, they send a vtp advertisement request to the vtp servers.
E. VTP client is the default vtp mode.
F. On switches that are configured to operate in client mode, vlans can be created, deleted or renamed locally.
Answer: B D[/am4show]
Question 4
[am4show have=’p2;’]Which three statements about VTP features are true? (Choose three)
A. VTP works at Layer 3 of the OSI model and requires that a management VLAN IP address be configured.
B. When properly configured, VTP minimizes VLAN misconfigurations and configuration inconsistencies.
C. When properly configured, VTP maintains VLAN configuration consistency and accelerates trunk link negotiation.
D. Each broadcast domain on a switch can have its own unique VTP domain.
E. VTP pruning is used to increase available bandwidth in trunk links.
F. To configure a switch to be part of two VTP domains, each domain must have its own passwords.
G. Client, server, and transparent are valid VTP modes.
Answer: B E G[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which IEEE standard does PVST+ use to tunnel information?
A. 802.1x
B. 802.1q
C. 802.1w
D. 802.1s
Answer: B[/am4show]
Explanation
Cisco developed PVST+ to allow strolling numerous STP instances, even over an 802.1Q network via the use of a tunneling mechanism. PVST+ utilizes Cisco gadgets to hook up with a Mono Spanning Tree area to a PVST+ region. No particular configuration is needed to attain this. PVST+ affords assist for 802.1Q trunks and the mapping of a couple of spanning trees to the single spanning tree of popular 802.1Q switches strolling Mono Spanning Tree.
Question 2
[am4show have=’p2;’]What is one benefit of PVST+?
A. PVST+ reduces the CPU cycles for all the switches in the network.
B. PVST+ automatically selects the root bridge location, to provide optimization.
C. PVST+ allows the root switch location to be optimized per vlan.
D. PVST+ supports Layer 3 load balancing without loops.
Answer: C[/am4show]
Explanation
Per VLAN Spanning Tree (PVST) maintains a spanning tree instance for each VLAN configured in the network. It means a switch can be the root bridge of a VLAN while another switch can be the root bridge of other VLANs in a common topology. For example, Switch 1 can be the root bridge for Voice data while Switch 2 can be the root bridge for Video data. If designed correctly, it can optimize the network traffic.
Question 3
[am4show have=’p2;’]Which spanning-tree feature places a port immediately into a forwarding stated?
A. BPDU guard
B. PortFast
C. loop guard
D. UDLD
E. Uplink Fast
Answer: B[/am4show]
Explanation
When you enable PortFast on the switch, spanning tree places ports in the forwarding state immediately, instead of going through the listening, learning, and forwarding states.
Question 4
[am4show have=’p2;’]If primary and secondary root switches with priority 16384 both experience catastrophic losses, which tertiary switch can take over?
A. a switch with priority 20480
B. a switch with priority 8192
C. a switch with priority 4096
D. a switch with priority 12288
Answer: A[/am4show]
Explanation
This is a tricky question. We know the switch with lowest value of priority is elected the root switch. Therefore in this question the switches with priority of 4096, 8192, 12288 (which are lower than the current value of the root bridge 16384) are not joining the root bridge election by somehow. The only suitable answer is the switch with priority 20480 will become the root bridge.
Question 5
[am4show have=’p2;’]Which factors generate bridge ID? (Choose two)
A. MAC address
B. IP Address
C. STP Priority
D. Bridge Priority
Answer: A D[/am4show]
Explanation
The switches compare their Bridge ID with each other to find out who will be the root bridge. The root bridge is the bridge with the lowest bridge ID.
Bridge ID = Bridge Priority + MAC Address
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which process is associated with spanning-tree convergence?
A. determining the path cost
B. electing designated ports
C. learning the sender bridge ID
D. assigning the port ID
Answer: B[/am4show]
Explanation
SPT must performs three steps to provide a loop-free network topology:
1. Elects one root bridge
2. Select one root port per nonroot bridge
3. Select one designated port on each network segment -> Answer B is correct.
Question 2
[am4show have=’p2;’]Which term describes a spanning-tree network that has all switch ports in either the blocking or forwarding state?
A. redundant
B. spanned
C. provisioned
D. converged
Answer: D[/am4show]
Explanation
Spanning Tree Protocol convergence (Layer 2 convergence) happens when bridges and switches have transitioned to either the forwarding or blocking state. When layer 2 is converged, root bridge is elected and all port roles (Root, Designated and Non-Designated) in all switches are selected.
Question 3
[am4show have=’p2;’]Refer to the exhibit. Which switch provides the spanning-tree designated port role for the network segment that services the printers?
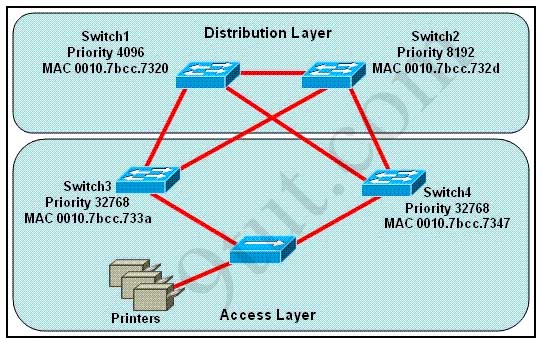
A. Switch1
B. Switch2
C. Switch3
D. Switch4
Answer: C[/am4show]
Explanation
First, the question asks what switch services the printers, so it can be Switch 3 or Switch 4 which is connected directly to the Printers.
Next, by comparing the MAC address of Switch 3 and Switch 4 we found that the MAC of Switch 3 is smaller. Therefore the interface connected to the Printers of Switch 3 will become designated interface and the interface of Switch 4 will be blocked. The picture below shows the roles of all ports:
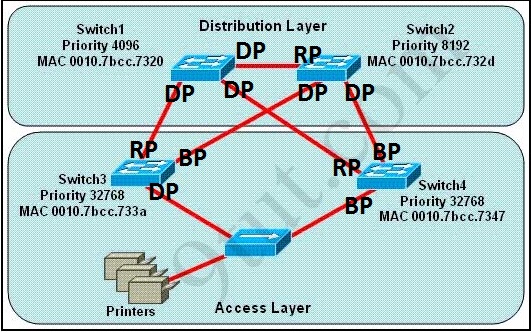
DP: Designated Port
RP: Root Port
BP: Blocked Port
(Please notice that Switch 1 will become the root bridge because of its lowest priority, not Switch 3)
Question 4
[am4show have=’p2;’]If primary and secondary root switches with priority 16384 both experience catastrophic losses, which tertiary switch can take over?
A. a switch with priority 20480
B. a switch with priority 8192
C. a switch with priority 4096
D. a switch with priority 12288
Answer: A[/am4show]
Explanation
This is a tricky question. We know the switch with lowest value of priority is elected the root switch. Therefore in this question the switches with priority of 4096, 8192, 12288 (which are lower than the current value of the root bridge 16384) are not joining the root bridge election by somehow. The only suitable answer is the switch with priority 20480 will become the root bridge.
Question 5
[am4show have=’p2;’]What kind of data message is send to elect the root bridge?
A. BPDU
B. Segment
C. Packets
D. Hello
Answer: A[/am4show]
Question 6
[am4show have=’p2;’]Which type does a port become when it receives the best BPDU on a bridge?
A. the backup port
B. the root port
C. the designated port
D. the alternate port
Answer: B[/am4show]
Question 7
[am4show have=’p2;’]Which value can you modify to configure a specific interface as the preferred forwarding interface?
A. the VLAN priority
B. the hello time
C. the port priority
D. the interface number
Answer: C[/am4show]
Question 8
[am4show have=’p2;’]Which VLAN bridge priority value is assigned by the set spantree root command?
A. 8192
B. 16384
C. 28672
D. 32768
Answer: A[/am4show]
Question 9
[am4show have=’p2;’]Which two statements about the spanning-tree bridge ID are true? (Choose two)
A. It is composed of a 4-bit bridge priority and a 12-bit system ID extension.
B. The bridge ID is transmitted in the IP header to elect the root bridge.
C. The system ID extension is a value between 1 and 4095.
D. It is composed of an 8-bit bridge priority and a 16-bit system ID extension.
E. The bridge priority must be incremented in blocks of 4096.
Answer: A E[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Refer to the exhibit. Each of these four switches has been configured with a hostname, as well as being configured to run RSTP. No other configuration changes have been made. Which three of these show the correct RSTP port roles for the indicated switches and interfaces? (Choose three)
A. SwitchA, Fa0/2, designated
B. SwitchA, Fa0/1, root
C. SwitchB, Gi0/2, root
D. SwitchB, Gi0/1, designated
E. SwitchC, Fa0/2, root
F. SwitchD, Gi0/2, root
Answer: A B F[/am4show]
Explanation
The question says “no other configuration changes have been made” so we can understand these switches have the same bridge priority. Switch C has lowest MAC address so it will become root bridge and 2 of its ports (Fa0/1 & Fa0/2) will be designated ports -> E is incorrect.
Because SwitchC is the root bridge so the 2 ports nearest SwitchC on SwitchA (Fa0/1) and SwitchD (Gi0/2) will be root ports -> B and F are correct.
Now we come to the most difficult part of this question: SwitchB must have a root port so which port will it choose? To answer this question we need to know about STP cost and port cost.
In general, “cost” is calculated based on bandwidth of the link. The higher the bandwidth on a link, the lower the value of its cost. Below are the cost values you should memorize:
| Link speed | Cost |
| 10Mbps | 100 |
| 100Mbps | 19 |
| 1 Gbps | 4 |
SwitchB will choose the interface with lower cost to the root bridge as the root port so we must calculate the cost on interface Gi0/1 & Gi0/2 of SwitchB to the root bridge. This can be calculated from the “cost to the root bridge” of each switch because a switch always advertises its cost to the root bridge in its BPDU. The receiving switch will add its local port cost value to the cost in the BPDU.
In the exhibit you also see FastEthernet port is connecting to GigabitEthernet port. In this case GigabitEthernet port will operate as a FastEthernet port so the link can be considered as FastEthernet to FastEthernet connection.
One more thing to notice is that a root bridge always advertises the cost to the root bridge (itself) with an initial value of 0.
Now let’s have a look at the topology again

SwitchC advertises its cost to the root bridge with a value of 0. Switch D adds 19 (the cost value of 100Mbps link although the port on Switch D is GigabitEthernet port) and advertises this value (19) to SwitchB. SwitchB adds 4 (the cost value of 1Gbps link) and learns that it can reach SwitchC via Gi0/1 port with a total cost of 23. The same process happens for SwitchA and SwitchB learns that it can reach SwitchC via Gi0/2 with a total cost of 38 -> Switch B chooses Gi0/1 as its root port -> D is not correct.
Now our last task is to identify the port roles of the ports between SwitchA & SwitchB. It is rather easy as the MAC address of SwitchA is lower than that of SwitchB so Fa0/2 of SwitchA will be designated port while Gi0/2 of SwitchB will be alternative port -> A is correct but C is not correct.
Below summaries all the port roles of these switches:
+ DP: Designated Port (forwarding state)
+ RP: Root Port (forwarding state)
+ AP: Alternative Port (blocking state)
Question 2
[am4show have=’p2;’]Refer to the exhibit. At the end of an RSTP election process, which access layer switch port will assume the discarding role?
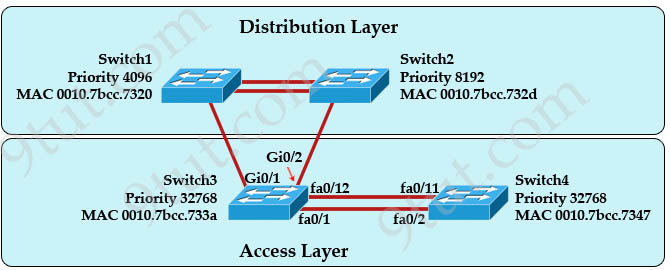
A. Switch3, port fa0/1
B. Switch3, port fa0/12
C. Switch4, port fa0/11
D. Switch4, port fa0/2
E. Switch3, port Gi0/1
Answer: C[/am4show]
Explanation
In this question, we only care about the Access Layer switches (Switch3 & 4). Switch 3 has a lower bridge ID than Switch 4 (because the MAC of Switch3 is smaller than that of Switch4) so both ports of Switch3 will be in forwarding state. The alternative port will surely belong to Switch4.
Switch4 will need to block one of its ports to avoid a bridging loop between the two switches. But how does Switch4 select its blocked port? Well, the answer is based on the BPDUs it receives from Switch3. A BPDU is superior than another if it has:
1. A lower Root Bridge ID
2. A lower path cost to the Root
3. A lower Sending Bridge ID
4. A lower Sending Port ID
These four parameters are examined in order. In this specific case, all the BPDUs sent by Sswitch3 have the same Root Bridge ID, the same path cost to the Root and the same Sending Bridge ID. The only parameter left to select the best one is the Sending Port ID (Port ID = port priority + port index). In this case the port priorities are equal because they use the default value, so Switch4 will compare port index values, which are unique to each port on the switch, and because Fa0/12 is inferior to Fa0/1, Switch4 will select the port connected with Fa0/1 (of Switch3) as its root port and block the other port -> Port fa0/11 of Switch4 will be blocked (discarding role).
If you are still not sure about this question, please read my RSTP tutorial.
Question 3
[am4show have=’p2;’]At which layer of the OSI model is RSTP used to prevent loops?
A. data link
B. network
C. physical
D. transport
Answer: A[/am4show]
Question 4
[am4show have=’p2;’]Which three statements about RSTP are true? (Choose three)
A. RSTP significantly reduces topology reconvening time after a link failure.
B. RSTP expands the STP port roles by adding the alternate and backup roles.
C. RSTP port states are blocking, discarding, learning, or forwarding.
D. RSTP provides a faster transition to the forwarding state on point-to-point links than STP does.
E. RSTP also uses the STP proposal-agreement sequence.
F. RSTP uses the same timer-based process as STP on point-to-point links.
Answer: A B D[/am4show]
Question 5
[am4show have=’p2;’]Which two switch states are valid for 802.1w? (Choose two)
A. listening
B. backup
C. disabled
D. learning
E. discarding
Answer: D E[/am4show]
Explanation
IEEE 802.1w is Rapid Spanning Tree Protocol (RSTP). There are only three port states left in RSTP that correspond to the three possible operational states. The 802.1D disabled, blocking, and listening states are merged into the 802.1w discarding state.
* Discarding – the port does not forward frames, process received frames, or learn MAC addresses – but it does listen for BPDUs (like the STP blocking state)
* Learning – receives and transmits BPDUs and learns MAC addresses but does not yet forward frames (same as STP).
* Forwarding – receives and sends data, normal operation, learns MAC address, receives and transmits BPDUs (same as STP).
Question 6
[am4show have=’p2;’]Which two of these statements regarding RSTP are correct? (Choose two)
A. RSTP cannot operate with PVST+.
B. RSTP defines new port roles.
C. RSTP defines no new port states.
D. RSTP is a proprietary implementation of IEEE 802.1D STP.
E. RSTP is compatible with the original IEEE 802.1D STP.
Answer: B E[/am4show]
Question 7
[am4show have=’p2;’]Which two states are the port states when RSTP has converged? (choose two)
A. discarding
B. learning
C. disabled
D. forwarding
E. listening
Answer: A D[/am4show]
Explanation
RSTP only has 3 port states that are discarding, learning and forwarding. When RSTP has converged there are only 2 port states left: discarding and forwarding.
Question 8
[am4show have=’p2;’]Refer to the exhibit:
Why has this switch not been elected the root bridge for VLAN1?
A. It has more than one internee that is connected to the root network segment.
B. It is running RSTP while the elected root bridge is running 802.1d spanning tree.
C. It has a higher MAC address than the elected root bridge.
D. It has a higher bridge ID than the elected root bridge.
Answer: D[/am4show]
Explanation
As we can see from the output above, the priority of the root bridge is 20481 while that of the local bridge is 32769.
Question 9
[am4show have=’p2;’]Refer to the exhibit. The output that is shown is generated at a switch. Which three of these statements are true? (Choose three)
A. All ports will be in a state of discarding, learning or forwarding.
B. Thirty VLANs have been configured on this switch.
C. The bridge priority is lower than the default value for spanning tree.
D. All interfaces that are shown are on shared media.
E. All designated ports are in a forwarding state.
F. The switch must be the root bridge for all VLANs on this switch.
Answer: A C E[/am4show]
Explanation
From the output, we see that all ports are in Designated role (forwarding state) -> A and E are correct.
The command “show spanning-tree vlan 30″ only shows us information about VLAN 30. We don’t know how many VLAN exists in this switch -> B is not correct.
The bridge priority of this switch is 24606 which is lower than the default value bridge priority 32768 -> C is correct.
All three interfaces on this switch have the connection type “p2p”, which means Point-to-point environment – not a shared media -> D is not correct.
The only thing we can specify is this switch is the root bridge for VLAN 30 but we can not guarantee it is also the root bridge for other VLANs -> F is not correct.
Question 10
[am4show have=’p2;’]Refer to the exhibit. Each of these four switches has been configured with a hostname, as well as being configured to run RSTP. No other configuration changes have been made. Which three of these show the correct RSTP port roles for the indicated switches and interfaces? (Choose three)

A. SwitchA, Fa0/2, designated
B. SwitchA, Fa0/1, root
C. SwitchB, Gi0/2, root
D. SwitchB, Gi0/1, designated
E. SwitchC, Fa0/2, root
F. SwitchD, Gi0/2, root
Answer: A B F[/am4show]
Explanation
The question says “no other configuration changes have been made” so we can understand these switches have the same bridge priority. Switch C has lowest MAC address so it will become root bridge and 2 of its ports (Fa0/1 & Fa0/2) will be designated ports -> E is incorrect.
Because SwitchC is the root bridge so the 2 ports nearest SwitchC on SwitchA (Fa0/1) and SwitchD (Gi0/2) will be root ports -> B and F are correct.
Now we come to the most difficult part of this question: SwitchB must have a root port so which port will it choose? To answer this question we need to know about STP cost and port cost.
In general, “cost” is calculated based on bandwidth of the link. The higher the bandwidth on a link, the lower the value of its cost. Below are the cost values you should memorize:
| Link speed | Cost |
| 10Mbps | 100 |
| 100Mbps | 19 |
| 1 Gbps | 4 |
SwitchB will choose the interface with lower cost to the root bridge as the root port so we must calculate the cost on interface Gi0/1 & Gi0/2 of SwitchB to the root bridge. This can be calculated from the “cost to the root bridge” of each switch because a switch always advertises its cost to the root bridge in its BPDU. The receiving switch will add its local port cost value to the cost in the BPDU.
In the exhibit you also see FastEthernet port is connecting to GigabitEthernet port. In this case GigabitEthernet port will operate as a FastEthernet port so the link can be considered as FastEthernet to FastEthernet connection.
One more thing to notice is that a root bridge always advertises the cost to the root bridge (itself) with an initial value of 0.
Now let’s have a look at the topology again

SwitchC advertises its cost to the root bridge with a value of 0. Switch D adds 19 (the cost value of 100Mbps link although the port on Switch D is GigabitEthernet port) and advertises this value (19) to SwitchB. SwitchB adds 4 (the cost value of 1Gbps link) and learns that it can reach SwitchC via Gi0/1 port with a total cost of 23. The same process happens for SwitchA and SwitchB learns that it can reach SwitchC via Gi0/2 with a total cost of 38 -> Switch B chooses Gi0/1 as its root port -> D is not correct.
Now our last task is to identify the port roles of the ports between SwitchA & SwitchB. It is rather easy as the MAC address of SwitchA is lower than that of SwitchB so Fa0/2 of SwitchA will be designated port while Gi0/2 of SwitchB will be alternative port -> A is correct but C is not correct.
Below summaries all the port roles of these switches:

+ DP: Designated Port (forwarding state)
+ RP: Root Port (forwarding state)
+ AP: Alternative Port (blocking state)
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Refer to the exhibit. Given the output shown from this Cisco Catalyst 2950, what is the most likely reason that interface FastEthernet 0/10 is not the root port for VLAN 2?
Switch# show spanning-tree interface fastethernet0/10
A. This switch has more than one interface connected to the root network segment in VLAN 2.
B. This switch is running RSTP while the elected designated switch is running 802.1d Spanning Tree.
C. This switch interface has a higher path cost to the root bridge than another in the topology.
D. This switch has a lower bridge ID for VLAN 2 than the elected designated switch.
Answer: C[/am4show]
Question 2
[am4show have=’p2;’]Which option describes how a switch in rapid PVST+ mode responds to a topology change?
A. It immediately deletes dynamic MAC addresses that were learned by all ports on the switch.
B. It sets a timer to delete all MAC addresses that were learned dynamically by ports in the same STP instance.
C. It sets a timer to delete dynamic MAC addresses that were learned by all ports on the switch.
D. It immediately deletes all MAC addresses that were learned dynamically by ports in the same STP instance.
Answer: D[/am4show]
Explanation
Rapid PVST+—This spanning-tree mode is the same as PVST+ except that is uses a rapid convergence based on the IEEE 802.1w standard. To provide rapid convergence, the rapid PVST+ immediately deletes dynamically learned MAC address entries on a per-port basis upon receiving a topology change. By contrast, PVST+ uses a short aging time for dynamically learned MAC address entries.
Question 3
[am4show have=’p2;’]Which port state is introduced by Rapid-PVST?
A. learning
B. listening
C. discarding
D. forwarding
Answer: C[/am4show]
Explanation
PVST+ is based on IEEE802.1D Spanning Tree Protocol (STP). But PVST+ has only 3 port states (discarding, learning and forwarding) while STP has 5 port states (blocking, listening, learning, forwarding and disabled). So discarding is a new port state in PVST+.
Question 4
[am4show have=’p2;’]Which command enables RSTP on a switch?
A. spanning-tree mode rapid-pvst
B. spanning-tree uplinkfast
C. spanning-tree backbonefast
D. spanning-tree mode mst
Answer: A[/am4show]
Question 5
[am4show have=’p2;’]Refer to the exhibit. Which statement is true?
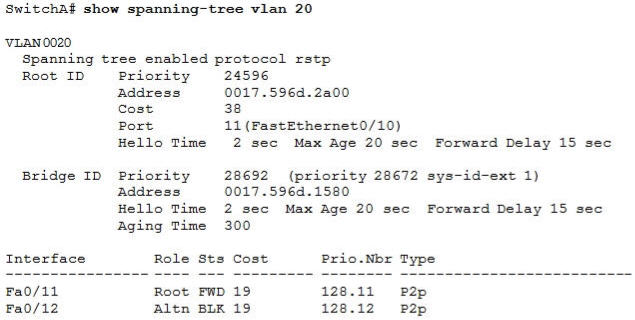
A. The Fa0/11 role confirms that SwitchA is the root bridge for VLAN 20.
B. VLAN 20 is running the Per VLAN Spanning Tree Protocol.
C. The MAC address of the root bridge is 0017.596d.1580.
D. SwitchA is not the root bridge, because not all of the interface roles are designated.
Answer: D[/am4show]
Explanation
Only non-root bridge can have root port. Fa0/11 is the root port so we can confirm this switch is not the root bridge -> A is not correct.
From the output we learn this switch is running Rapid STP, not PVST -> B is not correct.
0017.596d.1580 is the MAC address of this switch, not of the root bridge. The MAC address of the root bridge is 0017.596d.2a00 -> C is not correct.
All of the interface roles of the root bridge are designated. SwitchA has one Root port and 1 Alternative port so it is not the root bridge -> D is correct.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Refer to the exhibit:
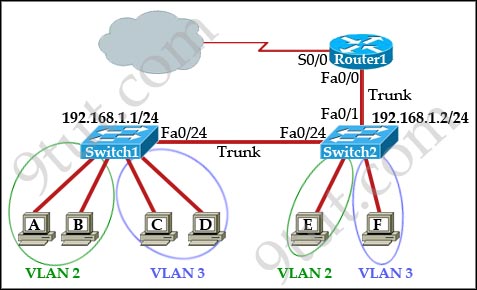
Which two statements are true about interVLAN routing in the topology that is shown in the exhibit? (Choose two)
A. Host E and host F use the same IP gateway address.
B. Routed and Switch2 should be connected via a crossover cable.
C. Router1 will not play a role in communications between host A and host D.
D. The FastEthernet 0/0 interface on Router1 must be configured with subinterfaces.
E. Router1 needs more LAN interfaces to accommodate the VLANs that are shown in the exhibit.
F. The FastEthernet 0/0 interface on Router1 and Switch2 trunk ports must be configured using the same encapsulation type.
Answer: D F[/am4show]
Question 2
[am4show have=’p2;’]Which statement about slow inter VLAN forwarding is true?
A. The VLAN is experiencing slowness in the point-to-point collisionless connection.
B. The VLANs are experiencing slowness because multiple devices are connected to the same hub.
C. The local VLAN is working normally, but traffic to the alternate VLAN is forwarded slower than expected.
D. The entire VLAN is experiencing slowness.
E. The VLANs are experiencing slowness due to a duplex mismatch.
Answer: E[/am4show]
Explanation
The causes of slow interVLAN are usually duplex mismatch or collision domain issues, user misconfiguration. For more information please read: http://www.cisco.com/c/en/us/support/docs/lan-switching/virtual-lans-vlan-trunking-protocol-vlans-vtp/23637-slow-int-vlan-connect.html#troubleshoot_slow_interv
Question 3
[am4show have=’p2;’]Which configuration can you apply to enable encapsulation on a subinterface?
A. interface FastEthernet 0/0
encapsulation dot1Q 30
ip address 10.1.1.30 255.255.255.0
B. interface FastEthernet 0/0.30
ip address 10.1.1.30 255.255.255.0
C. interface FastEthernet 0/0.30
description subinterface vlan 30
D. interface FastEthernet 0/0.30
encapsulation dot1Q 30
ip address 10.1.1.30 255.255.255.0
Answer: D[/am4show]
Explanation
To enabe encapsulation on a subinterface we have type the “encapsulation” command under that subinterface, not the main interface. An example of configuring encapsulation on subinterface of Fa0/1 is shown below:
|
Router(config)#interface f0/0 (Note: The main interface f0/0 doesn’t need an IP address but it must be turned on) Router(config)#interface f0/0.0 |
Note: In the “encapsulation dot1q 10”, number 10 is the VLAN applied to that subinterface. Or you can understand that the subinterface belongs to that VLAN.
Question 4
[am4show have=’p2;’]Refer to the exhibit:
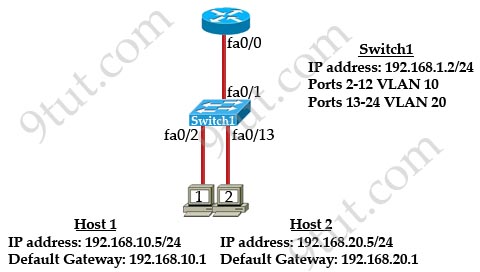
What commands must be configured on the 2950 switch and the router to allow communication between host 1 and host 2? (Choose two)
A. Router(config)#interface fastethernet 0/0
Router(config-if)#ip address 192.168.1.1 255.255.255.0
Router(config-if)#no shut down
B. Router(config)#interface fastethernet 0/0
Router(config-if)#no shutdown
Router(config)#interface fastethernet 0/0.1
Router(config-subif)#encapsulation dot1q 10
Router(config-subif)#ip address 192.168.10.1 255.255.255.0
Router(config-subif)#interface fastethernet 0/0.2
Router(config-subif)#encapsulation dot1q 20
Router(config-subif)#ip address 192.168.20.1 255.255.255.0
C. Router (config)#router eigrp 100
Router(config-router)#network 192.168.10.0
Router(config-router)#network 192.168.20.0
D. Switch1(config)# vlan database
Switch1(config-vlan)# vtp domain XYZ
Switch1(config-vlan)# vtp server
E. Switch1(config) # interface fastEthernet 0/1
Switch1(config-if)# switchport mode trunk
F. Switch1(config)# interface vlan 1
Switch1(config-if)# ip default-gateway 192.168.1.1
Answer: B E[/am4show]
Question 5
[am4show have=’p2;’]Refer to the exhibit:

C-router is to be used as a “router-on-a-stick” to route between the VLANs. All the interfaces have been properly configured and IP routing is operational. The hosts in the VLANs have been configured with the appropriate default gateway. What can be said about this configuration?
A. These commands need to be added to the configuration:
C-router(config)# router eigrp 123
C-router(config-router)# network 172.19.0.0
B. No further routing configuration is required.
C. These commands need to be added to the configuration:
C-router(config)# router ospf 1
C-router(config-router)# network 172.19.0.0 0.0.3.255 area 0
D. These commands need to be added to the configuration:
C-router(config)# router rip
C-router(config-router)# network 172.19.0.0
Answer: B[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Refer to the exhibit. The show interfaces serial 0/1 command was issued on the R10-1 router. Based on the output displayed which statement is correct?
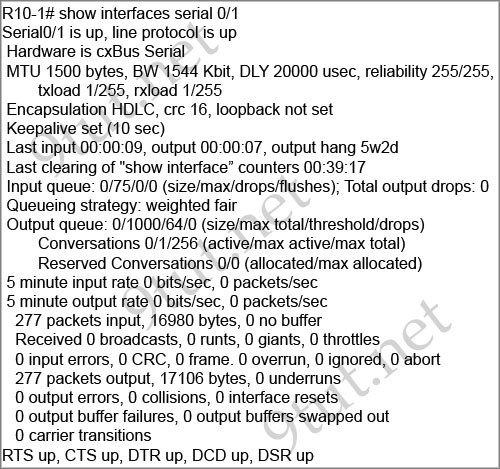
A. The cable connected to the serial 0/1 interface of the R10-1 router is a DTE cable.
B. The R10-1 router can ping the router interface connected to the serial 0/1 interface.
C. The clock rate used for interface serial 0/1 of the R10-1 router is 1,544,000 bits per second.
D. The CSU used with the serial 0/1 interface of the R10-1 router has lost connection to the service provider.
E. The interface of the remote router connected to the serial 0/1 interface of the R10-1 router is using the default serial interface encapsulation.
Answer: E[/am4show]
Explanation
From the output, we see the the line “Serial0/1 is up, line protocol is up”. That means the link is good and the interface is functioning normally. Also the encapsulation used on this interface is HDLC -> The other end must use the same encapsulation. Otherwise the line protocol will go down.
Question 2
[am4show have=’p2;’]Which two options are valid WAN connectivity methods? (Choose two)
A. PPP
B. WAP
C. DSL
D. L2TPv3
E. Ethernet
Answer: A C[/am4show]
Question 3
[am4show have=’p2;’]Which device classes are used over serial links?
A. DCE
B. DTE
C. LCP
D. HDLC
E. PPP
F. LMI
Answer: A B[/am4show]
Question 4
[am4show have=’p2;’]Which WAN technology uses labels to make decisions about data forwarding?
A. Metro Ethernet
B. Frame Relay
C. MPLS
D. ISDN
E. VSAT
Answer: C[/am4show]
Question 5
[am4show have=’p2;’]Which WAN solution is secured by default?
A. VPN
B. DSL
C. LCP
D. PPP
Answer: A[/am4show]
Question 6
[am4show have=’p2;’]Which WAN topology provides a direct connection from each site to all other sites on the network?
A. single-homed
B. full mesh
C. point-to-point
D. hub-and-spoke
Answer: B[/am4show]
Question 7
[am4show have=’p2;’]After you configure a GRE tunnel between two networks, the tunnel comes up normally, but workstations on each side of the tunnel cannot communicate. Which reason for the problem is most likely the true?
A. The tunnel source address is incorrect.
B. The tunnel destination address is incorrect.
C. The route between the networks is undefined.
D. The IP MTU is incorrect.
E. The distance configuration is missing.
Answer: C[/am4show]
Question 8
[am4show have=’p2;’]What is the default encapsulation type for Cisco WAN serial interfaces?
A. GRE
B. PPP
C. Frame Relay
D. IEEE 802.1Q
E. HDLC
Answer: E[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which feature does PPP use to encapsulate multiple protocols?
A. NCP
B. LCP
C. IPCP
D. IPXP
Answer: A[/am4show]
Question 2
[am4show have=’p2;’]Which two statements about using the CHAP authentication mechanism in a PPP link are true? (Choose two)
A. CHAP uses a two-way handshake.
B. CHAP uses a three-way handshake.
C. CHAP authentication periodically occurs after link establishment.
D. CHAP authentication passwords are sent in plaintext.
E. CHAP authentication is performed only upon link establishment.
F. CHAP has no protection from playback attacks.
Answer: B C[/am4show]
Explanation
Point-to-Point Protocol (PPP) can use either Password Authentication Protocol (PAP) or Challenge Handshake Authentication Protocol (CHAP) for authentication. CHAP is used upon initial link establishment and periodically to make sure that the router is still communicating with the same host. CHAP passwords arc exchanged as message digest algorithm 5 (MD5) hash values.
The three-way handshake steps are as follows:
Challenge: The authenticator generates a frame called a Challenge and sends it to the initiator. This frame contains a simple text message (sometimes called the challenge text). The message has no inherent special meaning so it doesn’t matter if anyone intercepts it. The important thing is that after receipt of the Challenge both devices have the same challenge message.
Response: The initiator uses its password (or some other shared “secret” that the authenticators also knows) to encrypt the challenge text. It then sends the encrypted challenge text as a Response back to the authenticator.
Success or Failure: The authenticator performs the same encryption on the challenge text that the initiator did. If the authenticator gets the same result that the initiator sent it in the Response, the authenticator knows that the initiator had the right password when it did its encryption, so the authenticator sends back a Success message. Otherwise, it sends a Failure message.
(Reference: CCNA Quick Reference Sheets)
Question 3
[am4show have=’p2;’]What is the purpose of LCP?
A. to perform authentication
B. to negotiate control options
C. to encapsulate multiple protocols
D. to specify asynchronous versus synchronous
Answer: B[/am4show]
Question 4
[am4show have=’p2;’]Which command is used to enable CHAP authentication with PAP as the fallback method on a serial interface?
A. (config-if)# authentication ppp chap fallback ppp
B. (config-if)# authentication ppp chap pap
C. (config-if)# ppp authentication chap pap
D. (config-if)# ppp authentication chap fallback ppp
Answer: C[/am4show]
Explanation
The command “ppp authentication chap pap” command indicates the CHAP authentication is used first. If it fails or is rejected by other side then uses PAP instead. If you want to use PAP first (then CHAP) you can use the “ppp authentication pap chap” command.
Question 5
[am4show have=’p2;’]What are three reasons that an organization with multiple branch offices and roaming users might implement a Cisco VPN solution instead of point-to-point WAN links? (Choose three)
A. reduced cost
B. better throughput
C. broadband incompatibility
D. increased security
E. scalability
F. reduced latency
Answer: A D E[/am4show]
Question 6
[am4show have=’p2;’]Which Layer 2 protocol encapsulation type supports synchronous and asynchronous circuits and has built-in security mechanisms?
A. HDLC
B. PPP
C. X.25
D. Frame Relay
Answer: B[/am4show]
Explanation
PPP supports both synchronous (like analog phone lines) and asynchronous circuits (such as ISDN or digital links). With synchronous circuits we need to use clock rate.
Note: Serial links can be synchronous or asynchronous. Asynchronous connections used to be only available on low-speed (<2MB) serial interfaces, but now, there are the new HWICs (High-Speed WAN Interface Cards) which also support asynchronous mode. To learn more about them please visit http://www.cisco.com/en/US/prod/collateral/modules/ps5949/ps6182/prod_qas0900aecd80274424.html.
Question 7
[am4show have=’p2;’]Which PPP subprotocol negotiates authentication options?
A. NCP
B. ISDN
C. SUP
D. LCP
E. DLCI
Answer: D[/am4show]
Explanation
Link Control Protocol (LCP) is a subprotocol within the Point-to-Point Protocol protocol suite that is responsible for link management. During establishment of a PPP communication session, LCP establishes the link, configures PPP options, and tests the quality of the line connection between the PPP client and PPP server. LCP automatically handles encapsulation format options and varies packet sizes over PPP communication links.
LCP also negotiates the type of authentication protocol used to establish the PPP session. Different authentication protocols are supported for satisfying the security needs of different environments.
Other subprotocol within PPP is Network Control Protocol (NCP), which is used to allow multiple Network layer protocols (routed protocols) to be used on a point-to-point connection.
Question 8
[am4show have=’p2;’]At which layer of the OSI model does PPP perform?
A. Layer 2
B. Layer 3
C. Layer 4
D. Layer 5
Answer: A[/am4show]
Explanation
Layer 2 includes the popular WAN standards, such as the Point-to-Point Protocol (PPP), High-Level Data-Link Control (HDLC) and Frame Relay protocols.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which type of interface can negotiate an IP address for a PPPoE client?
A. Ethernet
B. dialer
C. serial
D. Frame Relay
Answer: B[/am4show]
Explanation
In the Dialer interface, we can use the “ip address negotiated” command to ask for an IP address from the PPPoE Server.
Question 2
[am4show have=’p2;’]Which part of the PPPoE server configuration contains the information used to assign an IP address to a PPPoE client?
A. virtual-template interface
B. DHCP
C. dialer interface
D. AAA authentication
Answer: A[/am4show]
Explanation
The picture below shows all configuration needed for PPPoE:
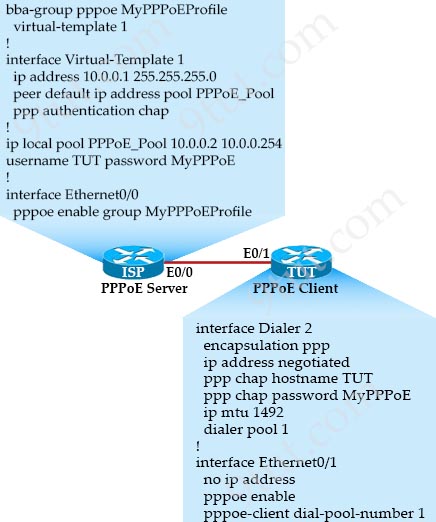
There is no Dialer interface on the PPPoE Server so answer “Dialer interface” is not correct. The most suitable answer is “Virtual Template” interface as it contains the pool which is used to assign IP address to the PPPoE Client. But this question is weird because according to the CCNAv3 syllabus, candidates only need to grasp the PPPoE on client-side, not sure why this question asked about PPPoE on Server side. For more information about PPPoE, please read our PPPoE tutorial.
Question 3
[am4show have=’p2;’]Which command do you enter to enable an interface to support PPPoE on a client?
A. Dev1(config)# bba-group pppoe bba 1
B. Dev1(config-if)# pppoe-client dial-pool-number 1
C. Dev1(config-if)# pppoe enable group bba1
D. Dev1(config-if)# pppoe enable
Answer: D[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which type of topology is required by DMVPN?
A. ring
B. full mesh
C. hub-and-spoke
D. partial mesh
Answer: C[/am4show]
Explanation
The topology of DMVPN is always hub-and-spoke as all Spokes are required to connect to the Hub router directly.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which statement about MPLS is true?
A. It operates in Layer 1.
B. It operates between Layer 2 and Layer 3.
C. It operates in Layer 3.
D. It operates in Layer 2.
Answer: B[/am4show]
Explanation
MPLS operates at a layer that lies between traditional definitions of Layer 2 (data link layer) and Layer 3 (network layer), and thus is often referred to as a “layer 2.5” protocol.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which three statements about HSRP operation are true? (Choose three)
A. The virtual IP address and virtual MAC address are active on the HSRP Master router.
B. The HSRP default timers are a 3 second hello interval and a 10 second dead interval.
C. HSRP supports only clear-text authentication.
D. The HSRP virtual IP address must be on a different subnet than the routers’ interfaces on the same LAN.
E. The HSRP virtual IP address must be the same as one of the router’s interface addresses on the LAN.
F. HSRP supports up to 255 groups per interface, enabling an administrative form of load balancing.
Answer: A B F[/am4show]
Explanation
The virtual MAC address of HSRP version 1 is 0000.0C07.ACxx, where xx is the HSRP group number in hexadecimal based on the respective interface. For example, HSRP group 10 uses the HSRP virtual MAC address of 0000.0C07.AC0A. HSRP version 2 uses a virtual MAC address of 0000.0C9F.FXXX (XXX: HSRP group in hexadecimal)
For more information about HSRP operation, please read our HSRP tutorial.
Question 2
[am4show have=’p2;’]What is a valid HSRP virtual MAC address?
A. 0000.5E00.01A3
B. 0007.B400.AE01
C. 0000.0C07.AC15
D. 0007.5E00.B301
Answer: C[/am4show]
Explanation
With HSRP, two or more devices support a virtual router with a fictitious MAC address and unique IP address. There are two version of HSRP.
+ With HSRP version 1, the virtual router’s MAC address is 0000.0c07.ACxx , in which xx is the HSRP group.
+ With HSRP version 2, the virtual MAC address if 0000.0C9F.Fxxx, in which xxx is the HSRP group.
Note: Another case is HSRP for IPv6, in which the MAC address range from 0005.73A0.0000 through 0005.73A0.0FFF.
-> C is correct.
(Good resource for HSRP: http://www.cisco.com/en/US/docs/switches/datacenter/sw/5_x/nx-os/unicast/configuration/guide/l3_hsrp.html)
Question 3
[am4show have=’p2;’]Which three options are the HSRP states for a router? (Choose three)
A. initialize
B. learn
C. secondary
D. listen
E. speak
F. primary
Answer: B D E[/am4show]
Explanation
HSRP consists of 6 states:
| State | Description |
| Initial | This is the beginning state. It indicates HSRP is not running. It happens when the configuration changes or the interface is first turned on |
| Learn | The router has not determined the virtual IP address and has not yet seen an authenticated hello message from the active router. In this state, the router still waits to hear from the active router. |
| Listen | The router knows both IP and MAC address of the virtual router but it is not the active or standby router. For example, if there are 3 routers in HSRP group, the router which is not in active or standby state will remain in listen state. |
| Speak | The router sends periodic HSRP hellos and participates in the election of the active or standby router. |
| Standby | In this state, the router monitors hellos from the active router and it will take the active state when the current active router fails (no packets heard from active router) |
| Active | The router forwards packets that are sent to the HSRP group. The router also sends periodic hello messages |
Please notice that not all routers in a HSRP group go through all states above. In a HSRP group, only one router reaches active state and one router reaches standby state. Other routers will stop at listen state.
Question 4
[am4show have=’p2;’]What about HSRP IP Address is true?
A. If its part of the LAN
B. Part of all other networks
C. Local to the interface
D. Appears in the routing table
E. Acts as default route for that interface
Answer: E[/am4show]
Question 5
[am4show have=’p2;’]Which of the following HSRP router states does an active router enter when it is preempted by a higher priority router?
A. active
B. speak
C. learn
D. listen
E. init
F. standby
Answer: B[/am4show]
Explanation
First we should review all the HSRP States:
| State | Description |
| Initial | This is the beginning state. It indicates HSRP is not running. It happens when the configuration changes or the interface is first turned on |
| Listen | The router knows both IP and MAC address of the virtual router but it is not the active or standby router. For example, if there are 3 routers in HSRP group, the router which is not in active or standby state will remain in listen state. |
| Speak | The router sends periodic HSRP hellos and participates in the election of the active or standby router. |
| Standby | In this state, the router monitors hellos from the active router and it will take the active state when the current active router fails (no packets heard from active router) |
| Active | The router forwards packets that are sent to the HSRP group. The router also sends periodic hello messages |
Now let’s take an example of a router passing through these states. Suppose there are 2 routers A and B in the network; router A is turned on first. It enters the initial state. Then it moves to listen state in which it tries to hear if there are already active or standby routers for this group. After learning no one take the active or standby state, it determines to take part in the election by moving to speak state. Now it starts sending hello messages containing its priority. These messages are sent to the multicast address 224.0.0.2 (which can be heard by all members in that group). When it does not hear a hello message with a higher priority it assumes the role of active router and moves to active state. In this state, it continues sending out periodic hello messages.
Now router B is turned on. It also goes through initial and listen state. In listen state, it learns that router A has been already the active router and no other router is taking standby role so it enters speak state to compete for the standby router -> it promotes itself as standby router.
Now to our main question! We want router B to become active router so we set a higher priority number than the priority of A and ask router B to take over the role of active router (with the preempt command). Now router A will fall back to the speak state to compete for active or standby state -> it becomes standby router because its priority is now lower than that of router A. (Therefore answer B is correct).
Note: Suppose router A is in active state while router B is in standby state. If router B does not hear hello messages from router A within the holdtime, router B goes into speak state to announce its priority to all HSRP members and compete for the active state. But if at some time it receives a message from the active router that has a lower priority than its priority (because the administrator change the priority in either router), it can take over the active role by sending out a hello packet with parameters indicating it wants to take over the active router. This is called a coup hello message.
(Reference and good resource: http://www.cisco.com/en/US/tech/tk648/tk362/technologies_tech_note09186a0080094a91.shtml)
Question 6
[am4show have=’p2;’]Which protocol specified by RFC 2281 provides network redundancy for IP networks, ensuring that user traffic immediately and transparently recovers from first-hop failures in network edge devices or access circuits?
A. ICMP
B. IRDP
C. HSRP
D. STP
Answer: C[/am4show]
Explanation
HSRP is a Cisco-proprietary protocol developed to allow several routers or multilayer switches to appear as a single gateway IP address. This protocol is described in RFC 2281.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which option is the benefit of implementing an intelligent DNS for a cloud computing solution?
A. It reduces the need for a backup data center.
B. It can redirect user requests to locations that are using fewer network resources.
C. It enables the ISP to maintain DNS records automatically.
D. It eliminates the need for a GSS.
Answer: B[/am4show]
Explanation
The Domain Name System (DNS) is used to resolve human-readable domain names like www.microsoft.com into machine-readable IP addresses like 104.43.195.251. DNS also provides other information about domain names, such as mail services.
Suppose Microsoft has some data centers located at different locations. For example one in USA and one in Canada. With normal DNS, only the data center in USA is chosen as the “active” server and the DNS server will return the IP address of the data center in USA when being asked.
With the use of intelligent DNS, the DNS server may return the IP addresses of the data center in USA or in Canada, depends on some rules (user’s geographical location, data center’s available resources…). Thus intelligent DNS helps share the load among the data centers -> Answer B is correct.
The Global Site Selector (GSS) is a crucial component of any data center architecture that requires a secure site-to-site global load balancing. The GSS allows businesses to deploy global Internet and intranet applications with the confidence that all application users will be quickly rerouted to a standby data center during a primary data center outage or overload.
Therefore GSS works in the same way as intelligent DNS but we are not sure about the answer “it eliminates the need for a GSS”. Maybe GSS can cooperate with intelligent DNS for better performance.
Note: The traffic flow itself (between the client and the server) never traverses the GSS or intelligent DNS. The GSS/DNS simply tells the client which server to target by resolving a name to an IP address.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which statement about QoS default behavior is true?
A. Ports are untrusted by default.
B. VoIP traffic is passed without being tagged.
C. Video traffic is passed with a well-known DSCP value of 46.
D. Packets are classified internally with an environment.
E. Packets that arrive with a tag are untagged at the edge of an administrative domain.
Answer: A[/am4show]
Explanation
By default, all ports are in the untrusted state when QoS is enabled.
Reference: https://www.cisco.com/c/en/us/support/docs/switches/catalyst-6000-series-switches/24055-173.html
Question 2
[am4show have=’p2;’]Which option describes the purpose of traffic policing?
A. It prioritizes routing protocol traffic.
B. It remarks traffic that is below the CIR
C. It drops traffic that exceeds the CIR.
D. It queues and then transmits traffic that exceeds the CIR.
Answer: C[/am4show]
Explanation
The following diagram illustrates the key difference between traffic policing and traffic shaping. Traffic policing propagates bursts. When the traffic rate reaches the configured maximum rate (or committed information rate), excess traffic is dropped (or remarked). The result is an output rate that appears as a saw-tooth with crests and troughs. In contrast to policing, traffic shaping retains excess packets in a queue and then schedules the excess for later transmission over increments of time. The result of traffic shaping is a smoothed packet output rate.

Note: Committed information rate (CIR): The minimum guaranteed data transfer rate agreed to by the routing device.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which option is a benefit of switch stacking?
A. It provides redundancy with no impact on resource usage.
B. It simplifies adding and removing hosts.
C. It supports better performance of high-needs applications.
D. It provides higher port density with better resource usage.
Answer: D[/am4show]
Explanation
Switch stacking technology allows the network engineer to make that stack of physical switches act like one switch. The stacking cables together make a ring between the switches. That is, the switches connect in series, with the last switch connecting again to the first.
Answer B is not correct as switch stacking is about connecting switches together so that they act as one switch, not about adding and removing hosts.
Answer C is not correct because switch stacking has nothing to do with performance of high-needs applications.
Surely switch stacking provides redundancy as stacking creates a ring of connection with two opposite paths. Whenever a frame is ready for transmission onto the path, a calculation is made to see which path has the most available bandwidth. The entire frame is then copied onto this half of the path.
With switch stacking, STP, CDP and VTP would run on one switch, not multiple switches. Also there would be one MAC address table, and it would reference all ports on all physical switches so we may say switch stacking has better resource usage. Also if we consider all stacking switches as one logical switch then surely the port density is increase very much. Therefore answer D is the most suitable one.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]If host Z needs to send data through router R1 to a storage server, which destination MAC address does host Z use to transmit packets?
A. the host Z MAC address
B. the MAC address of the interface on R1 that connects to the storage server
C. the MAC address of the interface on R1 that connects to host Z
D. the MAC address of the storage server interface
Answer: C[/am4show]
Explanation
Host Z will use ARP to get the MAC address of the interface on R1 that connects to it and use this MAC as the destination MAC address. It use the IP address of the storage server as the destination IP address.
For example in the topology below, host A will use the MAC address of E0 interface of the router as its destination MAC address to reach the Email Server.
Question 2
[am4show have=’p2;’]Refer to the exhibit. RTA is configured with a basic configuration. The link between the two routers is operational and no routing protocols are configured on either router. The line shown in the exhibit is then added to router RTA. Should interface Fa0/0 on router RTB shut down, what effect will the shutdown have on router RTA?
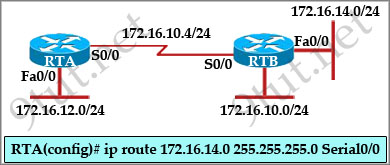
A. A route to 172.16.14.0/24 will remain in the RTA routing table.
B. A packet to host 172.16.14.225 will be dropped by router RTA
C. Router RTA will send an ICMP packet to attempt to verify the route.
D. Because router RTB will send a poison reverse packet to router RTA, RTA will remove the route.
Answer: A[/am4show]
Explanation
Static routes remain in the routing table even if the specified gateway becomes unavailable. If the specified gateway becomes unavailable, you need to remove the static route from the routing table manually. However, static routes are removed from the routing table if the specified interface goes down, and are reinstated when the interface comes back up.
Therefore the static route will only be removed from the routing table if the S0/0 interface on RTA is shutdown.
(Reference: http://www.cisco.com/en/US/docs/security/asa/asa84/configuration/guide/route_static.html)
Question 3
[am4show have=’p2;’]A router is running three routing processes: RIP, OSPF, and EIGRP, each configured with default characteristics. Each process learns a route to the same remote network.
If there are no static routes to the destination and none of the routes were redistributed, which route will be placed in the IP routing table?
A. the route learned through EIGRP
B. the route learned through OSPF
C. the route learned through RIP
D. the route with the lowest metric
E. all three routes with the router load balancing
Answer: A[/am4show]
Question 4
[am4show have=’p2;’]Which parameter would you tune to affect the selection of a static route as a backup, when a dynamic protocol is also being used?
A. hop count
B. administrative distance
C. link bandwidth
D. link delay
E. link cost
Answer: B[/am4show]
Explanation
By default a static route has the Administrative Distance (AD) of 1, which is always preferred to dynamic routing protocols. In some cases we may want to use dynamic routing protocols and set static routes as a backup route when the “dynamic” routes fail -> we can increase the AD of that static route to a higher value than the AD of the dynamic routing protocols.
Question 5
[am4show have=’p2;’]A router receives information about network 192.168.10.0/24 from multiple sources. What will the router consider the most reliable information about the path to that network?
A. an OSPF update for network 192.168.0.0/16
B. a static router to network 192.168.10.0/24
C. a static router to network 192.168.10.0/24 with a local serial interface configured as the next hop
D. a RIP update for network 192.168.10.0/24
E. a directly connected interface with an address of 192.168.10.254/24
F. a default route with a next hop address of 192.168.10.1
Answer: E[/am4show]
Question 6
[am4show have=’p2;’]Which statement is true, as relates to classful or classless routing?
A. RIPV1 and OSPF are classless routing protocols.
B. Classful routing protocols send the subnet mask in routing updates.
C. Automatic summarization at classful boundaries can cause problems on discontigous networks.
D. EIGRP and OSPF are classful routing protocols and summarize routes by default.
Answer: C[/am4show]
Explanation
Discontiguous networks are networks that have subnets of a major network separated by a different major network. Below is an example of discontiguous networks where subnets 10.10.1.0/24 and 10.10.2.0/24 are separated by a 2.0.0.0/8 network.
If we configure automatic summarization at classful boundaries, users on network 10.10.1.0/24 cannot communicate with users on network 10.10.2.0/24.
If you are not clear about automatic summarization please read the last part of this tutorial: http://www.9tut.com/eigrp-routing-protocol-tutorial.
Question 7
[am4show have=’p2;’]Which two are advantages of static routing when compared to dynamic routing? (Choose two)
A. Security increases because only the network administrator may change the routing tables.
B. Configuration complexity decreases as network size increases.
C. Routing updates are automatically sent to neighbors.
D. Route summarization is computed automatically by the router.
E. Routing traffic load is reduced when used in stub network links.
F. An efficient algorithm is used to build routing tables using automatic updates.
G. Routing tables adapt automatically to topology changes.
Answer: A E[/am4show]
Explanation
Static routing can only be configured for each route manually so it is more secure than dynamic routing which only needs to declare which networks to run -> A is correct.
Also static route does not use any complex algorithm to find out the best path so no routing updates need to be sent out -> reduce routing traffic load. Static routing is useful especially in stub network links.
Note: Stub network (or stub router) is used to describe a network (or router) that does not have any information about other networks except a default route. This type of network (or router) usually has only one connection to the outside.
Question 8
[am4show have=’p2;’]A technician pastes the configurations in the exhibit into the two new routers shown. Otherwise, the routers are configured with their default configurations. A ping from Host1 to Host2 fails, but the technician is able to ping the S0/0 interface of R2 from Host1. The configurations of the hosts have been verified as correct. What is the cause of the problem?
A. The serial cable on R1 needs to be replaced.
B. The interfaces on R2 are not configured properly.
C. R1 has no route to the 192.168.1.128 network.
D. The IP addressing scheme has overlapping subnetworks.
E. The ip subnet-zero command must be configured on both routers.
Answer: C[/am4show]
Explanation
Host1 can ping the Serial interface of R2 because R1 has the network of 192.168.1.4/30 as directly connected route. But R1 does not know how to route to the network of Host2 (192.168.1.128/26) so R1 will drop that ping without trying to send it out S0/0 interface. To make the ping work, we have to configure a route pointing to that network (for example: ip route 192.168.1.128 255.255.255.192 s0/0 on R1).
Question 9
[am4show have=’p2;’]How does a router handle an incoming packet whose destination network is missing from the Routing table?
A. It discards the packet.
B. It broadcasts the packet to each network on the router.
C. It routes the packet to the default route.
D. It broadcasts the packet to each interface on the router.
Answer: A[/am4show]
Question 10
[am4show have=’p2;’]What are two drawbacks of implementing a link-state routing protocol? (Choose two)
A. the sequencing and acknowledgment of link-state packets
B. the requirement for a hierarchical IP addressing scheme for optimal functionality
C. the high volume of link-state advertisements in a converged network
D. the high demand on router resources to run the link-state routing algorithm
E. the large size of the topology table listing all advertised routes in the converged network
Answer: B D[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Refer to the exhibit, Host A pings interface S0/0 on router 3, what is the TTL value for that ping?
A. 253
B. 252
C. 255
D. 254
Answer: A[/am4show]
Explanation
From the CCNA ICND2 Exam book: “Routers decrement the TTL by 1 every time they forward a packet; if a router decrements the TTL to 0, it throws away the packet. This prevents packets from rotating forever.” I want to make it clear that before the router forwards a packet, the TTL is still remain the same. For example in the topology above, pings to S0/1 and S0/0 of Router 2 have the same TTL.
The picture below shows TTL values for each interface of each router and for Host B. Notice that Host A initializes ICMP packet with a TTL of 255:
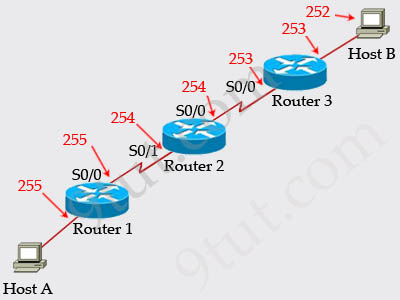
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]What are two drawbacks of implementing a link-state routing protocol? (Choose two)
A. the sequencing and acknowledgment of link-state packets
B. the requirement for a hierarchical IP addressing scheme for optimal functionality
C. the high volume of link-state advertisements in a converged network
D. the high demand on router resources to run the link-state routing algorithm
E. the large size of the topology table listing all advertised routes in the converged network
Answer: B D[/am4show]
Question 2
[am4show have=’p2;’]Which two statements describe the process identifier that is used in the command to configure OSPF on a router? (Choose two)
Router(config)# router ospf 1
A. All OSPF routers in an area must have the same process ID.
B. Only one process number can be used on the same router.
C. Different process identifiers can be used to run multiple OSPF processes
D. The process number can be any number from 1 to 65,535.
E. Hello packets are sent to each neighbor to determine the processor identifier.
Answer: C D[/am4show]
Question 3
[am4show have=’p2;’]What are three characteristics of the OSPF routing protocol? (Choose three)
A. It converges quickly.
B. OSPF is a classful routing protocol.
C. It uses cost to determine the best route.
D. It uses the DUAL algorithm to determine the best route.
E. OSPF routers send the complete routing table to all directly attached routers.
F. OSPF routers discover neighbors before exchanging routing information.
Answer: A C F[/am4show]
Explanation
OSPF is a link-state routing protocol so it converges more quickly than distance-vector protocol. OSPF uses cost to determine the best route. The popular formula to calculate OSPF cost is: cost = 108 / Bandwidth [ in bps] (in fact the formal formula is: cost = reference bandwidth / configured bandwidth of interface in kbps. On Cisco routers, the reference bandwidth defaults to 100000 kbps)
Question 4
[am4show have=’p2;’]Which two statements about the OSPF Router ID are true? (Choose two)
A. It identifies the source of Type 1 LSA
B. It should be the same on all routers in an OSPF routing instance
C. By default, the lowest IP address on the router becomes the OSPF router ID
D. The router automatically chooses the IP address of a loopback as the OSPF Router ID
E. It is created using the MAC Address of the loopback interface
Answer: A D[/am4show]
Explanation
From the output of the “show ip ospf database”:

We can see OSPF Router ID will be used as source of Type 1 LSA (1.1.1.1 & 2.2.2.2). Also the router will chose the highest loopback interface as its OSPF router ID (if available).
Question 5
[am4show have=’p2;’]What are two enhancements that OSPFv3 supports over OSPFv2? (Choose two)
A. It requires the use of ARP.
B. It can support multiple IPv6 subnets on a single link.
C. It supports up to 2 instances of OSPFv3 over a common link.
D. It routes over links rather than over networks.
Answer: B D[/am4show]
Explanation
Unlike OSPFv2 which form adjacencies using their IPv4 interface addresses, OSPFv3 use the link-local addresses (FE80::/10) to form adjacencies. Therefore it can support multiple IPv6 subnets on a single link as an interface can have multiple IPv6 addresses (and two nodes can communicate with each other even if they do not share a common IP subnet.) -> B is correct.
IPv6 uses the term “link” instead of “subnet” or “network” to define a medium used to communicate between nodes at the link layer -> D is correct.
OSPFv3 can support more than 1 instance over a common link. For example you can run instance 1 on an interface with the command:
Router(config-if)# ipv6 ospf 100 area 0 instance 1
-> C is not correct.
Question 6
[am4show have=’p2;’]You enter the “show ipv6 route” command on an OSPF device and the device displays a route. Which conclusion can you draw about the environment?
A. OSPF is distributing IPv6 routes to BGP.
B. The router is designated as an ABR.
C. The router is designated as totally stubby.
D. OSPFv3 is in use.
Answer: D[/am4show]
Explanation
The “show ipv6 route” displays the current contents of the IPv6 routing table. This device is running OSPF so we can deduce it is running OSPFv3 (OSPF for IPv6). An example of the “show ip v6 route” is shown below:

Question 7
[am4show have=’p2;’]What are OSPF default hello and dead timers? (Choose two)
A. The hello timer is 10 seconds.
B. The hello timer is 60 seconds.
C. The dead timer is 40 seconds.
D. The dead timer is 120 seconds.
E. The hello timer is 20 seconds.
Answer: A C[/am4show]
Explanation
By default, OSPF uses a 10-second hello timer and 40-second hold (dead) timer on broadcast and point-to-point links, and a 30-second hello timer and 120-second hold timer for all other network types.
Question 8
[am4show have=’p2;’]Refer to the exhibit. Router edge-1 is unable to establish OSPF neighbor adjacency with router ISP-1. Which two configuration changes can you make on edge-1 to allow the two routers to establish adjacency? (Choose two)
A. Set the subnet mask on edge-1 to 255 255.255.252.
B. Reduce the MTU on edge-1 to 1514.
C. Set the OSPF cost on edge-1 to 1522.
D. Reduce the MTU on edge-1 to 1500.
E. Configure the ip ospf mtu-ignore command on the edge-1 Gi0/0 interface.
Answer: D E[/am4show]
Explanation
In order to become OSPF neighbor following values must be match on both routers:
+ Area ID
+ Authentication
+ Hello and Dead Intervals
+ Stub Flag
+ MTU Size
Therefore we need to adjust the MTU size on one of the router so that they are the same. Or we can tell OSPF to ignore the MTU size check with the command “ip ospf mtu-ignore”.
Question 9
[am4show have=’p2;’]Which commands are required to properly configure a router to run OSPF and to add network 192.168.16.0/24 to OSPF area 0? (Choose two)
A. Router(config)# router ospf 0
B. Router(config)# router ospf 1
C. Router(config)# router ospf area 0
D. Router(config-router)# network 192.168.16.0 0.0.0.255 0
E. Router(config-router)# network 192.168.16.0 0.0.0.255 area 0
F. Router(config-router)# network 192.168.16.0 255.255.255.0 area 0
Answer: B E[/am4show]
Explanation
In the router ospf command, the ranges from 1 to 65535 so o is an invalid number -> B is correct but A is not correct.
Question 10
[am4show have=’p2;’]Refer to the exhibit.
The internetwork infrastructure of company XYZ consists of a single OSPF area as shown in the graphic. There is concern that a lack of router resources is impeding internetwork performance.
As part of examining the router resources the OSPF DRs need to be known.
All the router OSPF priorities are at the default and the router IDs are shown with each router.
Which routers are likely to have been elected as DR? (Choose two)
A. Corp-1
B. Corp-2
C. Corp-3
D. Corp-4
E. Branch-1
F. Branch-2
Answer: D F[/am4show]
Explanation
There are 2 segments on the topology above which are separated by Corp-3 router. Each segment will have a DR so we have 2 DRs.
To select which router will become DR they will compare their router-IDs. The router with highest (best) router-ID will become DR. The router-ID is chosen in the order below:
+ The highest IP address assigned to a loopback (logical) interface.
+ If a loopback interface is not defined, the highest IP address of all active router’s physical interfaces will be chosen.
In this question, the IP addresses of loopback interfaces are not mentioned so we will consider IP addresses of all active router’s physical interfaces. Router Corp-4 (10.1.40.40) & Branch-2 (10.2.20.20) have highest “active” IP addresses so they will become DRs.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Refer to the exhibit. The network is converged. After link-state advertisements are received from Router_A, what information will Router_E contain in its routing table for the subnets 208.149.23.64 and 208.149.23.96?
A. 208.149.23.64[110/13] via 190.173.23.10, 00:00:00:07, FastEthernet0/0
208.149.23.96[110/13] via 190.173.23.10, 00:00:00:16, FastEthernet0/0
B. 208.149.23.64[110/1] via 190.173.23.10, 00:00:00:07, Serial1/0
208.149.23.96[110/3] via 190.173.23.10, 00:00:00:16, FastEthernet0/0
C. 208.149.23.64[110/13] via 190.173.23.10, 00:00:00:07, Serial1/0
208.149.23.96[110/13] via 190.173.23.10, 00:00:00:16, Serial1/0
208.149.23.96[110/13] via 190.173.23.10, 00:00:00:16, FastEthernet0/0
D. 208.149.23.64[110/13] via 190.173.23.10, 00:00:00:07, Serial1/0
208.149.23.96[110/13] via 190.173.23.10, 00:00:00:16, Serial1/0
Answer: A[/am4show]
Explanation
Router_E learns two subnets subnets 208.149.23.64 and 208.149.23.96 via Router_A through FastEthernet interface. The interface cost is calculated with the formula 108 / Bandwidth. For FastEthernet it is 108 / 100 Mbps = 108 / 100,000,000 = 1. Therefore the cost is 12 (learned from Router_A) + 1 = 13 for both subnets -> B is not correct.
The cost through T1 link is much higher than through T3 link (T1 cost = 108 / 1.544 Mbps = 64; T3 cost = 108 / 45 Mbps = 2) so surely OSPF will choose the path through T3 link -> Router_E will choose the path from Router_A through FastEthernet0/0, not Serial1/0 -> C & D are not correct.
In fact, we can quickly eliminate answers B, C and D because they contain at least one subnet learned from Serial1/0 -> they are surely incorrect.
Question 2
[am4show have=’p2;’]What OSPF command, when configured, will include all interfaces into area 0?
A. network 0.0.0.0 255.255.255.255 area 0
B. network 0.0.0.0 0.0.0.0 area 0
C. network 255.255.255.255 0.0.0.0 area 0
D. network all-interfaces area 0
Answer: A[/am4show]
Explanation
The ‘network … area …’ command under OSPF process has the following meaning: It searches all the active interfaces, if the IP address of that interface belong to the ‘network …’ configured under OSPF process then the router will run OSPF on that interface. Therefore when we configure ‘network 0.0.0.0 255.255.255.255 area 0’ command, all interfaces are matched -> OSPF is enabled on all active interfaces on the router.
Question 3
[am4show have=’p2;’]What are two benefits of using a single OSPF area network design? (Choose two)
A. It is less CPU intensive for routers in the single area.
B. It reduces the types of LSAs that are generated.
C. It removes the need for virtual links.
D. It increases LSA response times.
E. It reduces the number of required OSPF neighbor adjacencies.
Answer: B C[/am4show]
Question 4
[am4show have=’p2;’]What can cause two OSPF neighbors to be stuck in the EXSTART state?
A. There is a low bandwidth connection between neighbors.
B. The neighbors have different MTU settings.
C. The OSPF interfaces are in a passive state.
D. There is only layer one connectivity between neighbors.
Answer: B[/am4show]
Question 5
[am4show have=’p2;’]Which parameter or parameters are used to calculate OSPF cost in Cisco routers?
A. Bandwidth, Delay and MTU
B. Bandwidth
C. Bandwidth and MTU
D. Bandwidth, MTU, Reliability, Delay and Load
Answer: B[/am4show]
Explanation
The well-known formula to calculate OSPF cost is
Cost = 108 / Bandwidth
so B is the correct answer.
Question 6
[am4show have=’p2;’]What is the default maximum number of equal-cost paths that can be placed into the routing of a Cisco OSPF router?
A. 16
B. 2
C. unlimited
D. 4
Answer: D[/am4show]
Explanation
The default number of equal-cost paths that can be placed into the routing of a Cisco OSPF router is 4. We can change this default value by using “maximum-paths” command:
Router(config-router)#maximum-paths 2
Note: Cisco routers support up to 16 equal-cost paths
Question 7
[am4show have=’p2;’]What information does a router running a link-state protocol use to build and maintain its topological database? (Choose two)
A. hello packets
B. SAP messages sent by other routers
C. LSAs from other routers
D. beacons received on point-to-point links
E. routing tables received from other link-state routers
F. TTL packets from designated routers
Answer: A C[/am4show]
Explanation
Link-state protocol uses hello packets to discover neighbors and establish adjacencies. After that, the routers begin sending out LSAs to every neighbor (each received LSA is copied and forwarded to every neighbor except the one that sent the LSA)
Question 8
[am4show have=’p2;’]Refer to the exhibit.
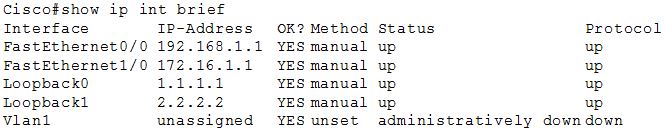
If the router Cisco returns the given output and has not had its router ID set manually, what value will OSPF use as its router ID?
A. 192.168.1.1
B. 172.16.1.1
C. 1.1.1.1
D. 2.2.2.2
Answer: D[/am4show]
Question 9
[am4show have=’p2;’]What is the default administrative distance of OSPF?
A. 90
B. 100
C. 110
D. 120
Answer: C[/am4show]
Explanation
The Administrative Distances (AD) of popular routing protocols are listed below:
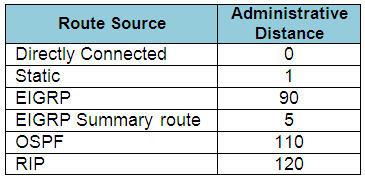
Question 10
[am4show have=’p2;’]When a router undergoes the exchange protocol within OSPF, in what order does it pass through each state?
A. exstart state > loading state > exchange state > full state
B. exstart state > exchange state > loading state > full state
C. exstart state > full state > loading state > exchange state
D. loading state > exchange state > full state > exstart state
Answer: B[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Refer to the exhibit. The network associate is configuring OSPF on the Core router. All the connections to the branches should be participating in OSPF. The link to the ISP should NOT participate in OSPF and should only be advertised as the default route. What set of commands will properly configure the Core router?
A. Core(config-router)#default-information originate
Core(config-router)#network 10.0.0.0 0.255.255.255 area 0
Core(config-router)#exit
Core(config)#ip route 0.0.0.0 0.0.0.0 10.10.2.14
B. Core(config-router)#default-information originate
Core(config-router)#network 10.10.2.13 0.0.0.242 area 0
Core(config-router)#exit
Core(config)#ip route 0.0.0.0 0.0.0.0 10.10.2.14
C. Core(config-router)#default-information originate
Core(config-router)#network 10.10.2.16 0.0.0.15 area 0
Core(config-router)#exit
Core(config)#ip route 0.0.0.0 0.0.0.0 10.10.2.14
D. Core(config-router)#default-information originate
Core(config-router)#network 10.10.2.32 0.0.0.31 area 0
Core(config-router)#exit
Core(config)#ip route 0.0.0.0 0.0.0.0 10.10.2.14
Answer: C[/am4show]
Explanation
The question states that the link to ISP should not participate in OSPF -> answers A, B are not correct.
In answer D, the “network 10.10.2.32 0.0.0.31 area 0” does not cover the IP address of S0/0.103 (10.10.2.21) -> D is not correct.
The default-information originate command advertises a default route to other routers, telling something like “please send me your unknown traffic”. So in this case, besides a full routing table, other routers will also receive a default route from Core router.
But please notice that Core router needs to have a default route in its routing table. That is why the command “ip route 0.0.0.0 0.0.0.0 10.10.2.14” is added to Core router. By adding the “always” (after “default-information originate” command) the default route will be advertised even if there is no default route in the routing table of router Core.
Question 2
[am4show have=’p2;’]Refer to the exhibit:
Assume that all of the router interfaces are operational and configured correctly. How will router R2 be affected by the configuration of R1 that is shown in the exhibit?
A. Router R2 will not form a neighbor relationship with R1.
B. Router R2 will obtain a full routing table, including a default route, from R1.
C. R2 will obtain OSPF updates from R1, but will not obtain a default route from R1.
D. R2 will not have a route for the directly connected serial network, but all other directly connected networks will be present, as well as the two networks connected to R1.
Answer: B[/am4show]
Explanation
The default-information originate command advertises a default route to other routers, telling something like “please send me your unknown traffic”. So in this case, besides a full routing table, R2 will also receive a default route from R1 -> B is correct.
Note: But in this question, the static route should be “ip route 0.0.0.0 0.0.0.0 serial0/1″ (not serial0/0), that may cause a routing loop.
Question 3
[am4show have=’p2;’]Refer to the exhibit. Which two statements are true about the loopback address that is configured on RouterB? (Choose two)
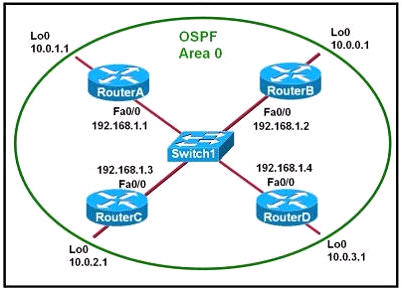
A. It ensures that data will be forwarded by RouterB.
B. It provides stability for the OSPF process on RouterB.
C. It specifies that the router ID for RouterB should be 10.0.0.1.
D. It decreases the metric for routes that are advertised from RouterB.
E. It indicates that RouterB should be elected the DR for the LAN.
Answer: B C[/am4show]
Explanation
A loopback interface never comes down even if the link is broken so it provides stability for the OSPF process (for example we use that loopback interface as the router-id) -> B is correct.
The router-ID is chosen in the order below:
+ The highest IP address assigned to a loopback (logical) interface.
+ If a loopback interface is not defined, the highest IP address of all active router’s physical interfaces will be chosen.
-> The loopback interface will be chosen as the router ID of RouterB -> C is correct.
Question 4
[am4show have=’p2;’]Refer to the exhibit.
R1 routing commands:
ip route 0.0.0.0 0.0.0.0 serial0/0
router ospf 1
network 172.16.100.0 0.0.0.3 area 0
network 172.16.100.64 0.0.0.63 area 0
network 172.16.100.128 0.0.0.31 area 0
default-information originate
Assuming that all router interfaces are operational and correctly configured, that OSPF has been correctly configured on router R2, how will the default route configured on R1 affect the operation of R2?
A. Any packet destined for a network that is not directly connected to router R1 will be dropped.
B. Any packet destined for a network that is not referenced in the routing table of router R2 will be directed to R1. R1 will then send that packet back to R2 and a routing loop will occur.
C. Any packet destined for a network that is not directly connected to router R2 will be dropped immediately.
D. Any packet destined for a network that is not directly connected to router R2 will be dropped immediately because of the lack of a gateway on R1.
Answer: B[/am4show]
Explanation
First, notice that the more-specific routes will always be favored over less-specific routes regardless of the administrative distance set for a protocol. In this case, because we use OSPF for three networks (172.16.100.0 0.0.0.3, 172.16.100.64 0.0.0.63, 172.16.100.128 0.0.0.31) so the packets destined for these networks will not be affected by the default route.
The default route configured on R1 “ip route 0.0.0.0 0.0.0.0 serial0/0″ will send any packet whose destination network is not referenced in the routing table of router R1 to R2, it doesn’t drop anything so answers A, B and C are not correct. D is not correct too because these routes are declared in R1 and the question says that “OSPF has been correctly configured on router R2″, so network directly connected to router R2 can communicate with those three subnetworks.
As said above, the default route configured on R1 will send any packet destined for a network that is not referenced in its routing table to R2; R2 in turn sends it to R1 because it is the only way and a routing loop will occur.
Question 5
[am4show have=’p2;’]RouterD# show ip interface brief
Given the output for this command, if the router ID has not been manually set, what router ID will OSPF use for this router?
A. 10.1.1.2
B. 10.154.154.1
C. 172.16.5.1
D. 192.168.5.3
Answer: C[/am4show]
Explanation
The highest IP address of all loopback interfaces will be chosen -> Loopback 0 will be chosen as the router ID.
Question 6
[am4show have=’p2;’]Which command is used to display the collection of OSPF link states?
A. show ip ospf link-state
B. show ip ospf lsa database
C. show ip ospf neighbors
D. show ip ospf database
Answer: D[/am4show]
Explanation
The output of the “show ip ospf database” is shown below:
From the output above we can see LSA Type 1 (Router Link State) and LSA Type 3 (Summary Net Link State).
Question 7
[am4show have=’p2;’]Which statement describes the process ID that is used to run OSPF on a router?
A. It is globally significant and is used to represent the AS number.
B. It is locally significant and is used to identify an instance of the OSPF database.
C. It is globally significant and is used to identify OSPF stub areas.
D. It is locally significant and must be the same throughout an area.
Answer: B[/am4show]
Question 8
[am4show have=’p2;’]Refer to the exhibit.
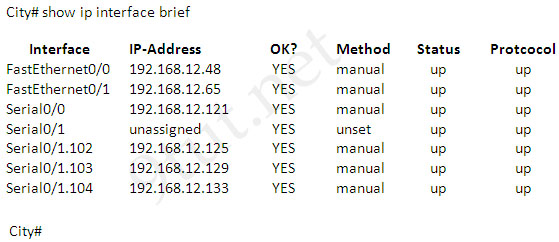
A network associate has configured OSPF with the command:
City(config-router)# network 192.168.12.64 0.0.0.63 area 0
After completing the configuration, the associate discovers that not all the interfaces are participating in OSPF.
Which three of the interfaces shown in the exhibit will participate in OSPF according to this configuration statement? (Choose three)
A. FastEthernet0/0
B. FastEthernet0/1
C. Serial0/0
D. Serial0/1.102
E. Serial0/1.103
F. Serial0/1.104
Answer: B C D[/am4show]
Explanation
The “network 192.168.12.64 0.0.0.63″ equals to network 192.168.12.64/26. This network has:
+ Increment: 64 (/26= 1111 1111.1111 1111.1111 1111.1100 0000)
+ Network address: 192.168.12.64
+ Broadcast address: 192.168.12.127
Therefore all interface in the range of this network will join OSPF -> B C D are correct.
Question 9
[am4show have=’p2;’]What is the default values for hello and dead packets in OSPF?
A. hello 10
B. hello 60
C. dead 40
D. dead 120
Answer: A C[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which configuration enables OSPF for network 192.168.1.0/24?
A. router ospf
router-id 192.168.1.0
B. router ospf 1
network 192.168.1.0 0.0.0.255 area 0
C. router ospf 1
neighbor 192.168.1.0
D. router ospf 1
area 0 virtual-link 192.168.1.0
Answer: B[/am4show]
Question 2
[am4show have=’p2;’]Which purpose of the network command in OSPF configuration mode is true?
A. It defines a wildcard mask to identify the size of the network.
B. It defines the area ID.
C. It defines the network by its classful entry.
D. It defines which networks are used for virtual links.
Answer: A[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which EIGRP for IPv6 command can you enter to view the link-local addresses of the neighbors of a device?
A. show ipv6 eigrp 20 interfaces
B. show ipv6 route eigrp
C. show ipv6 eigrp neighbors
D. show ip eigrp traffic
Answer: C[/am4show]
Explanation
The “show ipv6 eigrp neighbors” command displays the neighbors discovered by the EIGRPv6. Notice that the neighbors are displayed by their link-local addresses.
Question 2
[am4show have=’p2;’]Refer to the exhibit. Based on the exhibited routing table, how will packets from a host within the 192.168.10.192/26 LAN be forwarded to 192.168.10.1?
A. The router will forward packets from R3 to R2 to R1
B. The router will forward packets from R3 to R1
C. The router will forward packets from R3 to R1 to R2
D. The router will forward packets from R3 to R2 to R1 AND from R3 to R1
Answer: D[/am4show]
Explanation
From the routing table we learn that network 192.168.10.0/30 is learned via 2 equal-cost paths (192.168.10.9 &192.168.10.5) -> traffic to this network will be load-balancing.
Question 3
[am4show have=’p2;’]Which option describes a difference between EIGRP for IPv4 and IPv6?
A. Only EIGRP for IPv6 advertises all connected networks.
B. Only EIGRP for IPv6 requires a router ID to be configured under the routing process
C. AS numbers are configured in EIGRP but not in EIGRPv3.
D. Only EIGRP for IPv6 is enabled in the global configuration mode.
Answer: B[/am4show]
Explanation
To configure EIGRP for IPv6 we must explicitly specify a router ID before it can start running. For example:
| ipv6 router eigrp 1 eigrp router-id 2.2.2.2 no shutdown |
Notice that EIGRP for IPv6 router-id must be an IPv4 address. EIGRP for IPv4 can automatically pick-up an IPv4 to use as its EIGRP router-id with this rule:
+ The highest IP address assigned to a loopback interface is selected as the router ID.
+ If there are not any loopback addresses configured, the highest IP address assigned to any other active interface is chosen as the router ID
EIGRPv3 also uses the AS number (for example: ipv6 eigrp 1 under interface mode).
Question 4
[am4show have=’p2;’]Refer to the exhibit. If the router R1 returns the given output and has not had its router ID set manually, what address will EIGRP use as its router ID?
A. 192.168.1.2
B. 172.16.4.1
C. 192.168.10.2
D. 1.1.1.1
Answer: D[/am4show]
Question 5
[am4show have=’p2;’]When running EIGRP what is required for RouterA to exchange routing updates with RouterC?
A. AS numbers must be changed to match on all the routers.
B. Loopback interface must be configured so a DR is elected.
C. The no auto-summary command is needed on Router A and Router C.
D. Router B needs to have two network statements, one for each connected network.
Answer: A[/am4show]
Explanation
We notice that 3 routers are using different AS numbers so they do not become neighbors and cannot exchange their routing updates. We need to choose only one AS number and use it on all 3 routers to make them exchange routing updates.
In this case we don’t need to use the “no auto-summary” command because network 10.0.0.0 is not separated by another major network.
Question 6
[am4show have=’p2;’]Refer to the exhibit. A packet with a source IP address of 192.168.2.4 and a destination IP address of 10.1.1.4 arrives at the HokesB router. What action does the router take?
A. forwards the received packet out the Serial0/0 interface
B. forwards a packet containing an EIGRP advertisement out the Serial0/1 interface
C. forwards a packet containing an ICMP message out the FastEthemet0/0 interface
D. forwards a packet containing an ARP request out the FastEthemet0/1 interface
Answer: C[/am4show]
Explanation
When a packet with destination IP address of 10.1.1.4 arrives at HokesB, it will look up in the routing table to find the most specific path. In this case no path is found so HokesB must inform to the source host that the destination is unreachable on the interface it has received this packet (it is Fa0/0 because the network 192.168.2.0/28 is learned from this interface). So the best answer here should be C – send an ICMP message out of Fa0/0.
Question 7
[am4show have=’p2;’]Refer to the exhibit. Given the output from the show ip eigrp topology command, which router is the feasible successor?
|
Router# show ip eigrp topology 10.0.0.5 255.255.255.255 IP-EIGRP topology entry for 10.0.0.5/32 State is Passive, Query origin flag is 1, 1 Successor(s), FD is 41152000 |
A.
10.1.0.3 (Serial0), from 10.1.0.3, Send flag is 0x0
Composite metric is (46866176/46354176), Route is Internal
Vector metric:
Minimum bandwidth is 56 Kbit
Total delay is 45000 microseconds
Reliability is 255/255
Load is 1/255
Minimum MTU is 1500
Hop count is 2
B.
10.0.0.2 (Serial0.1), from 10.0.0.2, Send flag is 0x0
Composite metric is (53973248/128256), Route is Internal
Vector metric:
Minimum bandwidth is 48 Kbit
Total delay is 25000 microseconds
Reliability is 255/255
Load is 1/255
Minimum MTU is 1500
Hop count is 1
C.
10.1.0.1 (Serial0), from 10.1.0.1, Send flag is 0x0
Composite metric is (46152000/41640000), Route is Internal Vector metric:
Minimum bandwidth is 64 Kbit
Total delay is 45000 microseconds
Reliability is 255/255
Load is 1/255
Minimum MTU is 1500
Hop count is 2
D.
10.1.1.1 (SerialO.1), from 10.1.1.1, Send flag is 0x0
Composite metric is (46763776/46251776), Route is External
Vector metric:
Minimum bandwidth is 56 Kbit
Total delay is 41000 microseconds
Reliability is 255/255
Load is 1/255
Minimum MTU is 1500
Hop count is 2
Answer: B[/am4show]
Explanation
First we must notice that all the 4 answers are parts of the “show ip eigrp topology” output. As you can see, there are 2 parameters in the form of [FD/AD] in each answer. For example answer C has [46152000/41640000], it means that the FD of that route is 46152000 while the AD is 41640000.
To become a feasible successor, a router must meet the feasibility condition:
“To qualify as a feasible successor, a router must have an AD less than the FD of the current successor route“
In four answer above, only answer B has an AD of 128256 and it is smaller than the FD of the current successor route (41152000) so it is the feasible successor -> B is correct.
Question 8
[am4show have=’p2;’]Which type of EIGRP route entry describes a feasible successor?
A. a backup route, stored in the routing table
B. a primary route, stored in the routing table
C. a backup route, stored in the topology table
D. a primary route, stored in the topology table
Answer: C[/am4show]
Explanation
Feasible successor is a route whose Advertised Distance is less than the Feasible Distance of the current best path. A feasible successor is a backup route, which is not stored in the routing table but stored in the topology table.
Question 9
[am4show have=’p2;’]What are the two default metrics used by EIGRP for route selection? (Choose two)
A. Bandwidth
B. Delay
C. Reliability
D. Load
E. MTU
Answer: A B[/am4show]
Explanation
The formula to caculate EIGRP metric is:
metric = [K1 * bandwidth + (K2 * bandwidth)/(256 – load) + K3 * delay] * [K5/(reliability + K4)]
By default, K1 = 1, K2 = 0, K3 = 1, K4 = 0, K5 = 0 which means that the default values use only bandwidth & delay parameters while others are ignored. The metric formula is now reduced to:
metric = bandwidth + delay
Note: But remember the bandwidth here is defined as the slowest bandwidth in the route to the destination & delay is the sum of the delays of each link.
Question 10
[am4show have=’p2;’]Refer to the exhibit.
Which three EIGRP routes will be present in the router R4’s routing table? (Choose three)
A. 172.16.1.0/24
B. 10.1.10.0/30
C. 10.0.0.0/8
D. 10.1.11.0/30
E. 172.16.0.0/16
F. 192.168.1.0/24
Answer: C E F[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]What does a router do if it has no EIGRP feasible successor route to a destination network and the successor route to that destination network is in active status?
A. It routes all traffic that is addressed to the destination network to the interface indicated in the routing table.
B. It sends a copy of its neighbor table to all adjacent routers.
C. It sends a multicast query packet to all adjacent neighbors requesting available routing paths to the destination network.
D. It broadcasts Hello packets to all routers in the network to re-establish neighbor adjacencies.
Answer: C[/am4show]
Explanation
When a router has no EIGRP feasible successor and the successor route to that destination network is in active status (the successor route is down, for example) a route recomputation occurs. A route recomputation commences with a router sending a query packet to all neighbors. Neighboring routers can either reply if they have feasible successors for the destination or optionally return a query indicating that they are performing a route recomputation. While in Active state, a router cannot change the next-hop neighbor it is using to forward packets. Once all replies are received for a given query, the destination can transition to Passive state and a new successor can be selected.
(Reference: http://www.cisco.com/en/US/tech/tk365/technologies_tech_note09186a0080093f07.shtml#rout_states)
Question 2
[am4show have=’p2;’]Which statement describes an EIGRP feasible successor route?
A. A primary route, added to the routing table
B. A backup route, added to the routing table
C. A primary route, added to the topology table
D. A backup route, added to the topology table
Answer: D[/am4show]
Question 3
[am4show have=’p2;’]Refer to the exhibit. How will the router handle a packet destined for 192.0.2.156?
A. The router will drop the packet.
B. The router will return the packet to its source.
C. The router will forward the packet via Serial2.
D. The router will forward the packet via either Serial0 or Serial1.
Answer: C[/am4show]
Explanation
From the output we see a line “Gateway of last resort is 192.168.4.1 to network 0.0.0.0”. Gateway of last resort refers to the next-hop router of a router’s current default route. Therefore all the traffic through this router to destination networks not matching any other networks or subnets in the routing table will be sent to 192.168.4.1 (which is on Serial2) -> packet destined for 192.0.2.156 (or an unknown destination) will be forwarded via Serial2.
An weird thing in the output above is the missing of the asterisk mask (*) which represents for the candidate default route. To set the “Gateway of last resort is 192.168.4.1 to network 0.0.0.0” as the output above we can use these commands:
ip route 0.0.0.0 0.0.0.0 192.168.4.1
ip default-network 192.168.4.0
But these commands will create an static routing in the routing table with an asterisk mask. Maybe the output shown above is missing that route.
For more information about the command ip default-network please visit: http://www.cisco.com/en/US/tech/tk365/technologies_tech_note09186a0080094374.shtml.
Question 4
[am4show have=’p2;’]Refer to the exhibit. From RouterA, a network administrator is able to ping the serial interface of RouterB but unable to ping any of the subnets attached to RouterB. Based on the partial outputs in the exhibit, what could be the problem?
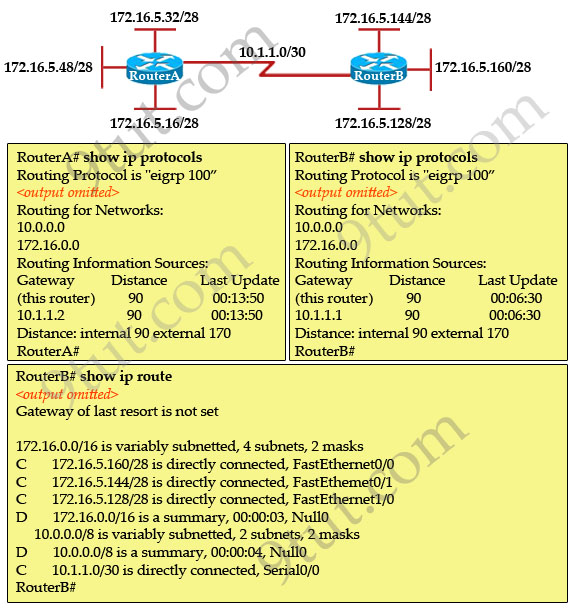
A. EIGRP does not support VLSM.
B. The EIGRP network statements are incorrectly configured.
C. The IP addressing on the serial interface of RouterA is incorrect.
D. The routing protocol has summarized on the classful boundary.
E. EIGRP has been configured with an invalid autonomous system number.
Answer: D[/am4show]
Explanation
From the output of “show ip route” command on RouterB, we learn that RouterB does not learn any networks in RouterA. Also the “172.16.0.0/26 is a summary, 00:00:03, Null0” line tells us this netwok is summarized.
Note: EIGRP performs auto-summarization each time it crosses a border between two major networks. For example, RouterA has networks of 172.16.x.x. It will perform auto-summarization when sending over network 10.1.1.0/30, which is in different major network (172.16.0.0/16 and 10.0.0.0/8 are called major networks in this case).
Question 5
[am4show have=’p2;’]Refer to the exhibit. The Lakeside Company has the internetwork in the exhibit. The Administrator would like to reduce the size of the routing table to the Central Router. Which partial routing table entry in the Central router represents a route summary that represents the LANs in Phoenix but no additional subnets?
A – 10.0.0.0 /22 is subnetted, 1 subnet
D 10.0.0.0 [90/20514560] via 10.2.0.2 6w0d, serial 0/1
B – 10.0.0.0 /28 is subnetted, 1 subnet
D 10.2.0.0 [90/20514560] via 10.2.0.2 6w0d, serial 0/1
C – 10.0.0.0 /30 is subnetted, 1 subnet
D 10.2.2.0 [90/20514560] via 10.2.0.2 6w0d, serial 0/1
D – 10.0.0.0 /22 is subnetted, 1 subnet
D 10.4.0.0 [90/20514560] via 10.2.0.2 6w0d, serial 0/1
E – 10.0.0.0 /28 is subnetted, 1 subnet
D 10.4.4.0 [90/20514560] via 10.2.0.2 6w0d, serial 0/1
F – 10.0.0.0 /30 is subnetted, 1 subnet
D 10.4.4.4 [90/20514560] via 10.2.0.2 6w0d, serial 0/1
Answer: D[/am4show]
Explanation
All the above networks can be summarized to 10.0.0.0 network but the question requires to “represent the LANs in Phoenix but no additional subnets” so we must summarized to 10.4.0.0 network. The Phoenix router has 4 subnets so we need to “move left” 2 bits of “/24”-> /22 is the best choice -> D is correct.
Question 6
[am4show have=’p2;’]The company uses EIGRP as the routing protocol.
R3# show ip route
Gateway of last resort is not set
192 168.20.0/24 is variably subnetted, 6 subnets, 2 masks
D 192.168.20.64/26 [90/2195456] via 192.168.20.9, 00:03:31, Serial0/0
D 192.168.20.0/30 [90/2681856] via 192.168.20.9, 00:03:31, Serial0/0
C 192.168.20.4/30 is directly connected, Serial 0/1
C 192.168.20.8/30 is directly connected, Serial 0/0
C 192.168.20.192/26 is directly connected, FastEthernet0/0
D 192.168.20.128/26 [90/2195456] via 192.168.20.5,00:03 31, Serial 0/1
What path will packets take from a host on 192.168.20.192/26 network to a host on the LAN attached to router R1?
A. The path of the packets will be R3 to R2 to R1.
B. The path of the packets will be R3 to R1 to R2.
C. The path of the packets will be both R3 to R2 to R1 and R3 to R1.
D. The path of the packets will be R3 to R1.
Answer: D[/am4show]
Explanation
From the line “D 192.168.20.64/26 [90/2195456] via 192.168.20.9, 00:03:31, Serial0/0″ we can see the IP address 192.168.20.9 belongs to network 192.168.20.8/30 and this network is between R1 and R3 -> Packet from 192.168.20.192/26 network destined to a host on the LAN attached to router R1 will go directly from R3 to R1.
Question 7
[am4show have=’p2;’]Which statements are true about EIGRP successor routes? (Choose two)
A. A successor route is used by EIGRP to forward traffic to a destination.
B. Successor routes are saved in the topology table to be used if the primary route fails.
C. Successor routes are flagged as “active” in the routing table.
D. A successor route may be backed up by a feasible successor route.
E. Successor routes are stored in the neighbor table following the discovery process.
Answer: A D[am4show have=’p2;’]
Explanation
C is not correct because successor routes are not flagged as “active”, they are always the best route to reach remote networks and are always used to send packets.
A and D are correct because successor route is the best and primary route to a remote network. It is stored in the routing table and topology table. If this route fails, a backup route (called feasible successor route) in the topology table will be used to route traffic to a destination.
E is not correct because neighbor table only contains a list of directly connected EIGRP routers that have an adjacency with this router, it doesn’t contain successor routes.
Question 8
[am4show have=’p2;’]What address is a feasible successor?
A. 172.16.4.0
B. 10.1.4.4
C. 10.1.2.2
D. 172.16.3.0
Answer: C[/am4show]
Question 9
[am4show have=’p2;’]A network administrator is troubleshooting an EIGRP problem on a router and needs to confirm the IP addresses of the devices with which the router has established adjacency. The retransmit interval and the queue counts for the adjacent routers also need to be checked.
What command will display the required information?
A. Router# show ip eigrp topology
B. Router# show ip eigrp interfaces
C. Router# show ip eigrp adjacency
D. Router# show ip eigrp neighbors
Answer: D[/am4show]
Explanation
Below is an example of the “show ip eigrp neighbors” command (from 9tut.com)
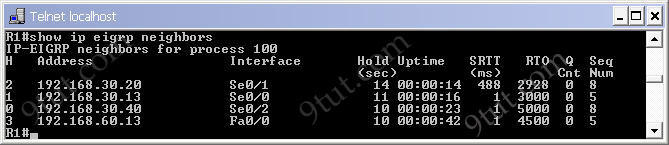
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which routing protocols are compatible with stubs? (Choose two)
A. OSPF
B. EIGRP
C. EGP
D. BGP
E. IS-IS
F. RIP
Answer: A B[/am4show]
Question 2
[am4show have=’p2;’]Which three checks must you perform when troubleshooting EIGRPv6 adjacencies? (Choose three)
A. Verify that IPv6 is enabled.
B. Verify that the network command has been configured.
C. Verify that auto summary is enabled.
D. Verify that the interface is up.
E. Verify that an IPv4 address has been configured.
F. Verify that the router ID has been configured.
Answer: A D F[/am4show]
Question 3
[am4show have=’p2;’]Which command do you enter to view EIGRPv6 adjacencies?
A. show ipv6 eigrp 1 interface
B. show ipv6 route eigrp
C. show ipv6 eigrp neighbors
D. show running-configuration eigrp
Answer: C[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which two components are used to identify a neighbor in a BGP configuration? (Choose two)
A. autonomous system number
B. version number
C. router ID
D. subnet mask
E. IP address
Answer: A E[/am4show]
Explanation
This is an example of how to configure BGP neighbor between two routers (suppose all interfaces are configured correctly)

| R1(config)#router bgp 1 R1(config-router)#neighbor 11.0.0.2 remote-as 2 |
R2(config)#router bgp 2 R2(config-router)#neighbor 11.0.0.1 remote-as 1 |
So as you see, we need the neighbor’s IP address and neighbor’s AS number for the BGP neighbor relationship.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which statement about the IP SLAs ICMP Echo operation is true?
A. The frequency of the operation specified in milliseconds.
B. It is used to identify the best source interface from which to send traffic.
C. It is configured in enable mode.
D. It is used to determine the frequency of ICMP packets.
Answer: D[/am4show]
Explanation
The ICMP Echo operation measures end-to-end response time between a Cisco router and any devices using IP. Response time is computed by measuring the time taken between sending an ICMP Echo request message to the destination and receiving an ICMP Echo reply. Many customers use IP SLAs ICMP-based operations, in-house ping testing, or ping-based dedicated probes for response time measurements.
Question 2
[am4show have=’p2;’]Which statement about the IP SLAs ICMP Echo operation is true?
A. It is configured in enable mode.
B. It is used to determine the one-way delay between devices
C. It is used to identify the best source interface from which to send traffic to a destination.
D. The frequency of the operation is specified in milliseconds.
Answer: B[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which protocol authenticates connected devices before allowing them to access the LAN?
A. 802.1d
B. 802.11
C. 802.1w
D. 802.1x
Answer: D[/am4show]
Explanation
802.1x is an IEEE Standard for port-based Network Access Control (PNAC). It is part of the IEEE 802.1 group of networking protocols. It provides an authentication mechanism to devices wishing to attach to a LAN.
Question 2
[am4show have=’p2;’]What is a difference between TACACS+ and RADIUS in AAA?
A. Only TACACS+ allows for separate authentication.
B. Only RADIUS encrypts the entire access-request packet.
C. Only RADIUS uses TCP.
D. Only TACACS+ couples authentication and authorization.
Answer: A[/am4show]
Explanation
TACACS+ is an AAA protocol developed by Cisco. TACACS+ separates the authentication, authorization, and accounting steps. This architecture allows for separate authentication solutions while still using TACACS+ for authorization and accounting. For example, it is possible to use the Kerberos Protocol for authentication and TACACS+ for authorization and accounting. After an AAA client passes authentication through a Kerberos server, the AAA client requests authorization information from a TACACS+ server without the necessity to re-authenticate the AAA client by using the TACACS+ authentication mechanism.
Authentication and authorization are not separated in a RADIUS transaction. When the authentication request is sent to a AAA server, the AAA client expects to have the authorization result sent back in reply.
Question 3
[am4show have=’p2;’]What can be done to secure the virtual terminal interfaces on a router? (Choose two)
A. Administratively shut down the interface.
B. Physically secure the interface.
C. Create an access list and apply it to the virtual terminal interfaces with the access-group command.
D. Configure a virtual terminal password and login process.
E. Enter an access list and apply it to the virtual terminal interfaces using the access-class command.
Answer: D E[/am4show]
Explanation
It is a waste to administratively shut down the interface. Moreover, someone can still access the virtual terminal interfaces via other interfaces -> A is not correct.
We can not physically secure a virtual interface because it is “virtual” -> B is not correct.
To apply an access list to a virtual terminal interface we must use the “access-class” command. The “access-group” command is only used to apply an access list to a physical interface -> C is not correct; E is correct.
The most simple way to secure the virtual terminal interface is to configure a username & password to prevent unauthorized login -> D is correct.
Question 4
[am4show have=’p2;’]Which protocol is an open standard protocol framework that is commonly used in VPNs, to provide secure end-to-end communications?
A. RSA
B. L2TP
C. IPsec
D. PPTP
Answer: C[/am4show]
Explanation
One of the most widely deployed network security technologies today is IPsec over VPNs. It provides high levels of security through encryption and authentication, protecting data from unauthorized access.
Question 5
[am4show have=’p2;’]Which IPsec security protocol should be used when confidentiality is required?
A. MD5
B. PSK
C. AH
D. ESP
Answer: D[/am4show]
Question 6
[am4show have=’p2;’]Which three options are types of Layer 2 network attack? (Choose three.)
A. ARP attacks
B. brute force attacks
C. spoofing attacks
D. DDOS attacks
E. VLAN hopping
F. botnet attacks
Answer: A C E[/am4show]
Question 7
[am4show have=’p2;’]Which option describes a drawback of proxy ARP?
A. It overwrites MAC addresses
B. It can make it more difficult for the administrator to locale device misconfigurations
C. It dynamically establishes layer 2 tunneling protocol which increase network overhead
D. If proxy ARP is configured on multiple devices , the internal L2 network may become vulnerable to DDOS
Answer: D[/am4show]
Question 8
[am4show have=’p2;’]What type of attack is when trusted source replace MAC tables with untrusted?
A. DHCP snooping
B. port snooping
C.
D.
Answer: A[/am4show]
Question 9
[am4show have=’p2;’]Which three response does TACAS+ give while querying..something like that. (Choose three)
A. error
B. accept
C. continue
D. persist
E. fault
Answer: A B C[/am4show]
Question 10
[am4show have=’p2;’]Which feature can validate address requests and filter out invalid messages?
A. IP Source Guard
B. port security
C. DHCP snooping
D. dynamic ARP inspection
Answer: C[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]The following configuration is applied to a Layer 2 Switch:
interface fastethernet 0/4
switchport mode access
switchport port-security
switchport port-security mac-address 0000.1111.1111
switchport port-security maximum 2
What is the result of the above configuration being applied to the switch?
A. A host with a mac address of 0000.1111.1111 and up to two other hosts can connect to FastEthernet 0/4 simultaneously
B. A host with a mac address of 0000.1111.1111 and one other host can connect to FastEthernet 0/4 simultaneously
C. Violating addresses are dropped and no record of the violation is kept
D. The switch can send an SNMP message to the network management station
E. The port is effectively shutdown
Answer: B[/am4show]
Question 2
[am4show have=’p2;’]Refer to the exhibit. Which of these correctly describes the results of port security violation of an unknown packet?
| Switch(config)#interface fastethernet 0/1 Switch(config-if)#switchport mode access Switch(config-if)#switchport port-security Switch(config-if)#switchport port-security maximum 3 Switch(config-if)#switchport port-security mac-address sticky Switch(config-if)#end |
A. port enabled; unknown packets dropped; no SNMP or syslog messages
B. port enabled; unknown packets dropped; SNMP or syslog messages
C. port disabled; no SNMP or syslog messages
D. port disabled; SNMP or syslog messages
Answer: D[/am4show]
Explanation
The default violation mode is shutdown, which will shutdown the port when the maximum number of secure MAC addresses is exceeded. It also sends an SNMP trap, logs a syslog message, and increments the violation counter.
The three violation modes are listed below:
+protect – When the number of secure MAC addresses reaches the limit allowed on the port, packets with unknown source addresses are dropped until you remove a sufficient number of secure MAC addresses or increase the number of maximum allowable addresses. You are not notified that a security violation has occurred.
+restrict – When the number of secure MAC addresses reaches the limit allowed on the port, packets with unknown source addresses are dropped until you remove a sufficient number of secure MAC addresses or increase the number of maximum allowable addresses. In this mode, you are notified that a security violation has occurred. Specifically, an SNMP trap is sent, a syslog message is logged, and the violation counter increments.
+shutdown – In this mode, a port security violation causes the interface to immediately become error-disabled, and turns off the port LED. It also sends an SNMP trap, logs a syslog message, and increments the violation counter. When a secure port is in the error-disabled state, you can bring it out of this state by entering the errdisable recovery cause psecure-violation global configuration command, or you can manually re-enable it by entering the shutdown and no shutdown interface configuration commands. This is the default mode.
(Reference: http://www.cisco.com/en/US/docs/switches/lan/catalyst6500/ios/12.2SX/configuration/guide/port_sec.html)
Question 3
[am4show have=’p2;’]Refer to the exhibit. What three actions will the switch take when a frame with an unknown source MAC address arrives at the interface? (Select three)
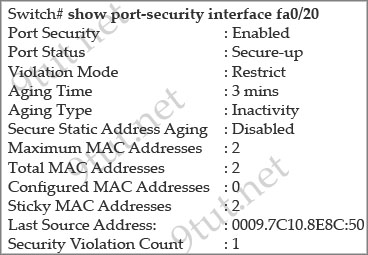
A. Send an SNMP trap.
B. Send a syslog message.
C. Increment the Security Violation counter.
D. Forward the traffic.
E. Write the MAC address to the startup-config.
F. Shut down the port.
Answer: A B C[/am4show]
Explanation
Notice that the Violation Mode is Restrict. In this mod, when the number of port secure MAC addresses reaches the maximum limit allowed on the port, packets with unknown source addresses are dropped. You have to remove the secure mac-addresses below the maximum allowed number in order to learn a new MAC or allowing a host on the port. Also a SNMP trap is sent, a syslog message is logged in the syslog server and the violation counter increases.
(Reference: http://www.cisco.com/en/US/docs/switches/lan/catalyst6500/ios/12.2SX/configuration/guide/port_sec.html)
Question 4
[am4show have=’p2;’]A network administrator needs to configure port security on a switch. Which two statements are true? (Choose two)
A. The network administrator can apply port security to dynamic access ports
B. The network administrator can configure static secure or sticky secure mac addresses in the voice vlan.
C. The sticky learning feature allows the addition of dynamically learned addresses to the running configuration.
D. The network administrator can apply port security to EtherChannels.
E. When dynamic mac address learning is enabled on an interface, the switch can learn new addresses up to the maximum defined.
Answer: C E[/am4show]
Explanation
Follow these guidelines when configuring port security:
+ Port security can only be configured on static access ports, trunk ports, or 802.1Q tunnel ports. -> A is not correct.
+ A secure port cannot be a dynamic access port.
+ A secure port cannot be a destination port for Switched Port Analyzer (SPAN).
+ A secure port cannot belong to a Fast EtherChannel or Gigabit EtherChannel port group. -> D is not correct
+ You cannot configure static secure or sticky secure MAC addresses on a voice VLAN. -> B is not correct.
+ When you enable port security on an interface that is also configured with a voice VLAN, you must set the maximum allowed secure addresses on the port to at least two.
+ If any type of port security is enabled on the access VLAN, dynamic port security is automatically enabled on the voice VLAN.
+ When a voice VLAN is configured on a secure port that is also configured as a sticky secure port, all addresses seen on the voice VLAN are learned as dynamic secure addresses, and all addresses seen on the access VLAN (to which the port belongs) are learned as sticky secure addresses.
+ The switch does not support port security aging of sticky secure MAC addresses.
+ The protect and restrict options cannot be simultaneously enabled on an interface.
Note: Dynamic access port or Dynamic port VLAN membership must be connected to an end station. This type of port can be configured with the “switchport access vlan dynamic” command in the interface configuration mode. Please read more about Dynamic access port here: http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3550/software/release/12-1_19_ea1/configuration/guide/3550scg/swvlan.html#wp1103064
Question 5
[am4show have=’p2;’]Refer to the exhibit. The following commands are executed on interface fa0/1 of 2950Switch.
2950Switch(config-if)#switchport port-security
2950Switch(config-if)#switchport port-security mac-address sticky
2950Switch(config-if)#switchport port-security maximum 1
The Ethernet frame that is shown arrives on interface fa0/1. What two functions will occur when this frame is received by 2950Switch? (Choose two)
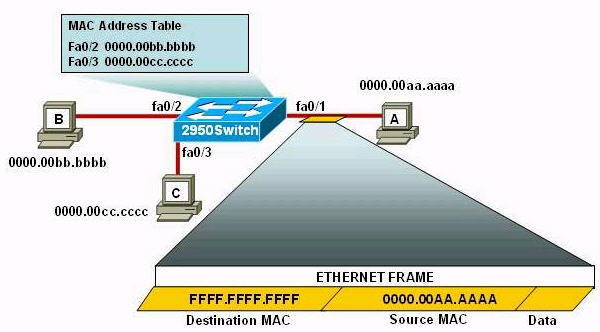
A. The MAC address table will now have an additional entry of fa0/1 FFFF.FFFF.FFFF.
B. Only host A will be allowed to transmit frames on fa0/1.
C. This frame will be discarded when it is received by 2950Switch.
D. All frames arriving on 2950Switch with a destination of 0000.00aa.aaaa will be forwarded out fa0/1.
E. Hosts B and C may forward frames out fa0/1 but frames arriving from other switches will not be forwarded out fa0/1.
F. Only frames from source 0000.00bb.bbbb, the first learned MAC address of 2950Switch, will be forwarded out fa0/1.
Answer: B D[/am4show]
Explanation
The first command 2950Switch(config-if)#switchport port-security is to enable the port-security in a switch port.
In the second command 2950Switch(config-if)#switchport port-security mac-address sticky, we need to know the full syntax of this command is switchport port-security mac-address sticky [MAC]. The STICKY keyword is used to make the MAC address appear in the running configuration and you can save it for later use. If you do not specify any MAC addresses after the STICKY keyword, the switch will dynamically learn the attached MAC Address and place it into your running-configuration. In this case, the switch will dynamically learn the MAC address 0000.00aa.aaaa of host A and add this MAC address to the running configuration.
In the last command 2950Switch(config-if)#switchport port-security maximum 1 you limited the number of secure MAC addresses to one and dynamically assigned it (because no MAC address is mentioned, the switch will get the MAC address of the attached MAC address to interface fa0/1), the workstation attached to that port is assured the full bandwidth of the port.Therefore only host A will be allowed to transmit frames on fa0/1 -> B is correct.
After you have set the maximum number of secure MAC addresses for interface fa0/1, the secure addresses are included in the “Secure MAC Address” table (this table is similar to the Mac Address Table but you can only view it with the show port-security address command). So in this question, although you don’t see the MAC address of host A listed in the MAC Address Table but frames with a destination of 0000.00aa.aaaa will be forwarded out of fa0/1 interface -> D is correct.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which version of SNMP first allowed user-based access?
A. SNMPv3 with RBAC
B. SNMPv3
C. SNMPv1
D. SNMPv2
Answer: B[/am4show]
Explanation
The user-based access control implemented by SNMPv3 is based on contexts and user names, rather than on IP addresses and community strings. It is a partial implementation of the view-based access control model (VACM).
Question 2
[am4show have=’p2;’]What is the first step you perform to configure an SNMPv3 user?
A. Configure server traps.
B. Configure the server group.
C. Configure the server host.
D. Configure the remote engine ID.
Answer: B[/am4show]
Explanation
The first step we need to do when configuring an SNMPv3 user is to configure the server group to enable authentication for members of a specified named access list via the “snmp-server group” command. For example:
| Router(config)# snmp-server group MyGroup v3 auth access snmp_acl |
In this example, the SNMP server group MyGroup is configured to enable user authentication for members of the named access list snmp_acl.
Question 3
[am4show have=’p2;’]Which feature can you use to restrict SNMP queries to a specific OID tree?
A. a server group
B. a view record
C. a community
D. an access group
Answer: B[/am4show]
Question 4
[am4show have=’p2;’]What is the minimum command to turn on encryption on SNMP?
A. SNMPV3authpriv
B. SMNPV3authnopriv
C. SNMPV3noauthpriv
D. SMNPV2authnopriv
E. SNMPV2NOAUTHPRIV
F. SNMPV2AUTHNOPRIV
Answer: A[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which feature can you use to monitor traffic on a switch by replicating it to another port or ports on the same switch?
A. copy run start
B. traceroute
C. the ICMP Echo IP SLA
D. SPAN
Answer: D[/am4show]
Explanation
Switched Port Analyzer (SPAN) is used to analyze network traffic passing through ports on a switch. For example we can configure the Switch to monitor its interface Fa0/0, which connects to the Core, by sending all traffic to/from Fa0/0 to its Fa0/1 interface. At Fa0/1 interface we connect to a computer and use such a software like Wireshark to capture the packets.
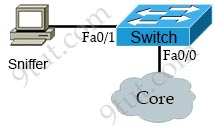
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
If you configure syslog messages without specifying the logging trap level, which log messages will the router send?
A. error conditions only
B. warning and error conditions only
C. normal but significant conditions only
D. all levels except debugging
E. informational messages only
Answer: D
Explanation
Syslog levels are listed below
| Level | Keyword | Description |
| 0 | emergencies | System is unusable |
| 1 | alerts | Immediate action is needed |
| 2 | critical | Critical conditions exist |
| 3 | errors | Error conditions exist |
| 4 | warnings | Warning conditions exist |
| 5 | notification | Normal, but significant, conditions exist |
| 6 | informational | Informational messages |
| 7 | debugging | Debugging messages |
The highest level is level 0 (emergencies). The lowest level is level 7. By default, the router will send informational messages (level 6). That means it will send all the syslog messages from level 0 to 6.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which two pieces of information are provided by the “show controllers serial 0” command? (Choose two)
A. the type of cable that is connected to the interface.
B. The uptime of the interface
C. the status of the physical layer of the interface
D. the full configuration of the interface
E. the interface’s duplex settings
Answer: A C[/am4show]
Explanation
Below is an example of the output of this command:
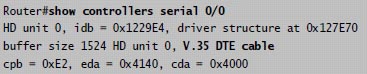
The “show controllers serial …” command tells us about the type of the cable (in the case V.35 DTE cable) and the status of the physical layer of the interface. In above output we learn that there is an cable attached on S0/0 interface. If no cable is found we will see the line “No DTE cable” instead.
Question 2
[am4show have=’p2;’]What is the best way to verify that a host has a path to other hosts in different networks?
A. Ping the loopback address.
B. Ping the default gateway.
C. Ping the local interface address.
D. Ping the remote network.
Answer: D[/am4show]
Question 3
[am4show have=’p2;’]While you were troubleshooting a connection issue, a ping from one VLAN to another VLAN on the same switch failed. Which command verifies that IP routing is enabled on interfaces and the local VLANs are up?
A. show ip interface brief
B. show ip nat statistics
C. show ip statistics
D. show ip route
Answer: D[/am4show]
Explanation
The “show ip nat statistics” only gives us information about NAT translation. We cannot know if IP routing is enabled or the VLANs are up not not.
The “show ip statistics” command does not exist.
With the “show ip interface brief” we can see if the interface VLANs are up or not but cannot see if IP routing is enabled or not. So let’s see what information can be learned with the “show ip route” command.
By using the command “show ip route” we will learn if IP routing is enabled. If it is not enabled we will see this output:
After enabling ip routing (via the “ip routing” in global configuration mode) we can see all the interfaces. For example:
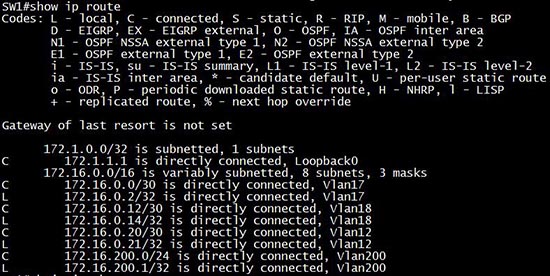
If we shut down an interface VLAN (Vlan18)
Sw1(config)#interface vlan 18
Sw1(config-if)#shutdown
then we will not see it in the routing table any more.
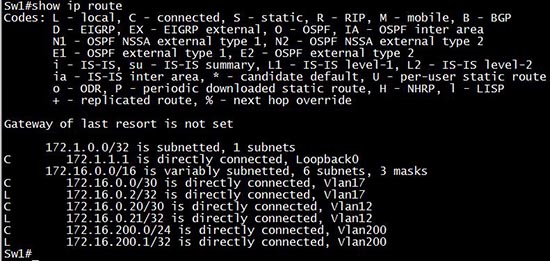
Therefore if the statement “local VLANs are up” means “the interface VLANs are up” then the “show ip route” is the best answer in this case.
Note: The IOS used to test is IOSv15.1
Question 4
[am4show have=’p2;’]Which command would you use on a Cisco router to verify the Layer 3 path to a host?
A. tracert address
B. traceroute address
C. telnet address
D. ssh address
Answer: B[/am4show]
Explanation
To check the connectivity between a host and a destination (through some networks) we can use both “tracert” and “traceroute” commands. But the difference between these two commands is the “tracert” command can display a list of near-side router interfaces in the path between the source and the destination. The “traceroute” command has the same function of the “tracert” command but it is used on Cisco routers only, not on a PC -> B is correct.
Question 5
[am4show have=’p2;’]A network administrator has configured access list 173 to prevent Telnet and ICMP traffic from reaching a server with the address of 192.168.13.26. Which commands can the administrator issue to verify that the access list is working properly? (Choose three)
A. Router# ping 192.168.13.26
B. Router# debug access-list 173
C. Router# show open ports 192.168.13.26
D. Router# show access-lists
E. Router# show ip interface
Answer: A D E[/am4show]
Explanation
Answer B is not correct because “debug access-list ” command does not exist.
The reason answer E is correct because this command can help us see if the access-list was applied to the correct interface or not.
Question 6
[am4show have=’p2;’]Refer to the exhibit:
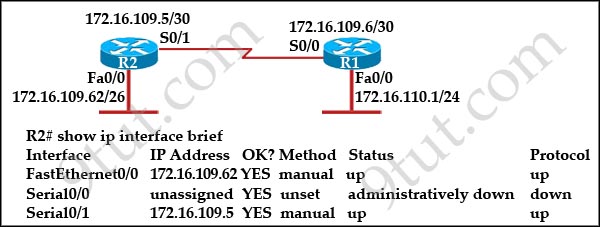
Assuming that the entire network topology is shown, what is the operational status of the interfaces of R2 as indicated by the command output shown?
A. One interface has a problem.
B. Two interfaces have problems.
C. The interfaces are functioning correctly.
D. The operational status of the interfaces cannot be determined from the output shown.
Answer: C[/am4show]
Explanation
The subnet of Fa0/0 of R2 is 172.16.109.0/26 (range from 172.16.109.0 to 172.16.109.63) which covers the subnet of S0/1 interface 172.16.109.4/30 so in fact the answer C is not correct. But from the output of the “show ip interface brief” command we see both Fa0/0 and S0/1 interfaces’ statuses are ‘up/up’ -> they are working normally. So we think there is a typo in the subnet mask of Fa0/0. It should not be ‘/26’ but longer one, ‘/28’, for example. So you should still choose answer C in this question.
Question 7
[am4show have=’p2;’]Refer to the exhibit. Hosts in network 192.168.2.0 are unable to reach hosts in network 192.168.3.0. Based on the output from RouterA, what are two possible reasons for the failure? (Choose two)
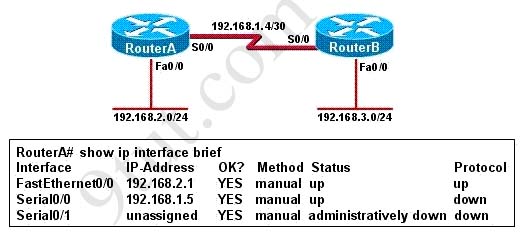
A. The cable that is connected to S0/0 on RouterA is faulty.
B. Interface S0/0 on RouterB is administratively down.
C. Interface S0/0 on RouterA is configured with an incorrect subnet mask.
D. The IP address that is configured on S0/0 of RouterB is not in the correct subnet.
E. Interface S0/0 on RouterA is not receiving a clock signal from the CSU/DSU.
F. The encapsulation that is configured on S0/0 of RouterB does not match the encapsulation that is configured on S0/0 of RouterA.
Answer: E F[/am4show]
Explanation
From the output we see the Serial0/0 of RouterA is in “status up/protocol down” state which indicates a Layer 2 problem so the problem can be:
+ Keepalives mismatch
+ Encapsulation mismatch
+ Clocking problem
Question 8
[am4show have=’p2;’]Which interface counter can you use to diagnose a duplex mismatch problem?
A. runts
B. CRC errors
C. no carrier
D. late collisions
E. deferred
F. giants
Answer: B[/am4show]
Explanation
At the end of each frame there is a Frame Check Sequence (FCS) field. FCS can be analyzed to determine if errors have occurred. FCS uses cyclic redundancy check (CRC) algorithm to detect errors in the transmitted frames. Before sending data, the sending host generates a CRC based on the header and data of that frame. When this frame arrives, the receiving host uses the same algorithm to generate its own CRC and compare them. If they do not match then a CRC error will occur. CRC errors (and input errors in general) are often caused by duplex mismatch or Physical layer issues (like faulty cable, faulty network interface card or excessive interference during the transmission,…).
On an Ethernet connection, a duplex mismatch is a condition where two connected devices operate in different duplex modes, that is, one operates in half duplex while the other one operates in full duplex.
Note:
+ Runts are frames which do not meet the minimum frame size of 64 bytes. Runts are usually created by collisions.
+ Giants: frames that are larger than 1,518 bytes
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which two Cisco IOS commands, used in troubleshooting, can enable debug output to a remote location? (Choose two)
A. no logging console
B. logging host ip-address
C. terminal monitor
D. show logging | redirect flashioutput.txt
E. snmp-server enable traps syslog
Answer: B C[/am4show]
Question 2
[am4show have=’p2;’]Routers R1 and R2 are on the same network segment, and both routers use interface GigabitEthernet0/0. If R1 loses communication to R2, which two items should you check as you begin troubleshooting? (Choose two)
A. Verify that R2 is using 802.1q encapsulation.
B. Verify that the GigabitEthernet0/0 interfaces on R1 and R2 are configured with the same subnet mask.
C. Verify that the R1 GigabitEthernet0/0 interface is up and line protocol is down.
D. Verify that R1 and R2 both are using HDLC encapsulation.
E. Verify that R1 GigabitEthernet0/0 interface is up and line protocol is up.
Answer: B E[/am4show]
Question 3
[am4show have=’p2;’]After you configure a new router to connect to a host through the GigabitEthernet0/0 port of the router, you log in to the router and observe that the new link is down. Which action corrects the problem?
A. Use a crossover cable between the host and R1.
B. Use a straight through cable between the host and R1.
C. Configure the host to use R1 as the default gateway.
D. Use a rollover cable between the host and R1.
Answer: A[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which command enables IPv6 forwarding on a Cisco router?
A. ipv6 local
B. ipv6 host
C. ipv6 unicast-routing
D. ipv6 neighbor
Answer: C[/am4show]
Explanation
An example of configuring RIPng (similar to RIPv2 but is used for IPv6) is shown below:
Router(config)#ipv6 unicast-routing (Enables the forwarding of IPv6 unicast datagrams globally on the router)
Router(config)#interface fa0/0
Router(config-if)#ipv6 rip 9tut enable (9tut is the process name of this RIPng)
Question 2
[am4show have=’p2;’]The network administrator has been asked to give reasons for moving from IPv4 to IPv6. What are two valid reasons for adopting IPv6 over IPv4? (Choose two)
A. telnet access does not require a password
B. nat
C. no broadcast
D. change of destination address in the IPv6 header
E. change of source address in the IPv6 header
F. autoconfiguration
Answer: C F[/am4show]
Explanation
With IPv6, devices can build a link-local address automatically. But notice this address is only used for communications within the local subnetwork, routers do not forward these addresses.
Question 3
[am4show have=’p2;’]Which of these represents an IPv6 link-local address?
A. FE08::280e:611:a:f14f.3d69
B. FE81::280f.512b:e14f:3d69
C. FE80::380e:611a:e14f:3d69
D. FEFE:0345:5f1b::e14d:3d69
Answer: C[/am4show]
Explanation
The range of IPv6 link-local address (similar to the Windows auto-configuration IP address of 169.254.x.x.) is FE80::/10. For more information about IPv6, please read my IPv6 tutorial.
Question 4
[am4show have=’p2;’]Which three approaches can be used while migrating from an IPv4 addressing scheme to an IPv6 scheme? (Choose three)
A. enable dual-stack routing
B. configure IPv6 directly
C. configure IPv4 tunnels between IPv6 islands
D. use proxying and translation to translate IPv6 packets into IPv4 packets
E. statically map IPv4 addresses to IPv6 addresses
F. use DHCPv6 to map IPv4 addresses to IPv6 addresses
Answer: A C D[/am4show]
Note (14th-Dec-2018): These new questions were gathered from our candidates so please learn them well before taking the ICND1 exam:
Question 1
Syslog – what does not belong?
A. host name
B. severity
C. timestamp
D. message
Answer: A
Question 2
What does a switch use for communication between VLANs?
A. STP
B. CDP
C. VTP
D. Etherchannel
Answer: C
Question 3
What is the maximum size of an Ethernet frame that uses 802.1Q tagging?
A. 1514 bytes
B. 128 bytes
C. 68 bytes
D. 1522 bytes
Answer: D
Question 4
When configuring a default gateway, should it be ip route 0.0.0.0…. or serial 0/0 0.0.0.0…… – dont know answer
Question 5
Which option does the route 0.0.0.0/0 represent?
A. Route with the lowest administrative distance
B. Gateway of last resort
C. Null route
D. Empty routing table
Answer: B
Explanation
In this question only the “Gateway of last resort” answer is suitable. A Gateway of Last Resort or Default gateway is a route used by the router when no other known route exists to transmit the IP packet. Known routes are present in the routing table. Hence, any route not known by the routing table is forwarded to the default route.
In fact this question is a bit unclear. Maybe it implies “creating a static route to network 0.0.0.0 0.0.0.0 is another way to set the gateway of last resort on a router.”
Reference: https://www.cisco.com/c/en/us/support/docs/ip/routing-information-protocol-rip/16448-default.html
Question 6
What is the purpose of a standard access list?
A. to filter traffic based on destination address
B. to deny traffic
C. to filter traffic based on source address
Answer: C
Question 7
If you are in VLAN 10 and it gets a packet from VLAN 2 with 802.1q enabled, what does it do with the packet?
A. Drops the packet
B. forwards it to VLAN 2
C. configures the port to handle traffic from VLAN 2
D. adds it to the VLAN database
Answer: A
Question 8
Drag drop question about cable types
Answer:
Coaxial <-> TV connection
Twisted <-> 10/100/1000 base
Fiber <-> BASE-5 BX
USB <-> connects two computers
Crossed-over <-> devices of the same type
Question 9
Which forwarding technology stores destination addresses in the cache?
A. MPLS
B. Cisco express forwarding
C. Process switching
D. Fast switching
Answer: B
Question 10
Which type of network topology requires each network node to be connected to one another?
A. Ring
B. Star
C. Mesh
D. Bus
Answer: C
Question 11
A router receives identical prefixes from OSPF, EIGRP, RIP and the same route is configured statically. Which route does the router use to forward traffic?
A. Static route
B. RIP route
C. EIGRP route
D. OSPF route
Answer: A
Question 12
Which route is the most secured : connected route
Question 13
Which syslog severity level logs informational messages?
A. 2
B. 6
C. 4
D. 0
Answer: B
Question 14
Which option describes a standard role that a firewall plays in an enterprise network?
A. It can permit unauthorized packets to pass to less secure segments of the network
B. It can decide which packets can traverse from a less secure segment of the network to a more secure
C. It can forward packets based on rules that are predetermined by IEEE standards
D. It can deny all packets from entering an administrative domain.
Answer: B
Question 15
A question with the mac table on a switch with mac 1111:1111:1111 and port 0/1 and the question was asking : You received a packet with destination mac 1111:1111:1111 on port 0/1 , how does the switch will handle the frame.
Answer: The switch forwards the frame to port 0/1 only.
Question 16
What cable use in star topology? (Choose two)
A.10 base2
B.10 base5
C.100 base2
D.100base5
…
Answer: 10Base-T, 100Base-T and 1000Base-T
Question 17
What is the binary of the IPv6 multicast address
Answer: 11111111
Explanation
IPv6 multicast addresses are distinguished from unicast addresses by the value of the high-order octet of the addresses: a value of 0xFF (binary 11111111) identifies an address as a multicast address; any other value identifies an address as a unicast address
Question 18
What is the lowest AD (IS-IS, IBGP, EIGRP, RIPv2 or OSPF)?
Answer: EIGRP
Explanation
The Administrative Distances (AD) of popular routing protocols is shown below:
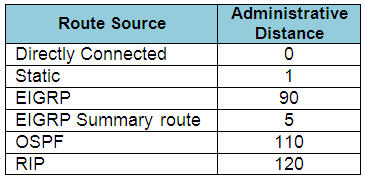
Note: For IS-IS, the AD is 115; Internal BGP (IBGP) is 200
Question 19
Assume all the routing protocol have the same length prefix, what would the router prefer?
A. OSPF
B. EIGRP
C. CONNECTED
D. BGP
Answer: C
Question 20
In which circumstances is static routing most useful?
A. On a stub network
B. On a large network that must share routes quickly between routers
C. On a network that experiences frequent link failures
D. On a network with frequent routing changes
Answers: A
Question 21
Which statement describes the dynamic route correctly?
A. more secure than static
B. high scaling for large network
C. easier to configure than static route
D. build for small network
Answer: B
Question 22
Which statement is correct when comparing dynamic route and static route?
A. static route is more secure
Question 23
What would the router use as metrics when having different routing protocol in the routing table
A. Prefix length
Question 24
Which of the following description is correct about DNS?
A. Host will sends a request to a DNS server…
Question 25
Which statement about standard access list is true?
A. They have an implicit permit statement at the end to allow all traffic
B. They can use either a wildcard mask or a subnet mask to identify host
C. They can be identified by a number from 1 to 99
D. They must be placed close to the source of traffic
Answer: C
Question 26
Which of the following item is used to establish telnet session by having the host name?
A. DNS lookup
B. Ping
C. Syslog
D. ARP
Answer: A
Question 27
Which of the following command can be use to access all the files in a system?
A. syslog
B. IFS
C. ping
D. NTP
Answer: B
Question 28
For which important purpose was IPv6 addressing developed?
A. To reduce the number of public IP addresses on the internet
B. To replace network address translation
C. To remove the need for classless inter-domain routing
D. To relieve the shortage of public IP addresses on the internet
Answer: D
Question 29
What does the 0.0.0.0/0 mean in a routing table?
A. wildcard
B. empty routing table
C. Null table
D. Gateway of last resort
Answer: should be default route
Question 30
A host is attempting to communicate with a server from an application layer. The connection has failed, what would be the first layer to start from the troubleshooting standpoint?
A. network
B. Application
C. physical
D. session
Answer: C
Question 31
[am4show have=’p2;’]The left describes the types of cables, while the right describes the purposes of the cables.
Drag the items on the left to the proper locations. (Not all items can be used.)
Answer:
+ switch access port to router: straight-through
+ switch to switch: crossover
+ PC COM to switch Console port: rollover[/am4show]
Explanation
To remember which type of cable you should use, follow these tips:
– To connect two serial interfaces of 2 routers we use serial cable
– To specify when we use crossover cable or straight-through cable, we should remember:
Group 1: Router, Host, Server
Group 2: Hub, Switch
One device in group 1 + One device in group 2: use straight-through cable
Two devices in the same group: use crossover cable
For example: we use straight-through cable to connect switch to router, switch to host, hub to host, hub to server… and we use crossover cable to connect switch to switch, switch to hub, router to router, host to host… )
Question 32
Which destination IP address can a host use to send one message to multiple devices across …?
A. 239.255.0.1
B. 172.20.1.0
C. 192.168.0.119
D. 127.0.0.1
Answer: A (multicast address)
Question 33
Which value is of primary importance when a router populates its routing table for unique routes?
A. Administrative distance
B. Prefix length
C. Network address
D. Metric
Answer: A
Explanation
Making a forwarding decision actually consists of three sets of processes: the routing protocols, the routing table, and the actual process which makes a forwarding decision and switches packets. The longest prefix match always wins among the routes actually installed in the routing table, while the routing protocol with the lowest administrative distance always wins when installing routes into the routing table.
Question 34
Which IPv6 address type is a public address?
A. Global unicast
B. Multicast
C. Link local
D. Unique-local
Answer: A
Question 35
How is the MAC address table of a switch populated?
A. When the switch receives an Ethernet frame with a new destination MAC address, it installs the destination MAC address and the ingress switch port in the MAC address table
B. When the switch receives an Ethernet frame with a new source MAC address, it installs the source MAC address and the ingress switch port in the MAC address table
C. When the switch receives an Ethernet frame with a new destination MAC address, it installs the destination MAC address and the egress switch port in the MAC address table
D. When the switch receives an Ethernet frame in which the source and destination MAC address are new, it installs the destination MAC address and the ingress switch port in the MAC address table
Answer: B
Explanation
A switch only learns (populates) its MAC address table with source MAC addresses only.
Question 36
Which statement describes the effect of exec-timeout 30 command?
A. The router disconnects the user session if it is inactive for 30 minutes
B. The router maintains a user session indefinitely after it is active for 30 mins
C. The router disconnects a user session if it is inactive for 30 seconds
D. The router maintains a user session indefinitely after it is active for 30 seconds.
Answer: A
Explanation
The “exec-timeout” command is used to configure the inactive session timeout on the console port or the virtual terminal. The syntax of this command is:
exec-timeout minutes [seconds]
Therefore we need to use the “exec-timeout 30” command to set the user inactivity timer to 30 minutes. To set the user inactivity timer to 30 seconds we use the “exec-timeout 0 30”.
Question 37
Which statement is true about port-security violations is true?
A. When a violation occurs on a switch port in restrict mode, the switch port continues to accept traffic from unknown MAC address until the administrator manually disables it.
B. When a violation occurs on a switch port in protect mode, it sends a syslog notification message
C. A port In the err-disabled state must be re-enabled manually, if recovery is disabled
D. When a switch port is in protect mode, it allows traffic from unknown MAC address until it has learned the maximum allowable number of MAC addresses
Answer: C
Question 38
Which statement is true about static and dynamic routing is true?
A. Only static routes are shared between connected interfaces
B. Dynamic routing is more scalable than static routing
C. Only dynamic routes are secure
D. Static routing is easier to maintain in a large network than dynamic routing.
Answer: B
Question 39
Which metric or metrics does RIP use to determine the routing table metric for a route?
A. Bandwidth and delay
B. Hop count
C. Bandwidth and hop count
D. Bandwidth
Answer: B
Question 40
Which network configuration allows a switch to send traffic from multiple VLANS over a single link to a router that routes between the VLANs?
A. Port channel
B. Router-on-a-stick
C. Virtual trunking
D. Spanning-tree
Answer: B
Question 41
Which statement about native VLAN traffic over 802.1Q trunk is true?
A. It is discarded by STP
B. It is placed is a high-priority queue
C. It is tagged with a value of 1
D. It is untagged
Answer: D
Question 42
Which feature allows a device to use a switch port that is configured for half-duplex to access the network?
A. Split horizon
B. CSMA/CD
C. IGMP
D. Port security
Answer: B
Explanation
CSMA/CD stands for Carrier Sense Multiple Access with Collision Detection. In an Ethernet LAN, before transmitting, a computer first listens to the network media. If the media is idle, the computer sends its data. If the media is not idle (another station is talking), the computer must wait for some time.
When a station transmits, the signal is referred to as a carrier. Carrier Sense means that before a station can send data onto an Ethernet wire, it have to listen to see if another “carrier” (of another station) is present. If another station is talking, this station will wait until there is no carrier present.
Multiple Access means that stations can access the network at any time. It is opposed to Token-Ring network where a station must have the “token” so that it can send data.
In short, CSMA/CD is the technology used for half-duplex switch port to transmit. CSMA/CD is not necessary for full-duplex switch port.
Question 43
Refer to the exhibit.
<exhibit missing>
If switch-A receives a frame with destination MAC address 0000.0000.0001 on its Fa0/1 interface, how does it process the frame?
A. It forwards the frame back out of interface Fa0/1
B. It floods the frame to all interfaces except Fa0/1
C. It holds the packet until the MAC address timer expires and then drops the frame
D. It drops the frame immediately
Answer: maybe B
Explanation
As the exhibit is missing so we can only guess. But B is the most suitable answer in all cases. If the MAC address 0000.0000.0001 is new to the switch (this MAC have not existed in the MAC address table) then surely the answer is B.
Question 44
When a router makes a routing decision for a packet that is received from one network and destined to another, which portion of the packet does it replace?
A. Layer 4 protocol
B. Layer 3 IP address
C. Layer 2 frame header and trailer
D. Layer 5 session
Answer: C
Explanation
During the transmission of a packet from source to destination, only Layer 2 information is replaced in the path. Layer 3 information remains the same (except when NAT is used).
Question 45
Which protocol can identify connected devices within a mixed-vendor infrastructure?
A. Virtual terminal protocol
B. Network time protocol
C. Link level discovery protocol
D. Cisco discovery protocol
Answer: C
Question 46
Which interface configuration is used with a router-on-a-stick configuration?
A. VRF
B. Subinterfaces
C. PIM sparse mode
D. Passive-interface
Answer: B
Question 47
You have configured the host computers on a campus LAN to receive their DHCP addresses from the local router to be able to browse their corporate site. Which statement about the network environment is true?
A. Two host computers may be assigned manually on each host
B. The DNS server must be configured manually on each host
C. It supports a DNS server for use by DHCP clients
D. The domain name must be configured locally on each host computer
Answer: C
Explanation
DHCP supports configuring a domain name to assign to the DHCP clients. For example:
Router(config)#ip dhcp pool CLIENTS
Router(dhcp-config)#domain-name 9tut.com
…
Question 48
Where is private IPv4 addressing used?
A. On the endpoints of a VPN tunnel that traverses outside an administrator domain
B. At a remote site that connects over public infrastructure to a hub
C. Within an enterprise
D. Over the internet
Answer: C
Question 49
Which protocol allows VLANs to be dynamically configured between multiple switches?
A. IGMP
B. STP
C. VTP
D. 802.1Q
Answer: C
Question 50
Client A cannot reach client B by its hostname. Which reason for the problem is most likely true?
A. The connected router is using the default domain lookup configuration
B. The hostname for client B is missing from the connected router
C. A DNS server has been misconfigured
D. Telnet has been disabled on the connected router.
Answer: C
Question 51
Which first step must a client perform to connect to an internal host when the hostname is known, but the IP address is unknown?
A. The client sends the host name in a DNS reply to a DNS server, and the DNS server responds with the host IP address
B. The client exchanges IP address information with a DNS server on the same LAN
C. The client looks up the hostname in the ARP table to determine the IP address
D. The client sends the host name in a DNS request to a DNS server, and the DNS server responds with the host IP address.
Answer: D
Explanation
When a client knew about the hostname but not the IP address, it needs to resolve the hostname to the IP address by sending a DNS request to its DNS server.
Notice that the ARP table is responsible for resolving IP address to MAC address only. It has nothing to do with the hostname.
==================New Questions added on 9th-Dec-2017==================
Question 52
Which route option can be used to back-up in case of fail?
Answer: floating route
Question 53
Which of the following is true about TCP and UDP?
Answer: only TCP order the transmission packets
Question 54
If a switch received a frame while forwarding others, how frame would be handled?
A. It will interrupt the frames
B. The switch will put the frame in a queue
C. Will be forwarded at the same time with the current frame
D. The new frame will forward first
Answer: C
Question 55
Which of the following true about access point?
A. It used physically to connect network devices
B. It is used as a router
C. Provide full duplex communication
D. It is a layer 2 device used to extend the LAN coverage to wireless devices
Answer: D
Question 56
Which of the following used to identify immediate destination?
A. Administrative distance
B. Metric
C. Next hop
D. Destination network
Answer: C
Question 57
Which of the following options could be used on router to prevent reassign IP address statically?
A. Pool
B. Lease
C. Client ID
D. Exclude address
Answer: D
Question 58
A router with a default setting deployed, how will act if it received mistype command?
A. Disable DNS look up
B. Recognizing the command
C. Try to resolve the command to an IP address
D. Try to correct the command
E. Show error message
Answer: C
Question 59
Which symbol ping of the following is for unknown packet?
A. .
B. *
C. ?
D. U
Answer: C
Explanation
The table below lists the possible output characters from the ping facility:
| Character | Description |
|---|---|
| ! | Each exclamation point indicates receipt of a reply. |
| . | Each period indicates the network server timed out while waiting for a reply. |
| U | A destination unreachable error PDU was received. |
| Q | Source quench (destination too busy). |
| M | Could not fragment. |
| ? | Unknown packet type. |
| & | Packet lifetime exceeded. |
Question 60
Which cables could be used for star topology? (Choose two)
A. 10 Base T
B. 100 Base T
C. 10 Base 5
D. 10 Base 2
Answer: A B
Question 61
Which of the following is true about dynamic route?
A. Reduce CPU of the network
B. More secure than static
C. Complicate the maintenance
D. Allow fast convergence when fail happen
Answer: D
Question 62
What RIPv2 use to elect of route?
A. Hop count
B. Administrative distance
C. Bandwidth
Answer: A
Question 63
Which of the following are two local host characters?
A. 32/prefix
B. 255.255.255.0
C. The administrative distance is 0
D. Dynamically learned
E. ?
Answer: A C
Question 64
Which attributes change all the path way (Choose two)
A. MAC destination address
B. MAC destination address
C. IP Source address
D. IP Source address
Answer: A B
Question 65
Why a host uses DNS server?
A. DNS client request to server
B. To resolve IP to FQDN
C. To resolve FQDN to IP
D. Assign IP
Answer: C
FQDN (Fully Qualified Domain Name)
E. Verify connection
==================New Questions added on 9th-Aug-2018==================
Question 66
What time zone is set by default on the router?
A. GMT
B. UMT
Answer: A
Explanation
By default, the router uses UTC, also called Coordinated Universal Time. UTC, formerly known as Greenwich Mean Time (GMT), has become the worldwide standard for time and date.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which component of the Cisco SDN solution serves as the centralized management system?
A. Cisco OpenDaylight
B. Cisco ACI
C. Cisco APIC
D. Cisco IWAN
Answer: C[/am4show]
Explanation
The Cisco Application Policy Infrastructure Controller (APIC) is the main architectural component of the Cisco ACI solution. It is the unified point of automation and management for the Cisco ACI fabric, policy enforcement, and health monitoring. The Cisco APIC is a centralized clustered controller that optimizes performance, supports any application anywhere, and unifies operation of physical and virtual environments. The controller manages and operates a scalable multitenant Cisco ACI fabric.
Question 2
[am4show have=’p2;’]Which two options are primary responsibilities of the APIC-EM controller? (Choose two)
A. It automates network actions between different device types.
B. It provides robust asset management.
C. It tracks license usage and Cisco IOS versions.
D. It automates network actions between legacy equipment.
E. It makes network functions programmable.
Answer: A E[/am4show]
Question 3
[am4show have=’p2;’]Which Cisco platform can verify ACLs?
A. Cisco Prime Infrastructure
B. Cisco Wireless LAN Controller
C. Cisco APIC-EM
D. Cisco IOS-XE
Answer: C[/am4show]
Explanation
In the “CCNA Routing and Switching ICND2 200-105 Official Cert Guide, Academic Edition” there is a section named “Verify ACLs using the APIC-EM Path Trace ACL analysis tool” so APIC-EM should be the correct answer.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which command should you enter to allow carrying voice, options:
A. switchport ?? (VLAN 10, maybe?)
B. switchport access
C. switchport trunk
D. switchport host
Answer: B[/am4show]
Question 2
[am4show have=’p2;’]What is the correct DSCP value used for voice traffic?
A. Expedited Forwarding (EF), 46, 101110
B. Assured Forwarding (AF), 31, 011010
C. Assured Forwarding (AF), 36, 100110
D. Expedited Forwarding (EF), 36, 101110
Answer: A[/am4show]
Question 3
[am4show have=’p2;’]Which feature can you implement to reserve bandwidth for VoIP calls across the call path?
A. PQ
B. Round Robin
C. CBWFQ
D. RSPV
Answer: D[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which two statement about proxy ARP are true ? (Choose two)
A. It is supported on networks without ARP.
B. It allows machines to spoof packets.
C. It requires larger ARP tables.
D. It reduces the amount of ARP traffic.
Answer: B C[/am4show]
Question 2
[am4show have=’p2;’]Which two statements about Ethernet standards are true? (Choose two)
A. Ethernet is defined by IEEE standard 802.2.
B. Ethernet is defined by IEEE standard 802.3.
C. Ethernet 10BASE-T does not support full-duplex.
D. When an Ethernet network uses CSMA/CD, it terminates transmission as soon as a collision occurs.
E. When an Ethernet network uses CSMA/CA. it terminates transmission as soon as a collision occurs.
Answer: B D[/am4show]
Question 3
[am4show have=’p2;’]If three devices are plugged into one port on a switch and two devices are plugged into a different port, how many collision domains are on the switch?
A. 2
B. 4
C. 5
D. 6
Answer: A[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Drag the term on the left to its definition on the right (not all options are used)
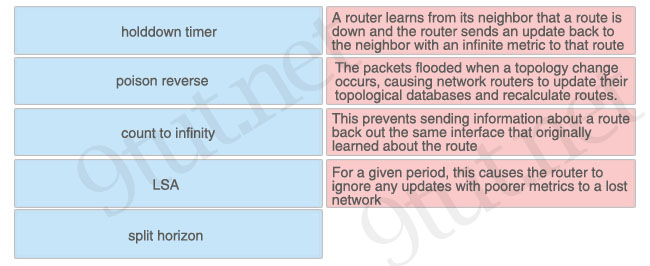
Answer:
+ poison reverse: A router learns from its neighbor that a route is down and the router sends an update back to the neighbor with an infinite metric to that route
+ LSA: The packets flooded when a topology change occurs, causing network routers to update their topological databases and recalculate routes
+ split horizon: This prevents sending information about a routeback out the same interface that originally learned about the route
+ holddown timer: For a given period, this causes the router to ignore any updates with poorer metrics to a lost network[/am4show]
Question 2
[am4show have=’p2;’]The above provides some descriptions, while the below provides some routing protocols. Drag the above items to the proper locations.
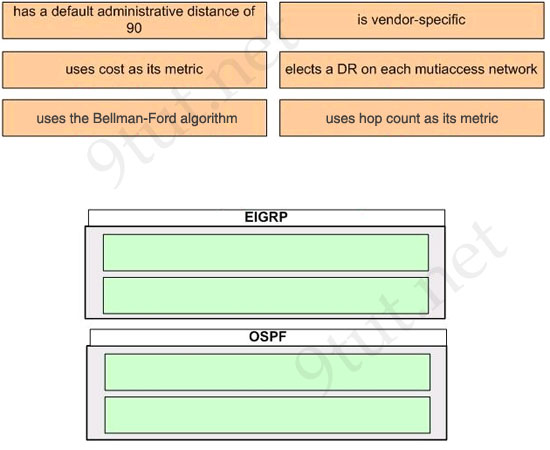
Answer:
EIGRP:
+ has a default administrative distance of 90
+ is vendor-specific
OSPF:
+ uses cost as its metric
+ elects a DR on each multiaccess network[/am4show]
Question 3
[am4show have=’p2;’]Drag each description on the left to the appropriate term on the right. Not all the descriptions are used.
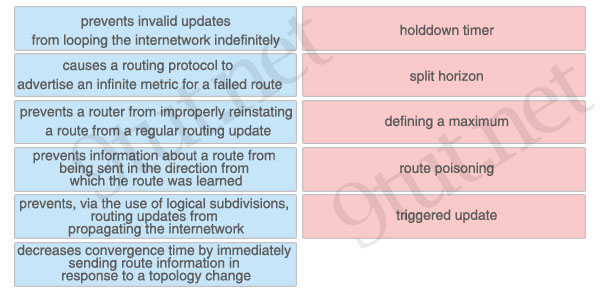
Answer:
+ holddown timer: prevents a router from improperly reinstating a route from a regular routing update
+ split horizon: prevents information about a route from being sent in the direction from which the route was learned
+ defining a maximum: prevents invalid updates from looping the internetwork indefinitely
+ route poisoning: causes a routing protocol to advertise an infinite metric for a failed route
+ triggered update: decreases convergence time by immediately sending route information in response to a topology change[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which two statements describe the operation of the CSMA/CD access method? (Choose two)
A. In a CSMA/CD collision domain, multiple stations can successfully transmit data simultaneously.
B. In a CSMA/CD collision domain, stations must wait until the media is not in use before transmitting.
C. The use of hubs to enlarge the size of collision domains is one way to improve the operation of the CSMA/CD access method.
D. After a collision, the station that detected the collision has first priority to resend the lost data.
E. After a collision, all stations run a random backoff algorithm. When the backoff delay period has expired, all stations have equal priority to transmit data.
F. After a collision, all stations involved run an identical backoff algorithm and then synchronize with each other prior to transmitting data.
Answer: B E[/am4show]
Explanation
CSMA/CD stands for Carrier Sense Multiple Access with Collision Detection. In an Ethernet LAN, before transmitting, a computer first listens to the network media. If the media is idle, the computer sends its data. If the media is not idle (another station is talking), the computer must wait for some time.
When a station transmits, the signal is referred to as a carrier. Carrier Sense means that before a station can send data onto an Ethernet wire, it have to listen to see if another “carrier” (of another station) is present. If another station is talking, this station will wait until there is no carrier present.
Multiple Access means that stations can access the network at any time. It is opposed to Token-Ring network where a station must have the “token” so that it can send data.
Although Carrier Sense help two stations not send data at the same time but sometimes two stations still send data at the same time! This is because two stations listen for network traffic, hear none, and transmit simultaneously -> a collision occurs and both stations must retransmit at some later time. Collision Detection is the ability of the media to detect collisions to know that they must retransmit.
Basically, the CSMA/CD algorithm can be summarized as follows:
+ A device that wants to send a frame must wait until the LAN is silent (no one is “talking”)
+ If a collision still occurs, the devices that caused the collision wait a random amount of time and then try to send data again.
Note: A switch separates each station into its own collision domain. It means that station can send data without worrying its data is collided with the data of other stations. It is as opposed to a hub which can cause collision between stations connected to it.
Question 2
[am4show have=’p2;’]On a live network, which commands will verify the operational status of router interfaces? (Choose two)
A. Router#show interfaces
B. Router#show ip protocols
C. Router#debug interface
D. Router#show ip interface brief
E. Router#show start
Answer: A D[/am4show]
Explanation
Only two commands “show interfaces” and “show ip interface brief” reveal the status of router interfaces (up/up, for example).
The outputs of two commands are shown below:
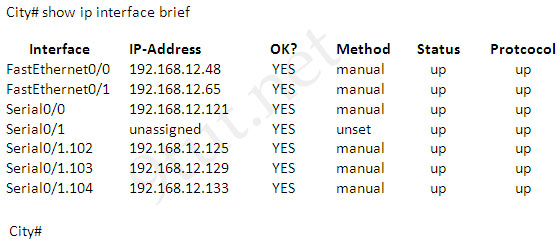
Question 3
[am4show have=’p2;’]What must occur before a workstation can exchange HTTP packets with a web server?
A. A UDP connection must be established between the workstation and its default gateway.
B. A UDP connection must be established between the workstation and the web server.
C. A TCP connection must be established between the workstation and its default gateway.
D. A TCP connection must be established between the workstation and the web server.
E. An ICMP connection must be established between the workstation and its default gateway.
F. An ICMP connection must be established between the workstation and the web sewer.
Answer: D[/am4show]
Explanation
HTTP is based on TCP connection so a TCP connection must be established first between the workstation and the web server.
Question 4
[am4show have=’p2;’]Refer to the exhibit. If the hubs in the graphic were replaced by switches, what would be virtually eliminated?
A. broadcast domains
B. repeater domains
C. Ethernet collisions
D. signal amplification
E. Ethernet broadcasts
Answer: C[/am4show]
Explanation
Hubs do not separate collision domains so if hub is used in the topology above, we will have only 1 collision domain. Switches do separate collision domains so if hubs are replaced by switches, we would have 22 collision domains (19 collision domains for hosts and 3 collision domains among three switches. Please notice that the WAN (serial) connection is not counted as a collision (or broadcast) domain.
Question 5
[am4show have=’p2;’]If a host experiences intermittent issues that relate to congestion within a network while remaining connected, what could cause congestion on this LAN?
A. half-duplex operation
B. broadcast storms
C. network segmentation
D. multicasting
Answer: B[/am4show]
Explanation
A broadcast storm can cause congestion within a network. For more information about broadcast storm please read my STP tutorial.
Question 6
[am4show have=’p2;’]Refer to the exhibit. The network administrator is testing connectivity from the branch router to the newly installed application server. What is the most likely reason for the first ping having a success rate of only 60 percent?
|
Branch# ping 192.168.2.167 Branch# ping 192.168.2.167 |
A. The network is likely to be congested, with the result that packets are being intermittently dropped.
B. The branch router had to resolve the application server MAC address.
C. There is a short delay while NAT translates the server IP address.
D. A routing table lookup delayed forwarding on the first two ping packets.
E. The branch router LAN interface should be upgraded to FastEthernet.
Answer: B[/am4show]
Explanation
Before a host can send ICMP (ping) packets to another device, it needs to learn the MAC address of the destination device so it first sends out an ARP Request. In fact, the first ping packet is dropped because the router cannot create a complete packet without learning the destination MAC address.
Question 7
[am4show have=’p2;’]An administrator is in the process of changing the configuration of a router. What command will allow the administrator to check the changes that have been made prior to saving the new configuration?
A. Router# show startup-config
B. Router# show current-config
C. Router# show running-config
D. Router# show memory
E. Router# show flash
F. Router# show processes
Answer: C[/am4show]
Explanation
The “show running-config” command displays active configuration in memory.
Question 8
[am4show have=’p2;’]What does a host on an Ethernet network do when it is creating a frame and it does not have the destination address?
A. drops the frame
B. sends out a Layer 3 broadcast message
C. sends a message to the router requesting the address
D. sends out an ARP request with the destination IP address
Answer: D[/am4show]
Question 9
[am4show have=’p2;’]Which IOS command is used to initiate a login into a VTY port on a remote router?
A. router# login
B. router# telnet
C. router# trace
D. router# ping
E. router(config)# line vty 0 5
F. router(config-line)# login
Answer: B[/am4show]
Question 10
[am4show have=’p2;’]Which three statements are true about the operation of a full-duplex Ethernet network? (Choose three)
A. There are no collisions in full-duplex mode.
B. A dedicated switch port is required for each full-duplex node.
C. Ethernet hub ports are preconfigured for full-duplex mode.
D. In a full-duplex environment, the host network card must check for the availability of the network media before transmitting.
E. The host network card and the switch port must be capable of operating in full-duplex mode.
Answer: A B E[/am4show]
Explanation
Full-duplex communication allows both sending and receiving of data simultaneously. Switches provide full-duplex communication capability. Half-duplex communication only allows data transmission in only one direction at a time (either sending or receiving).
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which two options will help to solve the problem of a network that is suffering a broadcast storm? (Choose two)
A. a bridge
B. a router
C. a hub
D. a Layer 3 switch
E. an access point
Answer: B D[/am4show]
Explanation
Only a router or a Layer 3 switch can mitigate a broadcast storm because they separate broadcast domains -> B and D are correct.
Question 2
[am4show have=’p2;’]Refer to the exhibit. A network has been planned as shown. Which three statements accurately describe the areas and devices in the network plan? (Choose three)
A. Network Device A is a switch.
B. Network Device B is a switch.
C. Network Device A is a hub.
D. Network Device B is a hub.
E. Area 1 contains a Layer 2 device.
F. Area 2 contains a Layer 2 device.
Answer: A D E[/am4show]
Explanation
AREA 1 has “multiple collision domains” so Network Device A must be a device operating in Layer 2 or above (a router or switch) -> A & E are correct.
AREA 2 only has “single collision domain” so Network Device B must be a device operating in Layer 1 (a hub or repeater) -> D is correct.
Question 3
[am4show have=’p2;’]Refer to the exhibit. If the resume command is entered after the sequence that is shown in the exhibit, which router prompt will be displayed?
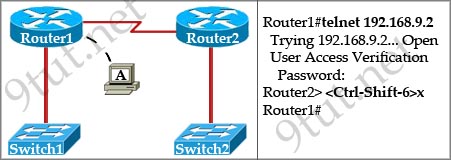
A. Router1>
B. Router1#
C. Router2>
D. Router2#
Answer: C[/am4show]
Explanation
The “Ctrl-Shift-6” and “x” is used to suspend the telnet session. In this case, the telnet session from Router1 to Router2 will be suspended.
If we enter the keyword “resume”, Router1 will try to resume the telnet session to Router2 (you will see the line [Resuming connection 1 to 192.168.9.2 … ]) and we will get back the Router2> prompt.
Question 4
[am4show have=’p2;’]Refer to the exhibit. All devices attached to the network are shown. How many collision domains are present in this network?
A. 2
B. 3
C. 6
D. 9
E. 15
Answer: E[/am4show]
Explanation
In the topology above only routers and switches are used so for each link we have one collision domains. In the picture below each pink ellipse represents for one collision domain.
Question 5
[am4show have=’p2;’]Which network topology allows all traffic to flow through a central hub?
A. bus
B. star
C. mesh
D. ring
Answer: B[/am4show]
Explanation
Star topology is the most popular topology for the network which allows all traffic to flow through a central device.
Question 6
[am4show have=’p2;’]On which type of device is every port in the same collision domain?
A. a router
B. a Layer 2 switch
C. a hub
Answer: C[/am4show]
Question 7
[am4show have=’p2;’]Which feature allows a device to use a switch port that is configured for half-duplex to access the network?
A. CSMA/CD
B. IGMP
C. port security
D. split horizon
Answer: A[/am4show]
Explanation
Carrier Sense Multiple Access with Collision Detection (CSMA/CD) is the LAN access method used in Ethernet. When a device wants to gain access to the network, it checks to see if the network is free. If the network is not free, the device waits a random amount of time before retrying. If the network is free and two devices access the line at exactly the same time, their signals collide. When the collision is detected, they both back off and wait a random amount of time before retrying.
CSMA/CD is used with devices operating in half-duplex mode only. CSMA/CD helps devices connecting to half-duplex switch ports operate correctly.
Question 8
[am4show have=’p2;’]Which MTU size can cause a baby giant error?
A. 1500
B. 9216
C. 1600
D. 1518
Answer: D[/am4show]
Explanation
Ethernet frame size refers to the whole Ethernet frame, including the header and the trailer while MTU size refers only to Ethernet payload. Baby giant frames refer to Ethernet frame size up to 1600 bytes, and jumbo frame refers to Ethernet frame size up to 9216 bytes (according to this link: http://www.cisco.com/c/en/us/support/docs/switches/catalyst-4000-series-switches/29805-175.html)
For example, standard Ethernet frame MTU is 1500 bytes. This does not include the Ethernet header and Cyclic Redundancy Check (CRC) trailer, which is 18 bytes in length, to make the total Ethernet frame size of 1518.
So according to strict definition, MTU size of 1600 cannot be classified as baby giant frames as the whole Ethernet frames will surely larger than 1600 -> Answer C is not correct.
Answer D is a better choice as the MTU is 1518, so the whole Ethernet frame would be 1536 (1518 + 18 Ethernet header and CRC trailer). This satisfies the requirement of baby giant frames “Baby giant frames refer to Ethernet frame size up to 1600 bytes”.
Question 9
[am4show have=’p2;’]What happens when the cable is too long?
A. Baby Giant
B. Late collision
C. Duplex mismatch
D. No connection
Answer: B[/am4show]
Question 10
[am4show have=’p2;’]To what type of port would a cable with a DB-60 connector attach?
A. Serial port
B. Console port
C. Ethernet port
D. Fibre optic port
Answer: A[/am4show]
Question 11
[am4show have=’p2;’]Refer to the exhibit:
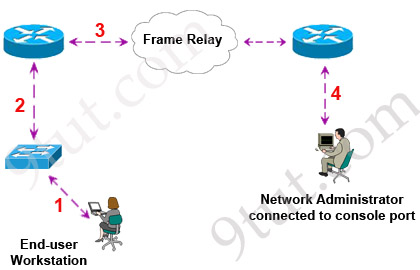
What kind of cable should be used to make each connection that is identified by the numbers shown?
A.
1 – Ethernet straight-through cable
2 – Ethernet crossover cable
3 – Serial cable
4 – Ethernet straight-through cable
B.
1 – Ethernet rollover cable
2 – Ethernet crossover cable
3 – Serial cable
4 – Null modem cable
C.
1 – Ethernet straight-through cable
2 – Ethernet crossover cable
3 – Serial cable
4 – Rollover cable
D.
1 – Ethernet crossover cable
2 – Ethernet straight-through cable
3 – Fiber Optic cable
4 – Rollover cable
E.
1 – Ethernet straight-through cable
2 – Ethernet straight-through cable
3 – Serial cable
4 – Rollover cable
Answer: E[/am4show]
Explanation
To remember which type of cable you should use, follow these tips:
– To connect two serial interfaces of 2 routers we use serial cable
– To specify when we use crossover cable or straight-through cable, we should remember:
Group 1: Router, Host, Server
Group 2: Hub, Switch
One device in group 1 + One device in group 2: use straight-through cable
Two devices in the same group: use crossover cable
For example: we use straight-through cable to connect switch to router, switch to host, hub to host, hub to server… and we use crossover cable to connect switch to switch, switch to hub, router to router, host to host… )
Notice in this question, connecting to the Frame Relay means connecting to another router. Also we must use serial cable (or Fiber Optic cable) because the distance to the Frame Relay is far so we can’t use Ethernet cables.
Rollover cable can be used to connect a computer terminal to a network router’s console port. This is often used when we turn on the router for the first time.
Question 12
[am4show have=’p2;’]Refer to the exhibit. How many collision domains are shown?
A. one
B. two
C. three
D. four
E. six
F. twelve
Answer: B[/am4show]
Question 13
[am4show have=’p2;’]Refer to the exhibit. Pierre has just installed the mail server and Switch2. For security reasons UDP packets are not permitted outbound on the Fa0/1 router interface. Pierre is now at his workstation testing the new installation and is not able to establish SMTP communication to the mail server.
What is the most likely cause for lack of communication between Pierre’s workstation and the mail server?
A. The crossover cable should be a straight-through cable.
B. UDP is blocked coming out of the Fa0/1 interface on the router.
C. The server should be directly connected to the router.
D. The IP addresses are all on the same network. No router is required.
Answer: A[/am4show]
Question 14
[am4show have=’p2;’]Refer to the exhibits labeled A through E. All devices are to be connected over Ethernet. Which three device-to-device configurations are likely to require the use of a crossover connection? (Choose three.)
A. exhibit A
B. exhibit B
C. exhibit C
D. exhibit D
E. exhibit E
Answer: A D E[/am4show]
Question 15
[am4show have=’p2;’]Refer to the exhibit. All devices attached to the network are shown. Which number of collision domains are present in this network?

A. 9
B. 3
C. 6
D. 2
E. 15
Answer: E[/am4show]
Explanation
Both switch and router separate collision domains. In other words, each port of the switch and router creates one collision domain so we have 15 collision domains in this topology.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Note: If you are not sure about OSI Model, please read my OSI Model Tutorial.
Question 1
[am4show have=’p2;’]Which OSI layer header contains the address of a destination host that is on another network?
A. application
B. session
C. transport
D. network
E. data link
F. physical
Answer: D[/am4show]
Question 2
[am4show have=’p2;’]At which layer of the OSI model does the protocol that provides the information that is displayed by the show cdp neighbors command operate?
A. application
B. transport
C. network
D. physical
E. data link
Answer: E[/am4show]
Explanation
CDP runs at Layer 2 (Data Link) of the OSI model -> E is correct.
Question 3
[am4show have=’p2;’]What are two common TCP applications? (Choose two)
A. TFTP
B. SMTP
C. SNMP
D. FTP
E. DNS
Answer: B D[/am4show]
Explanation
SMTP stands for Simple Mail Transfer Protocol. It’s a set of communication guidelines that allow software to transmit email over the Internet while File Transfer Protocol (FTP) is a standard network protocol used to transfer files from one host to another host over TCP-based network.
Note: Simple Network Management Protocol (SNMP) uses UDP as the transport protocol for passing data between managers and agents. SNMP uses UDP to help reduce the impact on your network’s performance. Although SNMP can be configured to run on TCP but we should only do it in special situations. SNMP uses the UDP port 161 for sending and receiving requests, and port 162 for receiving traps from managed devices.
DNS work on both the TCP and UDP protocols. DNS uses TCP for zone exchanges between servers and UDP when a client is trying to
resolve a hostname to an IP address. Therefore in most cases we say “DNS uses UDP”.
Question 4
[am4show have=’p2;’]Which two characteristics describe the access layer of the hierarchical network design model? (Choose two)
A. layer 3 support
B. port security
C. redundant components
D. VLANs
E. PoE
Answer: B D[/am4show]
Explanation
The primary function of an access-layer is to provide network access to the end user.
The hardware and software attributes of the access layer that support high availability include security services for additional security against unauthorized access to the network through the use of tools such as 802.1x, port security, DHCP snooping, Dynamic ARP Inspection, and IP Source Guard.
Question 5
[am4show have=’p2;’]Which layer of the TCP/IP stack combines the OSI model physical and data link layers?
A. Internet layer
B. transport layer
C. application layer
D. network access layer
Answer: D[/am4show]
Explanation
The picture below compares the two TCP/IP and OSI models:

Question 6
[am4show have=’p2;’]Which layer of the OSI model controls the reliability of communications between network devices using flow control, sequencing and acknowledgments?
A. Physical
B. Data-link
C. Transport
D. Network
Answer: C[/am4show]
Explanation
Transmission Control Protocol (TCP) has all the features mentioned above and TCP resides in Transport Layer (Layer 4) of the OSI model.
Flow control: A methodology used to ensure that receiving units are not overwhelmed with data from sending devices when buffers at a receiving unit are full, a message is transmitted to the sending unit to temporarily halt trans-missions until all the data in the receiving buffer has been processed and the buffer is again ready for action.
Sequencing: is used to number segments before sending so they can be put back together again in the correct order at the receiving side.
Acknowledgment: When the receiver gets the data, it sends a response telling the sender that the data have been safely arrived.
Question 7
[am4show have=’p2;’]Which network device functions only at Layer 1 of the OSI model?
A.  bridge
bridge
B. ![]() hub
hub
C.  NIC
NIC
D. ![]() router
router
E. ![]() switch
switch
Answer: B[/am4show]
Explanation
In CCNA, the popular devices operate in Layer 1 are hub and repeater.
Question 8
[am4show have=’p2;’]A network administrator cannot connect to a remote router by using SSH. Part of the show interfaces command is shown.
| router#show interfaces Serial0/1/0 is up, line protocol is down |
At which OSI layer should the administrator begin troubleshooting?
A. physical
B. data link
C. network
D. transport
Answer: B[/am4show]
Question 9
[am4show have=’p2;’]On which OSI layer does a VLAN operate?
A. Layer 1
B. Layer 2
C. Layer 3
D. Layer 4
Answer: B[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which of the following are types of flow control? (Choose three)
A. buffering
B. cut-through
C. windowing
D. congestion avoidance
E. load balancing
Answer: A C D[/am4show]
Explanation
Three types of flow control are buffering, windowing & congestion avoidance:
+ Buffering: If a device receives packets too quickly for it to handle then it can store them in a memory section called a buffer and proceed them later.
+ Windowing: a window is the quantity of data segments that the transmitting device is allowed to send without receiving an acknowledgment for them. For example:
With the window size of 1, the sending device sends 1 segment and the receiving device must reply with 1 ACK before the sending device can send the next segment. This “waiting” takes some time.
By increasing the window size to 3, the sending device will send up to 3 segments before waiting an ACK -> helps reduce the waiting time.
+ Congestion avoidance: lower-priority traffic can be discarded when the network is overloaded -> minimize delays.
Question 2
[am4show have=’p2;’]A receiving host has failed to receive all of the segments that it should acknowledge. What can the host do to improve the reliability of this communication session?
A. decrease the window size
B. use a different source port for the session
C. decrease the sequence number
D. obtain a new IP address from the DHCP server
E. start a new session using UDP
Answer: A[/am4show]
Question 3
[am4show have=’p2;’]What must occur before a workstation can exchange HTTP packets with a web server?
A. A UDP connection must be established between the workstation and its default gateway.
B. A UDP connection must be established between the workstation and the web server.
C. A TCP connection must be established between the workstation and its default gateway.
D. A TCP connection must be established between the workstation and the web server.
E. An ICMP connection must be established between the workstation and its default gateway.
F. An ICMP connection must be established between the workstation and the web sewer.
Answer: D[/am4show]
Explanation
HTTP is based on TCP connection so a TCP connection must be established first between the workstation and the web server.
Question 4
[am4show have=’p2;’]How does TCP differ from UDP? (Choose two)
A. TCP provides best effort delivery.
B. TCP provides synchronized communication.
C. TCP segments are essentially datagrams.
D. TCP provides sequence numbering of packets.
E. TCP uses broadcast delivery.
Answer: B D[/am4show]
Explanation
Before two computers can communicate over TCP, they must synchronize their initial sequence numbers (ISN) -> B is correct.
TCP uses a sequence number to identify each byte of data. The sequence number identifies the order of the bytes sent from each computer so that the data can be reconstructed in order, regardless of any fragmentation, disordering, or packet loss that may occur during transmission -> D is correct.
Question 5
[am4show have=’p2;’]What is the purpose of flow control?
A. To ensure data is retransmitted if an acknowledgement is not received.
B. To reassemble segments in the correct order at the destination device.
C. To provide a means for the receiver to govern the amount of data sent by the sender.
D. To regulate the size of each segment.
Answer: C[/am4show]
Question 6
[am4show have=’p2;’]Refer to the exhibit. A network technician has added host A to the network. Host A cannot communicate on the network. A ping that is issued on the host to address 127.0.0.1 fails. What is the problem?
A. The router is not forwarding the ping packets to network 127.0.0.0.
B. The remote host at 127.0.0.1 is unreachable.
C. The default gateway is incorrect.
D. The IP address of host A is incorrect.
E. The TCP/IP protocols are not loaded.
Answer: E[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]A switch has 48 ports and 4 VLANs. How many collision and broadcast domains exist on the switch?
A. 4, 48
B. 48, 4
C. 48, 1
D. 1, 48
E. 4, 1
Answer: B[/am4show]
Explanation
Each port on a switch is a collision domain while each VLAN is a broadcast domain because broadcast is only forwarded within that VLAN so we have 48 collision domains and 4 broadcast domains on this switch (if all ports are used).
Question 2
[am4show have=’p2;’]A switch receives a frame on one of its ports. There is no entry in the MAC address table for the destination MAC address. What will the switch do with the frame?
A. drop the frame
B. forward it out of all ports except the one that received it
C. forward it out of all ports
D. store it until it learns the correct port
Answer: B[/am4show]
Question 3
[am4show have=’p2;’]Which address type does a switch use to make selective forwarding decisions?
A. source IP address
B. destination IP address
C. source and destination IP address
D. source MAC address
E. destination MAC address
Answer: E[/am4show]
Explanation
When a switch receives a frame, it first checks for the destination MAC address and tries to find a matching entry in its MAC address table. If found, the switch then forwards that frame on the corresponding port associated with that MAC address. If no entry is found, the switch will flood that frame out of all (active) ports except the port that sent it.
Question 4
[am4show have=’p2;’]Which two characteristics apply to Layer 2 switches? (Choose two)
A. increases the number of collision domains
B. decreases the number of collision domains
C. implements VLAN
D decreases the number of broadcast domains
E. uses the IP address to make decisions for forwarding data packets
Answer: A C[/am4show]
Question 5
[am4show have=’p2;’]What is the purpose of assigning an IP address to a switch?
A. provides local hosts with a default gateway address
B. allows remote management of the switch
C. allows the switch to respond to ARP requests between two hosts
D. ensures that hosts on the same LAN can communicate with each other
Answer: B[/am4show]
Question 6
[am4show have=’p2;’]How does a switch differ from a hub?
A. A switch does not induce any latency into the frame transfer time.
B. A switch tracks MAC addresses of directly-connected devices.
C. A switch operates at a lower, more efficient layer of the OSI model.
D. A switch decreases the number of broadcast domains.
E. A switch decreases the number of collision domains.
Answer: B[/am4show]
Explanation
A hub is not as “intelligent” as a switch because a hub does not try to remember anything passing to it. It just floods out all the ports (except the one that sent it) when it receives a frame.
Question 7
[am4show have=’p2;’]Refer to the exhibit. The ports that are shown are the only active ports on the switch. The MAC address table is shown in its entirety. The Ethernet frame that is shown arrives at the switch. What two operations will the switch perform when it receives this frame? (Choose two)
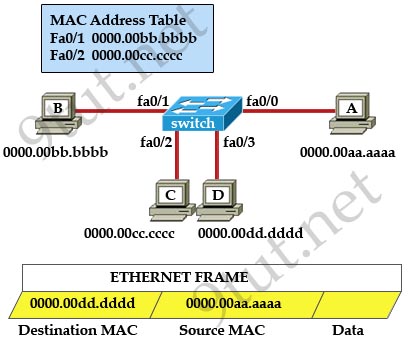
A. The MAC address of 0000.00aa.aaaa will be added to the MAC address table.
B. The MAC address of 0000.00dd.dddd will be added to the MAC address table.
C. The frame will be forwarded out port fa0/3 only.
D. The frame will be forwarded out fa0/1, fa0/2, and fa0/3.
E. The frame will be forwarded out all the active ports.
Answer: A D[/am4show]
Explanation
When a switch receives a frame, it first checks for the destination MAC address and tries to find a matching entry in its MAC address table. If found, the switch then forwards that frame on the corresponding port associated with that MAC address. If no entry is found, the switch will flood that frame out of all active ports except the port that sent it. In this case, the destination MAC address 0000.00dd.dddd has not been in the MAC address table so the switch will flood the frame out all of its ports except fa0/0 (the port that it received the frame) -> D is correct.
Also, the switch learns that the MAC address 0000.00aa.aaaa is received on fa0/0 -> the switch adds 0000.00aa.aaaa and its corresponding port fa0/0 to the MAC address table -> A is correct.
Question 8
[am4show have=’p2;’]Refer to the exhibit. The MAC address table is shown in its entirety. The Ethernet frame that is shown arrives at the switch. What two operations will the switch perform when it receives this frame? (Choose two)
A. The switch will not forward a frame with this destination MAC address.
B. The MAC address of 0000.00aa.aaaa will be added to the MAC Address Table.
C. The MAC address of ffff.ffff.ffff will be added to the MAC address table.
D. The frame will be forwarded out all active switch ports except for port fa0/0.
E. The frame will be forwarded out fa0/0 and fa0/1 only.
F. The frame will be forwarded out all the ports on the switch.
Answer: B D[/am4show]
Explanation
The destination MAC address is ffff.ffff.ffff so this is a broadcast frame so the switch will forward the frame out all active switch ports except for port fa0/0.
Question 9
[am4show have=’p2;’]Refer to the exhibit. The exhibit is showing the topology and the MAC address table. Host A sends a data frame to host D. What will the switch do when it receives the frame from host A?
A. The switch will add the source address and port to the MAC address table and forward the frame to host D.
B. The switch will discard the frame and send an error message back to host A.
C. The switch will flood the frame out of all ports except for port Fa0/3.
D. The switch will add the destination address of the frame to the MAC address table and forward the frame to host D.
Answer: A[/am4show]
Explanation
In this case the destination MAC address has been learned so the switch just forwards the frame to the corresponding port. It also learn that the source MAC address of host A has not been existed in the MAC address table so it will add it (and port fa0/3) to its MAC address table.
Question 10
[am4show have=’p2;’]Refer to the topology and switching table shown in the graphic. Host B sends a frame to Host C. What will the switch do with the frame?
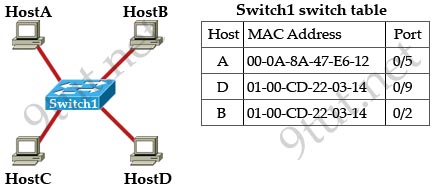
A. drop the frame
B. send the frame out all ports except port 0/2
C. return the frame to Host B
D. send an ARP request for Host C
E. send an ICMP Host Unreachable message to Host B
F. record the destination MAC address in the switching table and send the frame directly to Host C
Answer: B[/am4show]
Question 11
[am4show have=’p2;’]Refer to the exhibit. SwitchA receives the frame with the addressing shown in the exhibit. According to the command output also shown in the exhibit, how will SwitchA handle this frame?
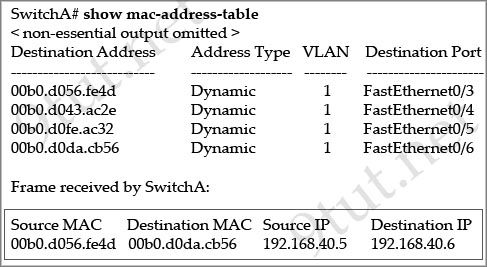
A. It will drop the frame.
B. It will forward the frame out port Fa0/6 only.
C. It will forward the frame out port Fa0/3 only.
D. It will flood the frame out all ports.
E. It will flood the frame out all ports except Fa0/3.
Answer: B[/am4show]
Question 12
[am4show have=’p2;’]Refer to the exhibit. An administrator replaced the 10/100 Mb NIC in a desktop PC with a 1 Gb NIC and now the PC will not connect to the network. The administrator began troubleshooting on the switch. Using the switch output shown, what is the cause of the problem?
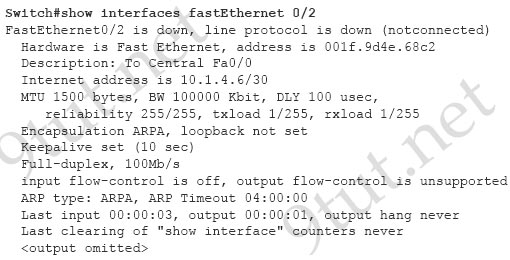
A. Speed is set to 100Mb/s.
B. Input flow control is off.
C. Encapsulation is set to ARPA.
D. The port is administratively down.
E. The counters have never been cleared.
Answer: A[/am4show]
Question 13
[am4show have=’p2;’]The system LED is amber on a Cisco Catalyst 2950 series switch. What does this indicate?
A. The system is not powered up.
B. The system is powered up and operational.
C. The system is malfunctioning.
D. The system is forwarding traffic.
E. The system is sensing excessive collisions.
Answer: C[/am4show]
Explanation
The system LED shows whether the system is receiving power and functioning properly. Below lists the LED colors and meanings:
| Color | System Status |
| Off | System is not powered up. |
| Green | System is operating normally. |
| Amber | System is receiving power but is not functioning properly. |
(Reference: http://www.cisco.com/en/US/docs/switches/lan/catalyst2950/hardware/installation/guide/hgovrev.html)
Question 14
[am4show have=’p2;’]SW-C has just been added to the network shown in the graphic
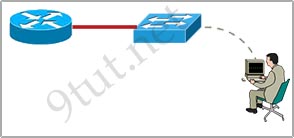
What is the purpose of assigning a default gateway to this switch?
A. allows connectivity to Router B from the switch prompt
B. allows console port connectivity to the switch from Host A
C. allows connectivity to remote network devices from Host B
D. allows the switch to pass traffic between Host A and Host B
Answer: A[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Refer to the exhibit. The exhibit is showing the topology and the MAC address table. Host A sends a data frame to host D. What will the switch do when it receives the frame from host A?

A. The switch will add the source address and port to the MAC address table and forward the frame to host D.
B. The switch will discard the frame and send an error message back to host A.
C. The switch will flood the frame out of all ports except for port Fa0/3.
D. The switch will add the destination address of the frame to the MAC address table and forward the frame to host D.
Answer: A[/am4show]
Explanation
In this case the destination MAC address has been learned so the switch just forwards the frame to the corresponding port. It also learn that the source MAC address of host A has not been existed in the MAC address table so it will add it (and port fa0/3) to its MAC address table.
Question 2
[am4show have=’p2;’]Which statement about unicast frame forwarding on a switch is true?
A. The TCAM table stores destination MAC addresses
B. If the destination MAC address is unknown, the frame is flooded to every port that is configured in the same VLAN except on the port that it was received on.
C. The CAM table is used to determine whether traffic is permitted or denied on a switch
D. The source address is used to determine the switch port to which a frame is forwarded
Answer: B[/am4show]
Question 3
[am4show have=’p2;’]Two hosts are attached to a switch with the default configuration. Which statement about the configuration is true?
A. IP routing must be enabled to allow the two hosts to communicate.
B. The two hosts are in the same broadcast domain.
C. The switch must be configured with a VLAN to allow the two hosts to communicate.
D. Port security prevents the hosts from connecting to the switch.
Answer: B[/am4show]
Explanation
All ports on a Layer 2 switch are in the same broadcast domain. Only router ports separate broadcast domains.
Question 4
[am4show have=’p2;’]Configuration of which option is required on a Cisco switch for the Cisco IP phone to work?
A. PortFast on the interface
B. the interface as an access port to allow the voice VLAN ID
C. a voice VLAN ID in interface and global configuration mode
D. Cisco Discovery Protocol in global configuration mode
Answer: B[/am4show]
Explanation
When you connect an IP phone to a switch using a trunk link, it can cause high CPU utilization in the switches. As all the VLANs for a particular interface are trunked to the phone, it increases the number of STP instances the switch has to manage. This increases the CPU utilization. Trunking also causes unnecessary broadcast / multicast / unknown unicast traffic to hit the phone link.
In order to avoid this, remove the trunk configuration and keep the voice and access VLAN configured along with Quality of Service (QoS). Technically, it is still a trunk, but it is called a Multi-VLAN Access Port (MVAP). Because voice and data traffic can travel through the same port, you should specify a different VLAN for each type of traffic. You can configure a switch port to forward voice and data traffic on different VLANs. Configure IP phone ports with a voice VLAN configuration. This configuration creates a pseudo trunk, but does not require you to manually prune the unnecessary VLANs.
The voice VLAN feature enables access ports to carry IP voice traffic from an IP phone. You can configure a voice VLAN with the “switchport voice vlan …” command under interface mode. The full configuration is shown below:
| Switch(config)#interface fastethernet0/1 Switch(config-if)#switchport mode access Switch(config-if)#switchport access vlan 10 Switch(config-if)#switchport voice vlan 20 |
Question 5
[am4show have=’p2;’]Which address type does a switch use to make selective forwarding decisions?
A. source IP address
B. destination IP address
C. source and destination IP address
D. source MAC address
E. destination MAC address
Answer: E[/am4show]
Explanation
When a switch receives a frame, it first checks for the destination MAC address and tries to find a matching entry in its MAC address table. If found, the switch then forwards that frame on the corresponding port associated with that MAC address. If no entry is found, the switch will flood that frame out of all (active) ports except the port that sent it.
Question 6
[am4show have=’p2;’]After the power-on self test (POST), the system LED of a Cisco 2950 switch turns amber. What is the status of the switch?
A. The switch has a problem with the internal power supply and needs an external power supply to be attached.
B. The switch has experienced an internal problem but data can still be forwarded at a slower rate.
C. The POST was successful.
D. POST failed and there is a problem that prevents the operating system of the switch from being loaded.
E. The switch passed POST, but all the switch ports are busy
Answer: D[/am4show]
Explanation
The system LED shows whether the system is receiving power and functioning properly. Below lists the LED colors and meanings:
| Color | System Status |
| Off | System is not powered up. |
| Green | System is operating normally. |
| Amber | System is receiving power but is not functioning properly. |
(Reference: http://www.cisco.com/en/US/docs/switches/lan/catalyst2950/hardware/installation/guide/hgovrev.html)
Question 7
[am4show have=’p2;’]Which option is a invalid hostname for a switch?
A. 5witch-Cisco
B. Switch-Cisco!
C. 5witchCisc0
D. SwitchCisc0
Answer: B[/am4show]
Explanation
The “!” is an invalid letter for a hostname. The name is alphanumeric so it can begin with a number.
Question 8
[am4show have=’p2;’]Refer to the exhibit. The ports that are shown are the only active ports on the switch. The MAC address table is shown in its entirety. The Ethernet frame that is shown arrives at the switch. What two operations will the switch perform when it receives this frame? (Choose two)

A. The MAC address of 0000.00aa.aaaa will be added to the MAC address table.
B. The MAC address of 0000.00dd.dddd will be added to the MAC address table.
C. The frame will be forwarded out port fa0/3 only.
D. The frame will be forwarded out fa0/1, fa0/2, and fa0/3.
E. The frame will be forwarded out all the active ports.
Answer: A D[/am4show]
Explanation
When a switch receives a frame, it first checks for the destination MAC address and tries to find a matching entry in its MAC address table. If found, the switch then forwards that frame on the corresponding port associated with that MAC address. If no entry is found, the switch will flood that frame out of all active ports except the port that sent it. In this case, the destination MAC address 0000.00dd.dddd has not been in the MAC address table so the switch will flood the frame out all of its ports except fa0/0 (the port that it received the frame) -> D is correct.
Also, the switch learns that the MAC address 0000.00aa.aaaa is received on fa0/0 -> the switch adds 0000.00aa.aaaa and its corresponding port fa0/0 to the MAC address table -> A is correct.
Question 9
[am4show have=’p2;’]Which table displays the MAC addresses that are learned on a switch?
A. FIB
B. ARP
C. TCAM
D. CAM
Answer: D[/am4show]
Explanation
In short, TCAM (Ternary Content Addressable Memory) is used for faster IP look up while ARP table is Layer3 address to Layer2 address resolution so they are not correct.
The Content Addressable Memory (CAM) table on a switch keeps track of MAC addresses and on what port they appear, along with some other stuff like age. When a device that’s plugged into a particular port sends a frame to the switch, the switch makes note of the source MAC and the port and checks the CAM table. Notice that the CAM table is built on the source MAC addresses (while the destination MAC addresses are ignored).
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]If a host experiences intermittent issues that relate to congestion within a network while remaining connected, what could cause congestion on this LAN?
A. half-duplex operation
B. broadcast storms
C. network segmentation
D. multicasting
Answer: B[/am4show]
Explanation
A broadcast storm can cause congestion within a network. For more information about broadcast storm please read my STP tutorial.
Question 2
[am4show have=’p2;’]Which two characteristics describe the access layer of the hierarchical network design model? (Choose two)
A. layer 3 support
B. port security
C. redundant components
D. VLANs
E. PoE
Answer: B D[/am4show]
Explanation
The primary function of an access-layer is to provide network access to the end user.
The hardware and software attributes of the access layer that support high availability include security services for additional security against unauthorized access to the network through the use of tools such as 802.1x, port security, DHCP snooping, Dynamic ARP Inspection, and IP Source Guard.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Refer to the exhibit. Which statement describes the effect of this configuration?
| Router#configure terminal Router(config)#vlan 10 Router(config-vlan)#do show vlan |
A. The VLAN 10 VTP configuration is displayed.
B. VLAN 10 spanning-tree output is displayed.
C. The VLAN 10 configuration is saved when the router exits VLAN configuration mode.
D. VLAN 10 is added to the VLAN database.
Answer: C[/am4show]
Explanation
With the configuration above, when we type “do show vlan” we would not see VLAN 10 in the VLAN database because it has not been created yet. VLAN 10 is only created when we exits VLAN configuration mode (with “exit” command).
Note: We are sure the answer of Q.1 is C although Packet Tracer may give different answer. We believe the author of this question wants to test us in this case. We also tested this with switch v15.2 and the answer is C.
Question 2
[am4show have=’p2;’]Which statement about native VLAN traffic is true?
A. Cisco Discovery Protocol traffic travels on the native VLAN by default
B. Traffic on the native VLAN is tagged with 1 by default
C. Control plane traffic is blocked on the native VLAN.
D. The native VLAN is typically disabled for security reasons
Answer: A[/am4show]
Explanation
Traffic on the native VLAN is untagged -> Answer B is not correct.
Control plane traffic (like CDP, VTP, STP…) runs on VLAN 1 by default. They are not blocked on the native VLAN -> Answer C is not correct.
If the answer says “the native VLAN should be set so that no real traffic running on it for security reasons” then it is correct but the native VLAN is not typically disabled -> Answer D is not correct.
CDP runs on VLAN 1 by default and the native VLAN is also VLAN 1 by default so answer A is the best choice here.
Question 3
[am4show have=’p2;’]Which method does a connected trunk port use to tag VLAN traffic?
A. IEEE 802.1w
B. IEEE 802.1D
C. IEEE 802.1Q
D. IEEE 802.1p
Answer: C[/am4show]
Explanation
IEEE 802.1Q is the networking standard that supports virtual LANs (VLANs) on an Ethernet network. When a frame enters the VLAN-aware portion of the network (a trunk link, for example), a VLAN ID tag is added to represent the VLAN membership of that frame. The picture below shows how VLAN tag is added and removed while going through the network.
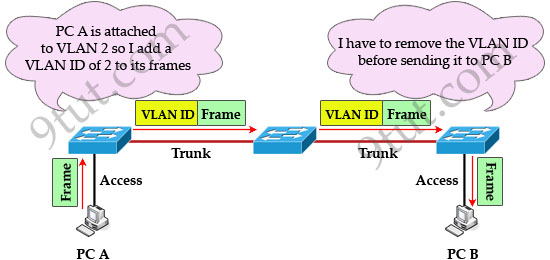
Question 4
[am4show have=’p2;’]Which function enables an administrator to route multiple VLANs on a router?
A. IEEE 802.1X
B. HSRP
C. port channel
D. router on a stick
Answer: D[/am4show]
Question 5
[am4show have=’p2;’]Which two VLANs are reserved for system use only? (Choose two)
A. 1
B. 4095
C. 4096
D. 0
E. 1001
Answer: B D[/am4show]
Explanation
The VLANs 0 and 4095 are reserved by the IEEE 802.1Q standard and you cannot create, delete, or modify them so they are the correct answers.
Note:
+ VLAN 0 and 4095 are reserved for system use only. You cannot see or use these VLANs.
+ VLAN 1 and VLANs 1002-1005 are default VLANs. Default VLANs are created automatically and cannot be configured or deleted by users.
+ VLAN 2 to 1001 are normal VLANs. You can create, use and delete them.
+ VLAN 1002 to 1005 are normal VLANs too but Cisco reserved for FDDI an Token Ring. You cannot delete these VLANs.
+ VLAN 1006 to 4094 are extended VLANs (for Ethernet VLANs only)
Reference: http://www.cisco.com/c/en/us/td/docs/ios/12_4t/12_4t15/ht_xvlan.html and http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SX/configuration/guide/book/vlans.html
Question 6
[am4show have=’p2;’]Which network configuration can you use to segregate traffic for two different department in our organization?
A. VTP
B. STP
C. VLAN
D. Etherchannel
Answer: C[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which statement about a router on a stick is true?
A. Its date plane router traffic for a single VLAN over two or more switches.
B. It uses multiple subinterfaces of a single interface to encapsulate traffic for different VLANs on the same subnet.
C. It requires the native VLAN to be disabled.
D. It uses multiple subinterfaces of a single interface to encapsulate traffic for different VLANs.
Answer: D[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Based on the network shown in the graphic
Which option contains both the potential networking problem and the protocol or setting that should be used to prevent the problem?
A. routing loops, hold down timers
B. Switching loops, split horizon
C. routing loops, split horizon
D. Switching loops, VTP
E. routing loops, STP
F. Switching loops, STP
Answer: F[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]By default, how many MAC addresses are permitted to be learned on a switch port with port security enabled?
A. 8
B. 2
C. 1
D. 0
Answer: C[/am4show]
Explanation
By default, port security limits the MAC address that can connect to a switch port to one. If the maximum number of MAC addresses is reached, when another MAC address attempting to access the port a security violation occurs.
Question 2
[am4show have=’p2;’]Which option is the default switch port port-security violation mode?
A. shutdown
B. protect
C. shutdown vlan
D. restrict
Answer: A[/am4show]
Explanation
Shutdown is the default switch port port-security violation mode. When in this mode, the switch will automatically force the switchport into an error disabled (err-disable) state when a violation occurs. While in this state, the switchport forwards no traffic. The switchport can be brought out of this error disabled state by issuing the errdisable recovery cause CLI command or by disabling and re-enabling the switchport.
Question 3
[am4show have=’p2;’]What is the purpose of the switchport command?
Switch(config-if)# switchport port-security maximum 1
Switch(config-if)# switchport port-security mac-address 0018.DE8B.4BF8
A. It ensures that only the device with the MAC address 0018.DE8B.4BF8 will be able to connect to the port that is being configured.
B. It informs the switch that traffic destined for MAC address 0018.DE8B.4BF8 should only be sent to the port that is being configured.
C. It will act like an access list and the port will filter packets that have a source or destination MAC of 0018.DE8B.4BF8.
D. The switch will shut down the port of any traffic with source MAC address of 0018.DE8B.4BF8.
Answer: A[/am4show]
Question 4
[am4show have=’p2;’]Which statement is a Cisco best practice for switch port security?
A. Vacant switch ports must be shut down.
B. Empty ports must be enabled in VLAN 1.
C. VLAN 1 must be configured as the native VLAN.
D. Err-disabled ports must be configured to automatically re-enable.
Answer: A[/am4show]
Question 5
[am4show have=’p2;’]An administrator connects devices to a switch and wants dynamically learned MAC addresses and add them to the running config. What accomplishes this?
A. Enable port security and use the keyword sticky
B. Set the switchport mode to trunk and save the running configuration
C. Use the switchport protected command to have the MAC addresses added to the configuration
D. Use the no switchport port-security command to allow MAC addresses to be added to the configuration
Answer: A[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which two of these functions do routers perform on packets? (Choose two)
A. examine the Layer 2 headers of inbound packets and use that information to determine the next hops for the packets
B. update the Layer 2 headers of outbound packets with the MAC addresses of the next hops
C. examine the Layer 3 headers of inbound packets and use that information to determine the next hops for the packets
D. examine the Layer 3 headers of inbound packets and use that information to determine the complete paths along which the packets will be routed to their ultimate destinations
E. update the Layer 3 headers of outbound packets so that the packets are properly directed to valid next hops
F. update the Layer 3 headers of outbound packets so that the packets are properly directed to their ultimate destinations
Answer: B C[/am4show]
Explanation
When packets travel through many routers, the source and destination IP addresses do not change but the source and destination MAC do change.
Question 2
[am4show have=’p2;’]Refer to the exhibit. An administrator cannot connect from R1 to R2. To troubleshoot this problem, the administrator has entered the command shown in the exhibit. Based on the output shown, what could be the problem?
A. The serial interface is configured for half duplex.
B. The serial interface does not have a cable attached.
C. The serial interface has the wrong type of cable attached.
D. The serial interface is configured for the wrong frame size.
E. The serial interface has a full buffer.
Answer: C[/am4show]
Explanation
The output above is unclear. Normally when we use this command we can see the type of serial connection on this interface, for example “V.35 DCE cable. Below is an example of the same command as above:
|
RouterA#show controllers serial 0 |
Or
|
RouterB#show controllers serial 0 |
but in this case we only get “V.35 cable”. So in fact we are not sure about the answer C. But the output above also does not have any information to confirm other answers are correct or not.
Just for your information, the V.35 male and V.35 female cable are shown below:


Question 3
[am4show have=’p2;’]What two things does a router do when it forwards a packet? (Choose two)
A. switches the packet to the appropriate outgoing interfaces
B. computes the destination host address
C. determines the next hop on the path
D. updates the destination IP address
E. forwards ARP requests
Answer: A C[/am4show]
Question 4
[am4show have=’p2;’]Refer to the exhibit. A network device needs to be installed in the place of the icon labeled Network Device to accommodate a leased line attachment to the Internet. Which network device and interface configuration meets the minimum requirements for this installation?
A. a router with two Ethernet interfaces
B. a switch with two Ethernet interfaces
C. a router with one Ethernet and one serial interface
D. a switch with one Ethernet and one serial interface
E. a router with one Ethernet and one modem interface
Answer: C[/am4show]
Question 5
[am4show have=’p2;’]Which two commands will display the current IP address and basic Layer 1 and 2 status of an interface? (Choose two)
A. Router#show version
B. Router#show ip interface
C. router#show protocols
D. router#show controllers
E. Router#show running-config
Answer: B C[/am4show]
Explanation
The outputs of “show protocols” and “show ip interface” are shown below:
| Global values: Internet Protocol routing is enabled Serial0/0 is up, line protocol is down Internet address is 10.1.1.1/30 Serial0/1 is up, line protocol is down Internet address is 209.65.200.225/30 Serial0/2 is up, line protocol is down Serial0/3 is up, line protocol is down NVI0 is up, line protocol is up Interface is unnumbered. Using address of NVI0 (0.0.0.0) Loopback0 is up, line protocol is up Internet address is 10.1.10.1/32 Loopback1 is up, line protocol is up Internet address is 10.1.2.1/27 Loopback6 is up, line protocol is up |
| Serial0/0 is up, line protocol is down Internet address is 10.1.1.1/30 Broadcast address is 255.255.255.255 Address determined by non-volatile memory MTU is 1500 bytes Helper address is not set Directed broadcast forwarding is disabled Multicast reserved groups joined: 224.0.0.5 Outgoing access list is not set Inbound access list is not set Proxy ARP is enabled Local Proxy ARP is disabled Security level is default Split horizon is disabled ICMP redirects are always sent ICMP unreachables are always sent ICMP mask replies are never sent IP fast switching is enabled IP fast switching on the same interface is enabled IP Flow switching is disabled IP CEF switching is disabled IP Feature Fast switching turbo vector IP multicast fast switching is enabled IP multicast distributed fast switching is disabled IP route-cache flags are Fast Router Discovery is disabled IP output packet accounting is disabled IP access violation accounting is disabled TCP/IP header compression is disabled RTP/IP header compression is disabled Policy routing is disabled Network address translation is enabled, interface in domain inside BGP Policy Mapping is disabled WCCP Redirect outbound is disabled WCCP Redirect inbound is disabled WCCP Redirect exclude is disabled |
Question 6
[am4show have=’p2;’]Refer to the exhibit. If the resume command is entered after the sequence that is shown in the exhibit, which router prompt will be displayed?

A. Router1>
B. Router1#
C. Router2>
D. Router2#
Answer: C[/am4show]
Explanation
The “Ctrl-Shift-6” and “x” is used to suspend the telnet session. In this case, the telnet session from Router1 to Router2 will be suspended.
If we enter the keyword “resume”, Router1 will try to resume the telnet session to Router2 (you will see the line [Resuming connection 1 to 192.168.9.2 … ]) and we will get back the Router2> prompt.
Question 7
[am4show have=’p2;’]When a router makes a routing decision for a packet that is received from one network and destined to another, which portion of the packet does if replace?
A. Layer 2 frame header and trailer
B. Layer 3 IP address
C. Layer 5 session
D. Layer 4 protocol
Answer: A[/am4show]
Explanation
The Layer 2 information (source and destination MAC) would be changed when passing through each router. The Layer 3 information (source and destination IP addresses) remains unchanged.
Question 8
[am4show have=’p2;’]Which two of these functions do routers perform on packets? (Choose two)
A. examine the Layer 2 headers of inbound packets and use that information to determine the next hops for the packets
B. update the Layer 2 headers of outbound packets with the MAC addresses of the next hops
C. examine the Layer 3 headers of inbound packets and use that information to determine the next hops for the packets
D. examine the Layer 3 headers of inbound packets and use that information to determine the complete paths along which the packets will be routed to their ultimate destinations
E. update the Layer 3 headers of outbound packets so that the packets are properly directed to valid next hops
F. update the Layer 3 headers of outbound packets so that the packets are properly directed to their ultimate destinations
Answer: B C[/am4show]
Explanation
When packets travel through many routers, the source and destination IP addresses do not change but the source and destination MAC do change.
Question 9
[am4show have=’p2;’]How do you bypass password on Cisco device?
A. Change the configuration register to 0x2142
B. Reset the device
C. Unplug and plug the power
Answer: A[/am4show]
Explanation
Change the configuration register to 0x2142. With this setting when that router reboots, it bypasses the startup-config and no password is required.
Question 10
[am4show have=’p2;’]Which router command can be used to determine the status of Serial 0/0?
A. show ip route
B. show interfaces
C. show s0/0 status
D. debug s0/0
E. show run
F. show version
Answer: B[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Refer to the exhibit. A network technician is asked to design a small network with redundancy. The exhibit represents this design, with all hosts configured in the same VLAN. What conclusions can be made about this design?
A. The design will function as intended
B. Spanning-tree will need to be used.
C. The router will not accept the addressing scheme.
D. The connection between switches should be a trunk.
E. The router interfaces must be encapsulated with the 802.1Q protocol.
Answer: C[/am4show]
Explanation
Each interface on a router must be in a different network. If two interfaces are in the same network, the router will not accept it and show error when the administrator assigns it.
Question 2
[am4show have=’p2;’]Refer to the exhibit. Why did the device return this message?
| Router#show ru % Ambiguous command: “show ru” Router# |
A. The command requires additional options or parameters
B. There is no show command that starts with ru.
C. The command is being executed from the wrong router mode.
D. There is more than one show command that starts with the letters ru.
Answer: D[/am4show]
Question 3
[am4show have=’p2;’]Which commands display information about the Cisco IOS software version currently running on a router? (Choose three)
A. show running-config
B. show stacks
C. show version
D. show flash
E. show protocols
F. show IOS
Answer: A C D[/am4show]
Question 4
[am4show have=’p2;’]After the shutdown command has been issued on the serial 0/0 interface, what will be displayed when the show interface serial 0/0 command is issued by the administrator?
A. Serial0/0 is administratively down, line protocol is down
B. Serial0/0 is down, line protocol is down
C. Serial0/0 is up, line protocol is down
D. Serial0/0 is administratively down, line protocol is administratively down
E. Serial0/0 is up, line protocol is up
F. Serial0/0 is down, line protocol is up
Answer: A[/am4show]
Question 5
[am4show have=’p2;’]Refer to the output of the three router commands shown in the exhibit. A new technician has been told to add a new LAN to the company router. Why has the technician received the error message that is shown following the last command?
A. The interface was already configured.
B. The interface type does not exist on this router platform.
C. The IOS software loaded on the router is outdated.
D. The router does not support LAN interfaces that use Ethernet.
E. The command was entered from the wrong prompt.
Answer: B[/am4show]
Explanation
From the output of the “show version” command, we learn that there are only 2 FastEthernet interfaces (2 FastEthernet/IEEE 802.3 interfaces) and this router does not have any Ethernet interface so an error will occur when we enter the “interface e0” command.
Question 6
[am4show have=’p2;’]Refer to the exhibit. Which two statements are true of the interface configuration? (Choose two)
A. The encapsulation in use on this interface is PPP.
B. The default serial line encapsulation is in use on this interface.
C. The address mask of this interface is 255.255.255.0.
D. This interface is connected to a LAN.
E. The interface is not ready to forward packets.
Answer: A C[/am4show]
Question 7
[am4show have=’p2;’]Refer to the exhibit. What does the address 192.168.2.167 represent?
A. the TFTP server from which the file startup-config is being transferred
B. the router from which the file startup-config is being transferred
C. the TFTP server from which the file router-confg is being transferred
D. the TFTP server to which the file router-confg is being transferred
E. the router to which the file router-confg is being transferred
F. the router to which the file startup-config is being transferred
Answer: D[/am4show]
Question 8
[am4show have=’p2;’]Which Ethernet interface command is present when you boot a new Cisco router for the first time?
A. speed 100
B. shutdown
C. ip address 192.168.1.1 255.255.255.0
D. duplex half
Answer: B[/am4show]
Question 9
[am4show have=’p2;’]Which statement describes the effect of the copy run start command on a router in enable mode?
A. The running configuration of the router is saved to NVRAM and used during the boot process.
B. The router reboots and loads the last saved running configuration.
C. A copy of the running configuration of the router is sent by FTP to a designated server.
D. A new running configuration is loaded from flash memory to the router.
Answer: A[/am4show]
Question 10
[am4show have=’p2;’]What does exec-timeout 30 mean?
A. the user inactivity timer is 30 seconds
B. the user inactivity timer is 30 minutes
C. the user inactivity timer is 30 hours
Answer: B[/am4show]
Explanation
The “exec-timeout” command is used to configure the inactive session timeout on the console port or the virtual terminal. The syntax of this command is:
exec-timeout minutes [seconds]
Therefore we need to use the “exec-timeout 30” command to set the user inactivity timer to 30 minutes. To set the user inactivity timer to 30 seconds we use the “exec-timeout 0 30”.
Question 11
[am4show have=’p2;’]How many primary IPv4 addresses can be assigned on router interface?
A. One
B. Two
C. More than one
D. More than two
Answer: A[/am4show]
Explanation
On each router interface we can only assign one primary IPv4 address (but we can assign many IPv6 addresses).
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which of the following statements are TRUE regarding Cisco access lists? (Choose two)
A. In an inbound access list, packets are filtered as they enter an interface.
B. In an inbound access list, packets are filtered before they exit an interface.
C. Extended access lists are used to filter protocol-specific packets.
D. You must specify a deny statement at the end of each access list to filter unwanted traffic.
E. When a line is added to an existing access list, it is inserted at the beginning of the access list.
Answer: A C[/am4show]
Question 2
[am4show have=’p2;’]Which feature automatically disables CEF when it is enabled?
A. RIB
B. ACL logging
C. multicast
D. IP redirects
Answer: B[/am4show]
Explanation
ACL Logging means to use the “log” or “log-input” parameters at the end of the ACL statements. For example: “access-list 100 deny icmp any any echo reply log-input”. In either situation, remember that using either of these two parameters disables CEF switching, which seriously impacts the performance of the router.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Refer to the exhibit. If CDP is enabled on all devices and interfaces, which devices will appear in the output of a show cdp neighbors command issued from R2?
A. R2 and R3
B. R1 and R3
C. R3 and S2
D. R1, S1, S2, and R3
E. R1, S1, S2, R3, and S3
Answer: C[/am4show]
Explanation
CDP runs at Layer 2 so it can recognize a switch (if that switch also runs CDP).
Question 2
[am4show have=’p2;’]On a Cisco switch, which protocol determines if an attached VoIP phone is from Cisco or from another vendor?
A. RTP
B. TCP
C. CDP
D. UDP
Answer: C[/am4show]
Explanation
Cisco Discovery Protocol (CDP) is a proprietary protocol of Cisco so if you can see the VoIP phone via the “show cdp neighbors” command on a Cisco switch then that phone is from Cisco.
Question 3
[am4show have=’p2;’]At which layer of the OSI model does the protocol that provides the information that is displayed by the show cdp neighbors command operate?
A. application
B. transport
C. network
D. physical
E. data link
Answer: E[/am4show]
Explanation
CDP runs at Layer 2 (Data Link) of the OSI model -> E is correct.
Question 4
[am4show have=’p2;’]Refer to the exhibit. For security reasons, information about RTA, including platform and IP addresses, should not be accessible from the Internet. This information should, however, be accessible to devices on the internal networks of RTA. Which command or series of commands will accomplish these objectives?
A – RTA(config)#no cdp run
B – RTA(config)#no cdp enable
C – RTA(config)#interface s0/0
RTA(config-if)#no cdp run
D – RTA(config)#interface s0/0
RTA(config-if)#no cdp enable
Answer: D[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which protocol uses a connection-oriented service to deliver files between end systems?
A. TFTP
B. DNS
C. FTP
D. SNMP
E. RIP
Answer: C[/am4show]
Explanation
File Transfer Protocol (FTP) is a standard network protocol used to transfer files from one host to another host over TCP-based network, such as the Internet.
Question 2
[am4show have=’p2;’]On a Cisco switch, which protocol determines if an attached VoIP phone is from Cisco or from another vendor?
A. RTP
B. TCP
C. CDP
D. UDP
Answer: C[/am4show]
Explanation
Cisco Discovery Protocol (CDP) is a proprietary protocol of Cisco so if you can see the VoIP phone via the “show cdp neighbors” command on a Cisco switch then that phone is from Cisco.
Question 3
[am4show have=’p2;’]Which transport layer protocol provides best-effort delivery service with no acknowledgment receipt required?
A. HTTP
B. IP
C. TCP
D. Telnet
E. UDP
Answer: E[/am4show]
Explanation
User Datagram Protocol (UDP) provides a connectionless datagram service that offers best-effort delivery, which means that UDP does not guarantee delivery or verify sequencing for any datagrams. UDP is typically used by programs that transmit small amounts of data at one time or have real-time requirements (voice, for example).
Question 4
[am4show have=’p2;’]Which statements accurately describe CDP? (Choose three)
A. CDP is an IEEE standard protocol.
B. CDP is a Cisco proprietary protocol.
C. CDP is a datalink layer protocol.
D. CDP is a network layer protocol.
E. CDP can discover directly connected neighboring Cisco devices.
F. CDP can discover Cisco devices that are not directly connected.
Answer: B C E[/am4show]
Explanation
CDP is a device discovery protocol that runs over Layer 2. We can view the CDP information with the show cdp neighbors command (thus the provided information is at layer 2), notice this command only shows information about directly connected devices. The output of the show cdp neighbors command is shown below:
There are 3 columns you must pay attention to:
* Local interface: type & ID of the local interface on which CDP information of the neighbor were received.
* Device platform: the neighboring device model.
* Port ID: the connected interface of the neighbor.
Question 5
[am4show have=’p2;’]A workstation has just resolved a browser URL to the IP address of a server. What protocol will the workstation now use to determine the destination MAC address to be placed into frames directed toward the server?
A. HTTP
B. DNS
C. DHCP
D. RARP
E. ARP
Answer: E[/am4show]
Explanation
After resolving a browser URL to an IP address (via DNS server), the workstation must learn the MAC address of the server so that it can create a complete packet (a complete packet requires destination MAC and IP address, source MAC and IP address). Therefore the workstation must use ARP to find out the MAC address from the IP address.
Question 6
[am4show have=’p2;’]How does TCP differ from UDP? (Choose two)
A. TCP provides best effort delivery.
B. TCP provides synchronized communication.
C. TCP segments are essentially datagrams.
D. TCP provides sequence numbering of packets.
E. TCP uses broadcast delivery.
Answer: B D[/am4show]
Explanation
Before two computers can communicate over TCP, they must synchronize their initial sequence numbers (ISN) -> B is correct.
TCP uses a sequence number to identify each byte of data. The sequence number identifies the order of the bytes sent from each computer so that the data can be reconstructed in order, regardless of any fragmentation, disordering, or packet loss that may occur during transmission -> D is correct.
Question 7
[am4show have=’p2;’]Refer to the exhibit. The two routers have had their startup configurations cleared and have been restarted. At a minimum, what must the administrator do to enable CDP to exchange information between R1 and R2?
![]()
A. Configure the router with the cdp enable command.
B. Enter no shutdown commands on the R1 and R2 fa0/1 interfaces.
C. Configure IP addressing and no shutdown commands on both the R1 and R2 fa0/1 interfaces.
D. Configure IP addressing and no shutdown commands on either of the R1 or R2 fa0/1 interfaces.
Answer: B[/am4show]
Explanation
By default CDP is enabled on Cisco routers -> A is not correct.
CDP runs at Layer 2 in the OSI model and it does not need an IP address to run -> C & D are not correct.
Question 8
[am4show have=’p2;’]Which statements are true regarding ICMP packets? (Choose two)
A. They acknowledge receipt of TCP segments.
B. They guarantee datagram delivery
C. TRACERT uses ICMP packets.
D. They are encapsulated within IP datagrams.
E. They are encapsulated within UDP datagrams
Answer: C D[/am4show]
Explanation
Tracert (or traceroute) is used to trace the path between the sender and the destination host. Traceroute works by sending packets with gradually increasing Time-to-Live (TTL) value, starting with TTL value = 1. The first router receives the packet, decrements the TTL value and drops the packet because it then has TTL value zero. The router sends an ICMP Time Exceeded message back to the source. The next set of packets are given a TTL value of 2, so the first router forwards the packets, but the second router drops them and replies with ICMP Time Exceeded. Proceeding in this way, traceroute uses the returned ICMP Time Exceeded messages to build a list of routers that packets traverse, until the destination is reached and returns an ICMP Echo Reply message -> C is correct.
ICMP is encapsulated in an IP packet. In particular, the ICMP message is encapsulated in the IP payload part of an IP datagram -> D is correct.
Note: The TRACERT command on Windows Operating System uses ICMP while MAC OS X and Linux TRACEROUTE use UDP.
Question 9
[am4show have=’p2;’]The network administrator is using a Windows PC application that is called putty.exe for remote communication to a switch for network troubleshooting. Which two protocols could be used during this communication? (Choose two)
A. SNMP
B. HTTP
C. Telnet
D. RMON
E. SSH
Answer: C E[/am4show]
Question 10
[am4show have=’p2;’]Which protocol verifies connectivity between two switches that are configured with IP addresses in the same network?
A. ICMP
B. STP
C. VTP
D. HSRP
Answer: A[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which RFC was created to alleviate the depletion of IPv4 public addresses?
A. RFC 4193
B. RFC 1519
C. RFC 1518
D. RFC 1918
Answer: D[/am4show]
Explanation
The RFC 1518 is Classless Interdomain Routing (CIDR), which is created to save the IPv4 addresses because we can now assign IP addresses classless. Therefore, instead of assigning the whole block of a class B or C address, now smaller blocks of a class can be assigned. For example, instead of assigning a whole block of 200.1.45.0/24, a smaller block, like 200.1.45.0/27 or 200.1.45.32/27, can be assigned.
The RFC 1918 is Address Allocation for Private Internets, which reserves IP addresses for private and internal use. These addresses can be used for networks that do not need to connect to the Internet.
Therefore the RFC 1918 is the best choice to “alleviate the depletion of IPv4 public addresses”.
Question 2
[am4show have=’p2;’]Which destination IP address can a host use to send one message to multiple devices across different subnets?
A. 172.20.1.0
B. 127.0.0.1
C. 192.168.0.119
D. 239.255.0.1
Answer: D[/am4show]
Explanation
In order to send traffic to multiple devices (not all) across different subnets we need to use multicast addresses, which are in the range 224.0.0.0 through 239.255.255.255 -> D is correct.
Question 3
[am4show have=’p2;’]Which technology allows a large number of private IP addresses to be represented by a smaller number of public IP addresses?
A. NAT
B. NTP
C. RFC 1631
D. RFC 1918
Answer: A[/am4show]
Question 4
[am4show have=’p2;’]Which IP address is a private address?
A. 12.0.0.1
B. 168.172.19.39
C. 172.20.14.36
D. 172.33.194.30
E. 192.169.42.34
Answer: C[/am4show]
Question 5
[am4show have=’p2;’]Which of the following IP addresses are valid Class B host addresses if a default Class B mask is in use? (Choose two)
A. 10.6.8.35
B. 133.6.5.4
C. 192.168.5.9
D. 127.0.0.1
E. 190.6.5.4
Answer: B E[/am4show]
Question 6
[am4show have=’p2;’]From where does a small network get its IP network address?
A. Internet Assigned Numbers Authority (IANA)
B. Internet Architecture Board (IAB)
C. Internet Service Provider (ISP)
D. Internet Domain Name Registry (IDNR)
Answer: C[/am4show]
Question 7
[am4show have=’p2;’]Which three network addresses are reserved for private network use? (Choose three)
A. 10.0.0.0
B. 172.15.0.0
C. 172.31.0.0
D. 192.162.24.0
E. 192.168.255.0
F. 224.192.0.0
Answer: A C E[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Note: If you are not sure about Subnetting, please read my Subnetting Made Easy tutorial.
Question 1
[am4show have=’p2;’]What is the subnet address for the IP address 172.19.20.23/28?
A. 172.19.20.0
B. 172.19.20.15
C. 172.19.20.16
D. 172.19.20.20
E. 172.19.20.32
Answer: C[/am4show]
Explanation
From the /28 we can find all information we need:
Increment: 16 (/28 = 11111111.11111111.11111111.11110000)
Network address: 172.19.20.16 (because 16 < 23)
Broadcast address: 172.16.20.31 (because 31 = 16 + 16 – 1)
In fact we don’t need to find out the broadcast address because the question only asks about subnet address (network address).
Question 2
[am4show have=’p2;’]What is the network address for the host with IP address 192.168.23.61/28?
A. 192.168.23.0
B. 192.168.23.32
C. 192.168.23.48
D. 192.168.23.56
E. 192.168.23.60
Answer: C[/am4show]
Explanation
From the /28 we can find all information we need:
Increment: 16 (/28 = 11111111.11111111.11111111.11110000)
Network address: 192.168.23.48 (because 48 = 16 * 3 and 48 < 61)
Question 3
[am4show have=’p2;’]Given an IP address of 192.168.1.42 255.255.255.248, what is the subnet address?
A. 192.168.1.8/29
B. 192.168.1.32/27
C. 192.168.1.40/29
D. 192.168.1.16/28
E. 192.168.1.48/29
Answer: C[/am4show]
Explanation
From the subnet mask of 255.255.255.248 we learn:
Increment: 8 (248 = 11111111.11111111.11111111.11111000)
Network address: 192.168.1.40 (because 40 = 8 * 5 and 40 < 42)
Question 4
[am4show have=’p2;’]Which IP addresses are valid for hosts belonging to the 10.1.160.0/20 subnet? (Choose three)
A. 10.1.168.0
B. 10.1.176.1
C. 10.1.174.255
D. 10.1.160.255
E. 10.1.160.0
F. 10.1.175.255
Answer: A C D[/am4show]
Explanation
From the /20 we can find all information we need:
Increment: 16 (/20 = 11111111.11111111.11110000.00000000). This is applied for the 3rd octet.
Network address: 10.1.160.0 (because 160 = 16 * 10 and 160 = 160 -> the IP address above is also the network address.
Broadcast address: 10.1.175.255 (because 175 = 160 + 16 – 1)
Therefore only 10.1.168.0, 10.1.174.255 and 10.1.160.255 are in this range. Please notice 10.1.174.255 is not a broadcast address and can be assigned to host.
Question 5
[am4show have=’p2;’]Which one of the following IP addresses is the last valid host in the subnet using mask 255.255.255.224?
A. 192.168.2.63
B. 192.168.2.62
C. 192.168.2.61
D. 192.168.2.60
E. 192.168.2.32
Answer: B[/am4show]
Explanation
Increment: 32 (224 = 11111111.11111111.11111111.11100000)
Network address: x.x.x.(0;32;64;96;128;160;192;224)
Broadcast address: x.x.x.(31;63;95;127;159;191;223)
-> Last valid host (reduced broadcast addresses by 1): x.x.x.(30;62;94;126;158;190;222) -> Only B is correct.
Question 6
[am4show have=’p2;’]An administrator is working with the 192.168.4.0 network, which has been subnetted with a /26 mask. Which two addresses can be assigned to hosts within the same subnet? (Choose two)
A. 192.168.4.61
B. 192.168.4.63
C. 192.168.4.67
D. 192.168.4.125
E. 192.168.4.128
F. 192.168.4.132
Answer: C D[/am4show]
Explanation
Increment: 64 (/26 = 11111111.11111111.11111111.11000000)
The IP 192.168.4.0 belongs to class C. The default subnet mask of class C is /24 and it has been subnetted with a /26 mask so we have 2(26-24) = 22 = 4 sub-networks:
1st subnet: 192.168.4.0 (to 192.168.4.63)
2nd subnet: 192.168.4.64 (to 192.168.4.127)
3rd subnet: 192.168.4.128 (to 192.168.4.191)
4th subnet: 192.168.4.192 (to 192.168.4.225)
In all the answers above, only answer C and D are in the same subnet.
Therefore only IPs in this range can be assigned to hosts.
Question 7
[am4show have=’p2;’]An administrator must assign static IP addresses to the servers in a network. For network 192.168.20.24/29, the router is assigned the first usable host address while the sales server is given the last usable host address. Which of the following should be entered into the IP properties box for the sales server?
A. IP address: 192.168.20.14
Subnet Mask: 255.255.255.248
Default Gateway. 192.168.20.9
B. IP address: 192.168.20.254
Subnet Mask: 255.255.255.0
Default Gateway: 192.168.20.1
C. IP address: 192.168.20.30
Subnet Mask: 255.255.255.248
Default Gateway: 192.168.20.25
D. IP address: 192.168.20.30
Subnet Mask: 255.255.255.240
Default Gateway: 192.168.20.17
E. IP address: 192.168.20.30
Subnet Mask: 255.255.255.240
Default Gateway. 192.168.20.25
Answer: C[/am4show]
Explanation
With network 192.168.20.24/29 we have:
Increment: 8 (/29 = 255.255.255.248 = 11111000 for the last octet)
Network address: 192.168.20.24 (because 24 = 8 * 3)
Broadcast address: 192.168.20.31 (because 31 = 24 + 8 – 1)
Therefore the first usable IP address is 192.168.20.25 (assigned to the router) and the last usable IP address is 192.168.20.30 (assigned to the sales server). The IP address of the router is also the default gateway of the sales server.
Question 8
[am4show have=’p2;’]Given a Class C IP address subnetted with a /30 subnet mask, how many valid host IP addresses are available on each of the subnets?
A. 1
B. 2
C. 4
D. 8
E. 252
F. 254
Answer: B[/am4show]
Explanation
The number of valid host IP addresses depends on the number of bits 0 left in the subnet mask. With a /30 subnet mask, only two bits 0 left (/30 = 11111111.11111111.11111111.11111100) so the number of valid host IP addresses is 22 – 2 = 2. Also please notice that the /30 subnet mask is a popular subnet mask used in the connection between two routers because we only need two IP addresses. The /30 subnet mask help save IP addresses for other connections. An example of the use of /30 subnet mask is shown below:
Question 9
[am4show have=’p2;’]Which two statements describe the IP address 10.16.3.65/23? (Choose two)
A. The subnet address is 10.16.3.0 255.255.254.0.
B. The lowest host address in the subnet is 10.16.2.1 255.255.254.0.
C. The last valid host address in the subnet is 10.16.2.254 255.255.254.0
D. The broadcast address of the subnet is 10.16.3.255 255.255.254.0.
E. The network is not subnetted.
Answer: B D[/am4show]
Explanation
Increment: 2 (/23 = 11111111.11111111.11111110.00000000 = 255.255.254.0)
Network address: 10.16.2.0 (because 2 = 2 * 1 and 2 < 3)
Broadcast address: 10.16.3.255 (because 2 + 2 – 1 = 3 for the 3rd octet)
-> The lowest (first assignable) host address is 10.16.2.1 and the broadcast address of the subnet is 10.16.3.255 255.255.254.0
Question 10
[am4show have=’p2;’]What is the subnet address of 172.16.159.159/22?
A. 172.16.0.0
B. 172.16.128.0
C. 172.16.156.0
D. 172.16.159.0
E. 172.16.159.128
F. 172.16.192.0
Answer: C[/am4show]
Explanation
Increment: 4 (/22 = 11111111.11111111.11111100.00000000)
Network address: 172.16.156.0 (156 is multiple of 4 and 156 < 159)
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Note: If you are not sure about Subnetting, please read my Subnetting Made Easy tutorial.
Question 1
[am4show have=’p2;’]Refer to the exhibit. The junior network support staff provided the diagram as a recommended configuration for the first phase of a four-phase network expansion project. The entire network expansion will have over 1000 users on 14 network segments and has been allocated this IP address space:
192.168.1.1 through 192.168.5.255
192.168.100.1 through 198.168.100.255
What are three problems with this design? (Choose three)
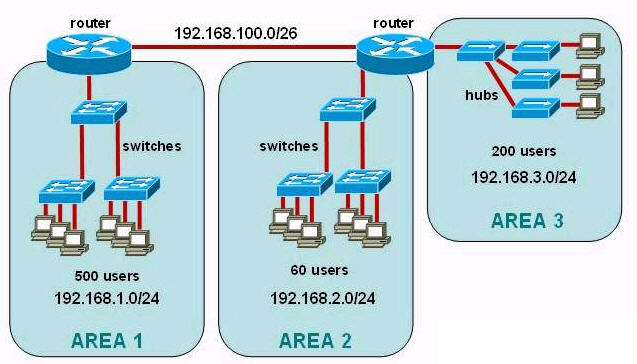
A – The AREA 1 IP address space is inadequate for the number of users.
B – The AREA 3 IP address space is inadequate for the number of users.
C – AREA 2 could use a mask of /25 to conserve IP address space.
D – The network address space that is provided requires a single network-wide mask.
E – The router-to-router connection is wasting address space.
F – The broadcast domain in AREA 1 is too large for IP to function.
Answer: A C E[/am4show]
Explanation
AREA 1 has 500 users but it uses class C which only supports 254 users (from 192.168.1.1 to 192.168.1.254)-> A is correct.
AREA 3 also uses class C and as mentioned above it supports 254 users so it is enough for 200 users -> B is incorrect.
In AREA 2 there are only 60 users < 64 = 26 so we can use a subnet mask which has 6 bits 0 -> /26. Of course we can use larger subnets (like /25) for future expansion -> C is correct.
A large network should never use a single network-wide mask. It should be some different subnet masks to make the network flexible and easy to be summarized -> D is incorrect.
For router-to-router connection we should use a subnet mask of /30 which supports 2 hosts per subnet. This subnet mask is ideal for router-to-router connection -> E is correct.
There is no limit for IP to function if we know how to organize our network -> F is incorrect.
Question 2
[am4show have=’p2;’]Refer to the exhibit. The enterprise has decided to use the network address 172.16.0.0. The network administrator needs to design a classful addressing scheme to accommodate the three subnets, with 30, 40, and 50 hosts, as shown. What subnet mask would accommodate this network?
| Net bits | Subnet mask | total-addresses per subnet |
| /20 | 255.255.240.0 | 4096 |
| /21 | 255.255.248.0 | 2048 |
| /22 | 255.255.252.0 | 1024 |
| /23 | 255.255.254.0 | 512 |
| /24 | 255.255.255.0 | 256 |
| /25 | 255.255.255.128 | 128 |
| /26 | 255.255.255.192 | 64 |
| /27 | 255.255.255.224 | 32 |
| /28 | 255.255.255.240 | 16 |
| /29 | 255.255.255.248 | 8 |
| /30 | 255.255.255.252 | 4 |
A. 255.255.255.192
B. 255.255.255.224
C. 255.255.255.240
D. 255.255.255.248
Answer: A[/am4show]
Explanation
The maximum number of hosts in this question is 50 hosts so we have to use /26 subnet mask or above.
Question 3
[am4show have=’p2;’]The network manager has requested a 300-workstation expansion of the network. The workstations are to be installed in a single broadcast domain, but each workstation must have its own collision domain. The expansion is to be as cost-effective as possible while still meeting the requirements. Which three items will adequately fulfill the request? (Choose three)
A. one IP subnet with a mask of 255.255.254.0
B. two IP subnets with a mask of 255.255.255.0
C. seven 48-port hubs
D. seven 48-port switches
E. one router interface
F. seven router interfaces
Answer: A D E[/am4show]
Explanation
To support 300 workstations in a single broadcast domain, we need to use a subnet mask which supports 512 hosts = 29 -> /23 or 255.255.254.0 in decimal form -> A is correct.
If we use 48-port switches we need 300/48 = 6.25 -> seven 48-port switches are enough because we also need trunking between them -> D is correct.
We only need one router interface and it is connected with one of seven switches -> E is correct.
Question 4
[am4show have=’p2;’]Which router command will configure an interface with the IP address 10.10.80.1/19?
A. router(config-if)# ip address 10.10.80.1/19
B. router(config-if)# ip address 10.10.80.1 255.255.0.0
C. router(config-if)# ip address 10.10.80.1 255.255.255.0
D. router(config-if)# ip address 10.10.80.1 255.255.224.0
E. router(config-if)# ip address 10.10.80.1 255.255.240.0
F. router(config-if)# ip address 10.10.80.1 255.255.255.240
Answer: D[/am4show]
Explanation
/19 = 255.255.224.0. The fast way to find out this subnet mask is to remember /16 = 255.255.0.0 and we need 3 more bits 1 for 3rd octet: 1110 0000 which is 224.
Question 5
[am4show have=’p2;’]Refer to the exhibit. A TFTP server has recently been installed in the Atlanta office. The network administrator is located in the NY office and has made a console connection to the NY router. After establishing the connection they are unable to backup the configuration file and IOS of the NY router to the TFTP server. What is the cause of this problem?
A. The NY router has an incorrect subnet mask.
B. The TFTP server has an incorrect IP address.
C. The TFTP server has an incorrect subnet mask.
D. The network administrator computer has an incorrect IP address.
Answer: C[/am4show]
Question 6
[am4show have=’p2;’]Which two statements describe the IP address 10.16.3.65/23? (Choose two)
A. The subnet address is 10.16.3.0 255.255.254.0.
B. The lowest host address in the subnet is 10.16.2.1 255.255.254.0.
C. The last valid host address in the subnet is 10.16.2.254 255.255.254.0
D. The broadcast address of the subnet is 10.16.3.255 255.255.254.0.
E. The network is not subnetted.
Answer: B D[/am4show]
Explanation
Increment: 2 (/23 = 11111111.11111111.11111110.00000000 = 255.255.254.0)
Network address: 10.16.2.0 (because 2 = 2 * 1 and 2 < 3)
Broadcast address: 10.16.3.255 (because 2 + 2 – 1 = 3 for the 3rd octet)
-> The lowest (first assignable) host address is 10.16.2.1 and the broadcast address of the subnet is 10.16.3.255 255.255.254.0
Question 7
[am4show have=’p2;’]Refer to the exhibit. The internetwork is using subnets of the address 192.168.1.0 with a subset mask of 255.255.255.224. The routing protocol in use is RIP version 1. Which address could be assigned to the FastEthernet interface on RouterA?
A. 192.168.1.31
B. 192.168.1.64
C. 192.168.1.127
D. 192.168.1.190
E. 192.168.1.192
Answer: D[/am4show]
Explanation
255.255.255.224 = 1111 1111.1111 1111.1111 1111.1110 0000 (binary form)
Increment: 32
First subnetwork: 192.168.1.0 -> 192.168.1.31 (A is incorrect because 192.168.1.31 is a broadcast address)
Second subnetwork: 192.168.1.32 -> 192.168.1.63
Third subnetwork: 192.168.1.64 -> 192.168.1.95 (B is incorrect because 192.168.1.64 is a network address)
Fourth subnetwork: 192.168.1.96 -> 192.168.1.127 (C is incorrect because 192.168.1.127 is a broadcast address)
Fifth subnetwork: 192.168.1.128 -> 192.168.1.159
Sixth subnetwork: 192.168.1.160 -> 192.168.1.191 (D is correct because 192.168.1.190 is the last assignable host address of this subnetwork)
Seventh subnetwork: 192.168.1.192 -> 192.168.1.224 (E is incorrect because 192.168.1.192 is a network address)
Question 8
[am4show have=’p2;’]A network administrator is connecting PC hosts A and B directly through their Ethernet interfaces as shown in the graphic. Ping attempts between the hosts are unsuccessful. What can be done to provide connectivity between the hosts? (Choose two)

A. A crossover cable should be used in place of the straight-through cable.
B. A rollover cable should be used in place of the straight-through cable.
C. The subnet masks should be set to 255.255.255.192
D. A default gateway needs to be set on each host.
E. The hosts must be reconfigured to use private IP addresses for direct connections of this type.
F. The subnet masks should be set to 255.255.255.0
Answer: A F[/am4show]
Question 9
[am4show have=’p2;’]If an Ethernet port on a router was assigned an IP address of 172.16.112.1/20, what is the maximum number of hosts allowed on this subnet?
A. 1024
B. 2046
C. 4094
D. 4096
E. 8190
Answer: C[/am4show]
Question 10
[am4show have=’p2;’]Refer to the exhibit. After configuring two interfaces on the HQ router, the network administrator notices an error message. What must be done to fix this error?
| HQ#configure terminal HQ(config)# interface fastethernet 0/0 HQ(config-if)# ip address 192.168.1.17 255.255.255.0 HQ(config-if)# no shutdown HQ(config-if)# interface serial 0/0 HQ(config-if)# ip address 192.168.1.65 255.255.255.240 HQ(config-if)# no shutdown % 192.168.1.0 overlaps with FastEthernet0/0 |
A. The serial interface must be configured first.
B. The serial interface must use the address 192.168.1.2
C. The subnet mask of the serial interface should be changed to 255.255.255.0
D. The subnet mask of the FastEthernet interface should be changed to 255.255.255.240
E. The address of the FastEthernet interface should be changed to 192.168.1.66
Answer: D[/am4show]
Question 11
[am4show have=’p2;’]Refer to the exhibit. Host B has just been added to the network and must acquire an IP address. Which two addresses are possible addresses that will allow host B to communicate with other devices in the network? (Choose two)
A. 192.168.10.32
B. 192.168.10.38
C. 192.168.10.46
D. 192.168.10.47
E. 192.168.10.49
F. 192.168.10.51
Answer: B C[/am4show]
Explanation
The IP address of host B must be in the range of 192.168.10.32/28 subnet, which ranges from 192.168.10.32 to 192.168.10.47 (Increment: 16), except the IP addresses of 192.168.10.32, 192.168.10.46 (which are the network and broadcast addresses of the subnet), 192.168.10.33, 192.168.10.34 (which have been assigned to the interface’s router and the switch). Therefore there are only two IP addresses of 192.168.10.38 & 192.168.10.46.
Question 12
[am4show have=’p2;’]A network administrator has subnetted the 172.16.0.0 network using a subnet mask of 255.255.255.192. A duplicate IP address of 172.16.2.120 has accidentally been configured on a workstation in the network. The technician must assign this workstation a new IP address within that same subnetwork. Which address should be assigned to the workstation?
A. 172.16.1.80
B. 172.16.2.80
C. 172.16.1.64
D. 172.16.2.64
E. 172.16.2.127
F. 172.16.2.128
Answer: B[/am4show]
Question 13
[am4show have=’p2;’]What is the maximum number of bits that can be borrowed to create subnets if a Class B network address is being used?
A. 2
B. 6
C. 8
D. 14
E. 16
Answer: D[/am4show]
Question 14
[am4show have=’p2;’]The internetwork shown in the diagram is experiencing network connectivity problems. What is the cause of the problem?
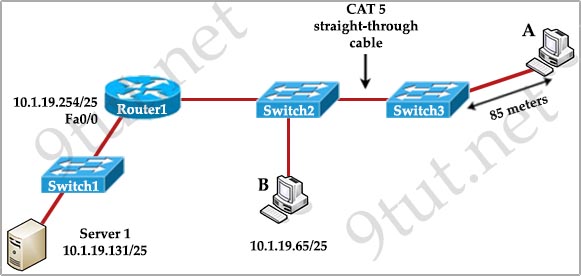
A. The cabling connecting host A to Switch3 is too long.
B. The address of host B is a broadcast address.
C. The IP address of interface Fa0/0 of Router1 is not a usable address.
D. The cable connecting Switch2 and Switch3 should be a crossover.
E. The IP address of Server 1 is in the wrong subnet.
Answer: D[/am4show]
Question 15
[am4show have=’p2;’]What is the subnet address for the IP address 172.19.20.23/28?
A. 172.19.20.0
B. 172.19.20.15
C. 172.19.20.16
D. 172.19.20.20
E. 172.19.20.32
Answer: C[/am4show]
Explanation
From the /28 we can find all information we need:
Increment: 16 (/28 = 11111111.11111111.11111111.11110000)
Network address: 172.19.20.16 (because 16 < 23)
Broadcast address: 172.16.20.31 (because 31 = 16 + 16 – 1)
In fact we don’t need to find out the broadcast address because the question only asks about subnet address (network address).
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Note: The ICND1 exam requires candidates to understand basic knowledge of dynamic routing protocols (RIP, EIGRP, OSPF).
Question 1
[am4show have=’p2;’]What is the best practice when assigning IP addresses in a small office of six hosts?
A. Use a DHCP server that is located at the headquarters.
B. Use a DHCP server that is located at the branch office.
C. Assign the addresses by using the local CDP protocol.
D. Assign the addresses statically on each node.
Answer: D[/am4show]
Question 2
[am4show have=’p2;’]The ip helper-address command does what?
A. assigns an IP address to a host
B. resolves an IP address from a DNS server
C. relays a DHCP request across networks
D. resolves an IP address overlapping issue
Answer: C[/am4show]
Explanation
By default, Cisco routers do not forward broadcast address. So what will happen if your PC does not in the same LAN with DHCP Server? Your PC (also a DHCP Client) will broadcast a packet but it is dropped by the router -> Your PC cannot get the IP from DHCP Server. So the “ip helper-address” command enables the DHCP broadcast to be forwarded to the DHCP server. For example, the IP address of your DHCP Server is 10.10.10.254 then we can type in the interface connecting with the DHCP Client (fa0/0 in this case) this command: “ip helper-address 10.10.10.254”.
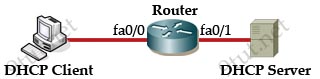
Note: When a client boots up for the first time, it transmits a DHCPDISCOVER message on its local physical subnet. Because the client has no way of knowing the subnet to which it belongs, the DHCPDISCOVER is an all-subnets broadcast (destination IP address of 255.255.255.255, which is a layer 3 broadcast address). The client does not have a configured IP address, so the source IP address of 0.0.0.0 is used.
Question 3
[am4show have=’p2;’]Refer to the exhibit. As packets travel from Mary to Robert, which three devices will use the destination MAC address of the packet to determine a forwarding path? (Choose three)
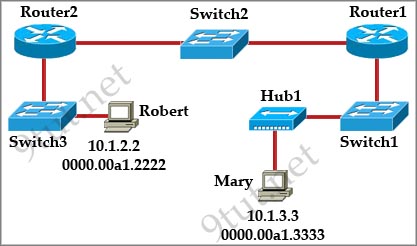
A. Hub1
B. Switch1
C. Router1
D. Switch2
E. Router2
F. Switch3
Answer: B D F[/am4show]
Explanation
Routers do not look to the destination MAC address to forward packet. It will find the next destination MAC address itself to replace the old destination MAC address of the received packet.
Hubs do not care about MAC addresses, it just flood the frames out of all its port except the port that sent it.
Therefore only three switches in the exhibit above use destination MAC address to determine the next hops.
Question 4
[am4show have=’p2;’]Refer to the exhibit. HostX is transferring a file to the FTP server. Point A represents the frame as it goes toward the Toronto router. What will the Layer 2 destination address be at this point?
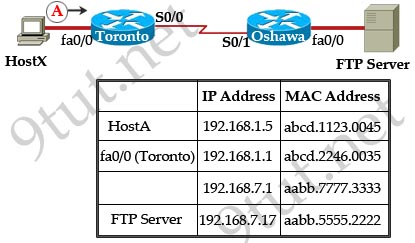
A. abcd. 1123.0045
B. 192.168.7.17
C. aabb.5555.2222
D. 192.168.1.1
E. abcd.2246.0035
Answer: E[/am4show]
Explanation
The destination MAC address at point A must be the MAC address of the interface fa0/0 of Toronto router -> E is correct.
Question 5
[am4show have=’p2;’]The command ip route 192.168.100.160 255.255.255.224 192.168.10.2 was issued on a router. No routing protocols or other static routes are configured on the router. Which statement is true about this command?
A. The interface with IP address 192.168.10.2 is on this router.
B. The command sets a gateway of last resort for the router.
C. Packets that are destined for host 192.168.100.160 will be sent to 192.168.10.2.
D. The command creates a static route for all IP traffic with the source address 192.168.100.160.
Answer: C[/am4show]
Explanation
The simple syntax of static route:
ip route destination-network-address subnet-mask {next-hop-IP-address | exit-interface}
+ destination-network-address: destination network address of the remote network
+ subnet mask: subnet mask of the destination network
+ next-hop-IP-address: the IP address of the receiving interface on the next-hop router
+ exit-interface: the local interface of this router where the packets will go out
Therefore the purpose of this command is to send any packets with destination IP address in the range of 192.168.100.160/27 subnet to 192.168.10.2. In fact, answer C is a bit weird when saying “host 192.168.100.160” because 192.168.100.160 is the network address in this case and it cannot be assigned to a host. But answer C is the most suitable answer for this question.
Question 6
[am4show have=’p2;’]What does administrative distance refer to?
A. the cost of a link between two neighboring routers
B. the advertised cost to reach a network
C. the cost to reach a network that is administratively set
D. a measure of the trustworthiness of a routing information source
Answer: D[/am4show]
Question 7
[am4show have=’p2;’]Refer to the exhibit. If host A sends an IP packet to host B, what will the source physical address be in the frame when it reaches host B?
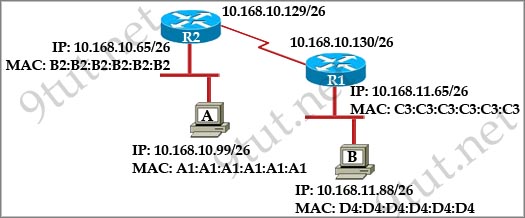
A. 10.168.10.99
B. 10.168.11.88
C. A1:A1:A1:A1:A1:A1
D. B2:B2:B2:B2:B2:B2
E. C3:C3:C3:C3:C3:C3
F. D4:D4:D4:D4:D4:D4
Answer: E[/am4show]
Explanation
After receiving a packet, the router will keep the source and destination IP addresses while change the source MAC address (to the MAC address of its outgoing interface) and the destination MAC address (to the MAC address of the next-hop interface). Therefore when the packet reaches host B, the source MAC address must be the MAC address of the outgoing interface of R1.
Question 8
[am4show have=’p2;’]Refer to the exhibit. Host A is sending a packet to Host B for the first time. What destination MAC address will Host A use in the ARP request?
A. 192.168.0.1
B. 172.16.0.50
C. 00-17-94-61-18-b0
D. 00-19-d3-2d-c3-b2
E. ff-ff-ff-ff-ff-ff
F. 255.255.255.255
Answer: E[/am4show]
Explanation
Host A knows the IP address of Host B but it does not know the MAC address of host B, so it have to create an ARP Request (which is a broadcast frame) to ask for the MAC address of host B. When Router1 receives this ARP Request, it answers with its own MAC address.
Question 9
[am4show have=’p2;’]Refer to the exhibit. Host A can communicate with Host B but not with Host C or D. How can the network administrator solve this problem?
A. Configure Hosts C and D with IP addresses in the 192.168.2.0 network.
B. Install a router and configure a route to route between VLANs 2 and 3.
C. Install a second switch and put Hosts C and D on that switch while Hosts A and B remain on the original switch.
D. Enable the VLAN trunking protocol on the switch.
Answer: B[/am4show]
Question 10
[am4show have=’p2;’]Refer to the exhibit. The host in Kiev sends a request for an HTML document to the server in Minsk. What will be the source IP address of the packet as it leaves the Kiev router?
A. 10.1.0.1
B. 10.1.0.5
C. 10.1.0.6
D. 10.1.0.14
E. 10.1.1.16
F. 10.1.2.8
Answer: E[/am4show]
Explanation
Along the routing path, the source and destination IP address will not change so the source IP will always be 10.1.1.16.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Note: The ICND1 exam requires candidates to understand basic knowledge of dynamic routing protocols (RIP, EIGRP, OSPF).
Question 1
[am4show have=’p2;’]Refer to the exhibit. Mary is sending an instant message to Robert. The message will be broken into a series of packets that will traverse all network devices. What addresses will populate these packets as they are forwarded from Router1 to Router2?
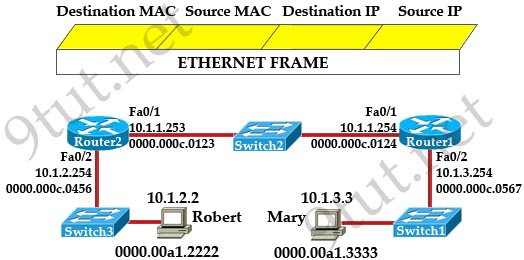
A. 
B.
C.
D.
Answer: A[/am4show]
Explanation
After receiving a packet, the router will keep the source and destination IP addresses (10.1.3.3 and 10.1.2.2, respectively) while change the source MAC address (to the MAC address of its outgoing interface) and the destination MAC address (to the MAC address of the next-hop interface). Therefore when the packet leaves Router1, the source MAC address must be the MAC address of the outgoing interface of Router1 (0000.000c.0124) and the destination MAC address must be the MAC of fa0/1 of R2 (0000.000c.0123).
Question 2
[am4show have=’p2;’]Refer to the exhibit. Which two statements are correct? (Choose two)
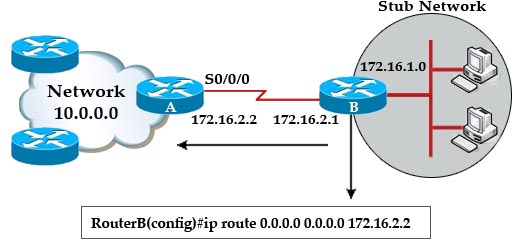
A. This is a default route.
B. Adding the subnet mask is optional for the ip route command.
C. This will allow any host on the 172.16.1.0 network to reach all known destinations beyond RouterA.
D. This command is incorrect, it needs to specify the interface, such as s0/0/0 rather than an IP address.
E. The same command needs to be entered on RouterA so that hosts on the 172.16.1.0 network can reach network 10.0.0.0.
Answer: A C[/am4show]
Explanation
A static route with 0.0.0.0 0.0.0.0 will become a default route. The default route means: “send all traffic to this IP address”. So the default route “ip route 0.0.0.0 0.0.0.0 172.16.2.2” will send all traffic to 172.16.2.2.
Question 3
[am4show have=’p2;’]Refer to the exhibit. Which command would you use to configure a static route on Router1 to network 192.168.202.0/24 with a nondefault administrative distance?
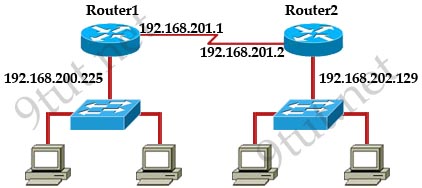
A. router1(config)#ip route 1 192.168.201.1 255.255.255.0 192.168.201.2
B. router1(config)#ip route 192.168.202.0 255.255.255.0 192.168.201.2 1
C. router1(config)#ip route 5 192.168.202.0 255.255.255.0 192.168.201.2
D. router1(config)#ip route 192.168.202.0 255.255.255.0 192.168.201.2 5
Answer: D[/am4show]
Explanation
The Administrative Distance (AD) parameter must be put at the end of the “ip route” command. The default AD is 1.
Question 4
[am4show have=’p2;’]Refer to the exhibit. The output is from a router in a large enterprise. From the output, determine the role of the router.
A. A Core router.
B. The HQ Internet gateway router.
C. The WAN router at the central site.
D. Remote stub router at a remote site.
Answer: D[/am4show]
Explanation
This router only have directly connected networks (symbolized by letter “C”) and one default route out of Serial0/0. Maybe this is a stub router with only one connection to the Headquarter or to the Internet.
Question 5
[am4show have=’p2;’]Refer to the exhibit. What is the simplest way to configure routing between the regional office network 10.89.0.0/20 and the corporate network?
A. router1(config)#ip route 10.89.0.0 255.255.240.0 10.89.16.2
B. router2(config)#ip route 10.89.3.0 255.255.0.0 10.89.16.2
C. router1(config)#ip route 10.89.0.0 255.255.240.0 10.89.16.1
D. router2(config)#ip route 0.0.0.0 0.0.0.0 10.89.16.1
Answer: D[/am4show]
Explanation
In this topology, R2 is a stub router with only one connection to the HQ network so the best way to configure routing is to set a static route (default route) to R1.
Question 6
[am4show have=’p2;’]Refer to the exhibit. What must be configured to establish a successful connection from Host A to switch SW-A through router RT-A?

A. VLAN 1 on RT-A
B. IP routing on SW-A
C. default gateway on SW-A
D. crossover cable connecting SW-A and RT-A
Answer: C[/am4show]
Explanation
Host A is in a different subnet of SW-A so SW-A does not know how to send data to host A so it needs to be assigned with a default gateway. The command to assign a default gateway to a switch is “ip default-gateway “. Please notice this command only has effect when “ip routing” is disabled on SW-A.
Question 7
[am4show have=’p2;’]Refer to the exhibit. Which default gateway address should be assigned to HostA?
A. 192.168.1.1
B. 192.168.1.65
C. 192.168.1.66
D. 192.168.1.129
E. 10.1.1.1
F. 10.1.1.2
Answer: B[/am4show]
Explanation
The default gateway of Host A should be the connected interface of the router, except host A is connected with a Layer 3 switch. In this case, Switch A is a pure Layer 2 switch and Switch A IP address is just for management purpose.
Question 8
[am4show have=’p2;’]Which value is indicated by the next hop in a routing table?
A. preference of the route source
B. IP address of the remote router for forwarding the packets
C. how the route was learned
D. exit interface IP address for forwarding the packets
Answer: B[/am4show]
Question 9
[am4show have=’p2;’]Which component of a routing table entry represents the subnet mask?
A. routing protocol code
B. prefix
C. metric
D. network mask
Answer: D[/am4show]
Question 10
[am4show have=’p2;’]Which component of the routing table ranks routing protocols according to their preferences?
A. administrative distance
B. next hop
C. metric
D. routing protocol code
Answer: A[/am4show]
Explanation
The administrative distance of each protocol is compared to see if that route is better or not.
Question 11
[am4show have=’p2;’]Which route source code represents the routing protocol with a default administrative distance of 90 in the routing table?
A. S
B. E
C. D
D. R
E. O
Answer: C[/am4show]
Explanation
Letter “D” is used to symbolize for EIGRP (with a default AD of 90). Letter “E” is not used for EIGRP because it has been used for Exterior Gateway Protocol (EGP) which is a obsolete routing protocol now.
Note: The ICND1 exam requires candidates to understand basic knowledge of dynamic routing protocols (RIP, EIGRP, OSPF).
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]When enabled, which feature prevents routing protocols from sending hello messages on an interface?
A. virtual links
B. passive-interface
C. directed neighbors
D. OSPF areas
Answer: B[/am4show]
Question 2
[am4show have=’p2;’]Which routing protocol has the smallest default administrative distance?
A. IBGP
B. OSPF
C. IS-IS
D. EIGRP
E. RIP
Answer: D[/am4show]
Explanation
The Administrative Distance (AD) of popular routing protocols is shown below. You should learn them by heart:
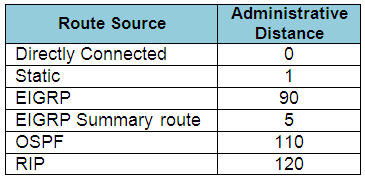
Note: The AD of iBGP is 200
The smaller the AD is, the better it is. The router will choose the routing protocol with smallest AD.
In this case EIGRP with AD of 90 is the smallest one.
Question 3
[am4show have=’p2;’]Which statement about static routes is true?
A. The source interface can be configured to make routing decisions.
B. A subnet mask is entered for the next-hop address.
C. The subnet mask is 255.255 255.0 by default
D. The exit interface can be specified to indicate where the packets will be routed.
Answer: D[/am4show]
Question 4
[am4show have=’p2;’]Which statement about routing protocols is true?
A. Link-state routing protocols choose a path by the number of hops to the destination.
B. OSPF is a link-state routing protocol.
C. Distance-vector routing protocols use the Shortest Path First algorithm.
D. IS-IS is a distance-vector routing protocol.
Answer: B[/am4show]
Question 5
[am4show have=’p2;’]Which dynamic routing protocol uses only the hop count to determine the best path to a destination?
A. IGRP
B. RIP
C. EIGRP
D. OSPF
Answer: B[/am4show]
Question 6
[am4show have=’p2;’]A workstation has just resolved a browser URL to the IP address of a server. What protocol will the workstation now use to determine the destination MAC address to be placed into frames directed toward the server?
A. HTTP
B. DNS
C. DHCP
D. RARP
E. ARP
Answer: E[/am4show]
Explanation
After resolving a browser URL to an IP address (via DNS server), the workstation must learn the MAC address of the server so that it can create a complete packet (a complete packet requires destination MAC and IP address, source MAC and IP address). Therefore the workstation must use ARP to find out the MAC address from the IP address.
Question 7
[am4show have=’p2;’]Refer to the exhibit. What is the simplest way to configure routing between the regional office network 10.89.0.0/20 and the corporate network?

A. router1(config)#ip route 10.89.0.0 255.255.240.0 10.89.16.2
B. router2(config)#ip route 10.89.3.0 255.255.0.0 10.89.16.2
C. router1(config)#ip route 10.89.0.0 255.255.240.0 10.89.16.1
D. router2(config)#ip route 0.0.0.0 0.0.0.0 10.89.16.1
Answer: D[/am4show]
Explanation
In this topology, R2 is a stub router with only one connection to the HQ network so the best way to configure routing is to set a static route (default route) to R1.
Question 8
[am4show have=’p2;’]Refer to the output of the corporate router routing table shown in the graphic. The corporate router receives an IP packet with a source IP address of 192.168.214.20 and a destination address of 192.168.22.3. What will the router do with this packet?
A. It will encapsulate the packet as Frame Relay and forward it out interface Serial 0/0.117.
B. It will discard the packet and send an ICMP Destination Unreachable message out interface FastEthernet 0/0.
C. It will forward the packet out interface Serial 0/1 and send an ICMP Echo Reply message out interface serial 0/0.102.
D. It will change the IP packet to an ARP frame and forward it out FastEthernet 0/0.
Answer: B[/am4show]
Question 9
[am4show have=’p2;’]The network administrator has found the following problem. The remote networks 172.16.10.0, 172.16.20.0, and 172.16.30.0 are accessed through the Central router’s serial 0/0 interface. No users are able to access 172.16.20.0. After reviewing the command output shown in the graphic, what is the most likely cause of the problem?
A. no gateway of last resort on Central
B. Central router’s not receiving 172.16.20.0 update
C. incorrect static route for 172.16.20.0
D. 172.16.20.0 not located in Central’s routing table
Answer: C[/am4show]
Question 10
[am4show have=’p2;’]What information does a router running a link-state protocol use to build and maintain its topological database? (Choose two)
A. hello packets
B. SAP messages sent by other routers
C. LSAs from other routers
D. beacons received on point-to-point links
E. routing tables received from other link-state routers
F. TTL packets from designated routers
Answer: A C[/am4show]
Explanation
Link-state protocol uses hello packets to discover neighbors and establish adjacencies. After that, the routers begin sending out LSAs to every neighbor (each received LSA is copied and forwarded to every neighbor except the one that sent the LSA)
Question 11
[am4show have=’p2;’]A router has learned three possible routes that could be used to reach a destination network. One route is from EIGRP and has a composite metric of 20514560. Another route is from OSPF with a metric of 782. The last is from RIPv2 and has a metric of 4. Which route or routes will the router install in the routing table?
A. the OSPF route
B. the EIGRP route
C. the RIPv2 route
D. all three routes
E. the OSPF and RIPv2 routes
Answer: B[/am4show]
Explanation
When one route is advertised by more than one routing protocol, the router will choose to use the routing protocol which has lowest Administrative Distance. The Administrative Distances of popular routing protocols are listed below:
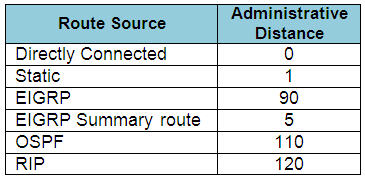
Note: The ICND1 exam requires candidates to understand basic knowledge of dynamic routing protocols (RIP, EIGRP, OSPF).
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Some routers have been configured with default routes. What are some of the advantages of using default routes? (Choose two)
A. They establish routes that will never go down.
B. They keep routing tables small.
C. They require a great deal of CPU power.
D. They allow connectivity to remote networks that are not in the routing table
E. They direct traffic from the internet into corporate networks.
Answer: B D[/am4show]
Question 2
[am4show have=’p2;’]Refer to the exhibit, PC1 pings PC2. What three things will CORE router do with the data that is received from PC1? (Choose three)
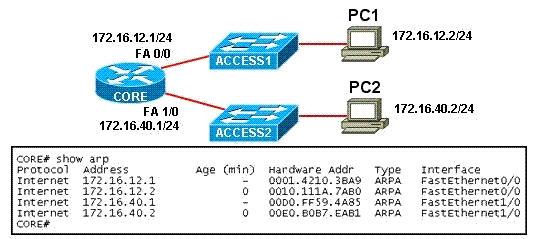
A. The data frames will be forwarded out interface FastEthernet0/1 of CORE router.
B. The data frames will be forwarded out interface FastEthernet1/0 of CORE router.
C. CORE router will replace the destination IP address of the packets with the IP address of PC2.
D. CORE router will place the MAC address of PC2 in the destination MAC address of the frames.
E. CORE router will put the IP address of the forwarding FastEthernet interface in the place of the source IP address in the packets.
F. CORE router will put the MAC address of the forwarding FastEthernet interface in the place of the source MAC address.
Answer: B D F[/am4show]
Question 3
[am4show have=’p2;’]Which three statements are correct about RIP version 2? (Choose three)
A. It has the same maximum hop count as version 1.
B. It uses broadcasts for its routing updates.
C. It is a classless routing protocol.
D. It has a lower default administrative distance than RIP version 1.
E. It supports authentication.
F. It does not send the subnet mask in updates.
Answer: A C E[/am4show]
Explanation
A and E are correct according to the theory of RIP.
RIP version 1 updates are broadcasts, and RIP version 2 updates are multicast to 224.0.0.9 -> B is not correct.
RIP v1 is a classful routing protocol but RIP v2 is a classless routing protocol -> C is correct.
RIPv1 and RIPv2 have the same default administrative distance of 120 -> D is not correct.
RIPv2 is a classless routing protocol so it does send the subnet mask in updates -> F is not correct.
Question 4
[am4show have=’p2;’]A technician pastes the configurations in the exhibit into the two new routers shown. Otherwise, the routers are configured with their default configurations. A ping from Host1 to Host2 fails, but the technician is able to ping the S0/0 interface of R2 from Host1. The configurations of the hosts have been verified as correct. What is the cause of the problem?

A. The serial cable on R1 needs to be replaced.
B. The interfaces on R2 are not configured properly.
C. R1 has no route to the 192.168.1.128 network.
D. The IP addressing scheme has overlapping subnetworks.
E. The ip subnet-zero command must be configured on both routers.
Answer: C[/am4show]
Explanation
Host1 can ping the Serial interface of R2 because R1 has the network of 192.168.1.4/30 as directly connected route. But R1 does not know how to route to the network of Host2 (192.168.1.128/26) so R1 will drop that ping without trying to send it out S0/0 interface. To make the ping work, we have to configure a route pointing to that network (for example: ip route 192.168.1.128 255.255.255.192 s0/0 on R1).
Question 5
[am4show have=’p2;’]After the show ip route command has been entered, the following routes are displayed. Which route will not be entered into the routing table of a neighboring router?
A. R 192.168.8.0/24 [120/1] via 192.168.2.2, 00:00:10, Serial0
B. R 192.168.11.0/24 [120/7] via 192.168.9.1, 00:00:03, Serial1
C. C 192.168.1.0/24 is directly connected, Ethernet0
D. R 192.168.5.0/24 [120/15] via 192.168.2.2, 00:00:10, Serial0
Answer: D[/am4show]
Explanation
The route 192.168.5.0/24 currently has the metric of 15 so this router will add 1 hop count before sending out to its neighboring router. With RIP, a metric of 16 means that network is down -> it will not be installed in the routing table of the neighboring router.
Question 6
[am4show have=’p2;’]Refer to the exhibit. What value should be displayed in Box 1 of the ipconfig output of host A?
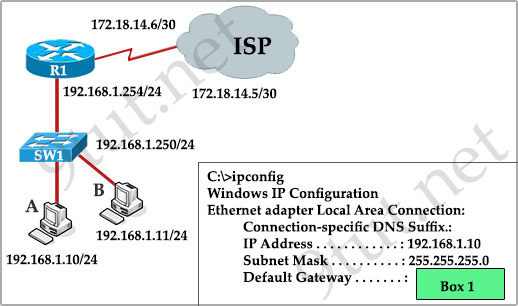
A. 172.18.14.5
B. 172.18.14.6
C. 192.168.1.10
D. 192.168.1.11
E. 192.168.1.250
F. 192.168.1.254
Answer: F[/am4show]
Question 7
[am4show have=’p2;’]After you configure a default route to the Internet on a router, the route is missing from the routing table. Which option describes a possible reason for the problem?
A. The next-hop address is unreachable.
B. The default route was configured on a passive interface.
C. Dynamic routing is disabled.
D. Cisco Discovery Protocol is disabled on the interface used to reach the next hop.
Answer: A[/am4show]
Explanation
The passive interface only prevents routing updates from being sent and received on that interface. It does not affect the default route. But if we configure a default route like this:
Router(config)#ip route 0.0.0.0 0.0.0.0 192.168.1.2
Then if the next-hop address is down (unreachable) then this default route would be removed from the routing table.
Question 8
[am4show have=’p2;’]Which information is used to install the best route to a destination in IP routing table?
A. the tunnel ID
B. the interface number
C. the prefix length
D. the autonoums system
Answer: C[/am4show]
Question 9
[am4show have=’p2;’]What is the administrative distance of connected routes?
A.1
B. 0
C. 10
D. 90
Answer: B[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Note: Although OSPF topic is under ICND2 but some very basic OSPF questions are asked in the ICND1 so you should take some time to know about it. If you are not sure about OSPF, please read my OSPF tutorial first.
Question 1
[am4show have=’p2;’]Which of the following describe the process identifier that is used to run OSPF on a router? (Choose two)
A. It is locally significant.
B. It is globally significant.
C. It is needed to identify a unique instance of an OSPF database.
D It is an optional parameter required only if multiple OSPF processes are running on the router.
E. All routers in the same OSPF area must have the same process ID if they are to exchange routing information.
Answer: A C[/am4show]
Question 2
[am4show have=’p2;’]Open Shortest Path First (OSPF) is a routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) working group of the Internet Engineering Task Force (IETF). What is the default administrative distance of the OSPF routing protocol?
A. 90
B. 100
C. 110
D. 20
E. 130
F. 170
Answer: C[/am4show]
Question 3
[am4show have=’p2;’]Which statements describe the routing protocol OSPF? (Choose three)
A. It supports VLSM.
B. It is used to route between autonomous systems.
C. It confines network instability to one area of the network.
D. It increases routing overhead on the network.
E. It allows extensive control of routing updates.
F. It is simpler to configure than RIPv2.
Answer: A C E[/am4show]
Explanation
Answer A and C are obviously correct. For answer E, it allows extensive control of routing updates via Link-State Advertisement (LSA). Administrators can filter these LSAs to meet their requirements easily.
Question 4
[am4show have=’p2;’]R1 is unable to establish an OSPF neighbor relationship with R3. What are possible reasons for this problem? (Choose two)
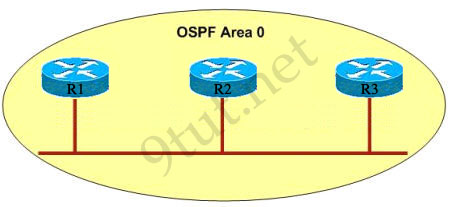
A. All of the routers need to be configured for backbone Area 1.
B. R1 and R2 are the DR and BDR, so OSPF will not establish neighbor adjacency with R3.
C. A static route has been configured from R1 to R3 and prevents the neighbor adjacency from being established.
D. The hello and dead interval timers are not set to the same values on R1 and R3.
E. EIGRP is also configured on these routers with a lower administrative distance.
F. R1 and R3 are configured in different areas.
Answer: D F[/am4show]
Explanation
A is not correct because the backbone area of OSPF is always Area 0.
B is not correct because R1 or R3 must be the DR or BDR -> it has to establish neighbor adjacency with the other.
C is not correct because OSPF neighbor relationship is not established based on static routing. It uses multicast address 224.0.0.5 to establish OSPF neighbor relationship.
E is not correct because configure EIGRP on these routers (with a lower administrative distance) will force these routers to run EIGRP, not OSPF.
D and F are correct because these entries must match on neighboring routers:
– Hello and dead intervals
– Area ID (Area 0 in this case)
– Authentication password
– Stub area flag
Question 5
[am4show have=’p2;’]Which address are OSPF hello packets addressed to on point-to-point networks?
A. 224.0.0.5
B. 172.16.0.1
C. 192.168.0.5
D. 223.0.0.1
E. 254.255.255.255
Answer: A[/am4show]
Question 6
[am4show have=’p2;’]RouterD# show ip interface brief

Given the output for this command, if the router ID has not been manually set, what router ID will OSPF use for this router?
A. 10.1.1.2
B. 10.154.154.1
C. 172.16.5.1
D. 192.168.5.3
Answer: C[/am4show]
Explanation
The highest IP address of all loopback interfaces will be chosen -> Loopback 0 will be chosen as the router ID.
Question 7
[am4show have=’p2;’]ROUTER# show ip route
| 192.168.12.0/24 is variably subnetted, 9 subnets, 3 masks C 192.168.12.64 /28 is directly connected, Loopback1 C 192.168.12.32 /28 is directly connected, Ethernet0 C 192.168.12.48 /28 is directly connected, Loopback0 O 192.168.12.236 /30 [110/128] via 192.168.12.233, 00:35:36, Serial0 C 192.168.12.232 /30 is directly connected, Serial0 O 192.168.12.245 /30 [110/782] via 192.168.12.233, 00:35:36, Serial0 O 192.168.12.240 /30 [110/128] via 192.168.12.233, 00:35:36, Serial0 O 192.168.12.253 /30 [110/782] via 192.168.12.233, 00:35:37, Serial0 O 192.168.12.249/30 [110/782] via 192.168.12.233, 00:35:37, Serial0 O 192.168.12.240/30 [110/128] via 192.168.12.233, 00:35:36, Serial0 |
To what does the 128 refer to in the router output above?
A. OSPF cost
B. OSPF priority
C. OSPF hop count 5
D. OSPF ID number
E. OSPF administrative distance
Answer: A[/am4show]
Explanation
OSPF uses a metric referred to as cost. The cost of the entire path is the sum of the costs of the outgoing interfaces along the path. Cisco uses a simple formula to calculate OSPF cost:
OSPF cost = 108 / Bandwidth (bit)
Therefore, a 100 Mbps FastEthernet interface will have the cost of 108 / 100,000,000 (bps) = 1
Note: Cost for interfaces with bandwidth equal or larger than 10^8 bps is normalized to 1 so a 1Gbps interface will also have OSPF cost of 1.
For “O 192.168.12.240 /30 [110/128] via 192.168.12.233, 00:35:36, Serial0″ line, the first number in the brackets is the administrative distance of the information source; the second number is the metric for the route -> In this case the second number is the OSPF cost.
Question 8
[am4show have=’p2;’]

The internetwork infrastructure of company XYZ consists of a single OSPF area as shown in the graphic. There is concern that a lack of router resources is impeding internetwork performance.
As part of examining the router resources the OSPF DRs need to be known.
All the router OSPF priorities are at the default and the router IDs are shown with each router.
Which routers are likely to have been elected as DR? (Choose two)
A. Corp-1
B. Corp-2
C. Corp-3
D. Corp4
E. Branch-1
F. Branch-2
Answer: D F[/am4show]
Explanation
There are 2 segments on the topology above which are separated by Corp-3 router. Each segment will have a DR so we have 2 DRs.
To select which router will become DR they will compare their router-IDs. The router with highest (best) router-ID will become DR. The router-ID is chosen in the order below:
+ The highest IP address assigned to a loopback (logical) interface.
+ If a loopback interface is not defined, the highest IP address of all active router’s physical interfaces will be chosen.
In this question, the IP addresses of loopback interfaces are not mentioned so we will consider IP addresses of all active router’s physical interfaces. Router Corp-4 (10.1.40.40) & Branch-2 (10.2.20.20) have highest “active” IP addresses so they will become DRs.
Question 9
[am4show have=’p2;’]What information does a router running a link-state protocol use to build and maintain its topological database? (Choose two)
A. hello packets
B. SAP messages sent by other routers
C. LSAs from other routers
D. beacons received on point-to-point links
E. routing tables received from other link-state routers
F. TTL packets from designated routers
Answer: A C[/am4show]
Question 10
[am4show have=’p2;’]What is the default administrative distance of OSPF?
A. 90
B. 100
C. 110
D. 120
Answer: C
Explanation
The Administrative Distances (AD) of popular routing protocols are listed below:

Question 11
[am4show have=’p2;’]Which characteristics are representative of a link-state routing protocol? (Choose three)
A. provides common view of entire topology
B. exchanges routing tables with neighbors
C. calculates shortest path
D. utilizes event-triggered updates
E. utilizes frequent periodic updates
Answer: A C D[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]What is the default lease time for a DHCP binding?
A. 24 hours
B. 12 hours
C. 48 hours
D. 36 hours
Answer: A[/am4show]
Explanation
We can use the “lease” command to specify the duration of the lease: lease {days [hours][minutes] | infinite}
The default is a one-day lease.
Question 2
[am4show have=’p2;’]Refer to the exhibit. The DHCP settings have recently been changed on the DHCP server and the client is no longer able to reach network resources. What should be done to correct this situation?
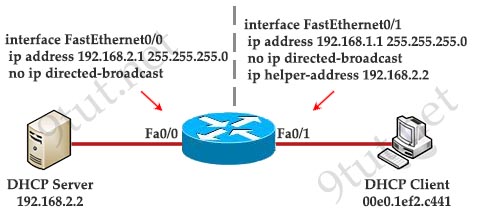
A. Verify that the DNS server address is correct in the DHCP pool.
B. Ping the default gateway to populate the ARP cache.
C. Use the tracert command on the DHCP client to first determine where the problem is located.
D. Clear all DHCP leases on the router to prevent address conflicts.
E. Issue the ipconfig command with the /release and /renew options in a command window.
Answer: E[/am4show]
Question 3
[am4show have=’p2;’]You have configured the host computers on a campus LAN to receive their DHCP addresses from the local router to be able to browse their corporate site. Which statement about the network environment is true?
A. It supports a DNS server for use by DHCP clients.
B. Two host computers may be assigned the same IP address.
C. The DNS server must be configured manually on each host.
D. The domain name must be configured locally on each host computer.
Answer: A[/am4show]
Explanation
The local router in this case is called a DHCP server. The main purpose of a DHCP server is to assign IP addresses to the clients. Besides that, a DHCP server can also specify the IP address of the DNS server and specify the domain name for the clients.
For more information about configuring a DHCP server, please read: http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/ipaddr_dhcp/configuration/12-4t/dhcp-12-4t-book/config-dhcp-server.html
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Note: If you are not sure about NAT/PAT, please read my Network Address Translation NAT Tutorial.
Question 1
[am4show have=’p2;’]What happens when computers on a private network attempt to connect to the Internet through a Cisco router running PAT?
A. The router uses the same IP address but a different TCP source port number for each connection.
B. An IP address is assigned based on the priority of the computer requesting the connection.
C. The router selects an address from a pool of one-to-one address mappings held in the lookup table.
D. The router assigns a unique IP address from a pool of legally registered addresses for the duration of the connection.
Answer: A[/am4show]
Explanation
Port Address Translation (PAT) can support thousands of users connect to the Internet using only one real global IP address. With PAT, each computer will be assigned a separate port number so that the router can identify which computer should receive the return traffic.
Question 2
[am4show have=’p2;’]In the configuration of NAT, what does the keyword overload signify?
A. When bandwidth is insufficient, some hosts will not be allowed to access network translation.
B. The pool of IP addresses has been exhausted.
C. Multiple internal hosts will use one IP address to access external network resources.
D. If the number of available IP addresses is exceeded, excess traffic will use the specified address pool.
Answer: C[/am4show]
Explanation
The keyword “overload” specifies we are using NAT Overload (PAT) in which multiple internal hosts will use only one IP address to access external network resources.
Question 3
[am4show have=’p2;’]When configuring NAT, the Internet interface is considered to be what?
A. local
B. inside
C. global
D. outside
Answer: D[/am4show]
Explanation
On the interface connecting to the Internet of the router we have to use the command “ip nat outside” for NAT to work. It identifies that interface as the outside interface.
Question 4
[am4show have=’p2;’]Which NAT type is used to translate a single inside address to a single outside address?
A. dynamic NAT
B. NAT overload
C. PAT
D. static NAT
Answer: D[/am4show]
Explanation
There are two types of NAT translation: dynamic and static.
Static NAT: Designed to allow one-to-one mapping between local and global addresses. This flavor requires you to have one real Internet IP address for every host on your network
Dynamic NAT: Designed to map an unregistered IP address to a registered IP address from a pool of registered IP addresses. You don’t have to statically configure your router to map an inside to an outside address as in static NAT, but you do have to have enough real IP addresses for everyone who wants to send packets through the Internet. With dynamic NAT, you can configure the NAT router with more IP addresses in the inside local address list than in the inside global address pool. When being defined in the inside global address pool, the router allocates registered public IP addresses from the pool until all are allocated. If all the public IP addresses are already allocated, the router discards the packet that requires a public IP address.
In this question we only want to translate a single inside address to a single outside address so static NAT should be used.
Question 5
[am4show have=’p2;’]Which statement about the inside interface configuration in a NAT deployment is true?
A. It is defined globally
B. It identifies the location of source addresses for outgoing packets to be translated using access or route maps.
C. It must be configured if static NAT is used
D. It identifies the public IP address that traffic will use to reach the internet.
Answer: B[/am4show]
Explanation
When we specify a NAT “inside” interface (via the “ip nat inside” command under interface mode), we are specifying the source IP addresses. Later in the “ip nat” command under global configuration mode, we will specify the access or route map for these source addresses.
For example the command:
Router(config)# ip nat inside source list 1 pool PoolforNAT
after the keyword “source” we need to specify one of the three keywords:
+ list: specify access list describing local addresses (but this command does not require an “inside” interface to be configured)
+ route-map: specify route-map
+ static: specify static local -> global mapping
Question 6
[am4show have=’p2;’]Under which circumstance should a network administrator implement one-way NAT?
A. when the network must route UDP traffic
B. when traffic that originates outside the network must be routed to internal hosts
C. when traffic that originates inside the network must be routed to internal hosts
D. when the network has few public IP addresses and many private IP addresses require outside access
Answer: B[/am4show]
Question 7
[am4show have=’p2;’]How many addresses will be available for dynamic NAT translation when a router is configured with the following commands?
Router(config)#ip nat pool TAME 209.165.201.23 209.165.201.30 netmask 255.255.255.224
Router(config)#ip nat inside source list 9 pool TAME
A. 7
B. 8
C. 9
D. 10
E. 24
F. 32
Answer: B[/am4show]
Question 8
[am4show have=’p2;’]What does the “Inside Global” address represent in the configuration of NAT?
A. the summarized address for all of the internal subnetted addresses
B. the MAC address of the router used by inside hosts to connect to the Internet
C. a globally unique, private IP address assigned to a host on the inside network
D. a registered address that represents an inside host to an outside network
Answer: D[/am4show]
Question 9
[am4show have=’p2;’]Refer to the graphic:
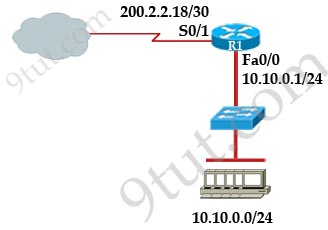
A company wants to use NAT in the network shown. Which commands will apply the NAT configuration to the proper interfaces? (Choose two)
A.
R1 (config)# interface serial0/1
R1 (config-if)# ip nat inside
B.
R1 (config)# interface serial0/1
R1 (config-if)# ip nat outside
C.
R1 (config)# interface FastEthernet0/0
R1 (config-if)# ip nat inside
D.
R1 (config)# interface FastEthernet0/0
R1 (config-if)# ip nat outside
E.
R1(config)# interface serial0/1
R1 (config-if)# ip nat outside source pool 200.2.2.18 255.255.255.252
F.
R1 (config)# interface FastEthernet0/0
R1 (config-if)# ip nat inside source 10.10.0.0 255.255.255.0
Answer: B C[/am4show]
Explanation
After configuring all the requirements for NAT, we need to apply them to “source interface” and “outgoing” interface by going to the appropriate interfaces and type the “ip nat inside” and “ip nat outside” commands.
Question 10
[am4show have=’p2;’]Which form of NAT maps multiple private IP addresses to a single registered IP address by using different ports?
A. static NAT
B. dynamic NAT
C. overloading
D. overlapping
E. port loading
Answer: C[/am4show]
Question 11
[am4show have=’p2;’]Which statement describes the effect of the overload keyword in the ip nat inside source list 90 interface ethernet 0/0 overload command?
A. Addresses that match address list inside are translated to the IP address of the Ethernet 0/0 interface.
B. Hosts that match access inside are translated to an address in the Ethernet 0/0 network.
C. Hosts on the Ethernet 0/0 LAN are translated to the address pool in access list 90.
D. Addresses that match access list 90 are translated through PAT to the IP address of the Ethernet 0/0 interface
Answer: D[/am4show]
Explanation
The command ip nat inside source list 90 interface ethernet 0/0 overload means:
+ “ip nat inside”: “I want to NAT from inside to outside”
+ “list 90” means “the source IP addresses to NAT are included in Access-list 90”
+ “interface ethernet 0/0” means “NAT out of this interface”
+ “overload” means “use PAT for the IP translation”
Question 12
[am4show have=’p2;’]Which NAT command can be applied to an interface?
A. ip nat inside
B. ip nat inside test access-list-number pool pool-name
C. ip nat inside source static 10.10.10.0 10.10.10.50
D. ip nat pool test 10.10.10.0 10.10.10.50 255.255.255.0
Answer: A[/am4show]
Explanation
The “ip nat inside” command can be applied to an interface to indicate this interface is the source NAT.
Question 13
[am4show have=’p2;’]Which command displays the number of times that an individual router translated an inside address to an outside address?
A. show ip protocol 0
B. show ip nat translation
C. show counters
D. show ip route
E. show ip nat statistics
Answer: E[/am4show]
Explanation
The outputs of the two commands “show ip nat statistics” and “show ip nat translation” are shown below:
Router#show ip nat statistics Total active translations: 2 (0 static, 2 dynamic; 2 extended) Peak translations: 3, occurred 5d04h ago Outside interfaces: Serial1/0 Inside interfaces: Ethernet0/1 Hits: 34531 Misses: 0 CEF Translated packets: 34526, CEF Punted packets: 0 Expired translations: 11 Dynamic mappings: -- Inside Source [Id: 1] access-list nat_traffic interface Serial1/0 refcount 2 Total doors: 0 Appl doors: 0 Normal doors: 0 Queued Packets: 0
Router#show ip nat translation Pro Inside global Inside local Outside local Outside global icmp 201.15.3.5:628 10.1.1.7:628 201.15.3.17:628 201.15.3.17:628 icmp 201.15.3.5:629 10.1.1.7:629 201.15.3.6:629 201.15.3.6:629 icmp 201.15.3.5:610 10.1.1.8:610 201.15.3.17:610 201.15.3.17:610 icmp 201.15.3.5:611 10.1.1.8:611 201.15.3.6:611 201.15.3.6:611 icmp 201.15.3.5:727 10.1.1.17:727 201.15.3.17:727 201.15.3.17:727 icmp 201.15.3.5:728 10.1.1.17:728 201.15.3.6:728 201.15.3.6:728 icmp 201.15.3.5:633 10.1.1.21:633 201.15.3.17:633 201.15.3.17:633 icmp 201.15.3.5:634 10.1.1.21:634 201.15.3.6:634 201.15.3.6:634 icmp 201.15.3.5:480 10.2.2.1:480 201.15.3.17:480 201.15.3.17:480 icmp 201.15.3.5:481 10.2.2.1:481 201.15.3.6:481 201.15.3.6:481 icmp 201.15.3.5:840 10.10.123.2:840 201.15.3.17:840 201.15.3.17:840 icmp 201.15.3.5:841 10.10.123.2:841 201.15.3.6:841 201.15.3.6:841 icmp 201.15.3.5:578 10.10.123.3:578 201.15.3.17:578 201.15.3.17:578 icmp 201.15.3.5:579 10.10.123.3:579 201.15.3.6:579 201.15.3.6:579 icmp 201.15.3.5:595 192.168.1.1:595 201.15.3.17:595 201.15.3.17:595 icmp 201.15.3.5:596 192.168.1.1:596 201.15.3.6:596 201.15.3.6:596
From that we can see the correct answer should be “show ip nat statistics”.
Question 14
[am4show have=’p2;’]Which NAT term is defined as a group of addresses available for NAT use?
A. one-way nat
B. static nat
C. dynamic nat
D. nat pool
Answer: D[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Refer to the exhibit. A TFTP server has recently been installed in the Atlanta office. The network administrator is located in the NY office and has made a console connection to the NY router. After establishing the connection they are unable to backup the configuration file and IOS of the NY router to the TFTP server. What is the cause of this problem?

A. The NY router has an incorrect subnet mask.
B. The TFTP server has an incorrect IP address.
C. The TFTP server has an incorrect subnet mask.
D. The network administrator computer has an incorrect IP address.
Answer: C[/am4show]
Question 2
[am4show have=’p2;’]Refer to the exhibit. A network administrator has configured a Catalyst 2950 switch for remote management by pasting into the console the configuration commands that are shown in the exhibit. However, a Telnet session cannot be successfully established from a remote host. What should be done to fix this problem?
| interface vlan 1 ip address 192.168.17.253 255.255.255.240 no shutdown exit ip default-gateway 192.168.17.1 line vty 0 15 password cisco login exit |
A. Change the first line to interface fastethernet 0/1.
B. Change the first line to interface vlan 0/1.
C. Change the fifth line to ip default-gateway 192.168.17.241.
D. Change the fifth line to ip route 0.0.0.0 0.0.0.0 192.168.17.1.
E. Change the sixth line to line con 0.
Answer: C[/am4show]
Question 3
[am4show have=’p2;’]Refer to the exhibit. The two connected ports on the switch are not turning orange or green. What would be the most effective steps to troubleshoot this physical layer problem? (Choose three)
A. Ensure that the Ethernet encapsulations match on the interconnected router and switch ports.
B. Ensure that cables A and B are straight-through cables.
C. Ensure cable A is plugged into a trunk port.
D. Ensure the switch has power.
E. Reboot all of the devices.
F. Reseat all cables.
Answer: B D F[/am4show]
Explanation
The ports on the switch are not up indicating it is a layer 1 (physical) problem so we should check cable type, power and how they are plugged in.
Question 4
[am4show have=’p2;’]Refer to the exhibit. A person is trying to send a file from a host on Network A of the JAX Company to a server on Network Z of the XYZ Company. The file transfer fails. The host on Network A can communicate with other hosts on Network A. Which command, issued from router RTA, would be the most useful for troubleshooting this problem?
A. show flash:
B. show history
C. show version
D. show interfaces
E. show controllers serial
Answer: D[/am4show]
Question 5
[am4show have=’p2;’]Refer to the exhibit. A user cannot reach any web sites on the Internet, but others in the department are not having a problem. What is the most likely cause of the problem?
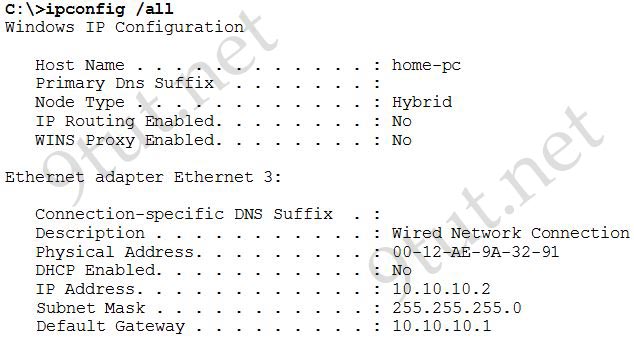
A. IP routing is not enabled.
B. The default gateway is not in the same subnet.
C. A DNS server address is not reachable by the PC.
D. A DHCP server address is not reachable by the PC.
E. NAT has not been configured on the router that connects to the Internet.
Answer: C[/am4show]
Question 6
[am4show have=’p2;’]Refer to the exhibit. A network administrator is troubleshooting a connectivity problem on the serial interfaces. The output from the show interfaces command on both routers shows that the serial interface is up, line protocol is down. Given the partial output for the show running-config in the exhibit, what is the most likely cause of this problem?

A. The serial cable is bad.
B. The MTU is incorrectly configured.
C. The Layer 2 framing is misconfigured.
D. The IP addresses are not in the same subnet.
Answer: C[/am4show]
Question 7
[am4show have=’p2;’]While troubleshooting a connectivity issue from a PC you obtain the following information:
Local PC IP address: 10.0.0.35/24
Default Gateway: 10.0.0.1
Remote Sever: 10.5.75.250/24
You then conduct the following tests from the local PC:
Ping 127.0.0.1 – Successful
Ping 10.0.0.35 – Successful
Ping 10.0.0.1 – Unsuccessful
Ping 10.5.75.250 – Unsuccessful
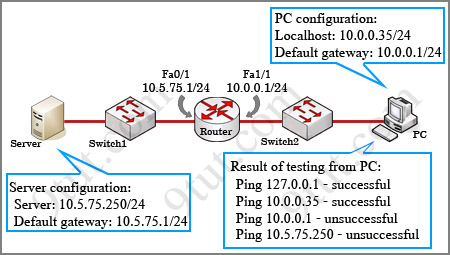
What is the underlying cause of this problem?
A. A remote physical layer problem exists.
B. The host NIC is not functioning.
C. TCP/IP has not been correctly installed on the host.
D. A local physical layer problem exists.
Answer: D[/am4show]
Question 8
[am4show have=’p2;’]Refer to the exhibit. A host is connected to switch port fa0/3. The host and switch have been fully configured for IP connectivity as shown. However, the indicator LED on switch port fa0/3 is not on, and the host cannot communicate with any other hosts including those connected to VLAN 2 on the same switch. Based on the given information, what is the problem?
A. switch port fa0/3 is not configured as a trunk port
B. there is a bad cable
C. the switch has been assigned an incorrect subnet mask
D. switch port fa0/3 has been blocked by STP
E. the switch and the host must be in the same subnet
Answer: B[/am4show]
Question 9
[am4show have=’p2;’]Refer to the exhibit:

Serial0/0 does not respond to a ping request from a host on the FastEthernet0/0 LAN. How can this problem be corrected?
A. Enable the Serial 0/0 interface.
B. Correct the IP address for Serial 0/0.
C. Correct the IP address for FastEthernet 0/0.
D. Change the encapsulation type on Serial 0/0.
E. Enable autoconfiguration on the Serial 0/0 interface.
Answer: A[/am4show]
Explanation
Serial0/0 is “administratively down”, that means this interface is shutting down.
Question 10
[am4show have=’p2;’]Refer to the exhibit. Why was this message received?
| Router#telnet 10.3.1.2 Trying 10.3.1.2 … Open Password required, but none set |
A. No VTY password has been set.
B. No enable password has been set.
C. No console password has been set.
D. No enable secret password has been set.
E. The login command has not been set on CON 0
F. The login command has not been set on the VTY ports.
Answer: A[/am4show]
Question 11
[am4show have=’p2;’]Refer to the exhibit. Which two of the output fields could help you determine if a broadcast storm has occurred? (Choose two.)
A. giants
B. no buffer
C. collisions
D. ignored
E. dribble condition
Answer: B D[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Two routers named Atlanta and Brevard are connected by their serial interfaces as shown in the exhibit, but there is no data connectivity between them. The Atlanta router is known to have a correct configuration. Given the partial configurations shown in the exhibit, what is the problem on the Brevard router that is causing the lack of connectivity?
A. A loopback is not set
B. The IP address is incorrect.
C. The subnet mask is incorrect.
D. The serial line encapsulations are incompatible.
E. The maximum transmission unit (MTU) size is too large.
F. The bandwidth setting is incompatible with the connected interface.
Answer: B[/am4show]
Question 2
[am4show have=’p2;’]Refer to the exhibit. A network technician is unable to ping from R1 to R2. Using the output of the show interfaces serial0/1 command, what should the administrator do to correct the problem?
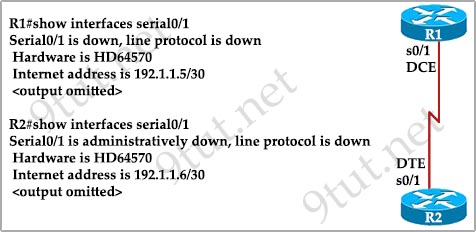
A. Replace the serial cable between R1 and R2.
B. Reseat the serial connectors on the R1 and R2 routers.
C. Configure the serial0/1 interface on R2 with the no shutdown command.
D. Configure the serial0/1 interface on R1 with the clock rate 56000 command.
E. Configure the serial0/1 interface on R1 with the ip address 192.1.1.7 255.255.255.252 command.
Answer: C[/am4show]
Question 3
[am4show have=’p2;’]Examine the network diagram and router output shown in the exhibit. Users on the BHM LAN are unable to access the server attached to the BHE router. What two things should be done to fix this problem? (Choose two)
A. Enter the configuration mode for interface fastethernet0/0.
B. Enter the configuration mode for interface serial0/0.
C. Enter the configuration mode for interface serial0/1.
D. Issue the run command.
E. Issue the enable command.
F. Issue the no shutdown command.
Answer: B F[/am4show]
Question 4
[am4show have=’p2;’]Refer to the exhibit. A network technician is unable to ping from R1 to R2. What will help correct the problem?
A. Ensure that the serial cable is correctly plugged in to the interfaces.
B. Apply the clock rate 56000 configuration command to the serial0/1 interface of R1.
C. Configure the serial0/1 interfaces on R1 and R2 with the no shutdown command.
D. Change the address of the serial0/1 interface of R1 to 192.1.1.4.
E. Change the subnet masks of both interfaces to 255.255.255.240.
Answer: A[/am4show]
Question 5
[am4show have=’p2;’]What happens when the cable is too long?
A. Baby Giant
B. Late collision
C. Duplex mismatch
D. No connection
Answer: B[/am4show]
Explanation
A late collision is defined as any collision that occurs after the first 512 bits of the frame have been transmitted. The usual possible causes are full-duplex/half-duplex mismatch, exceeded Ethernet cable length limits, or defective hardware such as incorrect cabling, non-compliant number of hubs in the network, or a bad NIC.
Late collisions should never occur in a properly designed Ethernet network. They usually occur when Ethernet cables are too long or when there are too many repeaters in the network.
Reference: https://www.cisco.com/en/US/docs/internetworking/troubleshooting/guide/tr1904.html
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which technology supports the stateless assignment of IPv6 addresses?
A. DNS
B. DHCPv6
C. DHCP
D. autoconfiguration
Answer: B[/am4show]
Explanation
There are several ways to assign IPv6 to a device:
+ Static IPv6: The IPv6 address, subnet prefix length and default gateway are configured manually in the system configuration file.
+ Dynamic Host Configuration Protocol for IPv6 (DHCPv6): this mode requires a DHCPv6 server in your LAN. This is the most used mode for IPv6 assignment. There are two methods of DHCPv6:
– stateless mode: Only extended information, such as primary and optional secondary DNS server, is obtained from a DHCPv6 server. IPv6 address is not assigned, so the IPv6 address from the Ethernet configuration is set for a Static address of Ethernet interface.
– stateful mode: DHCPv6 server maintains a database of leased IPv6 addresses, and assigns to the client an unused IPv6 address. The DHCPv6 server specifies also a primary and optional secondary DNS server. The DNS server is used to resolve the IP address for a known host name.
+ IPv6 Stateless Address Autoconfiguration (SLAAC): provides the ability to address a host based on a network prefix that is advertised from a local network router via Router Advertisements (RA). Notice that with this mode, the device which requires an IPV6 always receive a dynamic IPv6 address.
The question asks about “stateless assignment of IPv6 addresses” which means stateless mode of DHCPv6.
Question 2
[am4show have=’p2;’]Which entity assigns IPv6 addresses to end users?
A. ICANN
B. APNIC
C. RIR
D. ISPs
Answer: D[/am4show]
Explanation
According to the official IANA website “Users are assigned IP addresses by Internet service providers (ISPs). ISPs obtain allocations of IP addresses from a local Internet registry (LIR) or National Internet Registry (NIR), or from their appropriate Regional Internet Registry (RIR): https://www.iana.org/numbers
Question 3
[am4show have=’p2;’]What is one requirement for interfaces to run IPv6?
A. An IPv6 address must be configured on the interface.
B. An IPv4 address must be configured.
C. Stateless autoconfiguration must be enabled after enabling IPv6 on the interface.
D. IPv6 must be enabled with the ipv6 enable command in global configuration mode.
Answer: A[/am4show]
Explanation
To run IPv6 on an interface we have to configure an IPv6 on that interface somehow -> A is correct.
IPv6 must be enabled first but with the “ipv6 unicast-routing”, not “ipv6 enable” command -> D is not correct.
Question 4
[am4show have=’p2;’]What is the requirement of configuring 6to4 tunnelling on two routers?
A. Both ipv6 and ipv4 must be configured
B. Only IPv6
C. Only IPv4
Answer: A[/am4show]
Question 5
[am4show have=’p2;’]Which command can you use to manually assign a static IPv6 address to a router interface?
A. ipv6 address PREFIX_1::1/64
B. ipv6 autoconfig 2001:db8:2222:7272::72/64
C. ipv6 autoconfig
D. ipv6 address 2001:db8:2222:7272::72/64
Answer: D[/am4show]
Question 6
[am4show have=’p2;’]Which two of these statements are true of IPv6 address representation? (Choose two)
A. The first 64 bits represent the dynamically created interface ID.
B. A single interface may be assigned multiple IPV6 addresses of any type.
C. Every IPV6 interface contains at least one loopback address.
D. Leading zeros in an IPV6 16 bit hexadecimal field are mandatory.
Answer: B C[/am4show]
Explanation
Leading zeros in IPv6 are optional do that 05C7 equals 5C7 and 0000 equals 0 -> D is not correct.
Question 7
[am4show have=’p2;’]Which option is a valid IPv6 address?
A. 2001:0000:130F::099a::12a
B. 2002:7654:A1AD:61:81AF:CCC1
C. FEC0:ABCD:WXYZ:0067::2A4
D. 2004:1:25A4:886F::1
Answer: D[/am4show]
Question 8
[am4show have=’p2;’]How many bits are contained in each field of an IPv6 address?
A. 24
B. 4
C. 8
D. 16
Answer: D[/am4show]
Question 9
[am4show have=’p2;’]Which three approaches can be used while migrating from an IPv4 addressing scheme to an IPv6 scheme? (Choose three)
A. static mapping of IPv4 address to IPv6 addresses
B. configuring IPv4 tunnels between IPv6 islands
C. use DHCPv6 to map IPv4 addresses to IPv6 addresses
D. use proxying and translation (NAT-PT) to translate IPv6 packets into IPv4 packets
E. configure IPv6 directly
F. enable dual-stack routing
Answer: B D F[/am4show]
Question 10
[am4show have=’p2;’]Which statement about IPv6 is true?
A. Addresses are not hierarchical and are assigned at random.
B. Broadcasts have been eliminated and replaced with multicasts.
C. There are 2.7 billion available addresses.
D. An interface can only be configured with one IPv6 address.
Answer: B[/am4show]
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Identify the four valid IPv6 addresses. (Choose four)
A. ::
B. ::192:168:0:1
C. 2000::
D. 2001:3452:4952:2837::
E. 2002:c0a8:101::42
F. 2003:dead:beef:4dad:23:46:bb:101
Answer: A B E F[/am4show]
Explanation
Answers B E F are correct because A and B are the short form of 0:0:0:0:192:168:0:1 and 2002:c0a8:0101:0:0:0:0:0042 while C are normal IPv6 address.
Answer A is correct because “::” is named the “unspecified” address and is typically used in the source field of a datagram that is sent by a device that seeks to have its IP address configured.
Answer C is not correct because a global-unicast IPv6 address is started with binary 001, denoted as 2000::/3 in IPv6 and it also known as an aggregatable global unicast address. The 2000:: (in particular, 2000::/3) is just a prefix and is not a valid IPv6 address.
In fact answer D is acceptable but it is considered the network portion of an IPv6 address so it is a worse choice than others.
The entire global-unicast IPv6 address range is from 2000::/128 to 3FFF:FFFF:FFFF:FFFF:FFFF:FFFF:FFFF/128, resulting in a total usable space of over 42,535,295,865,117,307,932,921,825,928,971,000,000 addresses, which is only 1/8th of the entire IPv6 address space!
Question 2
[am4show have=’p2;’]Which two statements describe characteristics of IPv6 unicast addressing? (Choose two)
A. Global addresses start with 2000::/3
B. Link-local addresses start with FE00:/12
C. Link-local addresses start with FF00::/10
D. There is only one loopback address and it is ::1
E. If a global address is assigned to an interface, then that is the only allowable address for the interface.
Answer: A D[/am4show]
Explanation
Below is the list of common kinds of IPv6 addresses:
| Loopback address | ::1 |
| Link-local address | FE80::/10 |
| Site-local address | FEC0::/10 |
| Global address | 2000::/3 |
| Multicast address | FF00::/8 |
From the above table, we learn that A and D are correct while B and C are incorrect. Notice that the IPv6 unicast loopback address is equivalent to the IPv4 loopback address, 127.0.0.1. The IPv6 loopback address is 0:0:0:0:0:0:0:1, or ::1.
E is not correct because of anycast addresses which are indistinguishable from normal unicast addresses. You can think of anycast addresses like this: “send it to nearest one which have this address”. An anycast address can be assigned to many interfaces and the first interface receives the packet destined for this anycast address will proceed the packet. A benefit of anycast addressing is the capability to share load to multiple hosts. An example of this benefit is if you are a Television provider with multiple servers and you want your users to use the nearest server to them then you can use anycast addressing for your servers. When the user initiates a connection to the anycast address, the packet will be routed to the nearest server (the user does not have to specify which server they want to use).
Question 3
[am4show have=’p2;’]Which statement is true?
A. An IPv6 address is 64 bits long and is represented as hexadecimal characters.
B. An IPv6 address is 32 bits long and is represented as decimal digits.
C. An IPv6 address is 128 bits long and is represented as decimal digits.
D. An IPv6 address is 128 bits long and is represented as hexadecimal characters.
Answer: D[/am4show]
Question 4
[am4show have=’p2;’]Which statements are TRUE regarding Internet Protocol version 6 (IPv6) addresses? (Choose three)
A. An IPv6 address is divided into eight 16-bit groups.
B. A double colon (::) can only be used once in a single IPv6 address.
C. IPv6 addresses are 196 bits in length.
D. Leading zeros cannot be omitted in an IPv6 address.
E. Groups with a value of 0 can be represented with a single 0 in IPv6 address.
Answer: A B E[/am4show]
Question 5
[am4show have=’p2;’]Which technique can you use to route IPv6 traffic over an IPv4 infrastructure?
A. NAT
B. 6to4 tunneling
C. L2TPv3
D. dual-stack
Answer: B[/am4show]
Explanation
“6to4 tunneling” is a technique which enables encapsulation of IPv6 packets into IPv4 for transport across an IPv4 network.
Question 6
[am4show have=’p2;’]Which header field is new in IPv6?
A. Version
B. Hop Limit
C. Flow Label
D. Traffic Class
Answer: C[/am4show]
Explanation
The IPv4 and IPv6 headers are shown below for your comparison. As we can see the Flow Label, Hop Limit, Traffic Class fields are all new but in fact Hop Limit in IPv6 is same as Time to live (TTL) in IPv4. Traffic Class is the equivalent of the DiffServ/DSCP portion of the IPv4 packet (in “Type of service” field) which carries the QoS markings of the packet. Just like in IPv4 the first 6 bits are designated for the DSCP value, and the next 2 bits are for ECN (Explicit Congestion Notifications) capable devices.
Flow-Label: This 20-bit field provides a special service for real-time applications. It can be used to inform routers and switches to maintain the same path for the packet flow so that packets are not reordered.
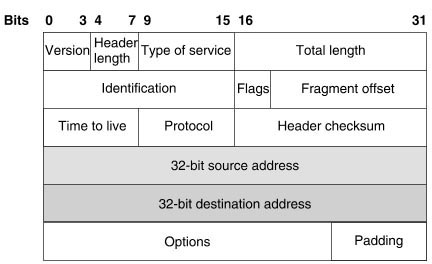 IPv4 Header fields
IPv4 Header fields
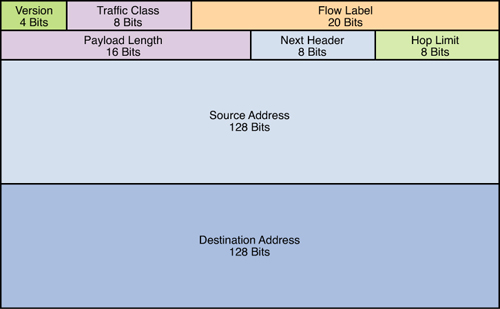 IPv6 Header fields
IPv6 Header fields
IPv6 eliminates the Header Checksum field, which handles error checking in IPv4.
Question 7
[am4show have=’p2;’]Which sequence begins a unique local IPv6 address in binary notation?
A. 1111000
B. 11111000
C. 11111100
D. 11100000
Answer: C[/am4show]
Explanation
A IPv6 Unique Local Address is an IPv6 address in the block FC00::/7. It is the approximate IPv6 counterpart of the IPv4 private address. It is not routable on the global Internet. Therefore FC00::/7 is equivalent to 1111 1100 0000 0000::/7 in binary notation.
Note: In the past, Site-local addresses (FEC0::/10) are equivalent to private IP addresses in IPv4 but now they are deprecated.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]Which NTP command configures the local device as an NTP reference clock source?
A. ntp peer
B. ntp broadcast
C. ntp master
D. ntp server
Answer: C[/am4show]
Explanation
If you want your system to become an authoritative NTP server from which other internal routers or machines can synchronise, you can achieve this with the “ntp master” command.
Note: Use the “ntp server” to form an association with a NTP server.
Question 2
[am4show have=’p2;’]Which NTP concept indicates the distance between a device and the reliable time source?
A. clock offset
B. stratum
C. reference
D. dispersion
Answer: B[/am4show]
Explanation
NTP uses a stratum to describe the distance between a network device and an authoritative time source:
+ A stratum 1 time server is directly attached to an authoritative time source (such as a radio or atomic clock or a GPS time source).
+ A stratum 2 NTP server receives its time through NTP from a stratum 1 time server.
Question 3
[am4show have=’p2;’]Which statement about NTP is true?
A. each device is enabled as server by default
B. the default authentication key number is 1
C. the default stratum number is 5
D. the default source of a NTP message is the interface connected to the next-hop for server peer address
Answer: D[/am4show]
Explanation
There is no document saying the default mode of NTP is server so we assume answer A is not correct.
There is no default authentication key number -> B is not correct.
If the network has “ntp master” configured and it cannot reach any clock with a lower stratum number, the system claims to be synchronized at the configured stratum number, and other systems synchronize to it via NTP. By default, the master clock function is disabled. When enabled, the default stratum is 8 -> Answer C is not correct.
NTP sets the source IP address for all NTP packets based on the address of the interface through which the NTP packet are sent. But there is no correct answer so maybe answer D is the best choice.
[am4show have=’p2;’]
Premium Member: You can test your knowledge with these questions first via this link.
[/am4show]
Question 1
[am4show have=’p2;’]An administrator has connected devices to a switch and, for security reasons, wants the dynamically learned MAC addresses from the address table added to the running configuration. What must be done to accomplish this?
A. Enable port security and use the keyword sticky.
B. Set the switchport mode to trunk and save the running configuration.
C. Use the switchport protected command to have the MAC addresses added to the configuration.
D. Use the no switchport port-security command to allow MAC addresses to be added to the configuration.
Answer: A[/am4show]
Explanation
This is the full command mentioned in answer A:
switchport port-security mac-address sticky [MAC]
If we don’t specify the MAC address (like in this question) then the switch will dynamically learn the attached MAC Address and place it into your running-configuration.
Question 2
[am4show have=’p2;’]The following commands are entered on the router:
Burbank(config)# enable secret fortress
Burbank(config)# line con 0
Burbank(config-line)# login
Burbank(config-line)# password n0way1n
Burbank(config-line)# exit
Burbank(config)# service password-encryption
What is the purpose of the last command entered?
A. to require the user to enter an encrypted password during the login process
B. to prevent the vty, console, and enable passwords from being displayed in plain text in the configuration files
C. to encrypt the enable secret password
D. to provide login encryption services between hosts attached to the router
Answer: B[/am4show]
Explanation
The “service password-encryption” command encrypts passwords used by “enable password” global configuration command, as well as the password line configuration command (VTY, console) that are saved in the router configuration file.
Note: The secret password (configured by the command “enable secret fortress”) is always encrypted even if the “service password-encryption” command is not used.
Also, the “service password-encryption” command encrypts both current and future passwords.
Question 3
[am4show have=’p2;’]Why would a network administrator configure port security on a switch?
A. to prevent unauthorized Telnet access to a switch port
B. to prevent unauthorized hosts from accessing the LAN
C. to limit the number of Layer 2 broadcasts on a particular switch port
D. block unauthorized access to the switch management interfaces
Answer: B[/am4show]
Question 4
[am4show have=’p2;’]A company has placed a networked PC in a lobby so guests can have access to the corporate directory. A security concern is that someone will disconnect the directory PC and re-connect their laptop computer and have access to the corporate network. For the port servicing the lobby, which three configuration steps should be performed on the switch to prevent this? (Choose three)
A. Enable port security.
B. Create the port as a trunk port.
C. Create the port as an access port.
D Create the port as a protected port.
E. Set the port security aging time to 0.
F. Statically assign the MAC address to the address table.
G. Configure the switch to discover new MAC addresses after a set time of inactivity.
Answer: A C F[/am4show]
Explanation
By configuring the port connected with the directory PC as access port the network administrator will mitigate a lot of security issues because access port does not have as much privilege as a trunk port -> C is correct.
The port security feature can also help mitigate security issue because it can learn the MAC address of the directory PC. When another laptop is plugged into the port, the switch will automatically block or shut down that port (if suitable configuration is used) -> A is correct. But nowadays a hacker can fake the MAC address of the directory PC.
By statically assigning the MAC address to the address table, only that MAC address can access to the network -> F is correct.
Question 5
[am4show have=’p2;’]What is the effect of using the service password-encryption command?
A. Only the enable password will be encrypted.
B. Only the enable secret password will be encrypted.
C. Only passwords configured after the command has been entered will be encrypted.
D. It will encrypt the secret password and remove the enable secret password from the configuration.
E. It will encrypt all current and future passwords.
Answer: E[/am4show]
Explanation
The “service password-encryption” command encrypts passwords used by “enable password” global configuration command, as well as the password line configuration command (VTY, console) that are saved in the router configuration file.
The “service password-encryption” command encrypts both current and future passwords.
Question 6
[am4show have=’p2;’]How can you ensure that only the MAC address of a server is allowed by switch port Fa0/1?
A. Configure port Fa0/1 to accept connections only from the static IP address of the server.
B. Configure the server MAC address as a static entry of port security.
C. Use a proprietary connector type on Fa0/1 that is incomputable with other host connectors.
D. Bind the IP address of the server to its MAC address on the switch to prevent other hosts from spoofing the server IP address.
Answer: B[/am4show]
Explanation
The command to configure port security on a switch is (in interface configuration mode):
switchport port-security mac-address sticky [MAC]
In this case we will type the server MAC address. That MAC address will be stored in the address table, and added to the switch running configuration.
Note: If we don’t specify the MAC address then the switch will dynamically learn the attached MAC Address and place it into your running-configuration
Question 7
[am4show have=’p2;’]Refer to the exhibit. The network administrator made the entries that are shown and then saved the configuration. From a console connection, what password or password sequence is required for the administrator to access privileged mode on Router1?
| Router# configure terminal Router(config)# hostname Router1 Router1(config)# enable secret sanfran Router1(config)# enable password cisco Router1(config)# line vty 0 4 Router1(config-line)# password sanjose Route r1(config-line)# |
A. cisco
B. sanfran
C. sanjose
D. either cisco or sanfran
E. either cisco or sanjose
F. sanjose and sanfran
Answer: B[/am4show]
Explanation
In the configuration above we have three passwords:
+ The “enable secret” password: sanfran
+ The “enable password” password: cisco
+ The VTY line password: sanjose
The two first “enable secret” and “enable password” are used to set password for entering privilege mode (an example of privilege mode: Router#). Both of them will be stored in the running configuration. But the password in “enable secret” command is always encrypted using MD5 hash while the password in “enable password” is in plain text.
Note: If you want to encrypt “enable password” you can use the command “service password-encryption” but it will be encrypted with a very basic form of encryption called vigenere cipher, which is very weak.
When you configure both an enable and a secret password, the secret password will be used -> B is correct.
Question 8
[am4show have=’p2;’]What should be part of a comprehensive network security plan?
A. Allow users to develop their own approach to network security
B. Physically secure network equipment from potential access by unauthorized individuals
C. Encourage users to use personal information in their passwords to minimize the likelihood of passwords being forgotten
D. Delay deployment of software patches and updates until their effect on end-user equipment is well known and widely reported
E. Minimize network overhead by deactivating automatic antivirus client updates
Answer: B[/am4show]
Explanation
All other answers are not recommended for a network security plan so only B is the correct answer.
Question 9
[am4show have=’p2;’]What are two recommended ways of protecting network device configuration files from outside network security threats? (Choose two)
A. Allow unrestricted access to the console or VTY ports.
B. Use a firewall to restrict access from the outside to the network devices.
C. Always use Telnet to access the device command line because its data is automatically encrypted.
D. Use SSH or another encrypted and authenticated transport to access device configurations.
E. Prevent the loss of passwords by disabling password encryption.
Answer: B D[/am4show]
Question 10
[am4show have=’p2;’]From which of the following attacks can Message Authentication Code (MAC) shield your network?
A. DoS
B. DDoS
C. spoofing
D. SYN floods
Answer: C[/am4show]